Comprehensive Guide to Data Loss Prevention (DLP) for Azure in 2025
Explore Azure DLP's role in protecting data, ensuring compliance, and mitigating risks in cloud environments. Find out how to ensure sensitive data is secure.
Microsoft Azure is a multi-faceted cloud computing platform offering services from virtual computing to analytics, storage, and networking, all essential for business scalability. However, cloud storage often requires stringent security measures due to its inherent vulnerabilities.
According to industry reports, organizations face financial and security challenges, with annual losses averaging $15.4 million due to insider threats, and 83% of organizations experience multiple data breaches. These staggering statistics underscore the need for robust security measures in cloud environments like Microsoft Azure.
That's where DLP (Data Prevention Loss) in Azure comes in. It safeguards sensitive data from unauthorized access and breaches, ensures compliance with data protection laws, and mitigates financial risks. Implementing an effective DLP solution protects valuable information and is crucial in reinforcing organizations' operational and economic stability. This blog covers the fundamentals of Azure DLP, its advantages, drawbacks, steps for implementation, and more. Let’s begin.
Azure's data ecosystem comprises a range of services, tools, and processes for storing, managing, and analyzing data. Let’s take a detailed look at them.
Data is stored across various Azure services tailored to users’ needs. These include:
Azure Blob Storage accommodates unstructured data such as images, documents, and backups. It offers scalable storage solutions, making it ideal for large data quantities for user access or analytical purposes.
Azure Virtual Machines (VMs) provide virtualized servers, allowing users to run cloud applications. They handle everything from application data and configurations to operating system files, offering a scalable and flexible computing environment.
Azure supports multiple database services like SQL Database, Cosmos DB, and Azure Database for PostgreSQL. These services manage structured data critical for application functionality, ensuring efficient data handling and quick retrieval.
Azure faces typical data security challenges that require proactive management. This includes:
Organizations must understand that while Azure secures the infrastructure, they are responsible for correctly configuring the platform and services. Inadequate security measures and poor access control can result in data breaches and failure to comply with regulations such as GDPR.
Misconfigured firewall settings can often lead to unauthorized access to Azure services and resources, exposing sensitive data. Organizations need to control access permissions to secure their data against breaches rigorously.
Storing data in Azure involves adherence to various regulatory compliance requirements:
Organizations dealing with EU citizens' data must meet GDPR requirements dictating data protection, privacy, and user consent standards. Azure aids organizations in achieving GDPR compliance through specific tools and functionalities.
For healthcare organizations managing sensitive patient information, HIPAA compliance is mandatory. Azure supports these requirements with HIPAA-compliant services and features that ensure secure data storage and processing.
Organizations that collect personal information from California residents are bound by CCPA, which mandates data privacy and consumer rights. Azure assists organizations in complying with CCPA through features that protect consumer data and ensure privacy.
Azure's built-in Data Loss Prevention (DLP) capabilities are designed to help organizations prevent the loss, misuse, or unauthorized access to sensitive data. These capabilities are integrated across various Azure services and Microsoft applications, providing a comprehensive approach to safeguarding critical information.
Apart from that Azure Information Protection (AIP) and Microsoft Purview are two distinct solutions offered by Microsoft, aimed at enhancing data security and governance across an organization's digital estate. Both play crucial roles in managing sensitive information, but they focus on different aspects of data protection and governance.
Below, we explore the key aspects of Azure's DLP capabilities, including policy creation, content inspection, and integration with other services.

Azure's built-in DLP allows organizations to define and apply DLP policies across their digital estate. These policies enable the identification, monitoring, and automatic protection of sensitive items across Microsoft 365 services such as Teams, Exchange, SharePoint, and OneDrive accounts. Policies are the cornerstone of DLP, outlining rules and conditions for identifying sensitive data, such as credit card numbers or confidential documents, and specifying actions to prevent unauthorized disclosure or exfiltration.
Another capability is the ability to scan and analyze data in real time, both at rest and in transit. This content inspection aims to identify sensitive information based on predefined criteria, encompassing emails, documents, chats, and other communication channels. Once identified, sensitive data is classified and labeled accordingly, applying metadata tags or encryption to enforce security controls. This classification enables organizations to track and manage data throughout its lifecycle.
Azure DLP is deeply integrated with Microsoft 365 cloud services, Office apps, and Microsoft Edge, providing built-in protection without the need for additional agents. Moreover, DLP controls can be extended to Chrome and Firefox browsers through the Microsoft Purview extension and to various non-Microsoft cloud apps such as Dropbox, Box, Google Drive, and others through integration with Microsoft Defender for Cloud Apps.
Azure Blueprints facilitates the orchestration of consistent deployment of Azure resources, including specific DLP settings. This helps ensure that data protection configurations are uniformly applied across Azure services, simplifying compliance and enforcement of security policies.
Azure Information Protection (AIP) is designed to safeguard sensitive data within cloud and on-premises environments. It offers tools for classifying and protecting information effectively.
AIP enables organizations to assign classifications to documents and emails according to sensitivity. This process uses predefined or custom labels, which can be implemented automatically, manually, or through a hybrid approach, ensuring data is consistently categorized.
Following data classification, AIP implements protection protocols such as encryption, access restrictions, and visual markings. These measures secure sensitive data and ensure that organizational policies strictly govern access.
AIP provides capabilities to track how shared data is used and to revoke access when necessary. This feature enhances control over data distribution and helps mitigate unauthorized access risks.
Setting up AIP involves defining how data is classified, labeled, and protected within the organization.
Label Configuration
Administrators have the flexibility to create custom labels or utilize AIP's default options, like
These labels can be tailored with specific protection actions to meet the organization's needs.
AIP can automate the application of labels based on specific triggers, such as content characteristics or metadata within documents and emails, enhancing efficiency and compliance.
To promote uniform data classification application, AIP policies may include user instructions detailing the implications of each label and providing guidance on applying labels manually when necessary.
AIP's monitoring and reporting tools offer vital insights into managing and protecting sensitive data.
AIP logs user activities, including document access, modifications, and sharing. This logging supports compliance and security audits by providing detailed records of data interactions.
AIP generates multiple types of reports, such as usage summaries, label activity reports, and protection status reports. These documents help organizations understand their data protection landscape and guide improvements.
Integration with Azure Sentinel and other SIEM tools allows AIP to extend its analytics capabilities. These tools offer advanced insights into data protection trends and anomalies, aiding in proactive security management.
Microsoft Purview Data Loss Prevention helps organizations protect sensitive data by discovering and classifying vital information. Some of its features include:
Microsoft Purview Data Loss Prevention is designed to identify and protect sensitive data across Azure services. It provides tools for real-time data monitoring, classification, and enforcement of security policies to prevent unauthorized access and breaches.
Purview DLP can classify data based on predefined or custom sensitive information types (SITs), allowing organizations to understand their sensitive data across Azure.
Once sensitive data is identified, Purview DLP can secure it with protection measures such as encryption, access restrictions, and visual markings.
Purview DLP offers a centralized view of sensitive data across Azure services, including cloud apps, endpoints, and on-premises environments, providing comprehensive data protection.
Purview DLP allows organizations to create and configure DLP policies to govern the handling of sensitive data:
Administrators can define DLP policies that specify the sensitive data to monitor, the actions to take (e.g., block, notify, encrypt), and the scope of enforcement (e.g., cloud apps, endpoints).
Purview DLP policies consist of elements like sensitive information types, conditions, actions, and exceptions, which can be customized to meet the organization's specific requirements.
The Microsoft Purview compliance portal provides a centralized interface for creating, managing, and deploying DLP policies across the organization.
Purview DLP helps organizations detect and respond to potential data loss incidents:
When a DLP policy is triggered due to a potential data loss event, Purview DLP generates alerts that can be viewed and investigated in the compliance portal.
Purview DLP integrates with other Microsoft security solutions, such as Microsoft Defender for Cloud, to provide a comprehensive view of security incidents and enable efficient incident response.
Purview DLP offers reporting and analytics capabilities to help organizations understand data loss trends, identify high-risk areas, and optimize their DLP policies over time.
Implementing Data Loss Prevention (DLP) in Azure involves several steps to ensure that sensitive data is identified, monitored, and protected across your Azure environment. Here’s a detailed guide on how to set up DLP in Azure:
Before implementing DLP, it's crucial to identify and classify the sensitive data within your organization. This involves understanding what data you have, where it resides, and its level of sensitivity. Tools like Azure Information Protection can help classify and label data.
Select a DLP solution that integrates well with Azure. Microsoft offers native DLP capabilities through Microsoft Purview, which can be used across various Azure services. Alternatively, advanced DLP solutions like Strac seamlessly integrate with Microsoft Azure, offering robust data protection and compliance features, advanced content inspection, and policy-driven controls, helping organizations safeguard sensitive information across Azure services.
Configure DLP policies tailored to your organization's needs. These policies define the rules for what constitutes sensitive data and the actions to take when such data is detected. Microsoft Purview allows you to create, deploy, and manage DLP policies directly from its compliance portal.
Implement continuous monitoring to check compliance with your DLP policies. Azure offers tools like Azure Security Center and Azure Monitor to track and report policy violations. This step is crucial for maintaining visibility over data movement and usage within your cloud environment.
Set up alerts to notify administrators of potential policy violations. Microsoft Purview provides an alert management system where you can configure notifications and automate responses to detected incidents. This helps in quick remediation and prevents data leakage.
Conduct regular audits to ensure DLP policies are effective and compliant with regulatory requirements such as GDPR, HIPAA, or PCI DSS. Use Azure's compliance and audit reports to assess the effectiveness of your DLP implementation and make necessary adjustments.
Integrate DLP with security measures like encryption, access controls, and threat detection systems. This layered approach enhances the overall security posture by preventing data loss and protecting against external and internal threats.
Building on the foundational security measures provided by Azure’s built-in DLP features, organizations can further enhance their data protection strategies by adopting specific best practices. These practices maximize Azure DLP's effectiveness and foster a comprehensive data security culture within the organization.
1. Defining Clear DLP Policies
Establishing clear and comprehensive Data Loss Prevention (DLP) policies is critical to effectively deploying Azure DLPy. Such policies should outline the types of sensitive data and information assets that need protection, set forth data classification levels and corresponding security measures, and specify permitted and prohibited data handling activities. This foundation is essential for maintaining consistency in securing sensitive data across various organizational facets.
2. Training Employees on DLP Policies and Procedures
To ensure that DLP policies are effectively implemented, training employees is crucial. Comprehensive education on data classification, labeling, and the specific protection measures each classification entails should be mandatory. Highlighting the importance of DLP and the potential risks of non-compliance can also drive home the critical nature of these practices. Continuous updates and training refreshers help align the workforce with policy changes and new security protocols.
3. Regularly Monitoring and Auditing DLP Effectiveness
Effective DLP requires not just initial setup but ongoing oversight. Regular monitoring and auditing of Azure DLP controls help verify their effectiveness and pinpoint areas needing enhancement. Establishing clear metrics and performance indicators, regularly reviewing logs and alerts for anomalies, and conducting periodic audits are all practices that ensure DLP measures are not only in place but also fully functional and effective.
4. Updating DLP Policies as Needed
The dynamic nature of the digital landscape means that DLP policies must evolve. Regular reviews and updates of DLP policies ensure they remain effective and relevant. Updates should incorporate insights from DLP incidents, adapt to new data types and technologies, and align with evolving regulatory and industry standards. Staying proactive in policy management helps organizations adapt to emerging threats and maintain a strong data protection stance.
Here are some key limitations of Azure's in-built DLP capabilities compared to independent DLP solutions:
1. Complexity and Expertise Required
2. Limited Customization and Flexibility
3. Potential Integration Challenges
4. Limited Scope or Functionality
Overall, Azure's in-built DLP may require more expertise to manage and configure, offer less customization and flexibility, and face integration challenges compared to dedicated third-party DLP solutions.
Strac’s DLP for Azure emerges as an exemplary solution for securing sensitive data within cloud storage environments. Here's why:
Strac excels in offering real-time monitoring, a crucial feature that allows you to identify data breaches immediately. Its sophisticated data redaction capabilities ensure that sensitive information is either obscured or eliminated, providing a solid barrier against unauthorized access.

Strac DLP boasts an extensive catalog of data elements, encompassing personal identification, financial details, protected health information, and more. This comprehensive catalog supports accurate identification and provides robust protection for diverse data types, thereby reassuring the audience about the thoroughness of our data security measures.
Strac guarantees adherence to regulatory standards such as GDPR, HIPAA, and PCI, equipping organizations to meet stringent data protection requirements and avoid compliance penalties.
Strac DLP integrates seamlessly with Azure and Office 365, ensuring a smooth transition and delivering a cohesive data protection strategy across your cloud platforms. This integration simplifies security management and ensures consistent safeguarding of your sensitive data.

Employing a Zero Data Architecture, Strac DLP ensures that sensitive data is tokenized and secured without storage on backend servers, significantly reducing the risk of data exposure and improving protection.
Strac implements role-based access control, enabling organizations to specify and regulate user permissions according to individual roles and responsibilities. This detailed control ensures that only authorized personnel can access sensitive data, enhancing security and maintaining confidentiality.
By adopting Strac DLP for Azure, organizations can leverage these advanced features to ensure robust security, regulatory compliance, and efficient management of sensitive data in the cloud.
Schedule a demo with Strac today and get started with DLP in Azure, which protects your data unlike ever before.

Data Loss Prevention (DLP) for Azure is critical for securing sensitive data, but many teams still underestimate how limited native protection can be. While Azure DLP helps detect and control data sharing inside Microsoft’s ecosystem, it doesn’t fully protect information once it moves across SaaS, cloud, or GenAI tools. To close those gaps and achieve true end-to-end security, organizations need an approach that expands Azure DLP beyond detection into proactive protection.
With Strac, Azure DLP transforms from a passive rule engine into an active guardian of your organization’s entire data ecosystem.
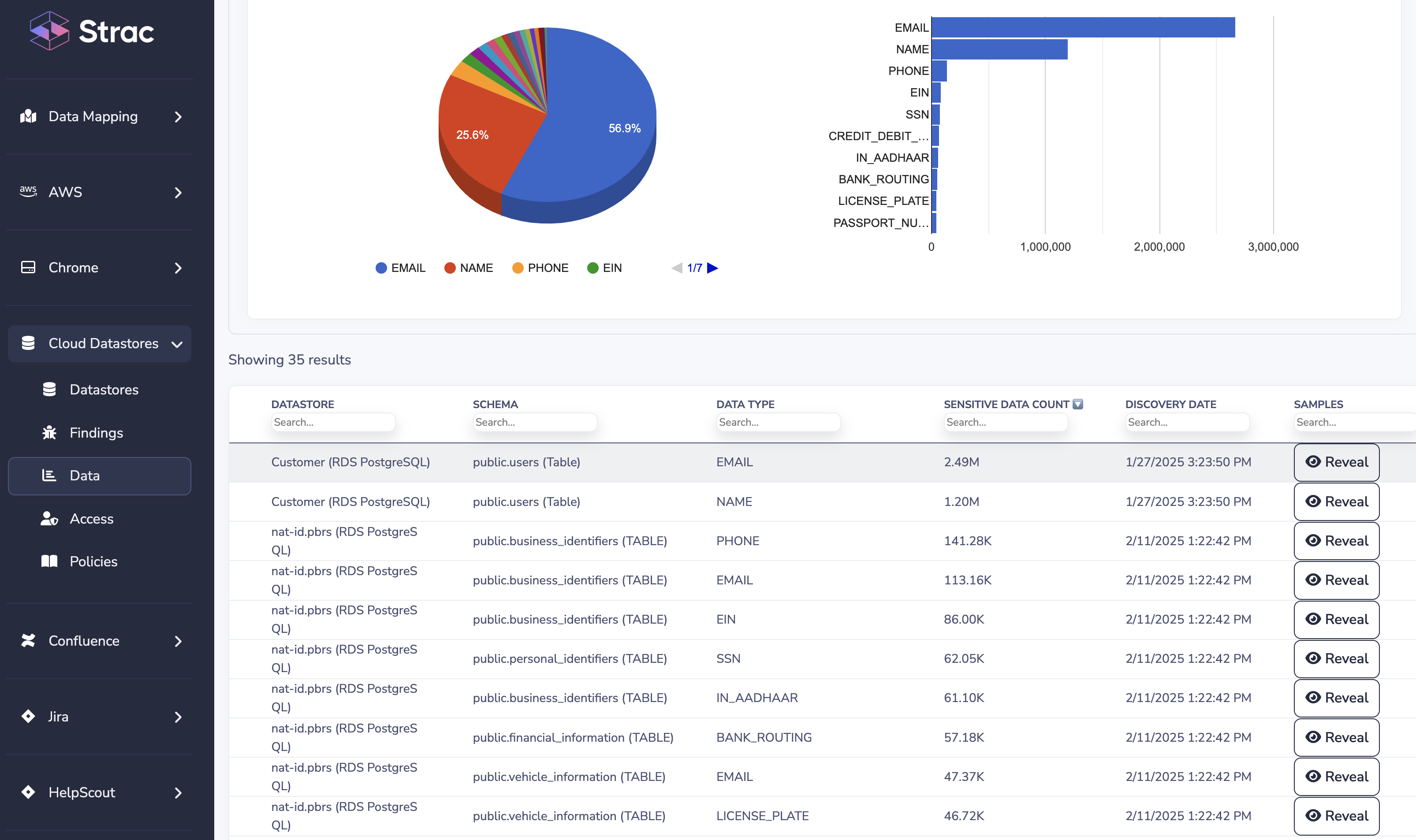
Data Loss Prevention (DLP) in Microsoft Azure refers to the set of security policies, tools, and controls that detect and prevent unauthorized sharing or movement of sensitive data across Azure services. Azure DLP scans data stored in cloud resources such as Azure Blob Storage, SQL databases, and Microsoft 365 apps connected to Azure. It helps organizations safeguard confidential information such as PII, PHI, and financial data through content inspection, policy enforcement, and automated remediation.
With Strac’s agentless DSPM + DLP, teams can extend Azure’s protection beyond the native ecosystem — applying unified data discovery, classification, and real-time redaction across SaaS, Cloud, GenAI, and endpoints.
Azure DLP helps organizations monitor, classify, and restrict access to sensitive information in motion and at rest across the cloud. It automatically detects data patterns like credit card numbers or social security numbers and enforces policies to block sharing, encrypt files, or trigger alerts when violations occur.
For example, an organization can use Azure DLP to:
Strac complements this by providing inline redaction, machine learning–based detection (no regex), and real-time remediation, ensuring sensitive data never leaves your cloud or SaaS ecosystem unprotected.
While both tools address data security, they serve distinct purposes within Microsoft’s ecosystem:
FeatureAzure Information Protection (AIP)Microsoft Purview DLPPrimary FocusData classification and labelingPolicy-based data loss preventionProtection TypeEncrypts and labels dataDetects, monitors, and restricts data sharingCoverageFiles and emails within Microsoft 365 appsCross-cloud and cross-service data activityPolicy EnforcementPersistent file-level protectionReal-time policy enforcementIntegration ScopeLimited to Azure and M365 stackExtends to endpoints and non-Microsoft services
Strac takes this further with unified DSPM + DLP, covering not only Azure and Microsoft 365 but also Slack, Salesforce, Gmail, and GenAI tools, providing a full data security posture across your hybrid environment.
To implement DLP policies effectively in Azure, organizations should follow a phased and automated approach that includes:
Strac simplifies these steps by offering pre-built compliance templates and automated redaction workflows, making Azure DLP implementation faster, smarter, and agentless.
While Azure’s native DLP capabilities are powerful, organizations often face several challenges:
Strac overcomes these gaps with machine learning–powered detection, real-time remediation, and unified visibility across cloud, SaaS, and endpoints — reducing friction while enhancing compliance confidence.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

