AI DLP Explained: How Data Really Leaks in Generative AI
Learn how AI DLP prevents sensitive data leaks in GenAI, copilots, and LLM workflows using real-time, context-aware controls.
Generative AI is already inside everyday enterprise workflows. ChatGPT, copilots, and internal models now sit directly in systems that handle customer data, source code, financial records, and internal context. Once data enters an AI workflow, traditional DLP loses visibility and control.
AI breaks the assumptions legacy DLP was built on:
If your DLP only understands files, emails, or endpoints, it cannot secure AI usage.
AI DLP exists because AI is a first-class data security surface, not an edge case.
AI DLP is best understood as data loss prevention purpose-built for LLM-driven workflows, not a simple extension of legacy controls. At its core, AI DLP governs how data moves into and out of generative AI systems by inspecting prompts, chat messages, uploads, and model-generated responses in real time. Unlike traditional approaches that focus on files or network traffic, what AI DLP is really about is controlling language, context, and intent; the fundamental units of data movement in large language models.
This distinction is critical. In LLM DLP and generative AI DLP, sensitive information does not only exist as static records or attachments. It appears inside free-form text, conversational context, embeddings, and AI outputs that may summarize or transform the original data. Effective prompt DLP must therefore analyze both structured and unstructured data inline and apply enforcement before information ever reaches the model or leaves it.

The definition of AI DLP must be operational, not theoretical. If a solution cannot see prompts in real time and cannot enforce controls before data is submitted to or returned from an LLM, it is not AI DLP in practice; it is simply legacy DLP watching from the sidelines.
Traditional DLP was built for fixed boundaries; email, files, endpoints, known network paths. AI workflows do not use those boundaries.
Most AI usage happens in the browser. Users copy text, paste context, upload snippets, and interact with models using free-form language. None of this reliably passes through legacy DLP control points.
This is why traditional DLP vs AI DLP is no longer theoretical. It fails in production.
Where traditional DLP breaks:
Spicy take; when DLP gets noisy, enterprises don’t tune it. They bypass it.
AI DLP is no longer forward-looking. Employees use AI every day for legitimate work; writing emails, debugging code, summarizing tickets, analyzing customer data. Most AI data leakage is accidental and happens fast.
Where risk shows up in practice:
If data protection cannot operate inline with AI interactions, it cannot reduce AI risk.
That is why AI DLP exists.
Anything else is visibility without control.
AI DLP only works if it reflects how data actually leaks in production GenAI workflows. Most organizations underestimate exposure because they think in terms of prompts alone. In reality, AI creates multiple parallel data leak paths.
If you cannot map where leakage happens, you cannot enforce controls where it matters. Discovery without inline enforcement does not reduce risk.
Where AI data leakage happens in practice:
Spicy take; most AI DLP failures happen after “prompt coverage” is declared complete.
AI DLP must enforce controls across inputs, uploads, integrations, and outputs in one system.
If remediation does not happen inline, AI DLP becomes observation, not protection.
Regulators do not distinguish between data leaked by email or by AI prompt. If sensitive data enters a model without controls, it is a compliance failure.
What auditors expect to see:
Shadow AI makes this unavoidable. Teams adopt new AI tools faster than governance can approve them. AI DLP focuses on controlling data inside AI tools, not pretending AI can be blocked entirely.
AI DLP implementation works best when it is treated as a phased rollout plan, not a one-time policy project. The fastest way to fail with AI DLP is to start with aggressive blocking before you understand where sensitive data is actually flowing across ChatGPT, GenAI tools, and Gemini usage. The goal is to move from policy on paper to enforcement in the prompt path, with measurable coverage, reduced noise, and audit-ready logs that prove governance is real.
Done this way, AI DLP is implementable in phases and improves over time. You can start with visibility and warnings, then progress to targeted enforcement without derailing productivity.
AI DLP for ChatGPT must be grounded in how people actually use the tool day to day. Most risk does not come from exotic API integrations; it comes from simple copy and paste, iterative prompt refinement, and document uploads for summarization, debugging, or analysis. Effective AI DLP focuses on these high-frequency workflows and enforces controls directly in the prompt path, while producing interaction-level audits that compliance teams can rely on and security teams can tune over time.
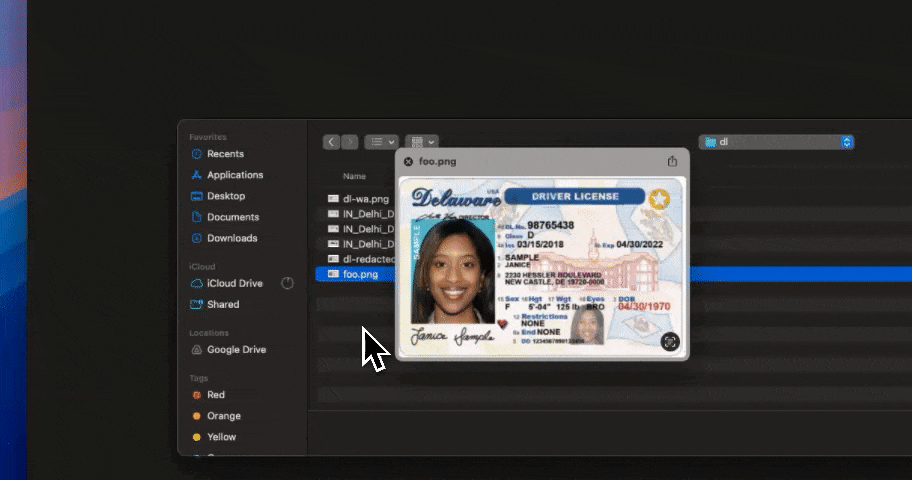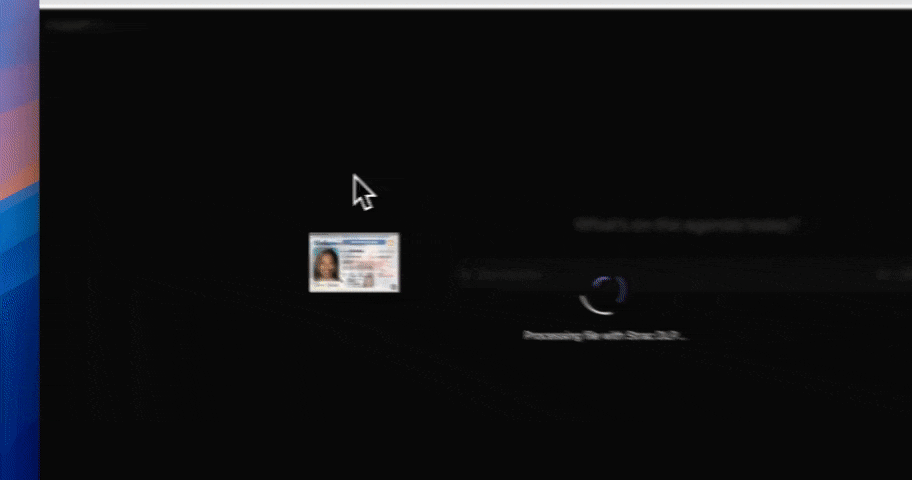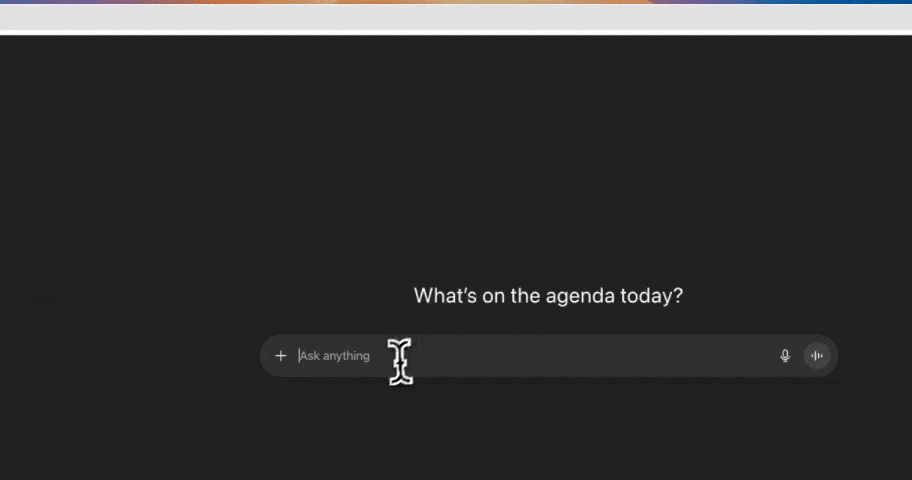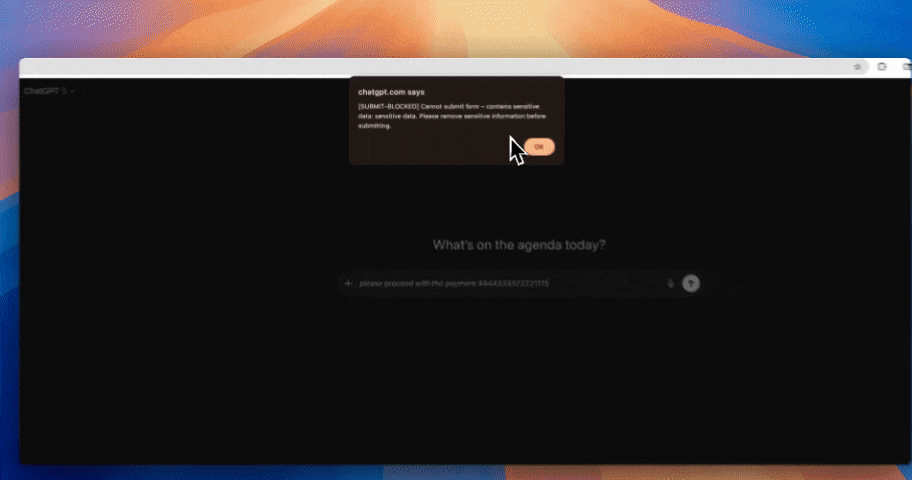
The foundation of AI DLP for ChatGPT is real-time prompt inspection. Every prompt and pasted text block should be analyzed for sensitive content before submission, including PII, PHI, PCI, credentials, secrets, source code, and internal documents. This detection must work on unstructured language, not just patterns, because prompts often mix natural language with data fragments. If prompt content cannot be inspected inline, ai dlp coverage collapses at the most critical control point.
Detection alone does not stop leakage. AI DLP must support inline remediation actions such as block, warn, or redact before sensitive data reaches ChatGPT. At the same time, every decision should be logged; who submitted what, which policy triggered, what action was taken, and when. These interaction audits are essential for investigations, compliance reviews, and proving that ai data loss prevention controls are enforced consistently.
AI DLP policies for ChatGPT should combine data categories with behavior patterns. Common examples include blocking prompts that contain raw PII or secrets, allowing masked email addresses, warning users when internal documents are pasted, and redacting sensitive fields while letting the rest of the prompt through. This flexibility is what keeps controls effective without breaking productivity.
The success metric for AI DLP in ChatGPT is simple and measurable. Sensitive data should be blocked or redacted before it ever reaches ChatGPT, not detected after the fact.
At the control layer, AI DLP for Gemini looks familiar. The same principles apply; inspect prompts, govern uploads, enforce inline, and log everything. What changes is how users share data. Gemini usage is deeply tied to Google ecosystem workflows, including Sheets, CSV exports, screenshots, and documents pulled from Drive. This means AI DLP must account for both conversational prompts and rich file-based inputs without relying solely on storage-level scanning.

Gemini DLP must inspect prompt text and uploaded files in real time. Users frequently paste tables from Sheets, upload CSVs for analysis, or attach screenshots and PDFs. AI DLP needs to classify structured and unstructured content inline and apply policy before the data is processed by the model.
As with ChatGPT, Gemini controls should start with audit and warn modes to tune policies, then progress to blocking or redaction for high-risk data. These remediation modes must be configurable by data type, user group, and use case to avoid unnecessary friction.
Gemini interactions must generate the same level of evidence as any other regulated workflow. AI DLP should produce detailed logs and integrate with SIEM or SOAR systems so security teams can correlate AI events with broader incident response and compliance reporting.
The key differentiator to understand is this. Workspace-only DLP that scans files at rest is not enough for Gemini. Gemini requires prompt-path controls that operate inline, at the browser or interaction layer, because that is where sensitive data actually moves.
Evaluating AI DLP is not about feature depth; it is about whether the tool survives real daily AI usage. If it cannot enforce controls inline, stay accurate at scale, and fit into existing security operations, it will be ignored or turned off.
What an AI DLP solution must prove:
Spicy take; if an AI DLP tool can’t enforce inline on day one, it won’t be enforcing six months later either.
AI DLP buyers are no longer looking for isolated controls bolted onto individual chatbots. They need a single control plane that governs how sensitive data moves across ChatGPT, Gemini, and other GenAI tools, without fragmenting policy management or operational visibility. Just as importantly, AI DLP must move beyond alerting. In production environments, teams need real-time enforcement and remediation that stop leaks as they happen, while producing evidence that stands up in audits. This is where a unified, enforcement-first approach becomes essential.
Strac approaches AI DLP as an end-to-end control layer that operates inline across GenAI workflows, rather than as a collection of point solutions. The focus is on consistent policy enforcement, real-time inspection, and audit-ready outcomes across tools and teams.
The outcome is clear and measurable. AI DLP with Strac enables teams to adopt AI confidently, stops regulated data from leaking in real time, and produces the audit evidence security and compliance programs require; without slowing down how people actually work.
AI DLP is quickly becoming the minimum viable control set for any enterprise adopting GenAI at scale. Prompts, uploads, and AI-generated outputs are no longer edge cases; they are now mainstream data exfiltration paths woven into everyday work. Treating AI risk as an extension of legacy DLP leaves organizations exposed precisely where sensitive data moves fastest and with the least friction.
The winning approach to AI DLP is not policy-only. It is visibility plus inline enforcement plus auditability. Security teams must be able to see how AI tools are used, enforce controls in real time before data reaches ChatGPT or Gemini, and produce clear evidence that policies were applied consistently. Without all three, AI governance collapses under real-world pressure.
The test is simple. If an AI DLP solution cannot inspect prompts, uploads, and outputs and remediate risk before sensitive data is submitted or returned, it will not meaningfully reduce exposure; and it will not hold up in compliance or audit reviews.
AI DLP, or AI data loss prevention, is a set of controls designed to prevent sensitive data from being exposed through generative AI systems. It governs how data enters and exits AI workflows by inspecting prompts, contextual memory, and model outputs in real time. Unlike legacy approaches, AI DLP is built for unstructured, conversational data and enforces protection before information is consumed by or emitted from AI models.
The difference between traditional DLP vs AI DLP comes down to context, timing, and data structure. Traditional DLP focuses on static objects such as files, emails, and databases, using deterministic rules and regex patterns. AI DLP operates inline within AI interactions, evaluates semantic meaning and intent, and enforces controls in real time. This makes it effective in environments where data is dynamic, unstructured, and continuously transformed.
Yes, AI DLP can prevent data leaks in tools like ChatGPT and enterprise copilots when it is integrated inline with those workflows. Effective AI DLP can:
This approach prevents sensitive information from being exposed rather than simply detecting it after the fact.
AI DLP supports GDPR and HIPAA compliance by enforcing controls on how regulated data is handled inside AI workflows. While regulations do not mandate specific AI DLP tools, they require organizations to prevent unauthorized disclosure of personal and health data. AI DLP provides the visibility, enforcement, remediation, and audit evidence needed to demonstrate that sensitive data is protected when AI systems are used.
Deployment time depends on architecture and integration depth, but modern AI DLP platforms are designed for rapid rollout. Many SaaS-native AI DLP solutions can be deployed in days rather than months by integrating directly with existing SaaS and GenAI tools. Faster deployment is critical, as AI adoption often outpaces traditional security implementation timelines.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

