- Product
.webp) SaaS DLPPIIPHIIdentify, Categorize and Redact PII, financial information,PHI, IP’s from SaaS applications.
SaaS DLPPIIPHIIdentify, Categorize and Redact PII, financial information,PHI, IP’s from SaaS applications..webp) Endpoint DLPPIIPHIEnforce content classification and contextual analysis to identify sensitive information at endpoints
Endpoint DLPPIIPHIEnforce content classification and contextual analysis to identify sensitive information at endpoints.webp) Enterprise DLPPIIPHIEnhance your enterprise data security layer for endpoints ,SaaS and Cloud with one DLP integration.
Enterprise DLPPIIPHIEnhance your enterprise data security layer for endpoints ,SaaS and Cloud with one DLP integration. Email SecurityPIIPHIScan and redact PII PHI and confidential data in Email flows
Email SecurityPIIPHIScan and redact PII PHI and confidential data in Email flows PII ScannerPIIPHIAccurate sensitive data scanning and classification across all Endpoints ,SaaS and Cloud
PII ScannerPIIPHIAccurate sensitive data scanning and classification across all Endpoints ,SaaS and Cloud
.webp) Mac DLPPIIPHISeamlessly integrate data loss prevention with MacOS
Mac DLPPIIPHISeamlessly integrate data loss prevention with MacOS.webp) Data DiscoveryPIIPHIAccurate sensitive data inspection and classification in Real-Time to Safeguard Information Tailored to Specific Needs
Data DiscoveryPIIPHIAccurate sensitive data inspection and classification in Real-Time to Safeguard Information Tailored to Specific Needs.webp) ChatGPT DLPPIIPHIPrevent PII ,PHI and sensitive files shared to AI models to safeguard customer info
ChatGPT DLPPIIPHIPrevent PII ,PHI and sensitive files shared to AI models to safeguard customer info Linux DLPPIIPHIMonitor ,Detect and remediate sensitive data in Linux systems.
Linux DLPPIIPHIMonitor ,Detect and remediate sensitive data in Linux systems.
ProductCompliances.webp) HIPAAPIIIdentify, Categorize and Redact PII, financial information,PHI, IP’s from SaaS applications.
HIPAAPIIIdentify, Categorize and Redact PII, financial information,PHI, IP’s from SaaS applications..webp) SOC2PIIPHIEnforce content classification and contextual analysis to identify sensitive information at endpoints
SOC2PIIPHIEnforce content classification and contextual analysis to identify sensitive information at endpoints ISO 27001PIIPHIEnhance your enterprise data security layer for endpoints ,SaaS and Cloud with one DLP integration.
ISO 27001PIIPHIEnhance your enterprise data security layer for endpoints ,SaaS and Cloud with one DLP integration..webp) CCPAPIIPHIScan and redact PII PHI and confidential data in Email flows
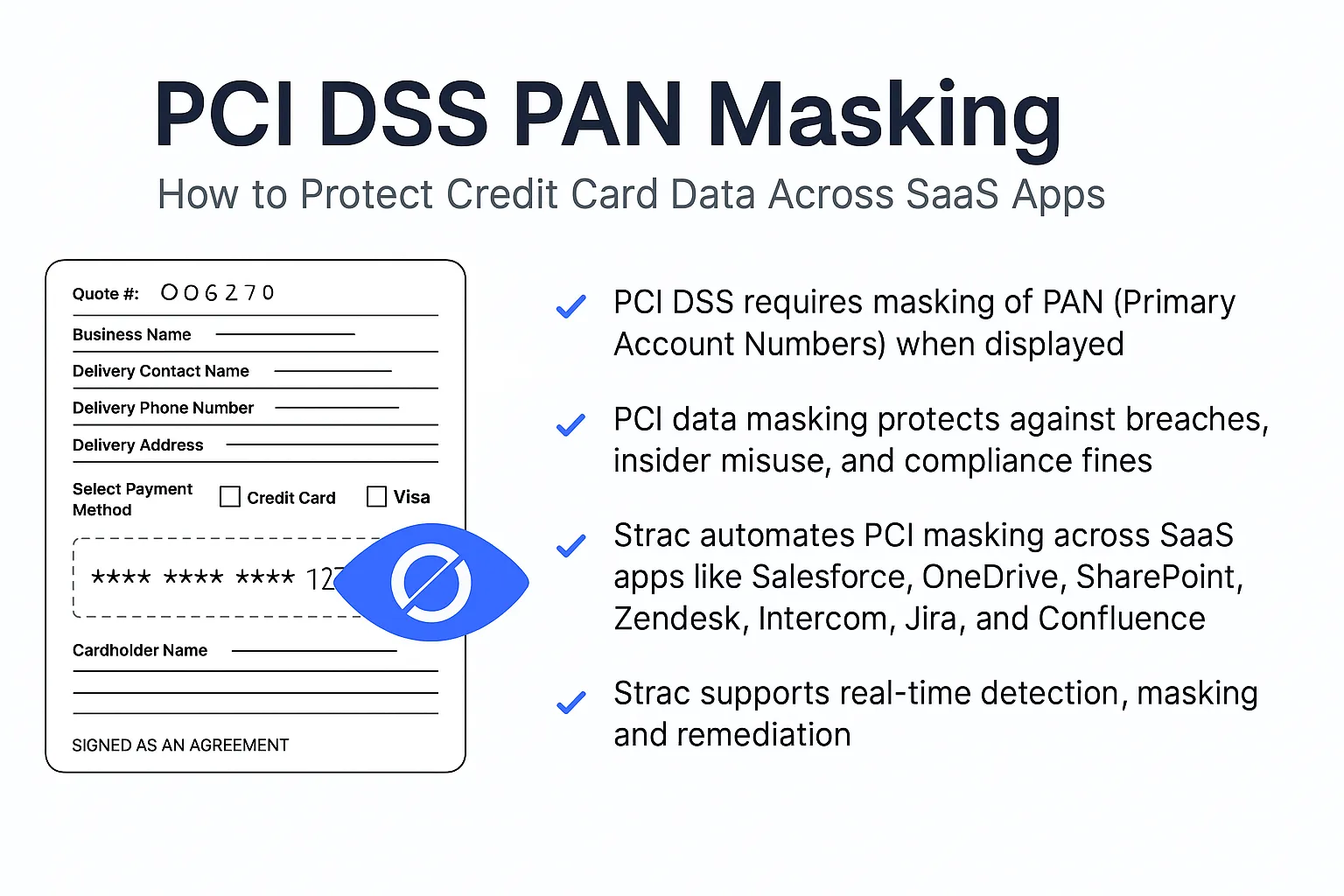
CCPAPIIPHIScan and redact PII PHI and confidential data in Email flows.avif) PCI DSSPIIPHIScan and redact PII PHI and confidential data in Email flows
PCI DSSPIIPHIScan and redact PII PHI and confidential data in Email flows
- Solutions
.webp) SaaS DLPPIIPHIIdentify, Categorize and Redact PII, financial information,PHI, IP’s from SaaS applications.
SaaS DLPPIIPHIIdentify, Categorize and Redact PII, financial information,PHI, IP’s from SaaS applications..webp) Endpoint DLPPIIPHIEnforce content classification and contextual analysis to identify sensitive information at endpoints
Endpoint DLPPIIPHIEnforce content classification and contextual analysis to identify sensitive information at endpoints.webp) Gen AI DLPPIIPHIEnhance your enterprise data security layer for endpoints ,SaaS and Cloud with one DLP integration.
Gen AI DLPPIIPHIEnhance your enterprise data security layer for endpoints ,SaaS and Cloud with one DLP integration. Email SecurityPIIPHIScan and redact PII PHI and confidential data in Email flows
Email SecurityPIIPHIScan and redact PII PHI and confidential data in Email flows PII ScannerPIIPHIAccurate sensitive data scanning and classification across all Endpoints ,SaaS and Cloud
PII ScannerPIIPHIAccurate sensitive data scanning and classification across all Endpoints ,SaaS and Cloud
.webp) Mac DLPPIIPHISeamlessly integrate data loss prevention with MacOS
Mac DLPPIIPHISeamlessly integrate data loss prevention with MacOS.webp) Data DiscoveryPIIPHIAccurate sensitive data inspection and classification in Real-Time to Safeguard Information Tailored to Specific Needs
Data DiscoveryPIIPHIAccurate sensitive data inspection and classification in Real-Time to Safeguard Information Tailored to Specific Needs.webp) ChatGPT DLPPIIPHIPrevent PII ,PHI and sensitive files shared to AI models to safeguard customer info
ChatGPT DLPPIIPHIPrevent PII ,PHI and sensitive files shared to AI models to safeguard customer info Linux DLPPIIPHIMonitor ,Detect and remediate sensitive data in Linux systems.
Linux DLPPIIPHIMonitor ,Detect and remediate sensitive data in Linux systems.
Use casesIndustries- HealthcarePIIIdentify, Categorize and Redact PII, financial information,PHI, IP’s from SaaS applications.
- FintechPIIPHIEnforce content classification and contextual analysis to identify sensitive information at endpoints
- PIIPHIEnhance your enterprise data security layer for endpoints ,SaaS and Cloud with one DLP integration.
- IntegrationsIntegrations
- IntegrationsDetect & Redact PIIPII
HandlingDocument Vault - Resources

- About
- Blog
Cart(
0
)
No items found.
Product is not available in this quantity.
1 / 16
Next










.webp)














.webp)