TL;DR:
- Strac's Gen AI DLP (Data Loss Prevention) solutions help organizations safely manage generative AI technologies like ChatGPT and Gemini.
- Generative AI tools pose risks such as data breaches, compliance issues, and shadow IT, which Strac's solutions address.
- Strac enables centralized policy enforcement, access management, and protection for data in generative AI platforms.
- The solutions also help mitigate shadow IT risks, secure sensitive data, and provide visibility and control over AI usage.
- With features like sensitive data discovery, data leakage prevention, and unified policy management, Strac ensures safe integration of generative AI tools.
As generative AI technologies like ChatGPT and Gemini gain popularity, they bring new risks to sensitive data. Organizations must navigate these challenges to harness the full potential of AI without compromising data security. Strac's industry-leading Data Loss Prevention (DLP) solutions provide the control and visibility necessary to manage generative AI chatbots safely and effectively.
Why You Need Generative AI DLP (Data Loss Prevention)
Generative AI tools offer immense benefits, from rapid financial analysis to automated code generation. However, they also present unique risks:
- Data Breaches and Leaks: Generative AI applications learn from the data input they receive, potentially exposing sensitive information if not properly managed.
- Compliance Risks: Regulatory frameworks like GDPR, HIPAA, and CCPA require stringent data protection measures. Using AI without adequate controls can lead to non-compliance.
- Shadow IT: Employees may use unauthorized AI tools, creating blind spots in your data security strategy.
- Intellectual Property (IP) Risks: Sensitive business information and intellectual property can be inadvertently shared with AI applications, risking leaks to competitors.
Strac’s generative AI DLP solutions address these concerns, enabling organizations to enjoy the benefits of AI while safeguarding their data.
How to Implement DLP for Generative AI (Step-by-Step)
Implementing Data Loss Prevention for Generative AI requires visibility into how sensitive data moves through prompts, responses, and integrations with SaaS tools. Because AI systems can unintentionally expose PII, PHI, PCI, secrets, and internal IP, a structured rollout of DLP ensures guardrails are in place before teams adopt AI broadly. With Strac’s agentless DSPM + DLP approach, organizations can implement LLM protection without slowing down innovation.
Step 1: Discover sensitive data flowing into AI prompts
Start by scanning prompts, messages, attachments, and workflow inputs where users interact with tools like ChatGPT, Bard, and Copilot. Strac automatically discovers PII, PHI, PCI, secrets, and company-specific sensitive data patterns.
Step 2: Classify and label data across AI workflows
Apply classification policies that identify which data types require redaction, masking, or blocking. This sets the baseline for automatic remediation.
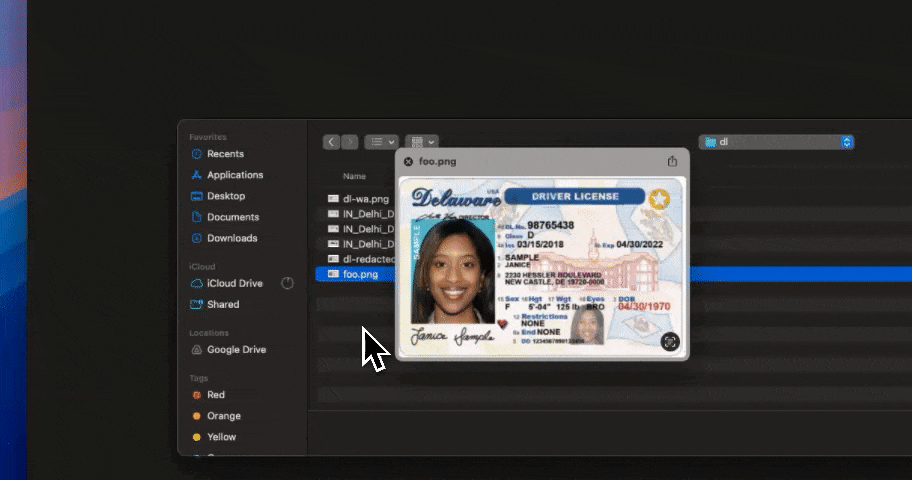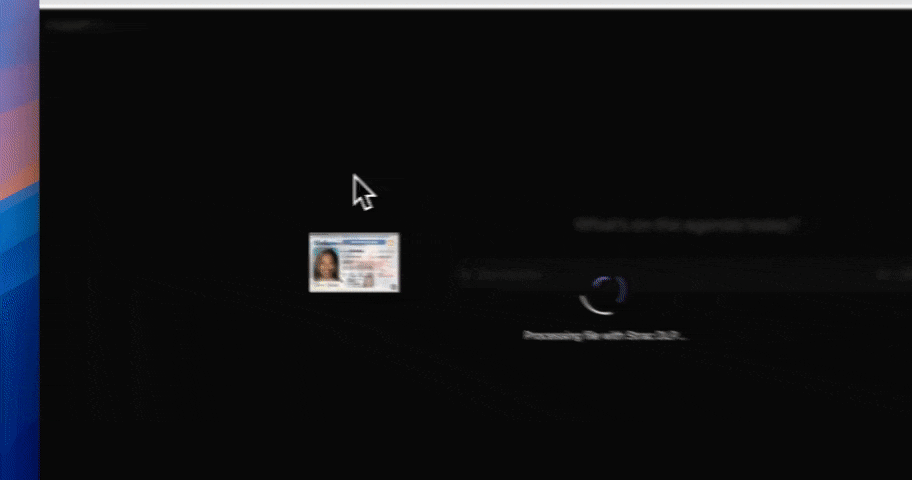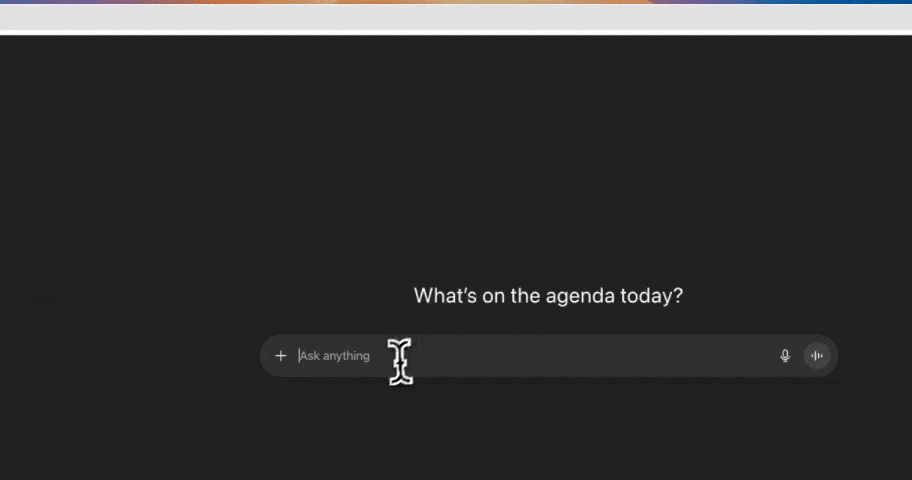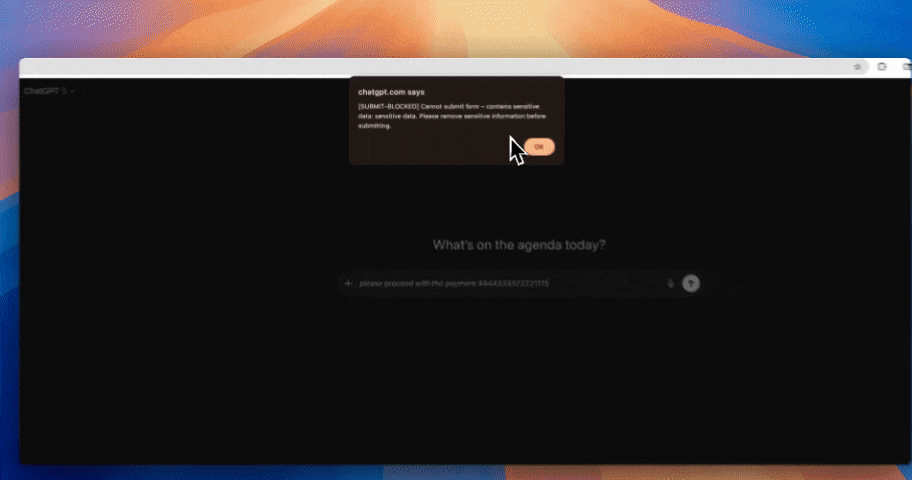
Step 3: Enforce real-time redaction before data leaves your environment
Strac can redact sensitive data inline before it reaches an external LLM. This prevents outbound leakage without relying on users to manually sanitize prompts.
Step 4: Inspect AI-generated responses for sensitive content
Models may hallucinate or echo sensitive information. Strac scans responses, attachments, summaries, and generated artifacts to ensure no PII/PHI/IP is returned to unintended channels.
Step 5: Apply least-privilege and governance controls
Restrict which teams and tools can send or receive sensitive information via AI integrations. Automatically block unauthorized flows and maintain audit logs for compliance.
Step 6: Remediate at scale
Use automated workflows for blocking, deleting, redacting, and notifying when sensitive data is detected. Strac remediates instantly across chat, email, support tools, and AI interfaces.
Step 7: Monitor, alert, and continuously improve
Real-time dashboards reveal AI data risks; alerts help security teams respond quickly. Over time, refine policies to reduce noise and increase accuracy.
Implementing Generative AI DLP becomes seamless when your organization combines discovery, classification, redaction, and automated remediation into one unified workflow.
✨How Strac can help with Managing Risks in Generative AI DLP
Centralized Policy Enforcement for Generative AI DLP
With Strac, organizations can centrally manage policies to control access to generative AI applications. This centralized approach simplifies policy management, ensuring consistent enforcement across the organization. Key features include:
- User and Group Management: Tailor access based on user roles, departments, and specific needs.
- Application Control: Limit access to approved AI tools and redirect users to sanctioned applications.
- Real-time Policy Updates: Implement policy changes like Alert, Warn, Block, Redact, Pseudonymize instantly across all devices and environments.
Strac Generative AI DLP Protects Data on ChatGPT, Google Gemini, Anthropic Claude, Microsoft Copilot
Strac’s DLP solutions offer comprehensive protection for data in ChatGPT, Gemini, and other generative AI platforms. Key capabilities include:
- Access Management: Control who can use generative AI within your organization.
- File Upload Prevention: Block the upload of sensitive files to AI applications.
- Clipboard Protection: Prevent pasting sensitive information into AI chatbots.
Exploring the Next Generation of Shadow IT Risk in Generative AI DLP
Generative AI tools can enhance productivity but also pose significant risks if not managed correctly. These applications can inadvertently expose sensitive information through data inputs. Strac’s solutions help mitigate these risks by:
- Controlling Usage: Determine who can access generative AI tools.
- Blocking Sensitive Data: Prevent the transfer of sensitive data to AI applications.
- Monitoring and Reporting: Provide detailed insights into AI usage and data interactions.
Best Practices for DLP When Using Generative AI
DLP for Generative AI requires a different approach than traditional endpoint or SaaS DLP; AI systems are dynamic, unpredictable, and often integrated into employee workflows. The goal is to empower teams to use AI safely while ensuring sensitive data never leaves controlled environments. These best practices help organizations maintain compliance and prevent accidental exposure.
1. Assume every AI prompt is a potential data leak
Employees frequently copy/paste customer data, support transcripts, source code, or internal documentation into AI assistants. Treat prompts as high-risk and scan them automatically.
2. Redact before the LLM, not after
Pre-prompt redaction ensures sensitive data never reaches external AI systems. Strac performs inline masking so users can still get value from AI without sharing protected information.
3. Apply policies consistently across all AI channels
Whether your teams use ChatGPT, Copilot, Bard, Slack AI, or internal LLMs, use a single set of rules for detecting and remediating sensitive data. Fragmented policies lead to blind spots.
4. Monitor both prompts and responses
Models may regenerate sensitive data through summarization, code generation, or hallucination. Inspect both outbound and inbound flows to prevent downstream exposure in SaaS tools.
5. Use agentless DLP to reduce adoption friction
Agent-based tools slow down deployment and rarely support AI interfaces. Strac’s agentless architecture ensures fast onboarding across SaaS, browsers, and AI integrations.
6. Establish audit trails for compliance
Track when sensitive data is detected, redacted, or blocked. Logs help demonstrate adherence to GDPR, PCI DSS, HIPAA, GLBA, and SOC 2 requirements.
7. Train teams on AI-safe data handling
Even with strong DLP controls, user awareness reduces unnecessary risks. Teach employees to avoid pasting raw customer data into prompts unless required for workflows protected by DLP.
When companies combine automated monitoring with real-time redaction, unified DLP policies, and strong governance, Generative AI becomes a safe and compliant tool—not a new attack surface.
Securing Generative AI Data with Strac Data Security
Strac’s comprehensive data security measures ensure that your organization can safely integrate generative AI tools. Our solutions include:
- Sensitive Data Discovery and Classification: Identify and classify sensitive data across your organization using 1,700+ out-of-the-box policies and classifiers.
- Data Leakage Prevention: Stop data loss through generative AI by blocking unauthorized actions, such as copying and pasting sensitive information.
- Unified Policy Management: Manage data loss prevention policies from a single, centralized interface.
✨Visibility and Control with Strac Generative AI DLP
Strac provides unparalleled visibility and control over AI usage within your organization. Our solutions allow you to:
- Limit Access: Control access to AI applications based on users, groups, and other criteria.
- Redirect Usage: Guide users towards approved AI applications and away from unapproved ones.
- Manage AI SaaS Apps: Securely manage the use of thousands of AI SaaS applications.
- Cover Emerging Tools: Ensure coverage of new and emerging AI tools through blanket policies based on AI categories.

📽️Strac Generative AI DLP Demo
Sensitive Data Types for Generative AI DLP
Checkout all the sensitive data elements and file formats supported by Strac: https://www.strac.io/blog/strac-catalog-of-sensitive-data-elements











.webp)














.webp)




.avif)


