How to Block PCI Credit Card Numbers in Google Drive Automatically
Learn how to automatically block credit card numbers (PCI data) in Google Drive using Strac’s real-time DLP engine to prevent sensitive files from being stored or shared.
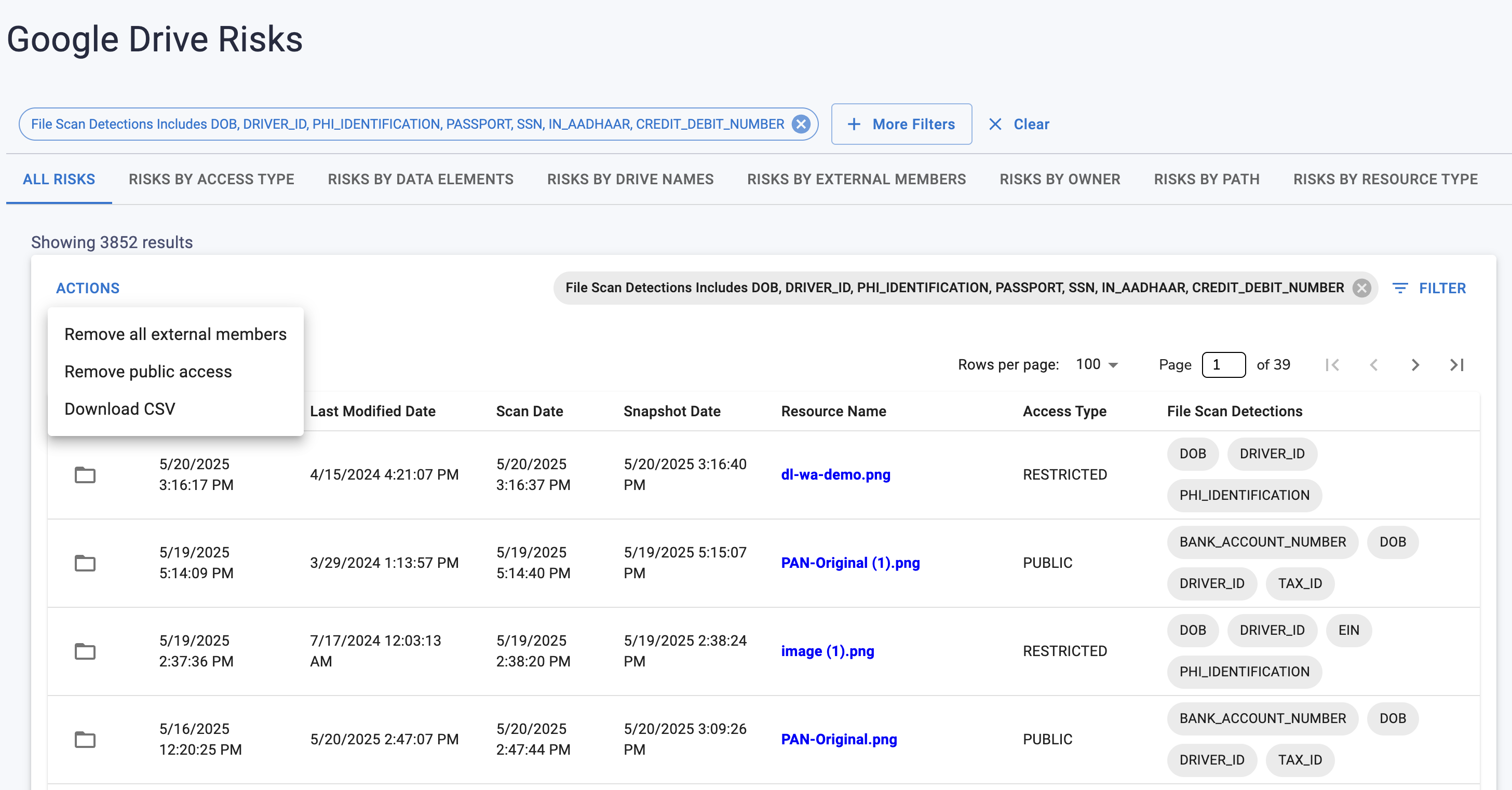
Google Drive stores massive amounts of financial and operational data; however it has no built-in mechanism to block card numbers before they are uploaded or shared. That means invoices with full PANs, Stripe/Shopify exports, or screenshots containing full card details can enter Drive and become accessible across teams or externally. This violates PCI DSS rules because unprotected PANs cannot be stored in shared repositories.
Strac prevents this by blocking files that contain PCI data before they reach Drive folders or Shared Drives.
Google Drive does not inspect file contents before upload; cannot recognize credit card patterns; and cannot stop a file from being saved if it contains PCI. Files with PANs can spread across shared folders; become synced to user devices; or be shared externally without visibility.
Google Drive lacks:
• PCI detection during upload;
• Pre-storage content scanning;
• OCR for images containing card numbers;
• Real-time blocking workflows;
• Misconfiguration detection for public or external sharing;
• PCI DSS audit logs.
Strac solves this by scanning the content of files before they reach Drive; blocking uploads or shares if PCI is detected.
PCI often enters Drive from operational workflows; and blocking must detect PANs across all file formats. Strac identifies PCI in text, spreadsheets, images, PDFs, and zipped folders; then blocks uploads or sharing actions to ensure compliance.
Strac blocks files containing:
• PANs such as 4242 4242 4242 4242;
• Full credit card numbers in spreadsheets;
• Screenshots containing card details;
• Payment exports from CRM or billing tools;
• PDFs with cardholder data or receipts;
• Transaction logs with visible card numbers;
• Customer disputes or chargeback documents.
When blocking occurs, Strac:
• Prevents the file from being stored in Drive;
• Notifies the uploader;
• Alerts admins or security teams;
• Logs the event for PCI DSS compliance.
Blocking applies across:
• My Drive
• Shared Drives
• Team Drives
• Synced folders
• Uploads via web or mobile
• File sharing events
• Third-party tool integrations
Strac integrates with Google Drive using API-level scanning; performing deep content inspection before files are stored or shared. Using AI, OCR, and PCI detection patterns, Strac ensures no unprotected card numbers enter Drive.
Blocking workflows include:
• Pre-upload PCI scanning;
• Preventing file creation when PCI is detected;
• Blocking external sharing of PCI-containing files;
• Notifying admins or security channels;
• Triggering SIEM alerts;
• Logging events for PCI DSS evidence;
• Optional redaction-first or delete-first workflows.
This prevents PCI from being stored in Drive while maintaining operational continuity.
Strac prevents PCI from entering Drive entirely. With AI-powered scanning, OCR, contextual PCI logic, and pre-upload blocking, Strac ensures your Google Drive remains compliant with PCI DSS and free of sensitive customer payment data.
Strac delivers:
• Real-time PCI blocking;
• OCR-based scanning for images and PDFs;
• Prevention of PCI storage in My Drive and Shared Drives;
• External sharing controls;
• Compliance-grade logs for audits;
• Fast, no-code deployment;
• Broad app coverage beyond Drive.
No; Drive cannot block PCI or inspect files for sensitive data.
Yes; OCR allows blocking of scanned or visual content.
Yes; blocked files never enter Drive or user sync folders.
Yes; policies apply to all Drive surfaces.
Yes; PCI DSS requires preventing unauthorized storage of PANs.
Strac ensures PCI never reaches Google Drive; protecting sensitive customer data and maintaining PCI DSS compliance.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

