Microsoft Purview DLP: Coverage, Licensing, and Best Pairings
Learn what Microsoft Purview DLP covers, where it’s strong, common gaps, and how Strac adds real-time redaction, ML/OCR accuracy, and multi-surface coverage.
Why this matters: Most data movement in Microsoft-centric orgs happens in email, files, chat, and on endpoints. If sensitive data slips through here, you risk breaches and compliance penalties.
Real example: A finance analyst emails a spreadsheet with PANs; Purview can detect and block or encrypt before it leaves Exchange.
How Strac helps: Keep Purview policies as your baseline, then use Strac to redact/mask inline and apply the same controls across non-Microsoft tools and AI workflows.
Key points
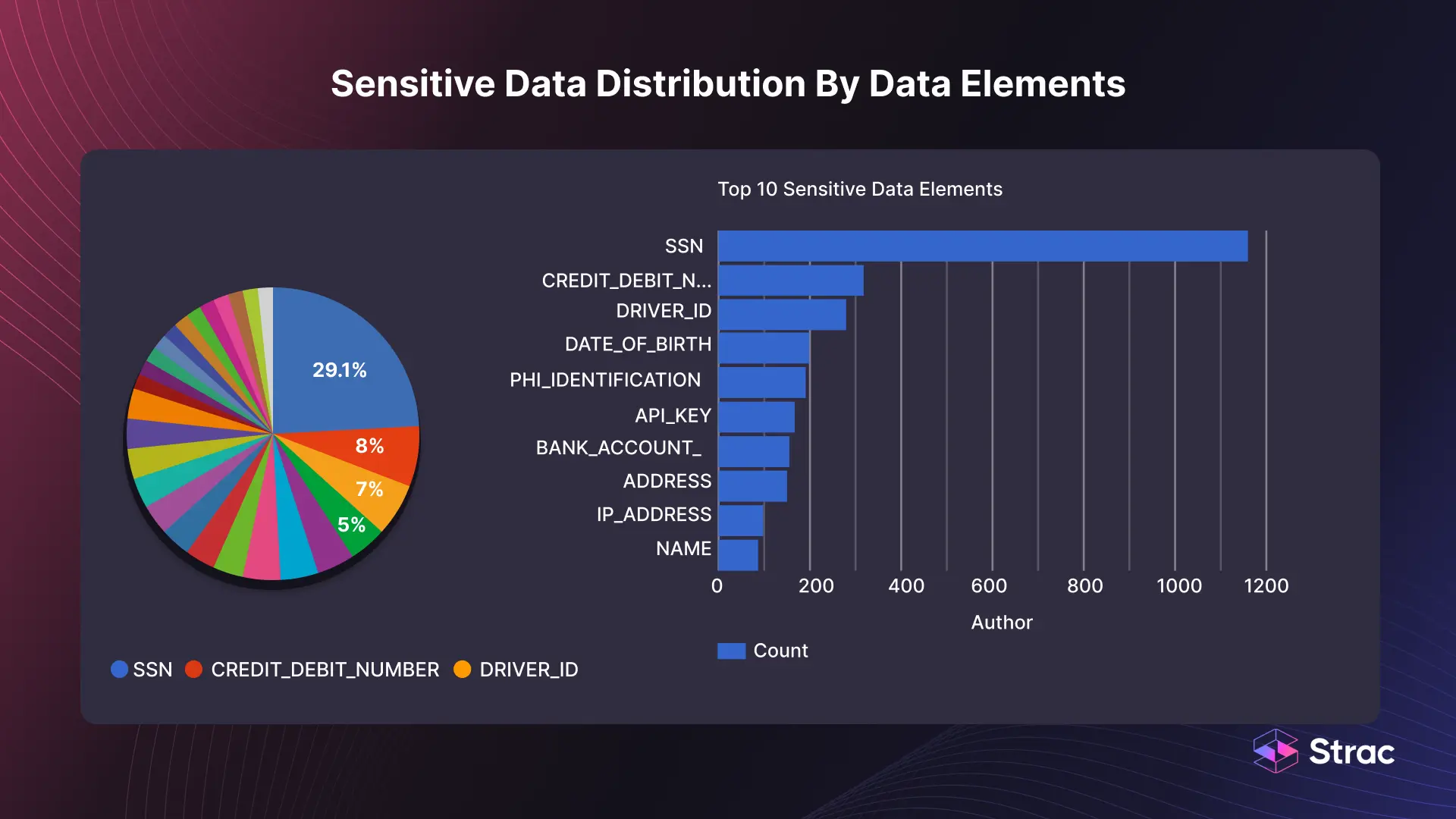
Why this matters: Classification is the backbone of effective DLP.
Compliance example: PCI DSS requires controlling access and transmission of PAN; labeling + policy tips reduce accidental egress.
How Strac helps: Strac’s content-aware ML/OCR boosts accuracy on unstructured content and attachments—reducing noise vs. pure pattern/regex.
Highlights
Why this matters: Teams frequently design policies the license won’t enforce.
Compliance example: A legal team expects Teams chat DLP, but the tenant is on E3 only—policies won’t apply to chats.
How Strac helps: Regardless of your Microsoft license mix, Strac adds consistent controls across Microsoft and non-Microsoft surfaces.
Quick guide
Why this matters: You get excellent first-party coverage where your users spend time.
Example: A SharePoint library with sensitive contracts inherits DLP guardrails without extra tooling.
How Strac helps: Keep Purview for native surfaces; add Strac for deeper detection and instant remediation where Microsoft actions stop at notify/block.
Strengths to leverage
Why this matters: Data doesn’t live only in Microsoft formats or clouds.
Example: A product team shares design files (Figma exports, CAD, images); basic patterns miss sensitive snippets inside images/PDFs.
How Strac helps: Strac uses ML/OCR to inspect unstructured and non-Office formats and can redact/mask inline—not just alert.
Typical gaps
Why this matters: Most orgs are hybrid—Microsoft + SaaS + Cloud + AI + Browser + Endpoints.
Example: A user uploads a CSV with PANs to a SaaS ticket; you want immediate masking, not a late alert.
How Strac helps: Strac unifies DSPM + DLP and brings agentless, content-aware, inline remediation to Microsoft and beyond.
What you get with Strac

Why this matters: Email is still the #1 exfiltration path.
Compliance example: PCI DSS requires protection of PAN in transit; coaching alone isn’t enough.
How Strac helps: Real-time scanning on compose/send and mailboxes with auto-redaction.
Capabilities
Why this matters: Sensitive files sprawl across team sites and libraries.
Compliance example: A public link to a contract with PHI/PII violates HIPAA/GDPR expectations.
How Strac helps: Discover sensitive files, map exposures, auto-redact inline where possible, and revoke risky shares quickly.
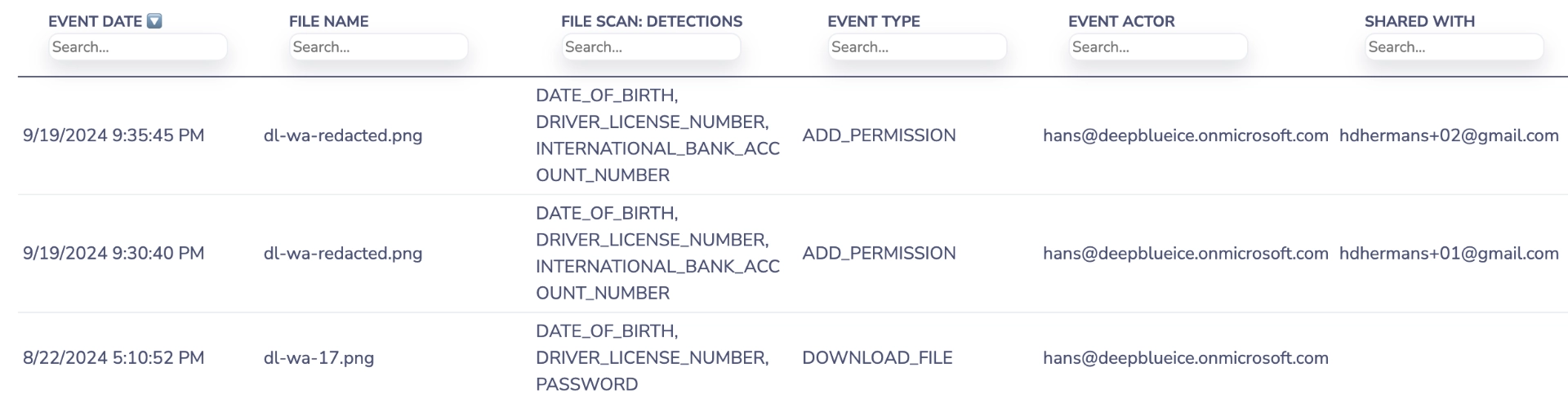
Why this matters: Shadow sharing and sync folders spread sensitive data.
Compliance example: External collaborator gets a OneDrive folder with invoices containing PANs.
How Strac helps: Continuous monitoring of access/shares; classify at scale; mask PCI/PII; enforce on downloads/external shares.
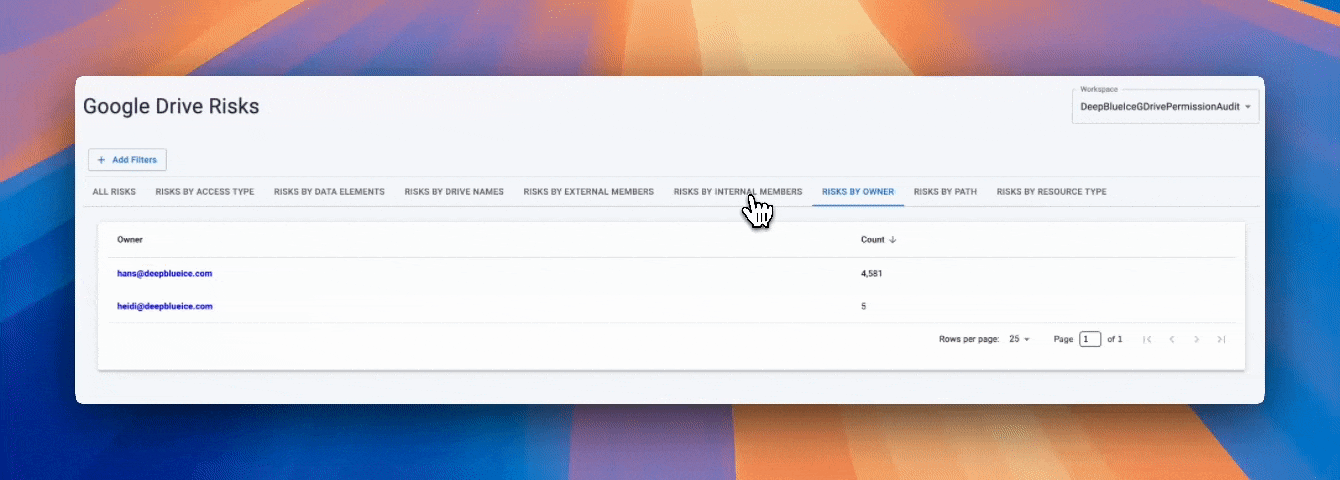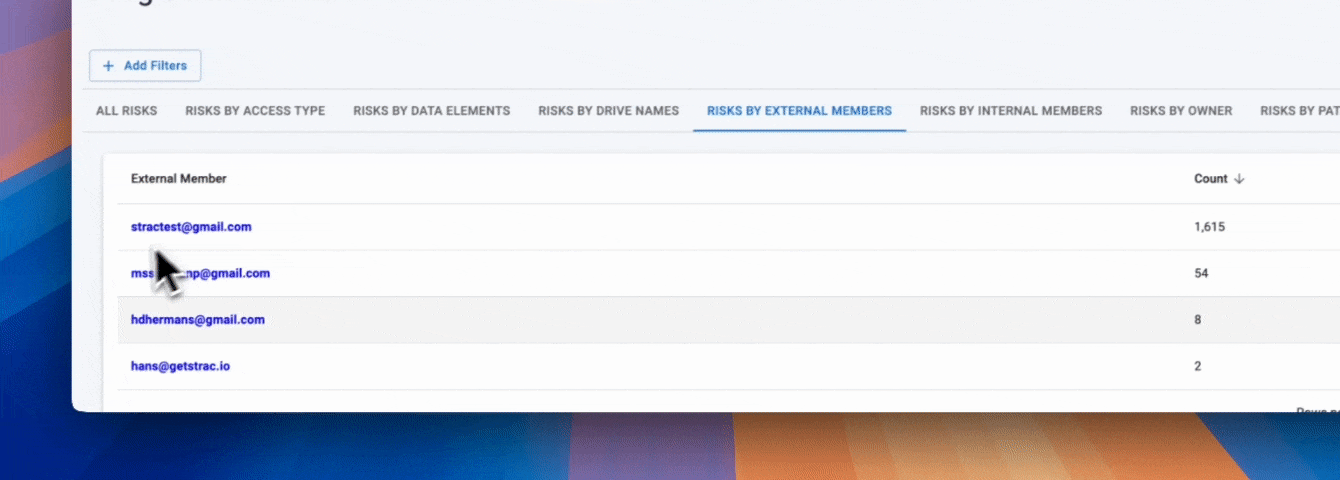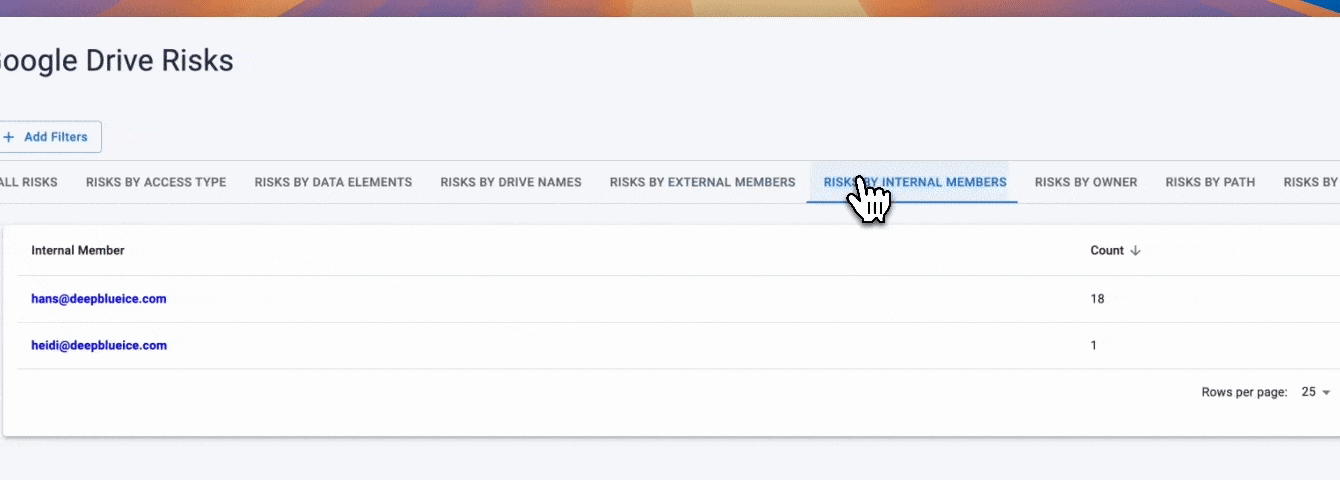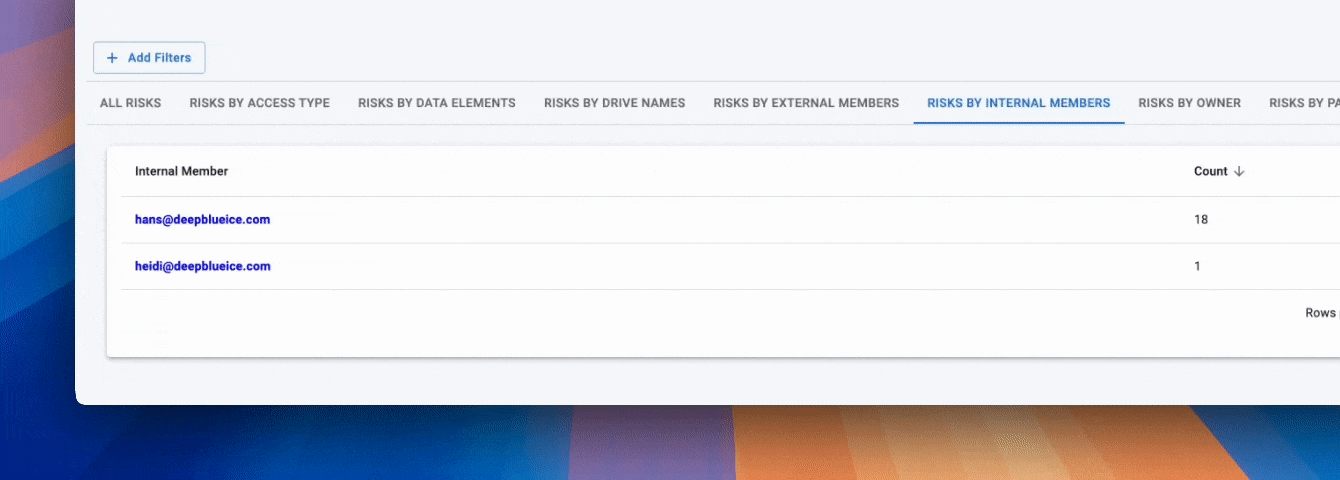
Use Microsoft Purview DLP to standardize native controls across Microsoft 365 and endpoints. Add Strac to cut dwell time with instant redaction/masking, reduce noise with ML/OCR detections, and extend DLP into SaaS, Cloud, GenAI, Browser, and Endpoints—without agents.
It depends on licensing. Many orgs need E5 (or add-ons) for Teams chat DLP. Strac can complement with inline actions for high-risk content in and beyond Teams.
Blocking alone creates friction and tickets. Strac auto-redacts/masks inline so legitimate business emails can proceed safely—and you keep a full audit.
No. Keep Purview for native Microsoft coverage and governance. Use Strac to improve accuracy, act in real time, and cover non-Microsoft tools and AI flows.
Purview can detect patterns, but screenshots and scans are tricky. Strac’s OCR reads images/PDFs and can mask/redact instantly.
Yes. Purview provides policy governance for Microsoft data; Strac extends sensitive-data controls to GenAI prompts/responses and non-Microsoft surfaces.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

