TL;DR
- AI assistants like Google Gemini can unintentionally leak sensitive data such as PII, PHI, or PCI during prompts and file uploads.
- Strac Gemini DLP automatically scans and classifies text, images, and files shared with Gemini.
- Prevents data exfiltration in real time by redacting or blocking sensitive inputs (e.g., SSN, credit card, medical data).
- Supports alerting and audit logs for compliance teams (SOC 2, HIPAA, PCI DSS, GDPR).
- Deployable via browser extension or API, ensuring organization-wide AI safety.
✨ Gemini DLP in Action
Why Gemini DLP Is Critical in the Age of AI
AI assistants like Google Gemini (formerly Bard) have become integral to enterprise workflows — helping with documentation, code, and data analysis. But these same AI tools can become data exfiltration points if employees accidentally share confidential data.
Example scenarios:
- A support engineer pastes a customer’s credit card number into Gemini to debug a billing issue.
- A healthcare analyst uploads a CSV of patient records to summarize symptoms.
- A marketing team member drops a Google Sheet with customer emails to refine segmentation.
In each case, data is now out of your control — copied into a third-party AI system, possibly retained or logged for model training.
Gemini DLP ensures these incidents never occur.
How Strac’s Gemini DLP Works
Strac’s Browser DLP and API-based inspection engine integrates directly into user workflows. It performs three core functions:
1. Real-Time Data Detection in Gemini DLP
- Inspects every prompt, chat message, or file upload to Gemini before submission.
- Uses LLM + Regex + Contextual keyword analysis to detect sensitive data such as:
- PII (name, SSN, address, email)
- PHI (diagnosis, MRN)
- PCI (credit card, bank account)
- Confidential data (API keys, source code, internal documents)
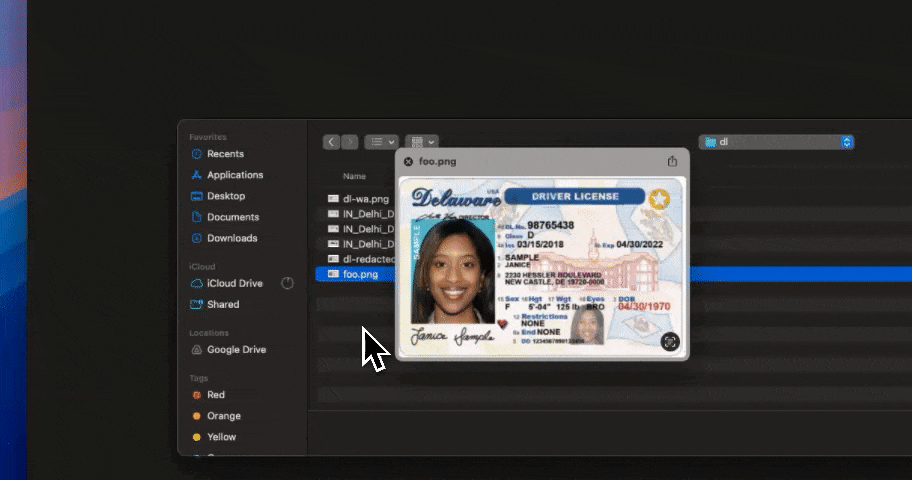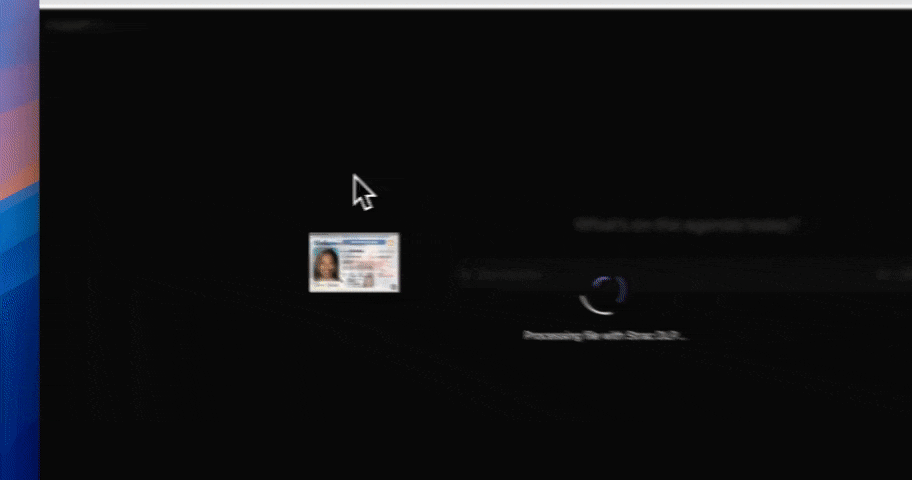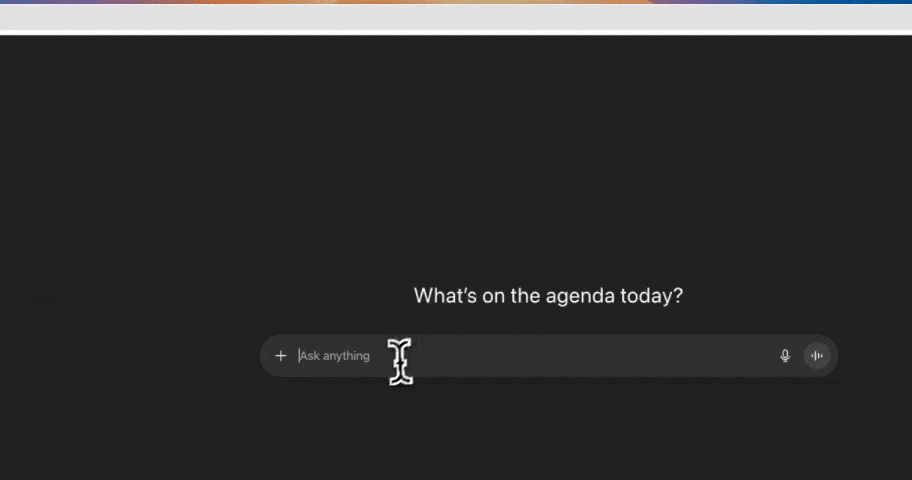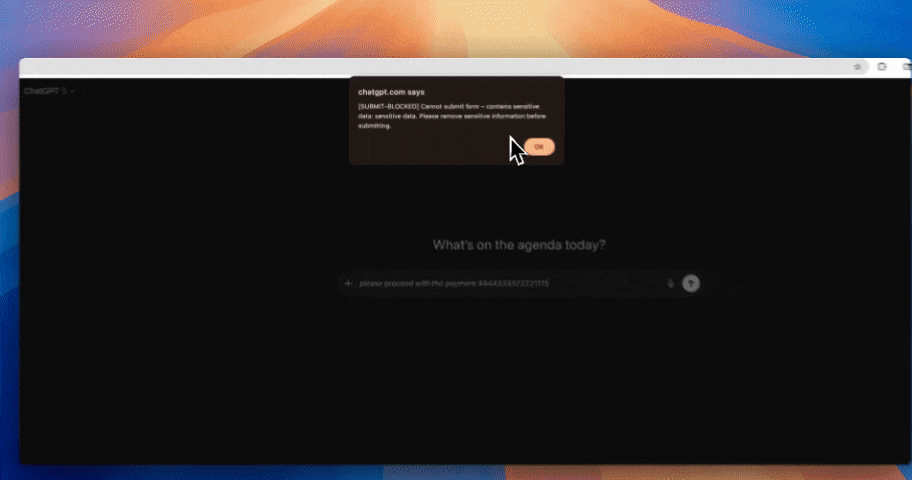
2. Remediation: Audit, Block or Warn in Gemini DLP
Once sensitive data is detected, Strac enforces customizable remediation:
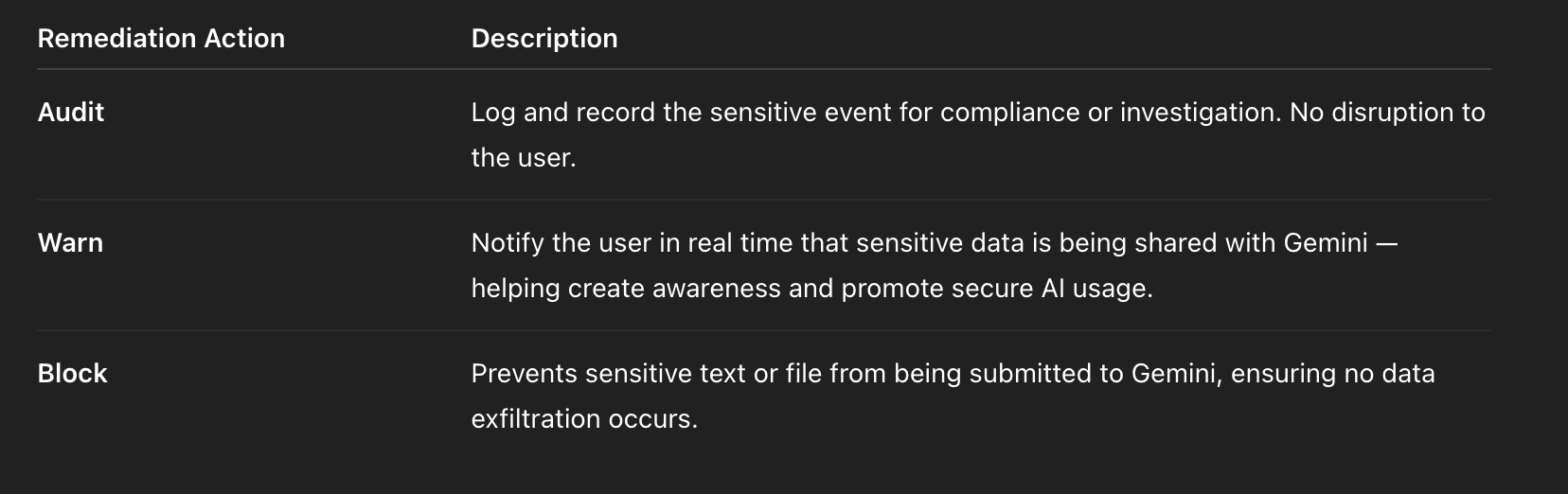
Administrators can configure behavior per data type and app policy (e.g., block credit cards but allow masked emails).
Gemini DLP Architecture Overview
Strac Gemini DLP operates agentlessly through a browser extension or lightweight proxy:
- Capture layer hooks into Gemini web traffic.
- Classification engine inspects payload using Strac’s ML + policy engine.
- Remediation engine enforces actions and sends real-time alerts.
- SIEM/SOAR Integration pushes events to tools like Splunk, Sumo Logic, or Microsoft Sentinel.
✨ Example: Real-Time Alert to Slack

Instant alerts when Gemini prompts contain sensitive information.
Gemini DLP Compliance and Audit Benefits
Gemini DLP helps organizations demonstrate compliance with frameworks such as:
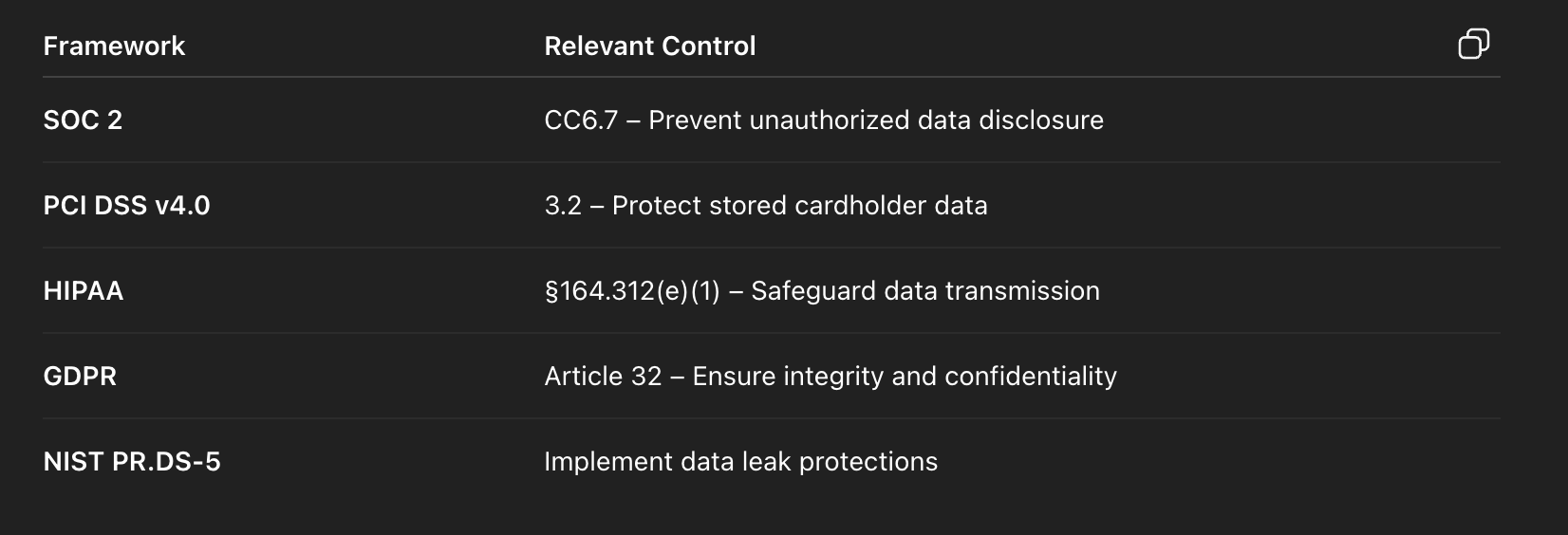
Every event is logged with:
- User identity and timestamp
- Policy triggered and remediation performed
- Optional screenshots for audit evidence
✨ Unified DLP Across AI Platforms

Strac protects Gemini, ChatGPT, Copilot, and all major SaaS apps through one unified DLP platform.
Spicy FAQs
What types of data can Gemini DLP detect?
Over 400+ data elements across PII, PHI, PCI, and confidential categories — including SSNs, credit cards, passwords, patient IDs, and secrets. Detection combines regex + context-aware ML for high accuracy.
Can Strac prevent sensitive screenshots or PDFs from being uploaded?
Yes. Strac uses OCR-based visual scanning to extract and analyze text from images, screenshots, and PDFs before upload — blocking or redacting sensitive visual data.
How does Gemini DLP differ from Google Workspace DLP or CASB tools?
Google’s DLP applies to Workspace (Drive, Gmail) via APIs. Strac’s Gemini DLP works at the browser layer, covering Gemini, ChatGPT, Copilot, Claude, and beyond — preventing leaks before they reach the AI system.
What happens when Gemini receives masked data?
Masked data (e.g., “4111-XXXX-XXXX-1234”) lets employees work productively without exposing the full value. Gemini still processes the context, but sensitive details remain protected.
Does Strac store user data?
No. Strac can be deployed in your environment, or data can be tokenized and redacted inline before leaving the browser. Nothing sensitive leaves your network.











.webp)














.webp)




.avif)


