Top 17 Data Loss Prevention (DLP) Solutions of 2025
Compare top Data Loss Prevention (DLP) solutions for 2025. Get insights & find the best Data Loss Prevention solutions with our in-depth analysis.
Looking for the best Data Loss Prevention (DLP) solutions in 2025? This guide compares the top 17 Data Loss Prevention (DLP) solutions, including Microsoft Purview, Symantec (Broadcom), Forcepoint, Proofpoint, Netskope, Trellix, and Digital Guardian, across cloud, SaaS, endpoint, and GenAI use cases.
We also outline how to evaluate Data Loss Prevention (DLP) Solutions (false positives, Mac/Windows parity, browser enforcement, reporting) so you can pick the right DLP solution fast.
Data breaches can lead to significant financial losses, reputational damage, and legal repercussions. Implementing DLP tools helps organizations monitor, detect, and prevent unauthorized access or transmission of sensitive data. These tools are crucial for maintaining data integrity, protecting intellectual property, and ensuring compliance with regulations such as GDPR, HIPAA, and PCI DSS.
More than 83% of companies believe that the fundamental question is not “Will data breaches happen?” but instead, “When will it happen?”
The recent IBM report on cybersecurity has put some serious numbers on the table. As per the report, a data breach in the United States costs an average of $9.44 million. But more importantly, a breach at scale costs the company sensitive personal records of customers and the reputation of the firm.
So what should companies do to ensure maximum security during such times?
Get Data Loss Prevention (DLP) solution that offers easy-to-plug security solutions.
Read on to get the list of our top 17 Data Loss Prevention Solutions .
Here is a detailed evaluation checklist to help in selecting a DLP solution:
Capabilities: The software should identify and categorize sensitive data, both structured and unstructured, throughout the organization in different settings (cloud, on-premises, endpoints).
Accuracy: Precision is key in classification and determining when DLP policies are activated. The software should reduce instances of false positives for accurate data management.
Customization: For effective DLP management, DLP policies should be customizable to meet unique business requirements and risks. They should also offer flexibility in adjusting policies as data types and business processes evolve.
Usability: User-friendly interfaces should empower administrators to modify policies without requiring deep technical expertise.
System compatibility: The DLP solution should effortlessly connect with current IT systems, such as email platforms, network setups, and various security tools.
API support: Strong APIs are essential for easy integration with diverse security solutions, bolstering data protection and incident response capabilities.
Alerts and remediation: The solution should provide immediate alerts and support automatic corrective actions to prevent data breaches
Workflow tools: It should incorporate workflow tools for incident handling, such as tracking, analysis, and reporting, to ensure a timely and efficient response to security incidents.
Resource Efficiency: The DLP solution should function effectively without causing any noticeable slowdown in system performance orhindering user productivity.
Growth Capability: It should grow alongside theorganization, accommodating larger data volumes and broader operational needswithout sacrificing performance quality.
Compliance Support: The DLP solution should adhere toregulations such as GDPR, HIPAA, PCI-DSS, etc., including audit provisions,data handling rules, and breach notifications.
Updates: Regular updates should be provided to ensurecompliance with the changing legal landscape
Expense analysis: Thoroughly assess all expenses associatedwith the DLP solution's deployment, operation, and maintenance.
Return on Investment: Take into account the possiblefinancial benefits of preventing data breaches, enhancing operationalproductivity, and adhering to regulations.
Technical Support: It should have reliable technical supportround the clock to quickly resolve any possible issues.
Educational materials and guidance: The vendor must providethorough training and guidance materials for continuous solutionmaintenance.
Technology innovation: The solution should be flexibleenough to accommodate emerging technologies and changing security risks, likeencryption and artificial intelligence progressions.
Scalability: Ensuring future readiness also means having thecapacity to grow and adjust to new business sectors, locations, and dataformats.
Strac is the one-stop hub for all things Personally Identifiable Information (PII) that secures businesses & safeguards from compliance risks through the following practices:
The best part?

It seamlessly integrates with cloud and SaaS-based platforms such as Zendesk, Slack, Gmail, Office 365, Salesforce, Box, ChatGPT and a wide range of other products and is compliant with PCI, SOC 2, HIPAA, GDPR, NIST CSF and NIST 800-53.
This prevents confidential data leaks across the entire product suite. Something that needs to be observed or focused by other Data loss prevention software vendors.
It allows users to define custom policies on what data elements to redact, when to redact, who should access, get audit reports and more.

Apart from that, here are some other key highlights:

Ensure Complete Zendesk Data Security and Compliance with Strac
Detect and Mask (redact) sensitive Zendesk Comments and Tickets.

Secure Sensitive Data in Slack with Strac
Slack users often send messages containing sensitive customer information, making account protection crucial. Strac Slack app works across all Slack channels and pricing plans and receives audit reports of who accessed what messages.

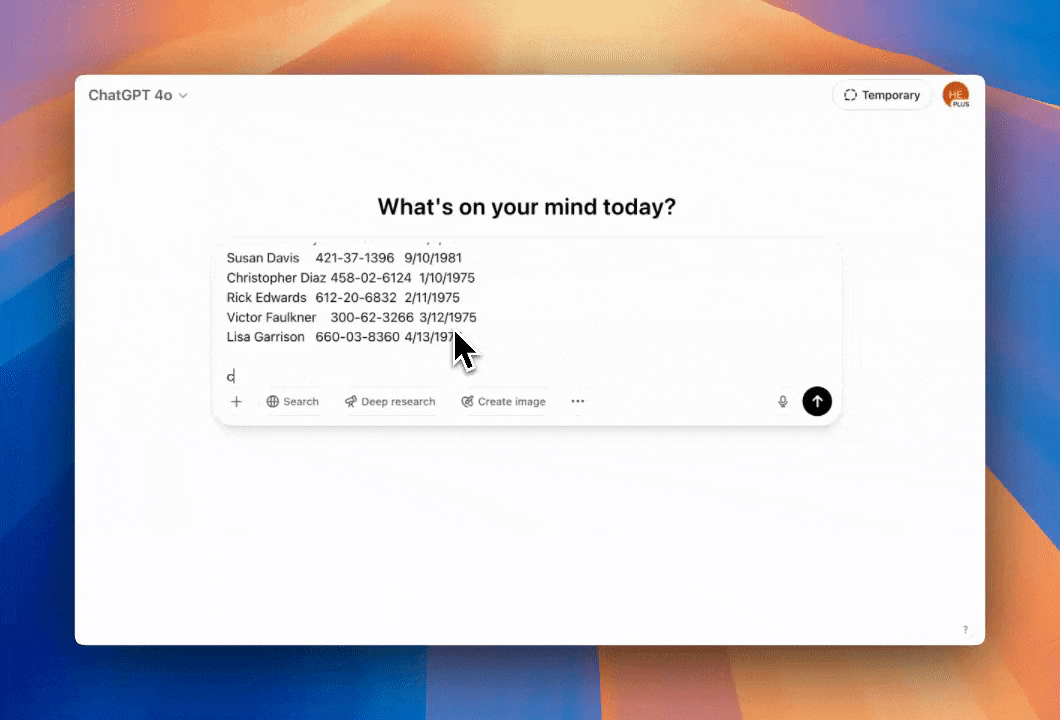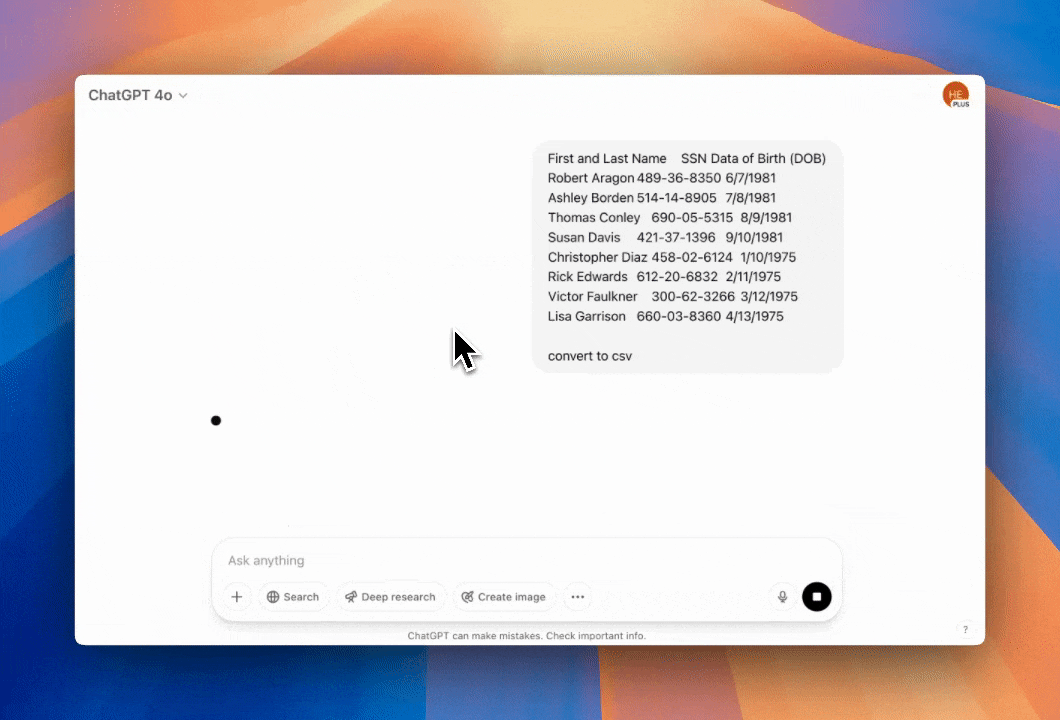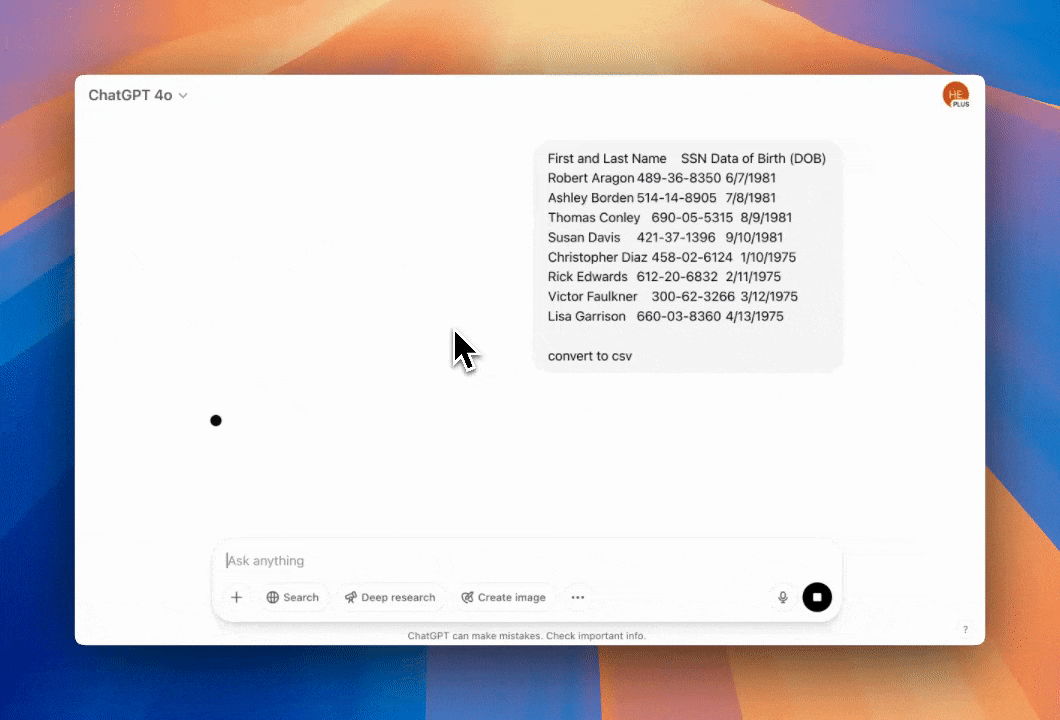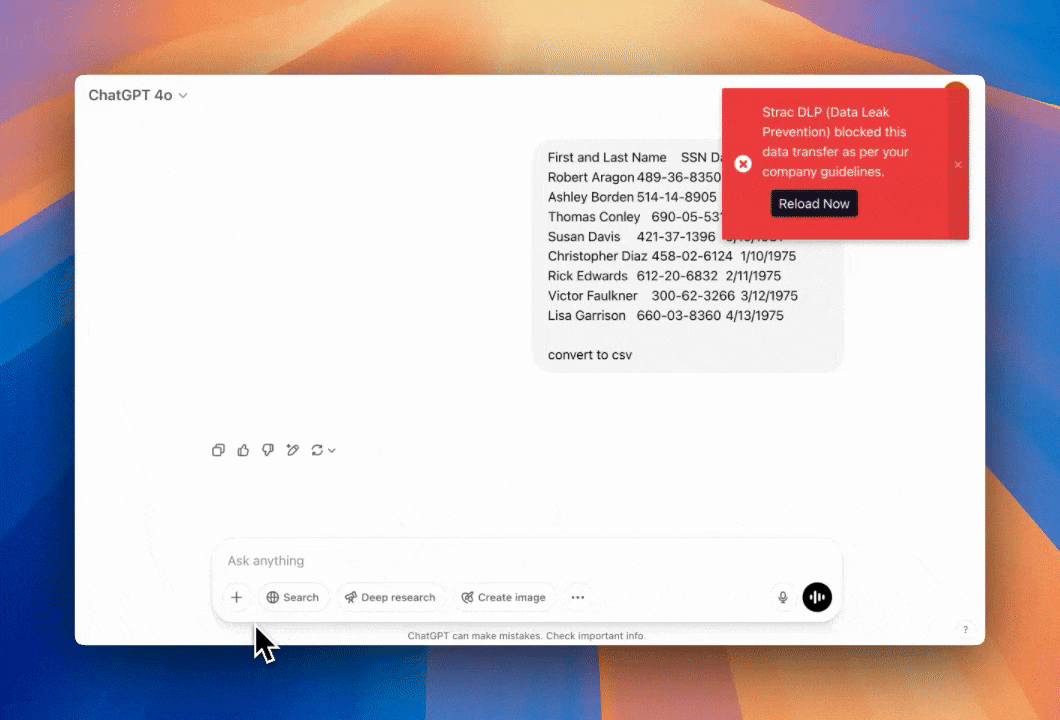

Detect and Mask (Redact) sensitive Salesforce cases. It can also block sensitive PII or PHI in Salesforce cases and all other Salesforce objects.
Strac provides multiple pricing options for teams of all sizes. Please connect with the Strac team.


Symantec, a global leader in security for household gadgets, is also one of the global champions in the DLP software market. The company brands itself in its parent company, Broadcom, and a wide range of products in the segment.
The company successfully enables critical data protection abilities through visibility and control, a unified policy framework, and ensures that security standards meet regulatory compliance benchmarks.
The software offerings, similar to Z-scaler's, are based on the Zero Trust security framework. Here is a list of safety features that Symantec makes possible:
Symantec Data Loss Prevention(DLP) solution enjoys an average rating of 4.5 on G2. Here is what a recent review has to say about the software:


Forcepoint, a true multinational, is known to have a geographical presence in over 150 countries and a healthy client base of 14,000+ companies. The company counts corporations such as IBM, Toyota, and MetLife as clients who leverage advanced machine learning capabilities and a data-first security approach of Forcepoint.

Some of the unique capabilities of Forcepoint that set it apart from its competitors are as follows:
Forcepoint One scores an average of 4 on G2. Here is a recent review of the product.
Digital Guardian comes across one of the leading Data Loss Prevention software vendors in the industry. The platform is driven by a focus on identifying and securing sensitive data, whether structured or unstructured. Apart from that, the company has successfully controlled data movements even at the most granular level.

Some of the key differentiators of the product are as follows:
Digital Guardian scores an average of 4.5 on G2.


Known for its advanced security measures, McAfee is among the data loss prevention companies that safeguard intellectual property and ensure compliance by sensitive data protection - data that may be present at any endpoint.
The McAfee endpoint DLP solutions delivered through low-maintenance appliances (physical or virtual) and McAfee ePolicy Orchestrator (ePO) platform for streamlined deployment, management, updates, and reports.
Some of the noticeable features of the following software are:
The product scores an average of 4.5 on G2.


Check Point Data Loss Prevention (DLP) is known for its pre-emptively protection capabilities from unintentional loss of valuable and sensitive information. The solution integrates with Check Point's Next Generation Firewalls (NGFW). On the other hand, network DLP solutions enables businesses to monitor data movement and empowers employees to work confidently while staying compliant with regulations and data security standards.
Some of the notable differentiators associated with Check Point DLP are as follows:
The product scores an average of 4.6 on G2.


Cisco's Data Loss Prevention for cloud DLP and web are high-performing, comprehensive security solutions for data in motion. Cisco's tool leverages content, context, and destination knowledge to identify emerging threats. This allows enterprises to control who, what, and where a user can send what information, thus, safeguarding accidental or malicious data loss.
Some of the leading capabilities of secure email protection tools are a secure email gateway, cloud DLP, and anti-spam solutions. This tool has strong detection capabilities, especially in email communications, one of the primary channels for data leakage.
G2 rates Cisco's product highest among its peers. Here is how it ranks.


Trend's Micro Integrated DLP solutions clubs Data Loss Prevention with its web security software solution, making it one of the unique solutions on our list. The company promises superior protection with centralized management, cloud storage access control, visibility, and flexible deployment options.
Trend Micro Integrated Data Loss Prevention doesn't have major differentiators. However, here are a few of them.
Trend micro data protection scores an average of 4 on G2. Here is a screenshot of the latest reviews about the product.

GTB Technologies is recognized for its accurate detection capabilities using proprietary detection algorithms. It claims to provide the most accurate detection and control across channels. They are available in all the major operating systems, and their DLP security engine accurately detects structured and unstructured data at the binary level.



Spririon, a leading DLP vendor, is a software solution marketplace segmented based on deployment type, solution type, end-user industry, and geography. The company follows a simple workflow - classification of data, monitoring and controlling, identifying violation of policies, enforcing remediation, and creating reports.
Some of the key factors that distinguish Spirion by other vendors are as follows:
Spirion scores an average of 4.5 on G2.


Safetica offers robust DLP software designed to protect sensitive data against human error and malicious intent. It focuses on proactive endpoint protection with continuous scanning for threats.
Users praise its effectiveness in preventing data leaks and ease of use.

Generally considered higher than competitors but justified by its robust features.

Code42 specializes in preventing data exfiltration with a focus on insider threats. Its cloud-native solution is designed for rapid detection without hindering user collaboration.
Highly rated for its visibility and recovery capabilities.

Competitive pricing model tailored for various organizational sizes.

Fortra Digital Guardian provides enterprise-wide data protection through comprehensive visibility into sensitive assets. It is known for its advanced analytics capabilities.
Users appreciate its flexibility in policy customization and effective monitoring capabilities.

Initial setup costs can be high but are deemed reasonable given the features offered.

Trellix DLP combines advanced content inspection techniques with a comprehensive approach to monitoring sensitive data across various channels.
Noted for its extensive feature set that enhances compliance efforts.

Pricing varies based on deployment options and organizational needs.

Proofpoint offers a human-centric approach to DLP, focusing on user behavior to prevent data loss across multiple channels including email and cloud applications.
Positive feedback on its unified console for incident management.

Scalable pricing based on user count and feature sets.

Endpoint Protector focuses on endpoint security with flexible deployment options tailored for various organizational needs.
Users highlight its effectiveness in preventing unauthorized access to sensitive data.

Offers diverse pricing tiers based on the number of endpoints secured.

Teramind provides an all-in-one insider threat detection, DLP software, and employee monitoring solution. It offers advanced analytics combined with productivity features aimed at enhancing both security and workforce efficiency.
Users appreciate its comprehensive feature set that enhances both security measures and employee productivity tracking.

Competitive pricing model based on deployment type (cloud or on-premises) and organizational size.
Choosing the best DLP solutions can be challenging, given the number of DLP vendors in the market.
This table provides a quick reference to analyze the key features and reviews of each DLP software solution along with their pricing details where available.
DLP tools are security technologies designed to stop sensitive data from leaking, whether it’s through email, cloud apps, endpoints, or careless employees. They monitor and control data in motion, at rest, and in use, ensuring compliance and reducing the risk of breaches.
Spicy Take: Most companies don’t think they need DLP tools—until they experience a breach. One data leak can cost millions in fines and lost trust. Why wait for a crisis to take action?
DLP tools combine content inspection, contextual analysis, rule-based policies, and increasingly machine learning to detect sensitive data. They can block risky actions, alert admins, redact information, or even encrypt it before it leaves your environment.
Spicy Take: Legacy DLP tools only “detect” and flood you with alerts. Modern tools like Strac go further—automating remediation so leaks are stopped, not just noticed.
Without DLP, organizations face data breaches, insider threats, and compliance failures. As cloud apps, remote work, and AI grow, traditional perimeter defenses are no longer enough. DLP tools give visibility and control where your sensitive data actually lives.
Spicy Take: Saying “our data is already protected” is the biggest lie in security. Can you prove your sensitive data isn’t leaving through Slack, Gmail, or Google Drive? If not, you need DLP tools.
DLP tools help organizations prevent fines, lawsuits, and brand damage. They enforce policies automatically, reduce human error, and provide real-time protection against both malicious and accidental leaks.
Spicy Take: CISOs who ignore DLP tools are betting their jobs. The blind spots today—SaaS apps, cloud storage, and employee endpoints—are exactly where modern tools like Strac shine.
Endpoint DLP tools are fading—struggling with BYOD, remote work, and SaaS-heavy environments. Cloud-native DLP tools, on the other hand, scale instantly, offer better visibility, and require no heavy installs.
Spicy Take: Endpoint DLP is like locking every single door in a skyscraper by hand. Cloud-based DLP tools are like smart, automated access control—faster, easier, and more effective.
While many adopt DLP for compliance (GDPR, HIPAA, PCI DSS), they quickly realize it’s equally critical for preventing real-world breaches. DLP tools help stop insider threats, careless mistakes, and external attacks.
Spicy Take: Compliance-only DLP is like wearing a seatbelt but leaving the doors wide open. The best DLP tools protect against both regulators and attackers.
The most common mistake? Treating DLP as a “set it and forget it” project. Policies must evolve with your data, business, and risk profile.
Spicy Take: If your DLP tools haven’t been updated in two years, you’re already behind. Data loss prevention isn’t a one-time project—it’s a living security strategy.
Yes. Rule-based DLP tools often create false positives that frustrate employees. AI-powered tools adapt in real-time to new patterns and threats, reducing noise while improving accuracy.
Spicy Take: If your DLP tool is still running regex policies from 2010, you’re toast. AI-driven tools like Strac are the only way to stay ahead of evolving threats.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

