What is Google Workspace / G-suite Data Loss Prevention (DLP)
Curious about GSuite or Google Workspace DLP? Find out how DLP tools can help you protect your data and safeguard your business from potential security risks in google workspace
When people refer to Google DLP, they’re usually talking about one of two different products that serve distinct purposes:
Both help reduce exposure of PII, PHI, and PCI data — but they live in different layers of Google’s ecosystem. Workspace DLP governs collaboration and sharing. Cloud DLP / Sensitive Data Protection powers programmatic detection and transformation inside data platforms.
Google Workspace isn’t a single application — it’s an ecosystem. Gmail, Drive, Docs, Sheets, Slides, Chat, and Meet all move sensitive data every day, often outside formal workflows.
That’s why Google Workspace DLP cannot stop at Drive.
A file-centric approach misses the most common and most dangerous data exfiltration path: communication.
The email problem:
Over 90% of security incidents still start with email. Sensitive data leaves organizations far more often through misdirected emails, auto-forwards, replies-all, and attachments than through intentional file sharing.
And unlike Drive, email leaks are usually instant, irreversible, and invisible until it’s too late.
A real Google Workspace DLP strategy must:
This guide covers DLP across the entire Google Workspace suite — with a deeper focus on Gmail, because that’s where most real-world data loss actually happens.
Start simple and expand over time:
In this page, Google DLP refers to Google Workspace DLP — the admin-side DLP for Gmail and Drive.
Google Cloud DLP / Sensitive Data Protection is a developer-facing API and service that discovers, classifies, and de-identifies data across cloud stores and pipelines using masking or tokenization.
Use Workspace DLP to govern collaboration and file-sharing.
Use Cloud DLP when you need programmatic discovery or de-identification inside apps, pipelines, or data lakes.
✨ Gmail – Detects sensitive data in messages and attachments. You can alert, quarantine, or block messages that violate policy.
✨ Drive / Docs / Sheets / Slides – Scans file content, labels risk, and applies sharing controls. Common detectors include payment cards, national IDs, and health terms.
For healthcare and life-sciences organizations, maintaining HIPAA compliance inside Workspace is critical — see our guide: [HIPAA on Google Workspace].
Policy tips: Coach users with in-context hints instead of hard blocks when business flow matters.
Reporting: Review incidents regularly and adjust thresholds to balance security and productivity.
1️⃣ PCI remediation and redaction in Gmail
Strac automatically redacts or masks PCI, PII, or PHI data in both incoming and outgoing emails — including message bodies and attachments — before delivery or storage. This protects users from accidental data exposure while keeping business flow uninterrupted.
2️⃣ Outgoing email control and workflow
If an outbound email contains sensitive data:
3️⃣ Drive remediation beyond detection
Strac automatically remediates risky Drive files by:
4️⃣ Extend protection beyond Drive
Keep Google’s sharing controls for Drive, and add Strac scanning and remediation in Slack threads, Salesforce cases, Zendesk tickets, Jira projects, and GenAI tools to stop sensitive data from leaking once it leaves Google.
5️⃣ OCR for images and exports
Strac’s OCR detects PII/PHI/PCI inside screenshots, scanned PDFs, and image attachments — redacting only the risky text segments, not the entire file.
6️⃣ One policy everywhere
Write “mask 16-digit PANs + block external shares” once and enforce it consistently across Gmail, Drive, Slack, Salesforce, and GenAI tools.
7️⃣ Centralized alerting and SIEM integration
Strac routes DLP alerts to Slack, Microsoft Teams, email, or SIEM systems for unified visibility, so security teams can respond instantly.
While Google Workspace DLP offers a foundational layer of protection, Strac extends data visibility and control far beyond native google workspace email dlp policies.
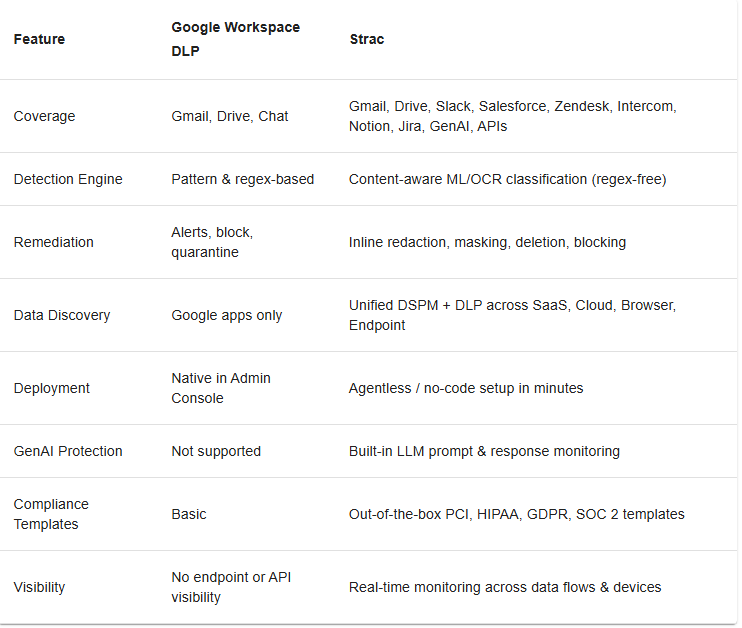
Strac expands the google workspace dlp overview into a complete SaaS security fabric, giving security teams visibility across every data channel; not just Gmail and Drive.
Unlike Google’s native tools, Strac unifies DSPM (Data Security Posture Management) with DLP to discover, classify, and remediate sensitive data in real time.
Strac integrates natively with Slack, Salesforce, Zendesk, Intercom, Notion, and GenAI tools; enabling consistent policies and unified visibility across hybrid stacks.
This prevents the fragmentation that occurs when sensitive data leaves Google Workspace through API connections or third-party collaboration tools.

With real-time detection, Strac automatically flags and redacts sensitive content across SaaS, browser, and endpoint surfaces; before data is exposed.
Unlike Google’s delayed policy enforcement, Strac gives instant visibility and contextual alerts, helping teams respond within seconds rather than hours.
Strac’s ML-powered engine detects PII, PHI, and PCI data without relying on regex; minimizing noise and false positives.
It reads unstructured text, attachments, and even screenshots using OCR, providing unmatched context that native google workspace dlp email rules can’t capture.
Beyond blocking or alerting, Strac can redact, mask, delete, or quarantine data directly inside Google Workspace or connected apps.
For example, a mis-sent Gmail with exposed PHI can be instantly quarantined, while Drive files with public links can be auto-restricted; no manual review needed.
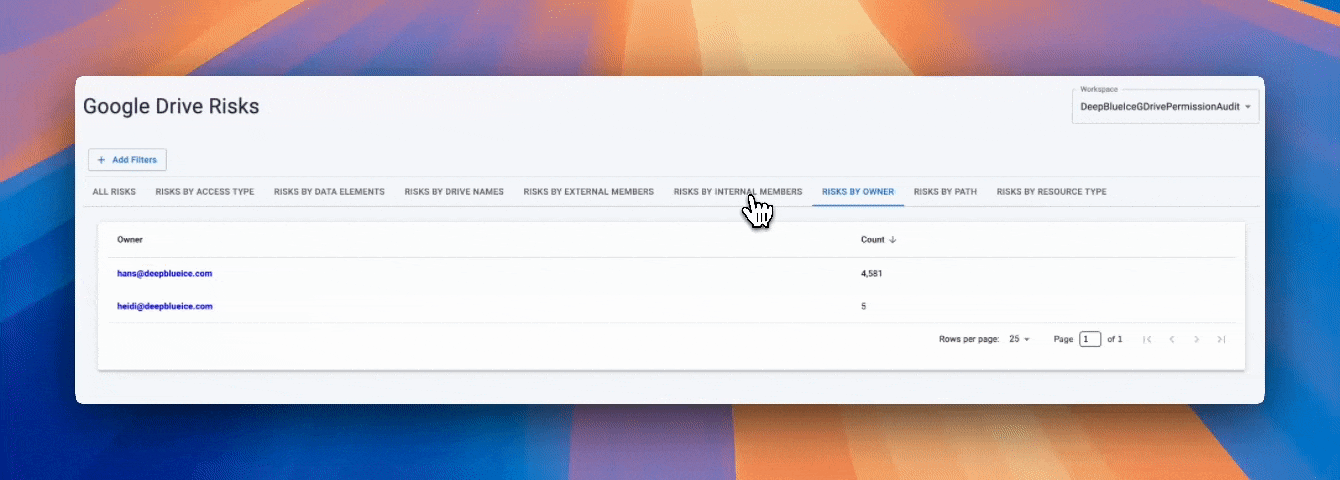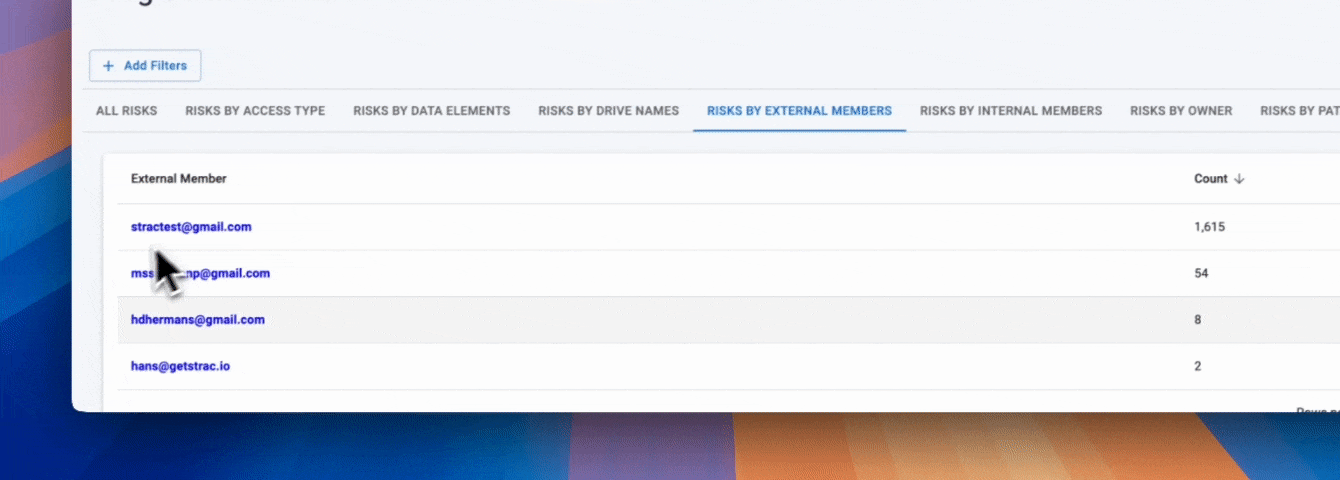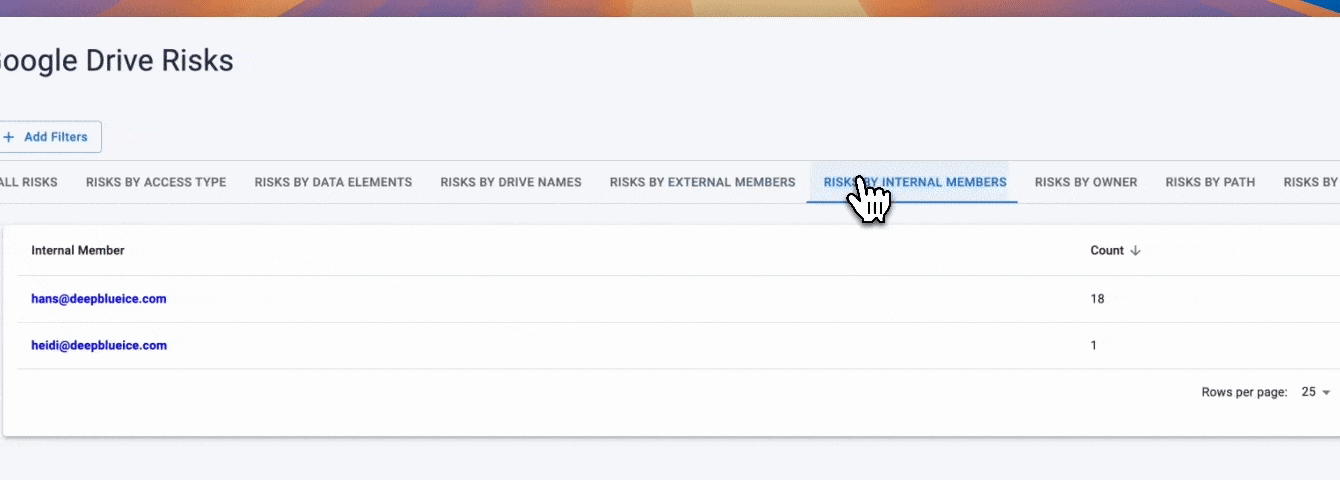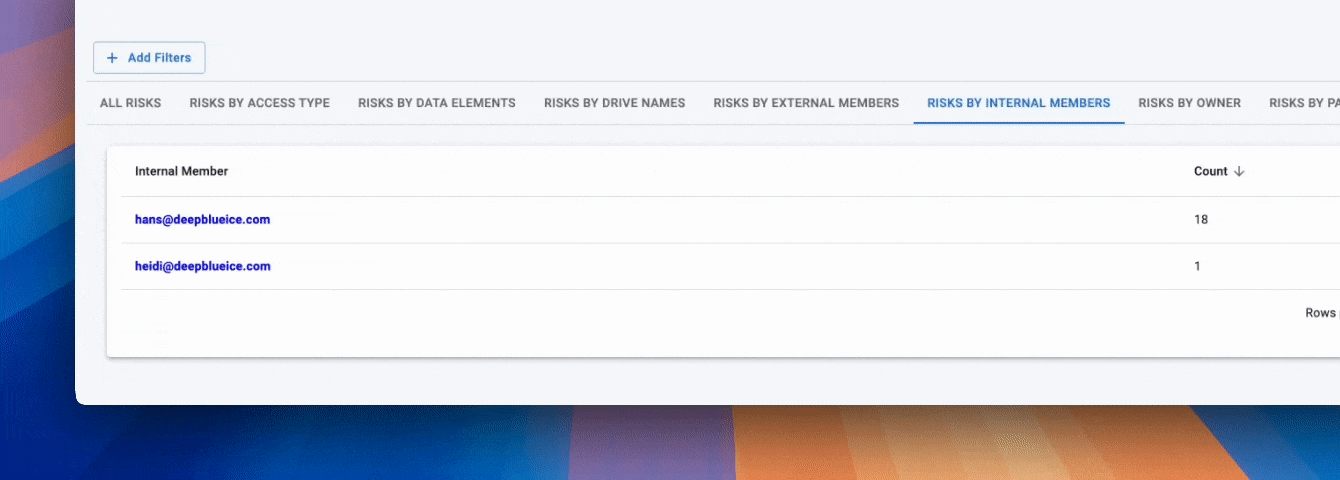
In Google Workspace DLP, labels are meant to signal how sensitive a file is, but on their own they lack operational context. A label does not tell you whether a file is publicly shared, accessible to external users, or sitting in an over-permissive Shared Drive. Strac bridges this gap by making Google Drive labels visible inside the Strac Vault, where they are evaluated alongside live exposure and access data, turning Workspace labels into a practical control for data loss prevention.
• Google Drive labels applied natively in Workspace are surfaced directly in Strac Vault
• Labels are shown with sharing status, exposure level, owners, paths, and access scope
• Security teams can assess labeled files based on real risk, not just classification
• Label changes remain aligned with Google Drive, keeping Workspace governance consistent
This approach keeps Google Workspace DLP focused on collaboration controls, while Strac adds the missing visibility layer needed to understand how labeled data is actually exposed across Drive.
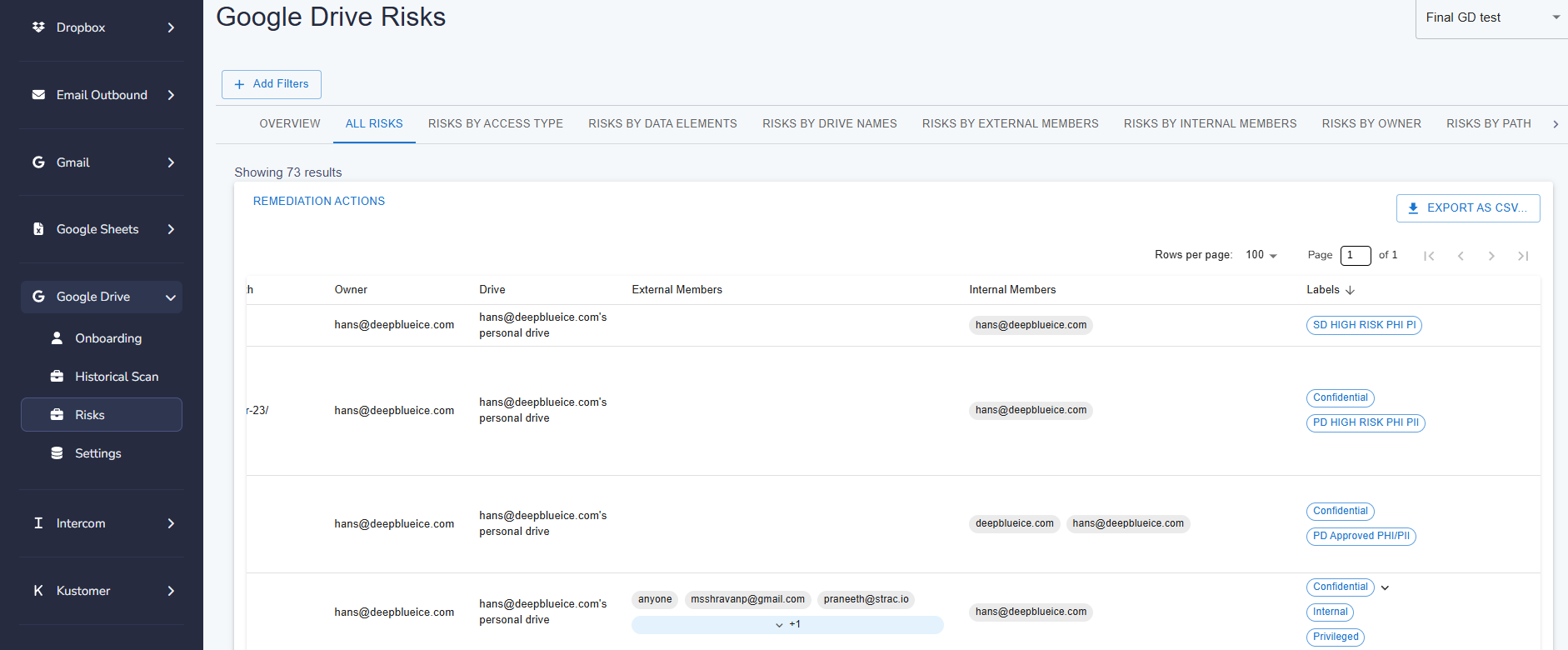
Google Workspace is the backbone of collaboration for millions of businesses, offering tools like Gmail, Google Drive, Docs, and Sheets. But with seamless collaboration comes data security risks. Sensitive data—ranging from customer PII, financial records, trade secrets, and employee payroll information—flows through these apps daily.
Yet, many organizations fail to realize the gaps in Google’s built-in security. A misplaced access permission, an overly shared Google Drive file, or an email sent to the wrong recipient can lead to costly data leaks.
That’s where Google Workspace Data Loss Prevention (DLP) comes in.
Google Workspace, as a cloud-based SaaS platform, is accessible from anywhere. While this makes it great for remote teams, it also introduces serious security risks:
🔹 Data Overexposure: Employees often overshare Google Drive files by setting permissions to "Anyone with the link." This creates a hidden attack surface for data leaks.
🔹 Misconfigured Email Settings: Gmail users can accidentally send sensitive information (credit card numbers, SSNs, patient health data) to unauthorized recipients.
🔹 Lack of Real-time Monitoring: Google’s native DLP provides some alerts, but there’s no real-time visibility into where your sensitive data is stored or how it’s being accessed.
🔹 Compliance Risks: If your organization is bound by GDPR, HIPAA, PCI DSS, or CCPA, you must prevent unauthorized access to sensitive data—or face fines and legal consequences.

Real-World Data Risk Stats:
Yes—each app presents different risks:
Protecting each app requires context-aware DLP that understands data movement across platforms. See how this applies in our Google Cloud DLP breakdown.
Yes, Google offers native DLP features, but they are limited.
✅ Google Drive DLP: Lets admins set up rules to detect sensitive data, but advanced security features (like blocking file sharing in real-time) are only available in higher-tier plans (Enterprise edition).
✅ Gmail DLP: Scans outbound emails for sensitive data, but only flags violations—it doesn’t provide automated remediation or advanced risk scoring.
🚨 The Limitations of Google’s Built-in DLP

To learn more about google workspace enterprise dlp limitations, please checkout: https://www.strac.io/blog/google-drive-dlp#what-are-the-google-workspace-enterprise-dlp-limitations
Google Workspace DLP (Data Loss Prevention) offers solid native capabilities for organizations using Gmail and Drive, but it has several key limitations—especially for companies that need enterprise-grade protection or want to extend security beyond the basics.
Here are the main limitations of Google Workspace DLP:
Google DLP works only within Google Workspace services (Gmail, Google Drive, Chat, etc.). It doesn't extend to other SaaS apps like Slack, Jira, Salesforce, Zendesk, or endpoint devices. So any sensitive data that moves outside the Google ecosystem goes unprotected.
Why it matters: Most companies use multiple SaaS apps; DLP should ideally provide unified visibility across them.
Google DLP is generally forward-looking — it scans files and emails when they're being shared or sent. It doesn’t:
Why it matters: Sensitive files that were shared in the past remain exposed unless manually reviewed.
Google Workspace DLP relies on predefined detectors (like SSNs, credit card numbers). It lacks:
Why it matters: Many real-world sensitive data types don't follow strict regex formats.
Available actions in Google Workspace DLP are limited to:
It does not support:
Why it matters: Alerting is just one piece—remediation is key in real-time DLP.
Creating and managing DLP rules in Google Admin Console can be:
Why it matters: At scale, security teams want intuitive UI, reusable templates, and flexible rule-building.
Google Workspace DLP doesn’t monitor:
Why it matters: A full DLP solution must cover endpoints to stop data exfiltration outside sanctioned apps.
There is no real-time incident response dashboard. Alerts are buried in the Security Center or logs, often requiring SIEM integration for actionability.
Why it matters: Faster response = reduced risk.
Google Workspace DLP doesn’t provide any visibility or control over usage of tools like ChatGPT, Gemini, or third-party GenAI tools integrated with Google Docs or Gmail.
Why it matters: With the rise of AI tools, companies need to ensure no sensitive data is shared with LLMs.
Yes—but it requires proper configuration and shared responsibility. You must:
Strac helps you go further with real-time classification and redaction. See how in our GDPR DLP guide.

Compare solutions in our DLP software guide
Use least-privilege permissions and monitor group memberships regularly.

Prevent credential-based attacks by requiring two-factor authentication for all users.

Detect anomalies like location changes, large file transfers, or mass deletions.
It is common to have third party plugins/apps access Google workspace. Understand the OAuth scopes

Train employees to avoid phishing, mishandling PII, and accidental shares.
Deploy a solution like Strac that integrates across your entire Google Workspace stack and automates protection.

Strac’s DLP engine detects:
Detection works across:
Yes—Strac integrates natively with:
This ensures complete visibility and remediation, no matter where the data lives or flows.
Here are six proven ways to protect your business from Google Workspace data leaks.
Many organizations unknowingly expose confidential Google Drive files due to open sharing settings.
✅ Solution:
📌 Strac’s Google Drive DLP automatically scans for publicly shared files, flags risks, and revokes external access in real-time.

If too many employees have admin or editing access, data leaks become inevitable.
✅ Solution:
📌 Strac’s DLP solution lets you enforce access policies automatically based on data sensitivity.
Weak passwords are a leading cause of Google Workspace data breaches.
✅ Solution:
📌 Strac’s Google Workspace Security scans for weak user credentials and enforces strong authentication policies.
Employees may accidentally send sensitive customer data via Gmail.
✅ Solution:
📌 Strac’s Gmail DLP solution integrates with Gmail to detect and block data leaks before they happen.
🔹 Google’s built-in DLP is not enough—it lacks real-time remediation, SaaS-wide visibility, and proactive security controls.
🔹 Strac Google Workspace DLP offers enterprise-grade data protection across Google Drive, Gmail, Docs, and Sheets.
Together, Strac and Google DLP deliver end-to-end protection — from native Workspace enforcement to real-time remediation across every SaaS, Cloud, and GenAI application.
Learn more about Google Drive DLP by Strac and see how unified policies, redaction, and remediation keep sensitive data safe everywhere.
Yes, Google Workspace includes built-in DLP controls for Gmail, Drive, and Chat. These policies allow admins to detect and block sensitive information such as credit card numbers, SSNs, or confidential documents from being shared externally. However, native Google Workspace DLP email policies are limited to pattern-based detection and do not provide full visibility across non-Google apps or endpoints. That’s where tools like Strac enhance protection with real-time redaction, machine learning detection, and unified coverage.
Yes, Strac integrates seamlessly with Gmail, Google Drive, Google Chat, and Shared Drives, offering visibility and remediation actions directly inside those environments. It automatically discovers and redacts sensitive data across messages, attachments, and shared files. Strac also connects Google Workspace with tools like Slack, Salesforce, and Zendesk to create a unified data loss prevention layer beyond Google’s native coverage.
This post explains that Google offers native DLP for Gmail and Drive — but availability depends on your Workspace tier.
Gmail DLP is only included with Google Workspace Enterprise. Business Starter, Standard, and Plus plans do not include native Gmail DLP controls. That’s why many teams on Business plans rely on third-party DLP tools to protect Gmail without upgrading their entire Workspace license.
As described in this guide, Google Workspace DLP applies policies across supported services, but native policy flexibility is limited.
In practice, Gmail and Drive have very different risk profiles:
Advanced Workspace DLP implementations typically require separate rules per app — for example, stricter blocking on Gmail and softer controls on Drive sharing — which is difficult to achieve with native Google DLP alone.
Yes — as covered in this post, Google Workspace DLP scans outbound Gmail content, including attachments. However, there are important practical limitations not always obvious during setup:
This means sensitive data embedded in screenshots, scans, or large files can go undetected unless additional scanning capabilities are added.
This article highlights misdirected email as one of the most common data loss paths in Google Workspace.
Preventing it requires outbound Gmail inspection with clear remediation actions, such as:
The key is intervening before delivery, not auditing after the data has already left the organization.
As explained earlier in this post, these are two separate products built for different environments.
Workspace DLP is designed for employee collaboration risk. Cloud DLP is designed for developer and data platform use cases.
This post discusses data movement across Workspace apps, but it’s important to be explicit:
Google’s native Workspace DLP does not cover Google Chat or Google Meet.
Chat messages and file uploads are a growing source of sensitive data exposure, especially in support and engineering teams. Protecting these channels typically requires additional monitoring beyond native Google Workspace controls. Meet recording scanning is not natively supported today.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

