Data Discovery and Data Classification: The Complete SaaS Guide for Data Governance
Understand data discovery and classification to enhance data security and manage sensitive data across cloud and hybrid environments.
Data discovery and data classification are the starting point of any serious data security strategy. Before you can protect sensitive information, you need to know where it lives and how critical it is. In most organizations, regulated data is spread across SaaS apps, cloud drives, databases, support tools, and now AI platforms; often without clear ownership or visibility.
Data discovery finds the data. Data classification defines its sensitivity and business impact. This is where modern data classification solutions play a critical role. The right data classification solutions automatically identify PII, PHI, PCI, financial records, and intellectual property across structured and unstructured environments, turning scattered data into something measurable and controllable.
When data discovery and data classification work together, security teams stop guessing and start enforcing real controls. Policies become accurate, compliance becomes provable, and risk becomes manageable.
The importance of Data Discovery and Classification has never been greater. With organizations managing vast amounts of structured and unstructured information across SaaS, cloud, GenAI, and endpoint environments, the ability to locate and label sensitive data determines how effectively you protect it. Companies that prioritize data discovery importance gain not only stronger data security but also strategic control over compliance and decision-making.
Today’s digital landscape is defined by:
By implementing a clear compliance framework and leveraging automation for classification, companies can significantly reduce data exposure and build customer trust. The result is an enterprise that not only complies with regulations but also uses its data securely and intelligently to drive value.
Data classification solutions help you understand what sensitive data you actually have and where it lives. Without classification, DLP and compliance tools are guessing. With it, security becomes intentional and enforceable.
Here’s what strong data classification solutions give you:
Clear visibility into sensitive data
Automatically identify PII, PHI, PCI, financial records, secrets, and IP across SaaS apps, cloud storage, databases, and even AI tools. You cannot protect what you cannot see.
Stronger security controls
Once data is classified, you can apply the right policies; restrict sharing, block uploads, redact content, or limit access based on risk.
Faster compliance
GDPR, HIPAA, PCI-DSS, SOC 2; they all require knowing where regulated data lives. Classification makes audits easier because you have proof, not assumptions.
Lower breach risk
By tagging sensitive data early, you reduce accidental exposure in email, chat, support tickets, data warehouses, and AI prompts.
Better data management
Teams get clarity on what data matters and what does not, which improves governance and reduces sprawl.
In short, data classification solutions turn unknown data risk into something measurable and controllable.
Data Discovery is the foundation of every modern security and compliance strategy. It enables organizations to locate, identify, and understand information across SaaS, cloud, and on-premise systems. With the exponential growth of unstructured data, effective data discovery tools are critical to ensure control, reduce risk, and maintain compliance across an ever-expanding digital landscape.
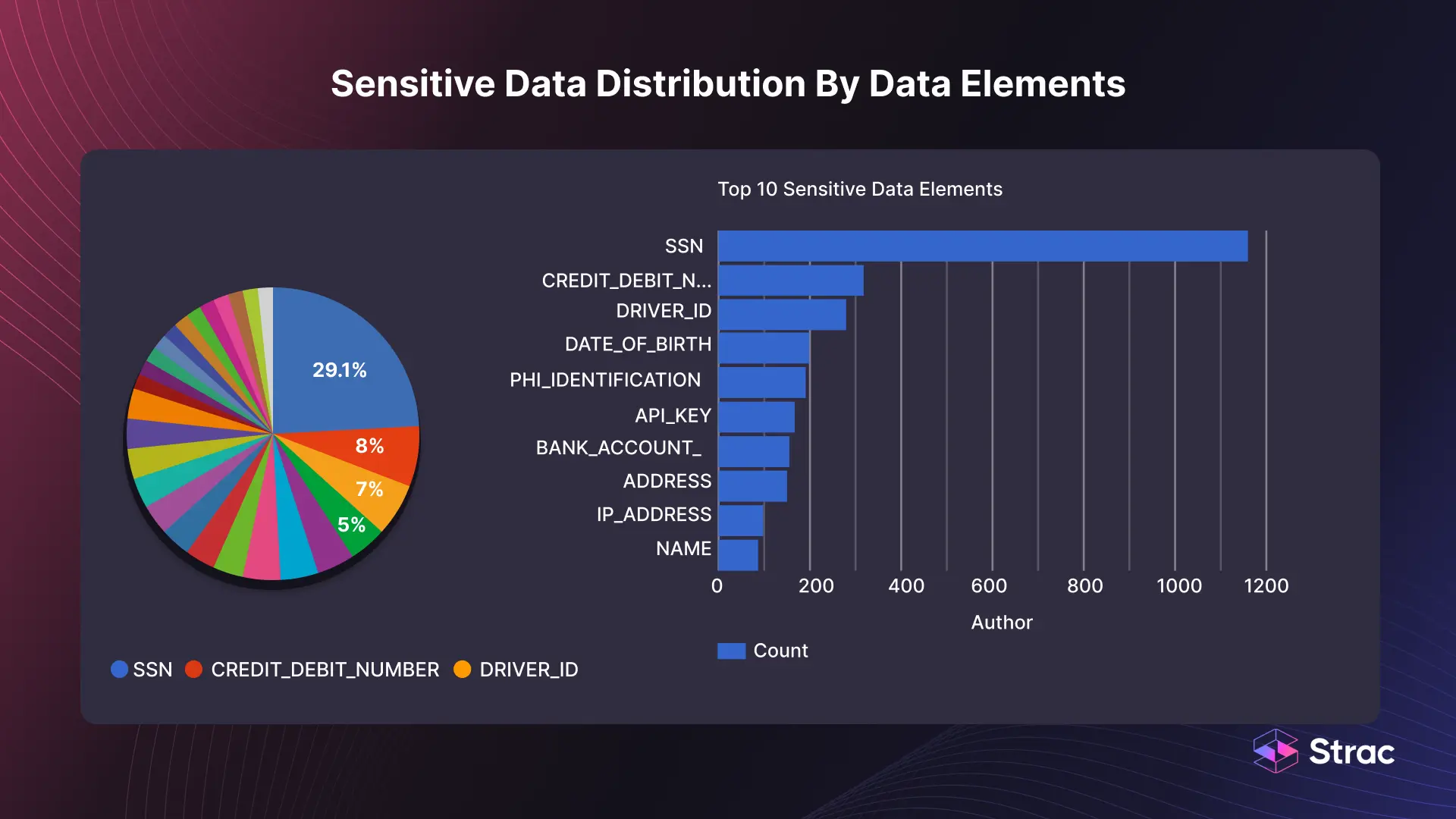
In modern enterprises, Data Discovery refers to the process of finding and understanding where information lives, how it flows, and who has access to it. As part of data governance and enterprise data management, it allows teams to uncover hidden datasets across databases, SaaS apps, and cloud storage. By discovering sensitive data, companies gain clarity over their digital assets and can apply stronger policies to protect them.
Cloud-based discovery has become a necessity for distributed organizations that operate across multiple environments. It provides unified visibility, allowing security teams to detect and manage data wherever it resides; from shared drives to collaboration tools; strengthening both compliance and operational control.
Effective Data Discovery techniques combine technology and strategy to ensure that no sensitive data goes unnoticed. These techniques include metadata scanning, automated system scanning, and metadata analysis, each designed to reveal how and where data moves. Together, they create a living map of an organization’s information ecosystem.
By implementing these data discovery techniques, organizations can ensure that data is not only found but also understood within its context, forming the foundation for better security decisions.
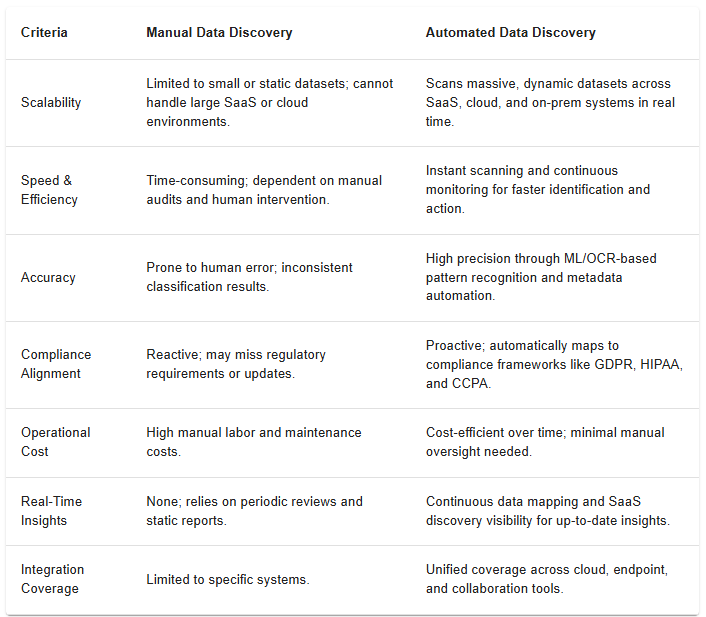
Organizations today face a choice between manual and automated Data Discovery methods. Manual approaches rely on human review and basic reporting, which can be time-consuming and error-prone. In contrast, automated Data Discovery software continuously scans environments to detect and classify information in real time, offering faster and more reliable insights.
Understanding their differences helps businesses align the right approach with their goals for accuracy, compliance, and efficiency.
Below is a clear comparison of Automated vs Manual Data Discovery approaches:
Data Classification is the process of organizing data according to its sensitivity, business value, and regulatory requirements. It allows organizations to identify which information must be most protected and what controls to apply. A well-defined data classification schema helps reduce risk, improve compliance, and strengthen overall data governance across SaaS, cloud, and endpoint environments.
Organizations typically classify information into several sensitivity levels to ensure that data is handled according to its risk and purpose. This structured data classification model simplifies enforcement and communication across departments, ensuring consistent labeling for public, internal, confidential, and restricted information. Properly applied, these data classification types create clarity about what can be shared, stored, or restricted.
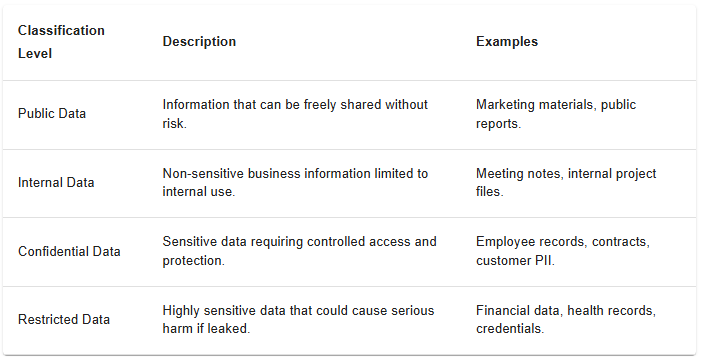
By applying these data classification levels, companies enable secure data labeling and visibility across systems. When every employee understands which data is restricted or confidential, accidental exposure risks drop significantly.
A classification framework is only effective when paired with the right security controls. Mapping each data classification level to protection mechanisms such as encryption, access management, and monitoring ensures proportional defense across all assets. Strong alignment between classification and security enables teams to enforce data protection controls that scale automatically.
When organizations integrate data classification security into workflows, they achieve deeper visibility and control. This ensures sensitive information is protected according to its risk level and regulatory importance.
Compliance depends on understanding the nature and sensitivity of data under protection. Frameworks like GDPR, CCPA, and HIPAA explicitly require organizations to identify and secure personal or regulated data. By implementing a robust data classification system, businesses can demonstrate compliance with privacy laws and avoid costly penalties.
GDPR data classification helps label personal data categories and define retention rules. HIPAA classification ensures that Protected Health Information (PHI) is encrypted and monitored, while CCPA classification supports the right to access and delete consumer data. Together, these structured models make audits smoother and reduce the complexity of maintaining continuous compliance.
Ultimately, data classification bridges the gap between policy and execution, transforming regulatory requirements into actionable safeguards.
While often mentioned together, Data Discovery and Data Classification serve distinct yet complementary purposes within the data governance framework. Discovery focuses on locating and mapping data assets, while classification organizes those assets based on sensitivity and compliance requirements. Together, they create the foundation of modern data management, ensuring visibility, control, and trust across the entire data lifecycle.
Data Discovery is the first step in building a strong data governance framework. It involves identifying data across systems, applications, and storage locations, then creating a comprehensive data inventory that shows where information resides and how it flows. This visibility helps organizations understand their data landscape and detect security or compliance risks early.
Key techniques for data mapping and data cataloging include automated scanning, metadata analysis, and system indexing. These methods reveal hidden or shadow data that traditional tools might overlook. Once discovered, every dataset can be assigned ownership, improving accountability and operational clarity.
After discovery, organizations move into Data Classification, where each dataset is labeled according to its sensitivity and business value. This structured process enables better access control, encryption, and monitoring of sensitive assets. Effective data categorization ensures that the right security measures are applied based on the importance of the data.
Through data classification controls, companies can enforce policies such as “restricted,” “internal,” or “confidential” access, reducing the risk of accidental exposure. Data labeling then provides visual and automated cues that help employees handle information safely and consistently across platforms.
Data Discovery and Classification work best as a unified process. Discovery identifies where data lives, and classification defines how it should be protected. When integrated into a single workflow, they create a powerful unified data management system that bridges visibility with control.
Together, these functions allow organizations to detect sensitive data, apply the right security measures, and continuously monitor compliance. In a mature data governance program, this integration ensures that every asset; whether in SaaS, cloud, or endpoint environments; is both known and properly secured.
Implementing Data Discovery and Classification across a complex IT ecosystem is not without obstacles. As organizations scale and adopt new SaaS, cloud, and endpoint tools, visibility becomes fragmented, creating blind spots and compliance risks. The main data management challenges arise from data sprawl, shadow IT, unstructured data, and regulatory compliance hurdles, all of which require scalable, automated solutions.
One of the biggest obstacles in Data Discovery and Classification is data sprawl; the uncontrolled growth of information across systems, devices, and applications. When employees use unsanctioned tools, it creates shadow IT and “shadow data” that evade monitoring and protection. This lack of visibility leads to significant compliance and security risks.
To manage data sprawl solutions effectively, organizations must centralize visibility and establish automated discovery processes that detect data across authorized and unapproved cloud platforms. Deploying continuous scanning ensures that even unapproved cloud applications are brought under governance without disrupting workflows.
Most corporate data today is unstructured, spread across emails, chat messages, PDFs, spreadsheets, and multimedia files. This type of data is harder to analyze, classify, and secure compared to structured records. Without automated tools, unstructured data classification becomes an overwhelming manual task prone to inaccuracy.
By applying sensitive data handling practices and using ML/OCR-driven discovery, organizations can locate and classify unstructured content in real time. Solutions that integrate data protection for unstructured data across SaaS and endpoint environments drastically reduce the risk of leaks, especially in tools like Slack, Google Drive, and Zendesk.
Static classification processes quickly become outdated in fast-changing digital environments. To maintain relevance and accuracy, organizations must adopt scalable data classification that updates automatically as data is created, modified, or shared. Manual reviews can’t keep pace with modern data velocity.
Continuous classification relies on automation and machine learning to track changes in real time. These automation in classification systems deliver ongoing visibility and policy enforcement, ensuring consistent protection and compliance. By embracing real-time classification updates, companies can safeguard sensitive information without operational bottlenecks.
Hybrid infrastructures; combining on-premise, private cloud, and public cloud systems; create major challenges for data discovery and classification. Data is often dispersed across multiple environments with different governance and security protocols. Managing hybrid IT systems requires unified visibility that bridges all environments under one compliance lens.
Through hybrid cloud data discovery, organizations can monitor data flows across applications, APIs, and endpoints from a single pane of glass. Multi-cloud classification ensures consistent policy application, regardless of where data lives, helping organizations maintain compliance and control in even the most complex hybrid ecosystems.
Successful Data Discovery and Classification depend on structure, automation, and continuous improvement. Implementing a phased approach allows teams to establish clear visibility, apply appropriate security measures, and evolve alongside changing compliance requirements. These data governance strategies form the foundation of long-term data protection and operational excellence.
Every data protection journey begins with an accurate data inventory. Organizations must first locate and understand where information resides across SaaS platforms, cloud storage, databases, and endpoint systems. Without full visibility, it’s impossible to apply consistent policies or detect risks.
Scanning data sources using automated discovery tools ensures no dataset remains hidden. Through cloud discovery and SaaS data scanning, teams gain a single, consolidated map of all information assets. This foundation supports every downstream process from classification to compliance tracking.
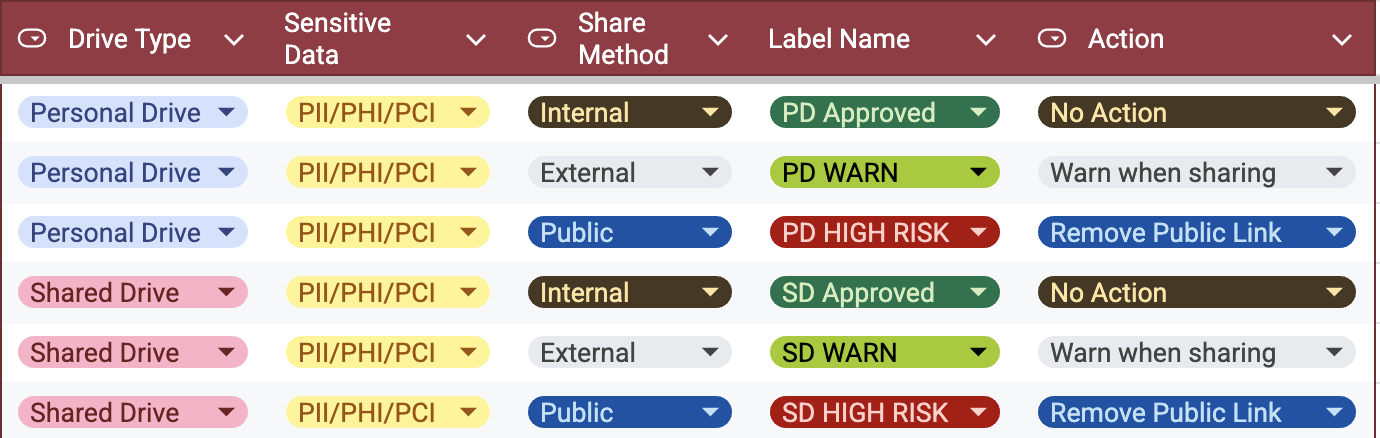
Once discovered, data must be categorized according to its sensitivity, purpose, and regulatory impact. This stage translates visibility into actionable control by assigning sensitivity labeling and structured categories such as “Public,” “Internal,” “Confidential,” or “Restricted.”
A well-defined data classification schema ensures consistent labeling across tools, while classification tools automate the process to reduce human error. The goal is to make every piece of data easily recognizable by its importance and to guide users and systems in applying the correct security measures automatically.
With classification in place, security must follow. Each category of data should correspond to specific security controls that enforce access restrictions and data protection rules. This phase connects governance frameworks to technical safeguards that prevent misuse or unauthorized access.
Key measures include data encryption, conditional access, and policy enforcement for sharing and retention. Strong data access management ensures sensitive files remain visible only to authorized users, while automated retention policies keep compliance efforts aligned with data lifecycle requirements.
Data security isn’t static; it requires ongoing visibility. Once controls are implemented, organizations must maintain continuous data monitoring and generate real-time reporting to detect changes or anomalies. These insights help verify compliance and ensure that classification rules remain relevant.
Automated audits and compliance tracking tools make it easier to identify where sensitive information moves or changes status. With proactive monitoring, teams can prevent data leaks before they occur and continuously adapt policies to the evolving threat landscape.
The final phase of an effective strategy is maintenance. Over time, business models, data types, and regulations evolve, making it essential to update classification schemas regularly. Stale classification frameworks often create compliance blind spots and missed security opportunities.
Through regular audits, teams can validate the accuracy of existing labels, adjust to new compliance standards, and optimize their approach to risk management. Conducting data security audits at defined intervals ensures every layer of protection remains strong, modern, and aligned with organizational goals.

By following this phase-by-phase model, organizations can move from reactive to proactive data management. Combining automation, structured labeling, and consistent policy updates ensures that every piece of data; no matter where it lives; is continuously protected, compliant, and actionable.
In modern data ecosystems, manual processes can’t keep pace with the speed, scale, and complexity of information movement. Data discovery automation is now essential for ensuring every file, message, and record is identified and secured instantly. By combining automation with AI-driven intelligence, organizations achieve faster results, higher accuracy, and greater resilience across cloud, SaaS, and endpoint environments.
Manual discovery processes are slow, fragmented, and easily outdated. Automation transforms this by enabling continuous scanning, indexing, and automated data identification across every connected system. With intelligent engines that work around the clock, organizations gain real-time awareness of where their data resides and how it moves.
AI-driven data discovery tools eliminate the need for repetitive, error-prone searches, detecting sensitive data even in hidden or siloed environments. This level of efficiency not only reduces operational overhead but also shortens response times when incidents occur. The result is smarter visibility and stronger protection with minimal manual intervention.
AI and machine learning for classification revolutionize how organizations label and protect data. Traditional methods rely on static rules or regex patterns that fail to capture nuanced data types. Intelligent automation replaces these with smart classification models that continuously learn from patterns, user behavior, and past outcomes.
AI data classification and automated labeling ensure consistent, context-aware tagging across structured and unstructured datasets. These systems adapt over time, improving accuracy and reducing false positives. By combining automation with human oversight, businesses gain both precision and agility in protecting sensitive information.
Compliance is no longer a periodic checklist; it’s an ongoing process that must be continuously validated. Automated compliance reports simplify this by tracking every discovery and classification event in real time. Through integrated data audit automation, organizations can instantly generate evidence for audits and regulatory reviews.
Automation tools transform regulatory reporting from a reactive task into a proactive advantage. Compliance tracking software continuously monitors policy adherence and highlights anomalies before they escalate into violations. By embedding automation into compliance workflows, companies save time, reduce costs, and maintain audit-ready posture at all times.

Modern cybersecurity strategies must be built around data visibility and control. Integrating Data Discovery and Classification directly into the data security framework ensures that every asset is continuously monitored, labeled, and protected within your broader defense posture. By linking discovery and classification with DLP, SIEM, and posture management tools, organizations can create a unified layer of intelligence that drives real-time detection, prevention, and compliance.
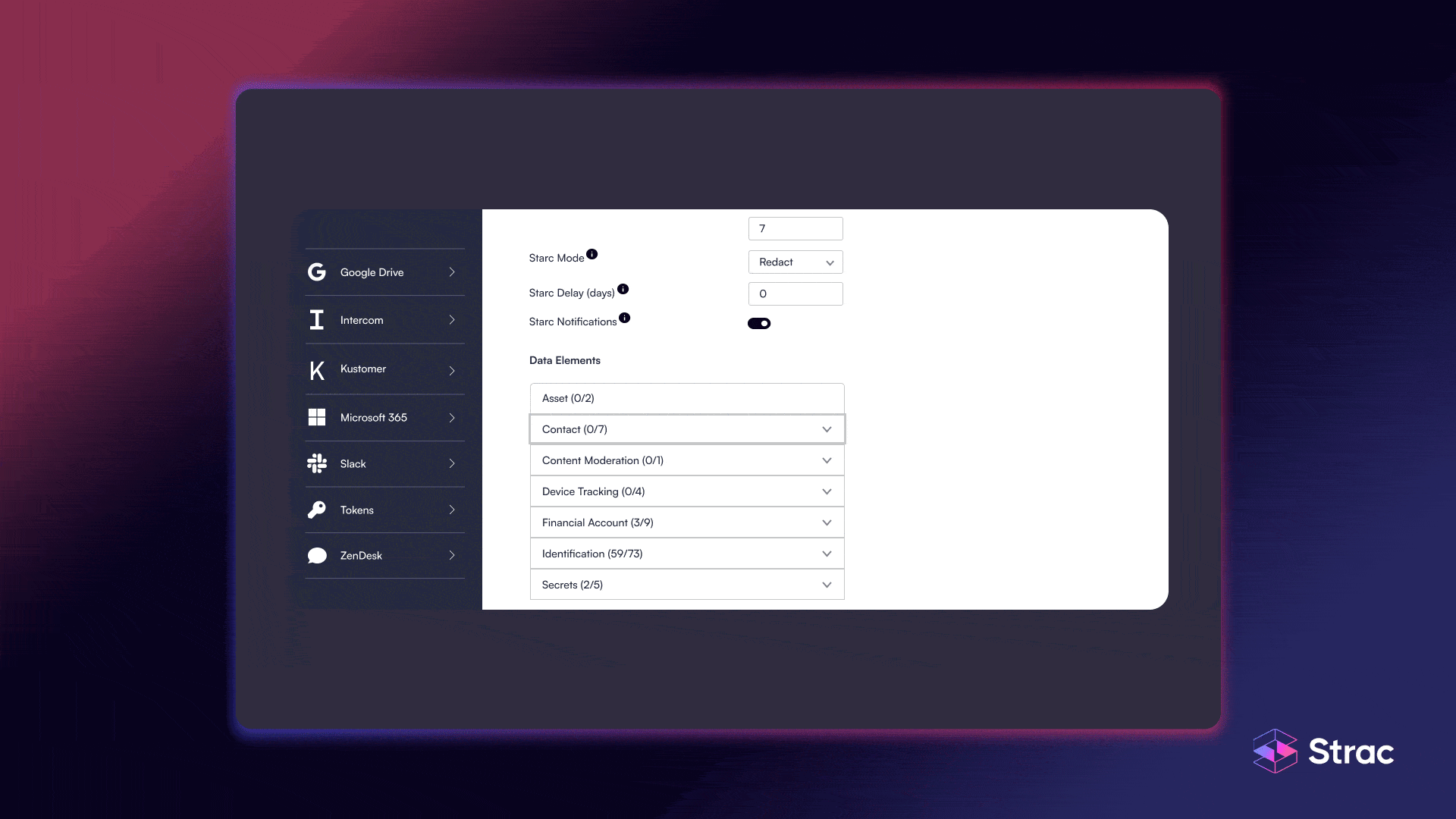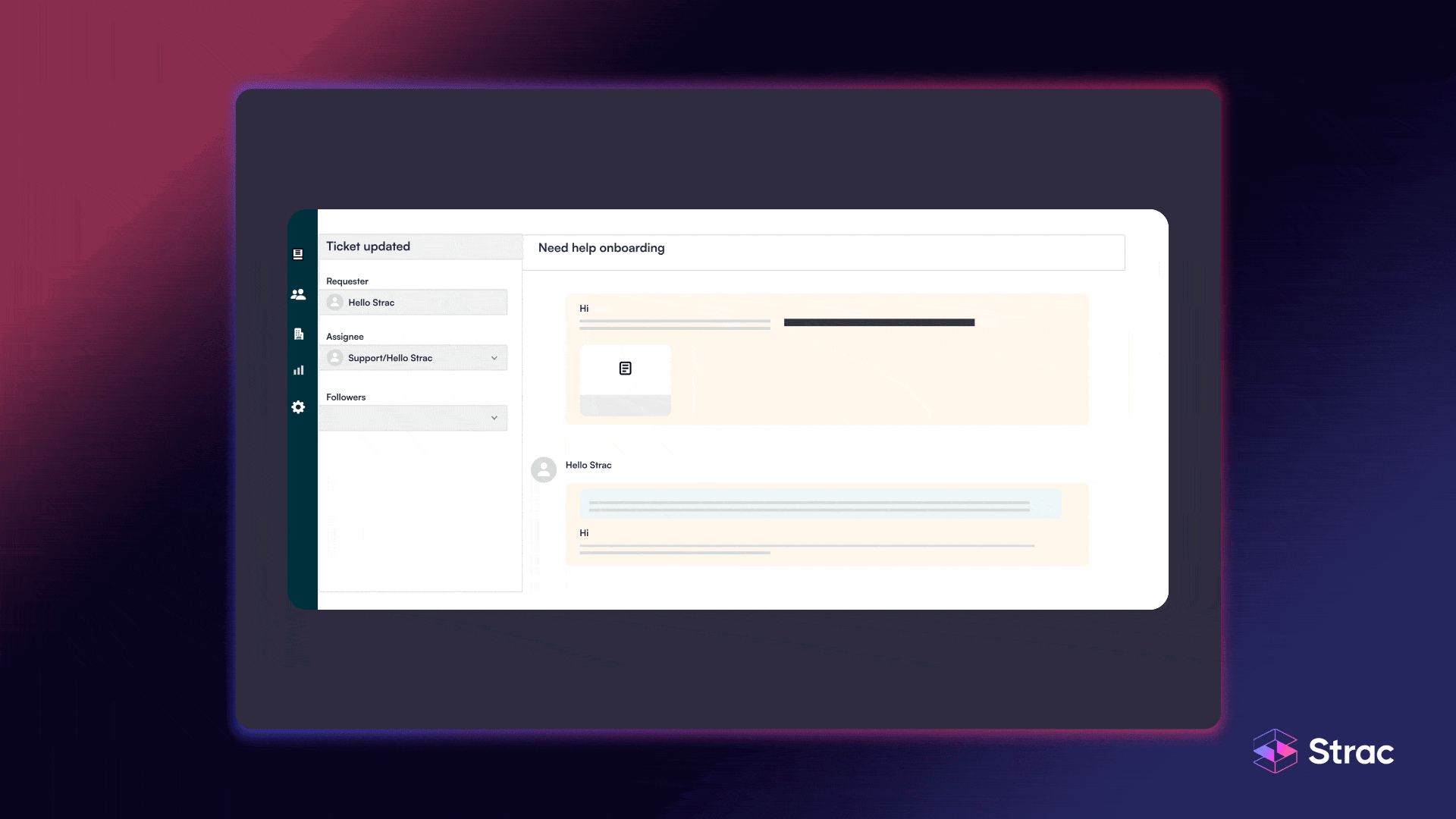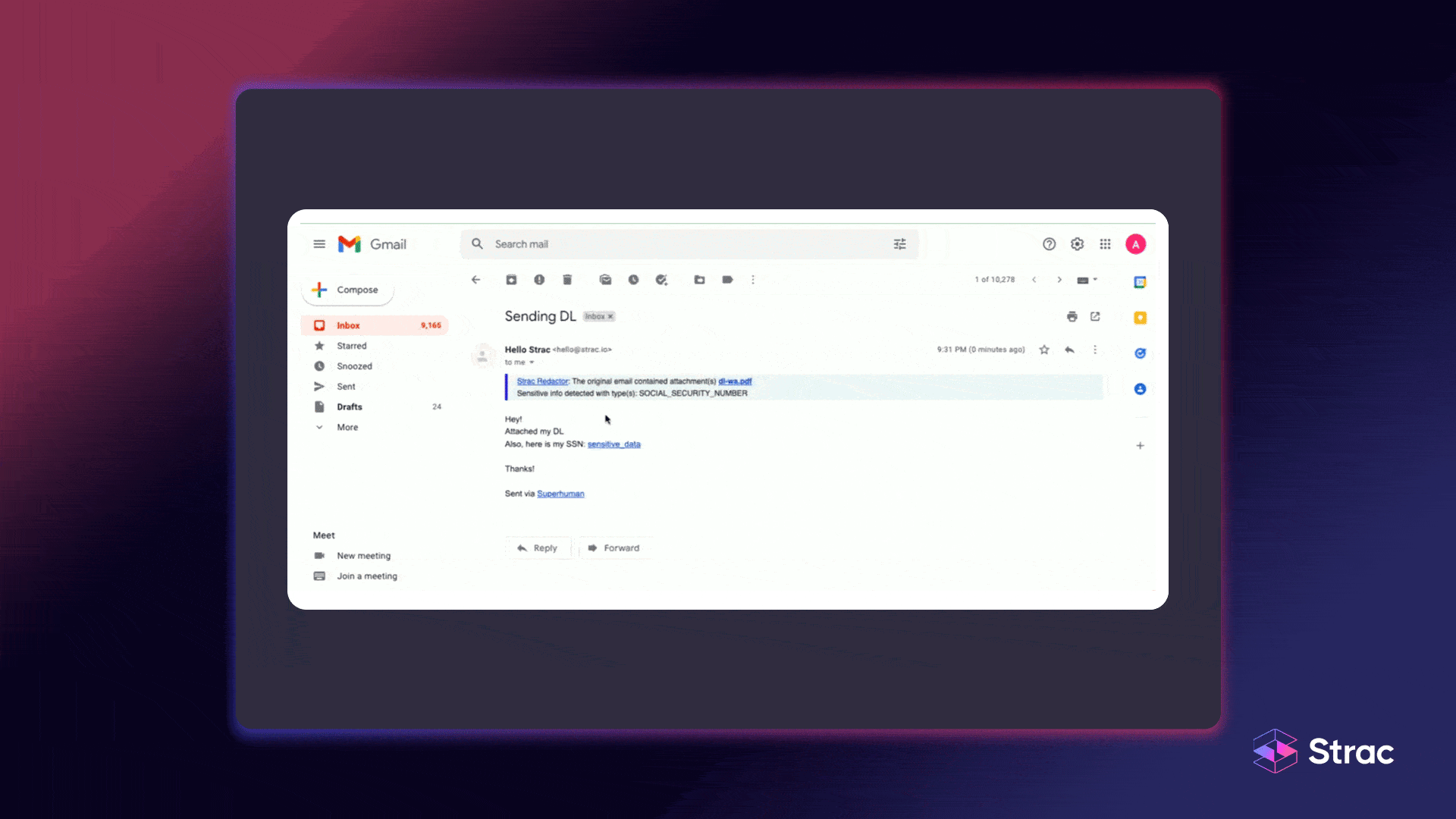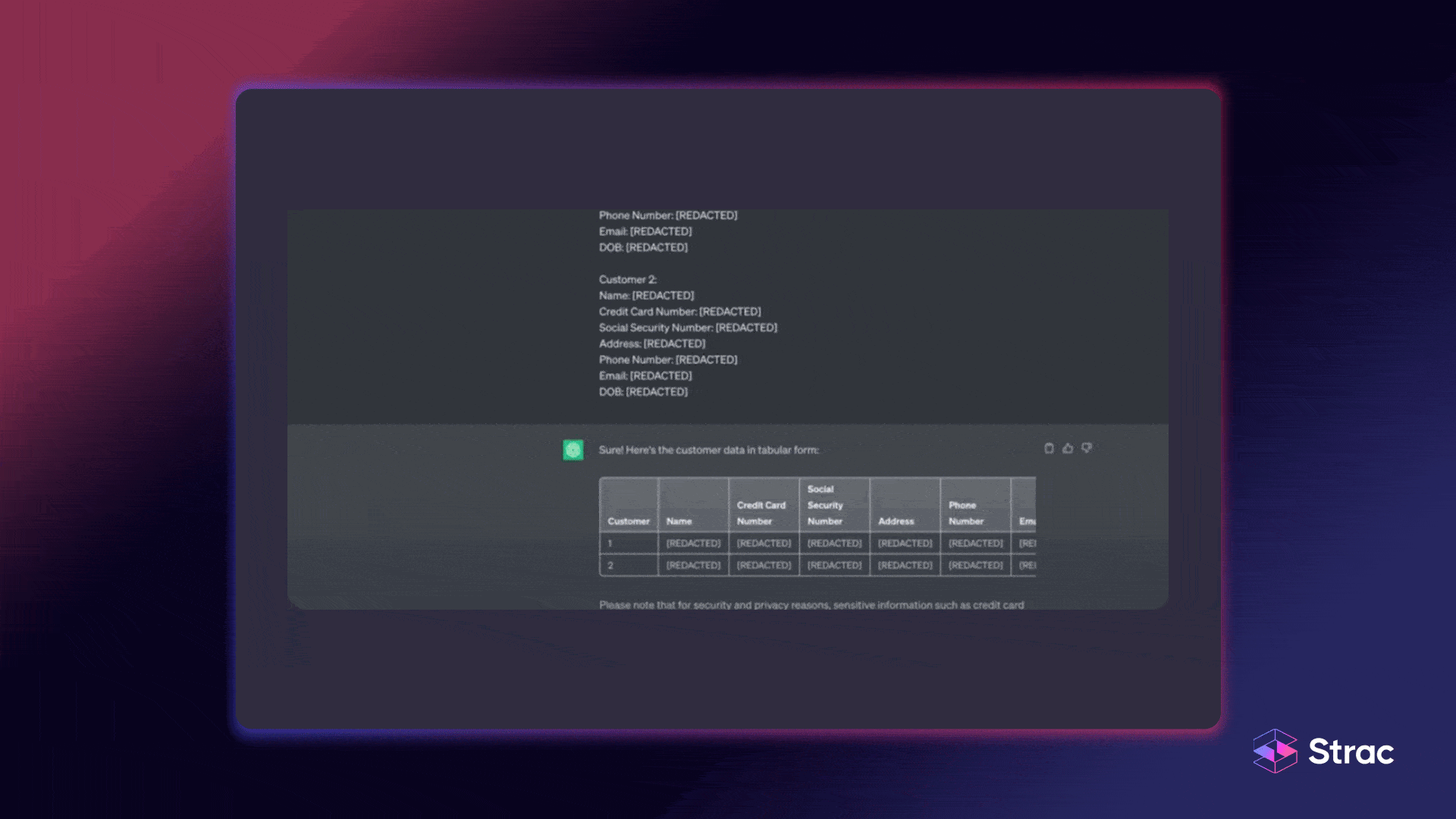
The power of data discovery integration lies in how it connects seamlessly with existing security systems. By embedding discovery and classification processes into DLP, SIEM, and CASB tools, organizations can automatically detect, label, and respond to sensitive data risks without human intervention. This not only accelerates incident response but ensures data protection remains consistent across every platform.
For example, integrating data discovery with DLP and SIEM allows for immediate action when sensitive data appears in unauthorized locations. DLP policies can redact or block exposures in real time, while SIEM systems correlate these events with broader threat intelligence. The result is a unified data security integration workflow that reduces complexity and increases precision.
A strong data-centric security strategy begins with knowing what data you have and how sensitive it is. Data classification provides the context that allows security systems to prioritize protection efforts intelligently. By aligning classification with encryption, identity management, and privacy policies, organizations can strengthen their security posture from the inside out.
When classification data flows directly into security controls, automated systems can adjust access rights, trigger alerts, or enforce data privacy controls based on sensitivity levels. This alignment ensures that resources are focused on protecting the most valuable and high-risk assets, creating a balanced and resilient defense model.
Incorporating data discovery into the risk management framework transforms security from reactive to predictive. Discovery tools identify where sensitive data resides, how it’s accessed, and where it may be at risk. This visibility helps organizations perform more accurate risk assessments and apply targeted controls that reduce potential exposure.
When integrated with risk control frameworks, continuous discovery creates a dynamic map of data behavior and movement. This enables teams to detect anomalies faster, prioritize remediation, and adapt strategies based on real-world usage patterns. As a result, data risk management evolves from a static checklist into a live, intelligence-driven process.
Data Discovery and Classification are not abstract security practices; they deliver measurable results across real business operations. Whether it’s preparing for a GDPR audit, managing a cloud migration, or maintaining continuous privacy compliance, organizations rely on these capabilities to reduce exposure and enhance governance. The following use cases illustrate how structured discovery and classification translate into tangible outcomes in regulated industries.
Real-World Context:
A healthtech or fintech company stores sensitive data like medical records or sensitive data across SaaS platforms (like Google Drive, Salesforce, Zendesk) and cloud storage (like S3, RDS, Azure Blob).
Use Case:
✅ Why it matters: Avoid fines, reduce audit fatigue, and stay compliant.
Real-World Context:
Employees copy-paste sensitive data in Slack or share sensitive customer info in Confluence pages, which remain there indefinitely.
Use Case:
✅ Why it matters: Keeps collaboration tools from becoming data breach liabilities.
Real-World Context:
Customer data flows from apps like Salesforce → Snowflake or BigQuery for analytics. Security tightened one place doesn’t protect the rest.
Use Case:
✅ Why it matters: Prevents data leakage through business intelligence or reporting pipelines.
Real-World Context:
A departing employee bulk downloads or uploads sensitive reports or customer files to a personal email, AirDrop, USB, or ChatGPT.
Use Case:
✅ Why it matters: Prevents theft of trade secrets, customer data, or regulated information.
Real-World Context:
Customers request to know what personal data a company holds on them or to delete it entirely. This includes emails, attachments, chat logs, and support files.
Use Case:
✅ Why it matters: Avoids non-compliance penalties and builds customer trust.
Modern organizations need more than visibility; they need precision and automation. Strac brings intelligence, scalability, and speed to every stage of Data Discovery and Classification. Built for SaaS, cloud, GenAI, and endpoint ecosystems, Strac enables real-time visibility and protection without disrupting
Strac.io unifies data discovery, classification, and remediation within a single agentless platform. Every process is built to automatically identify, label, and secure sensitive data wherever it resides, ensuring organizations maintain compliance and control.
Key Strac features include:
By combining these capabilities, Strac eliminates visibility gaps, minimizes manual overhead, and provides a scalable foundation for modern data governance.
A key advantage of Strac.io is how easily it integrates with your existing security tools. Whether your organization uses DLP, SIEM, or CASB solutions, Strac extends their capabilities by embedding real-time discovery and automated classification into the workflow.
Strac integrates seamlessly with:
This integration ensures consistent visibility and unified security across all environments, strengthening your overall data security framework.
Unlike traditional tools that require complex configuration, Strac offers a fast, frictionless onboarding experience. Its agentless, no-code architecture allows organizations to deploy automation within hours and start discovering and classifying data immediately.
Implementation steps include:
Getting started with Strac means instant visibility, accurate classification, and continuous compliance; a modern solution that scales with your business and keeps your data secure across every channel.
Modern organizations generate more data than ever before, making security a moving target. Without visibility and control, sensitive data becomes a liability; one breach or compliance lapse can cause financial and reputational damage. Implementing Data Discovery and Classification gives businesses the tools to stay ahead, ensuring every file, message, and record is accounted for, labeled correctly, and protected consistently.
Strac.io simplifies this journey through automation. With AI-driven discovery, real-time classification, and agentless deployment, it brings visibility, security, and compliance under one roof. Companies using Strac gain measurable control over their data while freeing teams from manual processes. The result is smarter governance, stronger protection, and a scalable security posture built for the future.
Data discovery is the process of locating, identifying, and understanding all data within an organization’s ecosystem; from SaaS and cloud apps to on-premise databases and endpoints. It helps businesses uncover where their sensitive information resides, how it flows, and who has access to it. Without this visibility, organizations risk compliance violations, data leaks, and poor decision-making.
By implementing automated data discovery, businesses can detect vulnerabilities early, improve regulatory readiness, and build stronger data governance foundations. It turns unknown data into controlled assets, empowering organizations to reduce risk and operate with confidence.
Data classification strengthens security by organizing information according to its sensitivity and business importance. When data is properly labeled; for instance, as public, internal, confidential, or restricted; teams can enforce security controls that match the associated risk level. This ensures that sensitive data is encrypted, access is limited, and usage is continuously monitored.
The benefits of an effective classification strategy include:
In essence, classification transforms data visibility into actionable security posture, turning policy frameworks into real-time protection.
Although data discovery and data classification are closely connected, they serve distinct purposes within a data governance framework. Discovery identifies where data lives and what it contains; classification determines how that data should be protected based on its content and context.
Discovery delivers the visibility that every security strategy depends on, while classification enforces the control that keeps information secure. Together, they form a complete lifecycle; discovery finds the data, classification defines its sensitivity, and both inform how it should be stored, shared, or deleted.
Automation is essential for managing data across hybrid and cloud ecosystems where information changes constantly. The right tools combine AI-driven discovery with automated classification to continuously identify and secure sensitive content at scale. Manual approaches can’t provide the speed or accuracy that modern compliance demands.
Some leading solutions include:
Among these, Strac offers the most comprehensive and unified coverage — combining discovery, classification, and inline remediation into one seamless platform designed for modern cloud-first organizations.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

