What is Generative AI Data Security
Learn how to secure and govern generative AI data using AI-native DSPM, real-time DLP, and enforceable AI data governance frameworks.
Generative AI runs inside everyday workflows; support, engineering, marketing, analytics; whereeversensitive data already lives. Prompts, uploads, embeddings, and AI-generated outputs now sit directly in the path of regulated data, IP, and internal communications.
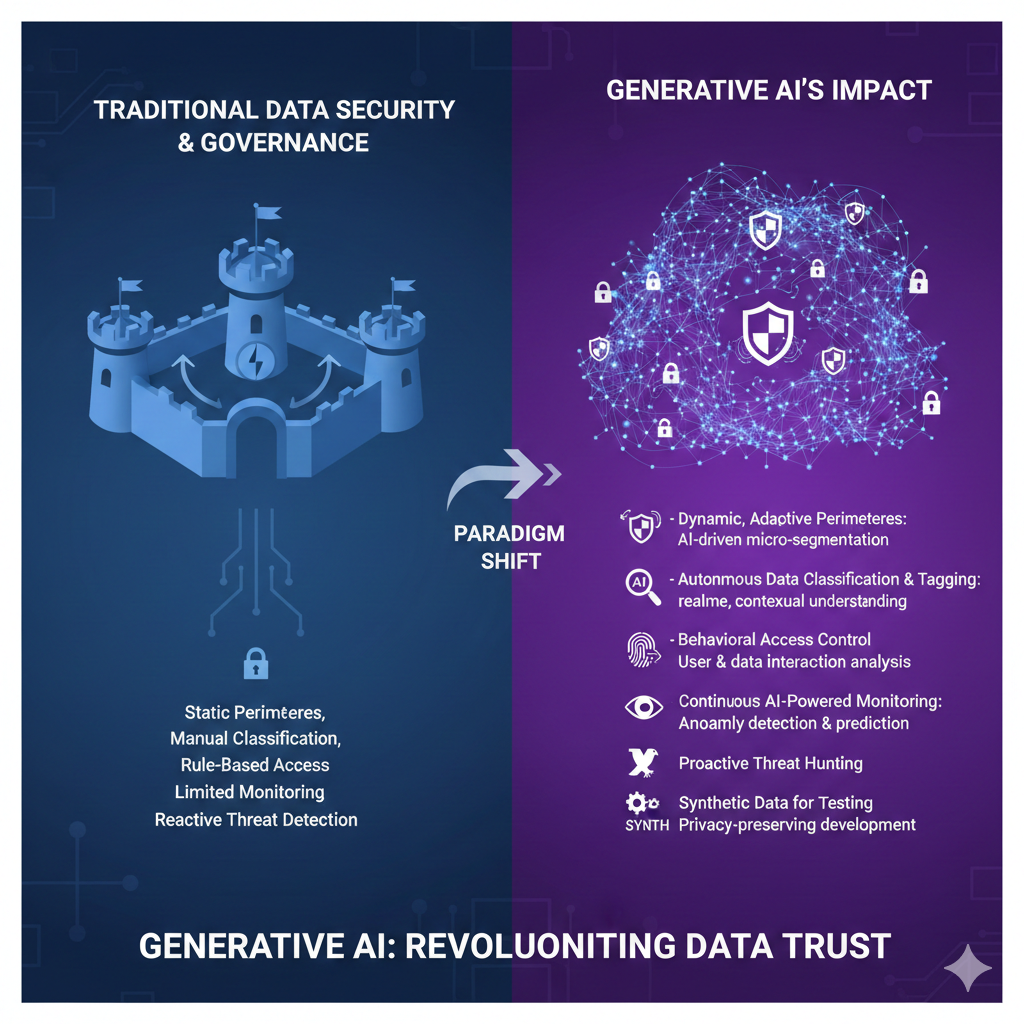
Traditional data security models were never designed for this. AI does not just move data; it processes, combines, and regenerates it in real time. That breaks perimeter-based assumptions and forces a new approach that treats visibility, governance, and runtime enforcement as one system.
Generative AI data security is about controlling what data can enter AI workflows and what can come out.
In real environments, teams paste customer data, internal documents, and proprietary context into ChatGPT, copilots, or internal assistants to get work done faster. That behavior is normal. The risk is that once data enters an AI context window, traditional controls lose visibility entirely.
What generative AI data security must cover:
Generative AI changes data security because data is no longer static.
Key assumptions that no longer hold:
Once sensitive data enters an LLM context, there is no file to scan and no record to classify. The data is still being processed; just outside traditional visibility.
Accountability does not disappear. Organizations are still responsible for protecting personal data, regulated information, and intellectual property; regardless of whether content is written by a human or generated by AI.
That is why generative AI data security requires real-time visibility and enforceable controls inside AI workflows. Policies alone do not prevent AI data leakage.
Generative AI introduces new data exposure paths that do not exist in traditional applications. These paths bypass familiar security boundaries and operate outside legacy inspection points. They are frequent, operational, and invisible unless governance and enforcement are designed specifically for AI workflows.
This is where most AI data security programs break; they govern systems, not usage.
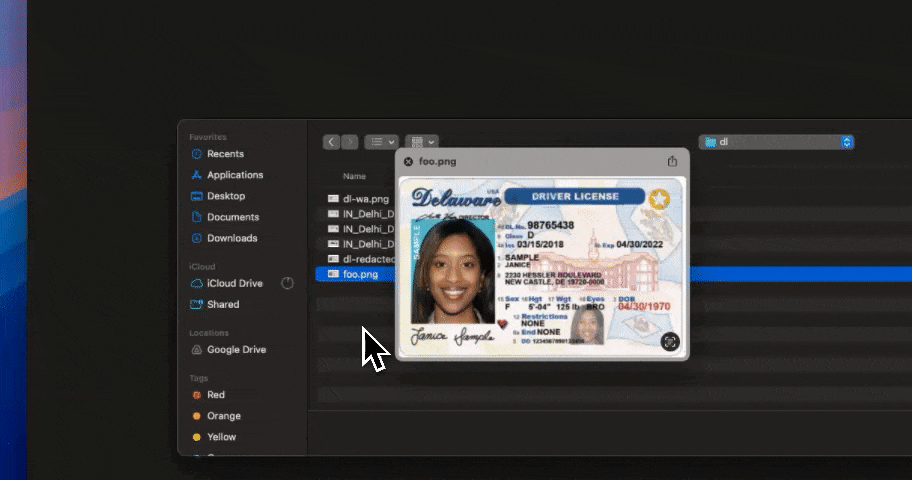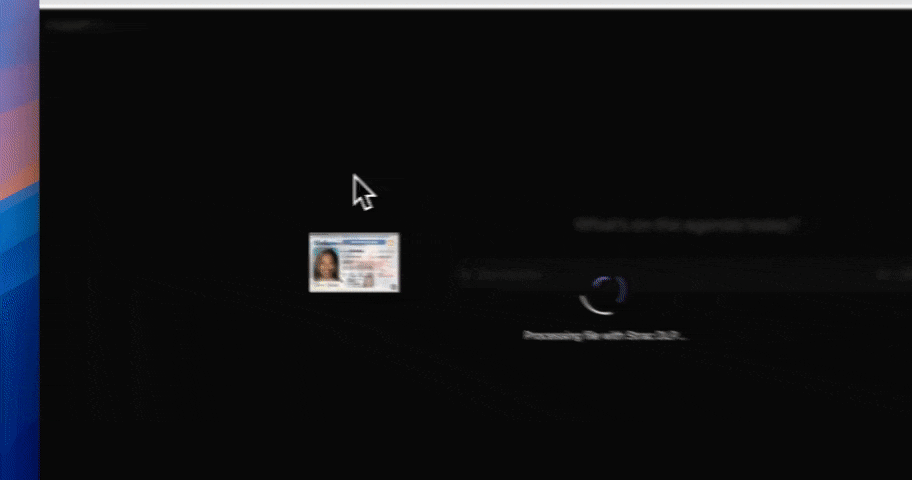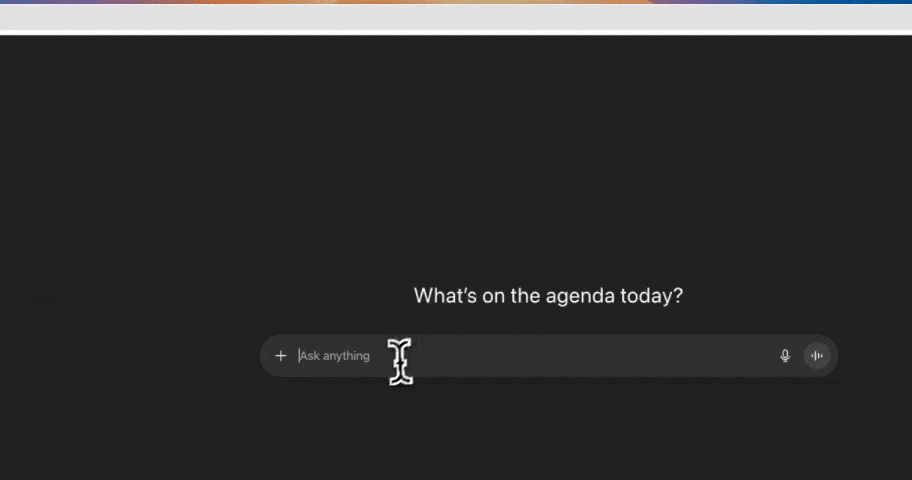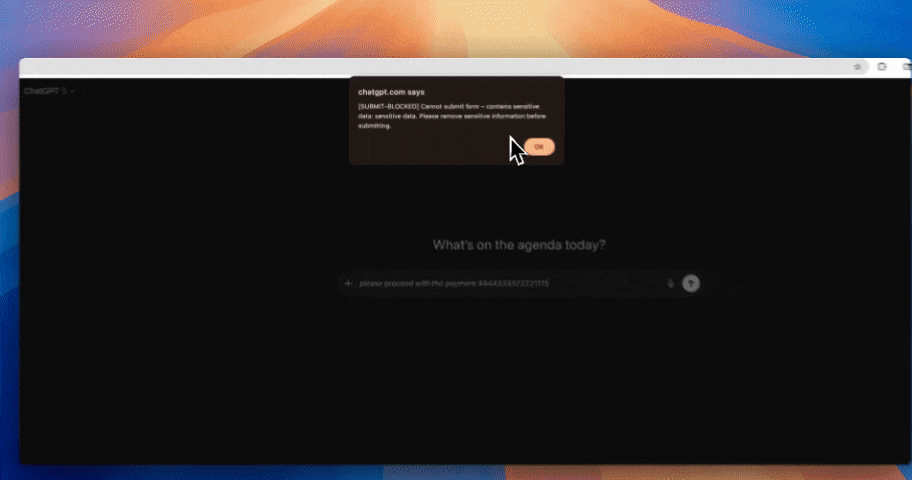
Prompts are now one of the largest sources of AI data exposure.
Employees paste sensitive information directly into chat-based AI tools to get work done faster. That includes PII, PHI, source code, internal strategy, API keys, and credentials. There is no file boundary, no attachment, and no perimeter to inspect.
Legacy DLP and governance tools were built to monitor emails, files, and databases. They cannot reliably see or control data once it is embedded inside a prompt. Policies may exist, but enforcement fails at the exact moment risk is introduced.
Spicy take; if your governance model doesn’t see prompts, it doesn’t see AI risk.
Prompts are not the only path.
Modern AI tools support file uploads and extended context windows. Users attach spreadsheets, PDFs, tickets, internal docs, and customer records to enrich AI responses. Once uploaded, that data is absorbed into the model’s working context rather than remaining in a governed repository.
This creates a blind spot:
From an AI data security perspective, uploads without inline inspection guarantee exposure.
Data exposure does not stop at ingestion.
AI-generated outputs can reproduce or infer sensitive information from prompts and context. Those outputs are copied, reused, shared internally, and sent to external systems. This creates a secondary exposure path that many governance models ignore.
Governance that only focuses on what enters AI systems is incomplete. Outputs must be inspected and controlled as well, or sensitive data simply exits through a different door.
Generative AI reshapes data governance because data now moves through:
If visibility, enforcement, and accountability do not span all four, AI data security is incomplete.
Generative AI exposes the limits of legacy controls immediately. Traditional DLP and policy-only AI governance were built for stable data paths and human-paced workflows. AI operates at runtime, inside live interactions, outside those assumptions.
This is not a governance gap. It is an execution gap.
This is the core mismatch in traditional DLP vs AI DLP; legacy tools cannot see or stop exposure happening inside live AI interactions.
Spicy take; policy without enforcement is paperwork, not security.
AI data protection must act inline; block, redact, or remediate before processing.
Generative AI data security only works as a live control system. Visibility, decision-making, and enforcement must operate together across real AI usage.
This shifts governance from abstract rules to real exposure awareness.
If controls don’t act at runtime, they don’t protect AI.
Centralization prevents drift and blind spots. AI data security becomes scalable, auditable, and enforceable; without slowing teams down.
Generative AI data security depends on more than controlling AI interactions in isolation. It requires a clear understanding of the organization’s underlying data posture, how sensitive data is distributed across systems, and how that data can realistically flow into AI workflows. DSPM, generative AI usage, and governance form a dependency chain; if one layer is missing, the entire security model weakens.
DSPM for AI provides the visibility foundation that effective AI data security requires. It identifies where sensitive data lives across SaaS applications, cloud storage, data warehouses, and collaboration platforms; long before that data is introduced into an AI prompt or uploaded to an LLM.
Without AI data posture management, organizations lack clarity on which datasets are sensitive, overexposed, or poorly governed. This creates blind spots where data can unintentionally flow into AI systems. DSPM closes that gap by mapping sensitive data locations, access patterns, and exposure levels, turning AI governance decisions into informed, risk-based actions rather than assumptions.
Generative AI does not create data sprawl; it accelerates and exposes it. Data that previously sat idle in documents, tickets, spreadsheets, or internal tools can instantly become active input through prompts, uploads, and context windows. This amplification effect increases ai data visibility requirements because AI systems pull from across the entire data estate, not from a single controlled repository.
In this environment, generative AI data security is only as strong as the organization’s weakest data posture. DSPM highlights where AI-driven workflows are most likely to introduce risk, allowing teams to prioritize controls based on real exposure rather than hypothetical scenarios.
AI data governance defines how data should be used, but DSPM determines whether that governance can realistically be enforced. Governance frameworks without posture awareness assume that data is already well understood and controlled; in practice, this is rarely the case.
When DSPM insights are connected to governance and runtime enforcement, governance becomes operational. Policies can be aligned with actual data locations, access paths, and exposure levels, enabling enforceable controls across AI and SaaS environments. In this way, DSPM does not sit alongside governance; it makes governance actionable within generative AI data security architectures.
AI governance only works when it operates inline with real usage. In production, that means enforcing controls across the full AI interaction lifecycle; prompt, upload, output, and audit.
What enforceable AI governance requires:
If governance does not inspect, enforce, and log at runtime, it is policy; not protection.
Generative AI data security doesn’t change compliance obligations; it exposes them. Regulations like GDPR, HIPAA, and PCI still apply to data shared with AI systems, including prompts, context, uploads, and generated outputs. Whether data is handled by a human or an AI model, organizations remain responsible.
AI does not remove accountability. If employees submit sensitive data to an AI tool, or if an AI response exposes regulated information, the organization is still liable. This makes generative AI data security a governance issue, not just a technical one.
Regulators expect evidence, not intent. Policies and training alone are not enough. Organizations must be able to show:
Without this visibility, defending AI usage during audits becomes difficult. Effective generative AI data security relies on real-time controls and audit-ready enforcement; not compliance on paper.
Generative AI changes how data security platforms must be evaluated. AI risk does not happen at rest or at the perimeter; it happens at runtime, across prompts, uploads, and generated outputs, inside SaaS workflows.
Visibility without enforcement fails here. Policy without execution fails faster. Strac was built for this reality; not retrofitted from legacy DLP.
AI governance only works if it is grounded in real exposure.
Strac discovers sensitive data based on how it is actually used in AI workflows; SaaS apps, support tickets, shared docs, internal datasets, and files users paste into prompts or upload to models. DSPM surfaces where sensitive data lives and who can access it, so AI controls are applied based on reality, not assumptions.
If you don’t know what data can reach AI, you can’t control it.
AI governance must execute, not just define intent.
Strac turns governance rules into runtime controls. Policies are enforced inline during AI interactions, ensuring sensitive data does not enter generative AI systems in violation of internal or regulatory requirements.
Spicy take; governance that cannot enforce at runtime does not survive an audit.
AI risk materializes at submission and generation.
Strac inspects prompts before submission, scans files uploaded to AI tools, and inspects AI-generated outputs before they are shared. Remediation; redaction, masking, blocking, removal; happens before exposure, not after alerts fire.
Alert-only AI DLP is still post-breach.
Detection does not scale in AI environments.
Strac performs inline redaction and automated remediation across AI and SaaS workflows without manual intervention. This reduces risk while keeping productivity intact.
Automation is not a feature here; it is the operating model.
Generative AI does not sit outside the business. Data flows from SaaS into AI and back again.
Strac applies consistent policies across ChatGPT, SaaS applications, and cloud environments in one control plane. No policy drift. No fragmented enforcement.
Disjointed controls create blind spots; unified control removes them.
DSPM shows where sensitive data exists. AI DLP controls how it is used.
Strac unifies both. Organizations can discover sensitive data, assess exposure, and enforce AI controls without stitching together multiple tools.
AI amplifies data sprawl; posture awareness is not optional.
AI adoption moves faster than traditional security rollouts.
Strac’s agentless, API-driven architecture deploys quickly across SaaS and AI workflows with minimal configuration and no endpoint agents.
If deployment takes months, AI risk has already moved on.
AI data security must be provable.
Strac provides detailed logs showing what data was inspected, what policy applied, and what action was taken; aligned with GDPR, HIPAA, PCI DSS, and SOC 2, including AI-specific enforcement evidence.
Auditors want proof, not promises.
AI security cannot live in isolation.
Strac integrates with SIEM and SOAR so AI data security events flow into existing monitoring, triage, and response workflows.
AI security is part of security operations; not a side console.
Generative AI data security is no longer optional. As AI systems become embedded in everyday workflows, organizations must move beyond policy-only AI governance toward enforceable, runtime controls that actively prevent sensitive data from entering generative AI systems. Visibility, governance, and enforcement must operate together; across prompts, uploads, and outputs; to meaningfully reduce risk.
The organizations that succeed will be those that treat AI data security as an operational capability, not a documentation exercise. By implementing real-time inspection, automated remediation, and audit-ready governance across AI and SaaS environments, teams can secure generative AI usage while preserving the speed and productivity that drove adoption in the first place.
Generative AI data security focuses on preventing sensitive information from being exposed through generative AI systems during real usage. It addresses how data flows into AI tools through prompts, file uploads, and context windows, and how it leaves those systems through generated outputs. Because exposure happens in real time, generative AI data security must operate inline rather than relying on delayed detection or after-the-fact review.
In practice, it combines visibility, governance, and enforcement into a single operational approach that can inspect and control AI interactions as they happen.
AI data governance defines how AI tools can be used, what data is allowed to enter them, and how usage is monitored and audited across the organization. It matters because AI does not remove regulatory or accountability obligations; organizations remain responsible for how personal data, regulated information, and intellectual property are processed.
Effective AI data governance includes:
Without enforcement, governance exists only on paper and does not reduce real AI data exposure.
Traditional DLP tools were designed for predictable data paths and static boundaries such as email, file transfers, and endpoints. ChatGPT changes the exposure surface by embedding data directly into text-based prompts and contextual memory.
Traditional DLP fails in this context because:
For ChatGPT, risk occurs at submission time, which is why AI-native, runtime enforcement is required.
DSPM supports AI data governance by providing visibility into where sensitive data actually resides across SaaS and cloud environments. This visibility is critical because AI systems pull context from across the organization, not from a single controlled repository.
DSPM enables governance by:
Without DSPM, AI governance decisions are based on assumptions rather than real data exposure.
Deployment timelines vary by organization, but modern AI data security platforms are designed to be deployed quickly without disrupting productivity. SaaS-native, agentless architectures significantly reduce rollout time compared to legacy security tools.
A typical rollout follows a staged approach:
This approach allows teams to achieve meaningful protection early while expanding coverage incrementally as AI usage grows.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

