AI Data Security Platforms: How to Evaluate & Deploy the Right Platform
Learn what AI data security platforms do, how they differ from point tools, and how to evaluate, deploy, and scale them securely.
1. AI data security platforms are enforcement systems, not monitoring tools. They discover, classify, and actively control sensitive data across AI prompts, responses, SaaS apps, APIs, and cloud workflows; stopping exposure before it happens.
2. Traditional DLP, DSPM-only tools, CASB, and AI gateways all leave gaps. These tools were not designed for unstructured, real-time AI data flows and typically rely on alerts or visibility instead of inline prevention.
3. Architecture matters more than feature lists. The strongest platforms unify discovery, AI-aware classification, and real-time enforcement in a single system rather than stitching together point solutions.
4. Real-time enforcement is the key differentiator. Redaction, masking, blocking, and quarantine at prompt-time and response-time are what prevent AI data leakage at scale; alert-only approaches do not.
5. Agentless, API-native deployment enables faster time to value. Modern AI data security platforms can deploy in days, minimize engineering effort, and scale as AI adoption grows without adding operational drag.
6. Compliance readiness now includes AI workflows. Regulators increasingly expect reasonable safeguards for AI-driven data processing; platforms that generate real enforcement evidence reduce audit friction and actual risk.
AI adoption has moved faster than most security architectures can adapt. Sensitive data now flows through prompts, copilots, SaaS apps, APIs, and automated workflows; often outside the visibility and control of traditional tools. This shift is why ai data security platforms have become a distinct category: not to document AI risk, but to prevent data exposure before it reaches AI systems.
This guide is written for security, privacy, and engineering leaders actively evaluating solutions. It focuses on what actually qualifies as an AI data security platform, where legacy tools fall short, how to evaluate vendors based on real-world AI data flows, and how to deploy protection quickly without slowing teams down. Throughout the guide, platforms like Strac are used as concrete examples of enforcement-first AI data security done right.
AI data security platforms are purpose-built systems designed to discover, classify, monitor, and enforce controls on data as it flows into, out of, and within AI systems. Unlike legacy security tools that were adapted after the fact, these platforms are built for modern AI data paths; including prompts, responses, training datasets, embeddings, logs, and file attachments. Their core goal is preventive enforcement: stopping sensitive data exposure before it reaches AI models or leaves controlled environments.
At an operational level, AI data security platforms sit at the intersection of SaaS applications, APIs, cloud data stores, and generative AI tools. They inspect data in motion and at rest, understand its sensitivity, and apply real-time actions such as redaction, masking, blocking, or quarantine. This approach reflects how AI is actually used in production environments today; not as an isolated model, but as a layer embedded across business workflows.
To qualify as a true ai data security platform, a solution must go beyond policy documentation or alerting. It should combine four foundational capabilities into a single system:
Tools that only observe AI usage or log prompts without enforcement fall short of this definition. They may be AI-aware, but they are not AI-secure.

AI data security platforms are designed to cover the full lifecycle of AI-related data, not just training datasets. In real-world environments, risk emerges from many less obvious places. Effective platforms protect:
This expanded scope is critical. Many data leaks occur not during model training, but during everyday usage; when employees paste customer data into prompts, upload CSVs into AI assistants, or automate workflows that pass sensitive context to external models.
A defining characteristic of modern ai data security software is that it protects data outside the model itself. AI does not operate in isolation. It is embedded in tools like Slack, Gmail, Salesforce, Zendesk, cloud storage platforms, internal APIs, and support systems.
As a result, AI data security platforms must secure:
This is where point solutions often fail. Traditional DLP may focus on email or endpoints, while AI gateways may only proxy prompts to specific models. A platform approach ensures coverage across the entire AI-enabled workflow.
Many vendors now claim AI support, but there is a meaningful distinction between being AI-aware and being AI-secure. AI-aware tools can detect that AI is being used or log interactions. AI-secure platforms actively prevent sensitive data exposure.
AI-aware tools typically:
AI-secure platforms, by contrast:
This difference matters in buyer evaluation. Alert-only tools increase operational burden and leave remediation to humans. AI data security platforms are designed to reduce risk automatically, without slowing down engineering or business teams.
AI data security platforms sit alongside; and increasingly unify; capabilities traditionally split across DLP, DSPM, CASB, and AI gateways. Rather than replacing every control, they provide a single enforcement layer focused on AI-related data flows.
Platforms like Strac exemplify this approach by combining data discovery, classification, and real-time remediation across SaaS, cloud, and generative AI workflows. The emphasis is not on visibility alone, but on enforcing data protection policies at the exact points where AI introduces new risk.
As organizations scale AI usage, this platform model becomes essential. Security teams cannot rely on fragmented tools or manual reviews. They need systems that understand how data moves through AI-enabled environments and can act instantly when risk appears.
In the next section, we will examine how AI data security platforms differ from traditional point tools; and why legacy DLP, CASB, DSPM, and AI gateways often fall short when applied to real-world AI data flows.
AI adoption is accelerating faster than most security architectures can adapt, and this mismatch is creating material ai data security challenges across enterprises. Tools designed for a perimeter-based world struggle to protect data once it enters AI-driven workflows, where context is fluid, data is unstructured, and enforcement must happen in real time. This gap explains why many organizations experience ai data leakage even after investing heavily in legacy security stacks.
Traditional DLP solutions were designed to inspect structured, predictable channels such as email, file transfers, and endpoint activity. Their detection logic assumes known formats and linear data movement, which breaks down when applied to AI usage. AI prompts, responses, embeddings, and chat-based workflows do not resemble classic DLP inspection points.
As a result, legacy DLP often fails when:
Even when detection occurs, enforcement typically happens after the fact. By the time an alert fires, the data has already been sent to an external model or stored in logs.
DSPM tools play an important role in identifying where sensitive data lives and who has access to it. However, most DSPM platforms stop at posture assessment. They show exposure but do not intervene when data is actively used in AI workflows.
This creates a critical ai security gap. Visibility alone cannot prevent leakage when:
Without inline enforcement, DSPM insights remain advisory. Security teams are forced to rely on downstream remediation or policy updates, neither of which stop immediate data exposure.
CASB tools and AI gateways attempt to control access to cloud apps or proxy traffic to specific AI models. While useful in limited scenarios, they struggle with the distributed reality of AI usage. AI interactions often occur inside SaaS applications, internal tools, and embedded copilots that do not route cleanly through a single gateway.
Common blind spots include:
Because these interactions bypass traditional control points, CASB and gateway-based approaches frequently miss the moments where sensitive data actually enters AI systems.
Perhaps the most damaging limitation of traditional tools is their reliance on alerts rather than action. As AI usage scales, so does alert volume. Security teams are flooded with notifications about risky behavior they cannot realistically triage in real time.
This leads to:
Preventive, inline enforcement changes this dynamic. Instead of notifying teams after exposure occurs, AI data security platforms stop sensitive data at the point of use; redacting, masking, or blocking it automatically without interrupting productivity.
European guidance increasingly treats AI as a major amplifier of privacy and data protection risk. ENISA has specifically warned that AI, and machine learning in particular, creates significant challenges for personal data protection; which is why safeguards must be operational and built into workflows, not left to policy and after-the-fact monitoring.
These gaps are no longer theoretical. They appear daily in production environments:
Each scenario represents a failure of traditional controls to adapt to AI-native data flows. Together, they explain why organizations are moving beyond point solutions toward unified AI data security platforms that combine visibility with real-time enforcement.

When evaluating ai data security platforms, feature checklists are misleading. Most vendors can claim detection, dashboards, or policy support. What actually separates effective platforms from incremental tools is architecture; how discovery, classification, and enforcement are designed to operate together in real time across AI-driven workflows. Strong ai data protection capabilities are not bolted on; they are built into the data path itself, before risk materializes.
Sensitive data discovery is the foundation of all ai data security tools, but AI environments dramatically expand what “discovery” must cover. Data no longer lives only in databases or file systems; it flows continuously through SaaS apps, APIs, collaboration tools, and AI interfaces.
Effective platforms provide:
One-time audits or periodic scans cannot keep up with AI usage. Discovery must be ongoing, adaptive, and embedded into the same surfaces where AI operates daily.
Discovery without intelligent classification creates noise instead of protection. AI data security platforms must understand data contextually, not just match patterns. This is where true ai data security features emerge.
Core requirements include:
Regex-only approaches struggle in AI environments due to high false positives and missed context. AI-aware classification ensures that enforcement decisions are accurate, explainable, and actionable.
The defining capability of an AI data security platform is enforcement. Alerting alone does not prevent ai data leakage. In AI-driven systems, action must occur inline, at the exact moment data is used.
Platforms must support:
Alert-only tools fail because AI workflows move faster than human response cycles. Inline remediation shifts security from reactive to preventive, reducing risk without disrupting productivity.
AI data security platforms must explicitly support generative AI and LLM usage, not treat it as an edge case. This requires controls that understand how AI systems are actually consumed by users and applications.
Key capabilities include:
Without this coverage, organizations are blind to some of the highest-risk data paths in modern environments.
Finally, leading ai data security platforms unify DSPM and DLP into a single system. Visibility without enforcement creates risk awareness but not risk reduction. Enforcement without visibility creates blind spots.
A unified architecture delivers:
Platforms such as Strac follow this model by combining continuous data discovery, AI-aware classification, and real-time remediation across SaaS and generative AI workflows. This architectural approach is what enables scalable, enforceable AI data security without adding friction for engineering or business teams.
Security leaders evaluating AI data security platforms should treat AI risk as a lifecycle problem; not a one-time control. The NIST AI Risk Management Framework reinforces this risk-based approach by emphasizing trustworthy AI through governance, measurement, and ongoing risk management across design, deployment, and use.
When buyers evaluate AI data security platforms, the goal should not be checkbox compliance or marketing claims. The real differentiators are how quickly a platform reduces real AI data risk and how much operational friction it introduces. In production environments, security controls that slow developers or block legitimate AI usage are ignored or bypassed; controls that enforce protection invisibly are adopted and scaled.
The following framework provides a practical, buyer-focused ai security vendor comparison grounded in real-world AI data flows.
Coverage determines whether a platform can protect AI usage as it exists today, not as vendors assume it exists. AI data flows rarely stay within a single tool or model.
Evaluate whether the platform supports:
Gaps in coverage create false confidence. If sensitive data can bypass inspection by moving through an unsupported app or API, the platform will not reduce risk meaningfully.
Detection quality directly impacts trust and adoption. Platforms that generate excessive false positives are often disabled; platforms that miss sensitive data create silent exposure.
Assess:
High-quality detection is essential for enforcing policies without disrupting workflows.
Enforcement is where most tools fail. Visibility without action does not prevent ai data leakage.
Buyers should confirm:
If enforcement requires manual intervention or delayed workflows, the platform will not scale with AI adoption.
Deployment friction determines time-to-value and long-term maintainability. Complex deployments slow adoption and increase cost.
Key considerations include:
Agentless, API-native platforms typically deploy faster and are easier to scale across SaaS and AI surfaces.
AI workflows are highly sensitive to latency. Even small delays can degrade user experience and discourage adoption.
Evaluation should include:
Security controls must operate inline without becoming a bottleneck.
AI environments introduce frequent policy changes. Buyers need systems that allow rapid iteration without complex reconfiguration.
Strong platforms offer:
Opaque or fragmented policy models increase risk and operational burden.
While compliance should not drive architecture, it remains a buying requirement. Platforms must generate defensible evidence.
Confirm support for:
Audit capabilities should reflect actual enforcement, not just policy intent.
AI usage expands quickly. Platforms that work for a pilot often fail at scale.
Buyers should evaluate:
Platforms like Strac are designed around scalability by combining agentless deployment, real-time enforcement, and unified policy management across SaaS and generative AI workflows.
In the next section, we will walk through what deployment and rollout actually look like; including timelines, ownership models, and how teams can enforce AI data security without slowing innovation.
When teams think about ai data security deployment, fear often comes from past experiences with heavyweight security tools. Long rollout cycles, intrusive agents, and frustrated users have trained buyers to expect disruption. Modern AI data security platforms are designed differently. The right deployment model minimizes engineering effort, accelerates time to value, and enforces protection without changing how people work.
The deployment model is one of the most important architectural decisions in an ai security rollout. It directly impacts speed, coverage, and long-term maintenance.
Agent-based approaches typically:
Agentless platforms, by contrast:
While agents can offer deep endpoint control, they are poorly suited for modern AI usage that lives primarily in SaaS applications, cloud platforms, and LLM APIs. For most organizations, agentless coverage aligns better with how AI is actually consumed.
Speed matters in AI security. Every week without enforcement increases exposure. Buyers should understand what “time to value” really looks like in practice.
In mature AI data security platforms:
Operational overhead should decrease over time, not increase. Platforms that require ongoing tuning, rule maintenance, or manual triage often become shelfware as AI usage grows.
Security that disrupts workflows will be bypassed. AI adoption succeeds when protection is invisible to end users.
Effective platforms:
Balancing security and productivity is not a trade-off when enforcement is built into the data path. This is why buyers increasingly favor platforms that protect AI usage quietly, rather than policing it loudly.
Many AI security initiatives fail for predictable reasons. These failures are rarely caused by user behavior; they are the result of architectural mismatches between tools and AI workflows.
Common pitfalls include:
AI data security failures are almost always architectural, not human. When platforms are designed to prevent exposure automatically, user behavior becomes far less relevant.
Understanding the difference between ai data security solutions and point tools is critical during vendor evaluation. Fragmented stacks create gaps, delays, and operational complexity that AI environments amplify.
Traditional DLP tools focus on email, endpoints, and file transfers. They struggle with AI prompts, unstructured conversations, and SaaS-native workflows. Enforcement is often delayed, making them ineffective for real-time AI usage.
DSPM excels at visibility and posture assessment, but most DSPM-only tools stop short of enforcement. They show where risk exists but do not prevent AI data leakage as it happens.
CASB tools control access to cloud apps but miss embedded AI features and API-driven interactions. They are not designed to inspect prompts, responses, or AI-generated outputs.
AI gateways can proxy traffic to specific models, but they often lack coverage across SaaS apps, attachments, and internal services. They also introduce latency and single points of failure.
Custom solutions are expensive to build, hard to maintain, and rarely keep pace with rapid AI adoption. They tend to address narrow use cases while leaving broader exposure unprotected.
Unified platforms outperform these approaches by combining discovery, classification, and enforcement across all AI-enabled data paths. Solutions like Strac replace fragmented controls with a single enforcement layer that scales as AI usage grows.
AI has changed regulatory expectations, even when regulations have not explicitly changed language. Frameworks such as GDPR, HIPAA, PCI DSS, and SOC 2 increasingly expect organizations to apply reasonable safeguards to AI-driven data processing.
Regulators are already providing concrete direction on how data protection principles apply to AI systems. The UK ICO’s guidance on AI and data protection is a useful benchmark for buyers because it connects AI adoption to practical expectations around data protection principles; including governance, accountability, and protecting individuals while using A
In practice, this means:
Auditors are looking for:
AI data security platforms support compliance by operationalizing controls. Instead of relying on static documentation, they generate real enforcement evidence across AI and SaaS workflows. This approach reduces audit friction while lowering actual risk, which is ultimately the goal of compliance in an AI-driven environment.
When organizations evaluate AI data security platforms, the differentiator is not how many risks a tool can identify; it is how effectively it can prevent sensitive data from ever reaching AI systems. Strac is purpose-built around this principle. It delivers real-time AI data governance by combining discovery, classification, and inline enforcement across SaaS, cloud, APIs, and generative AI workflows; without slowing teams down.
Strac is a unified AI data security platform designed for how AI is actually used in modern organizations.
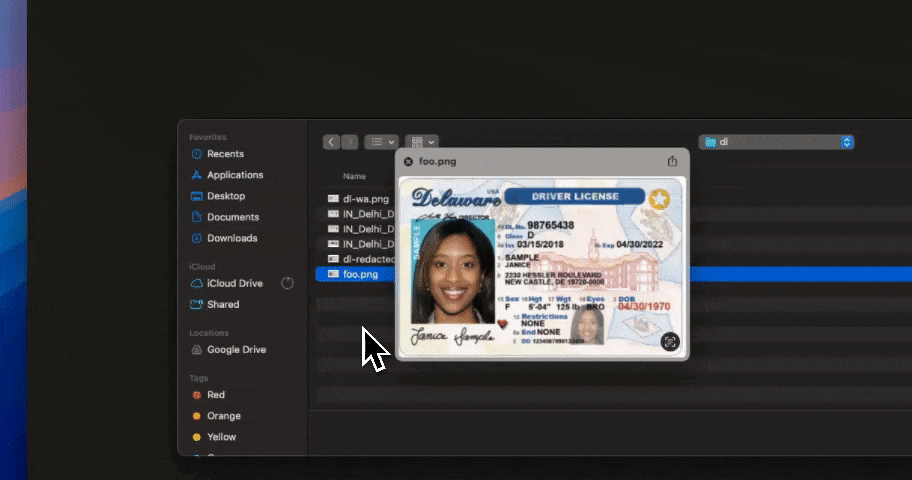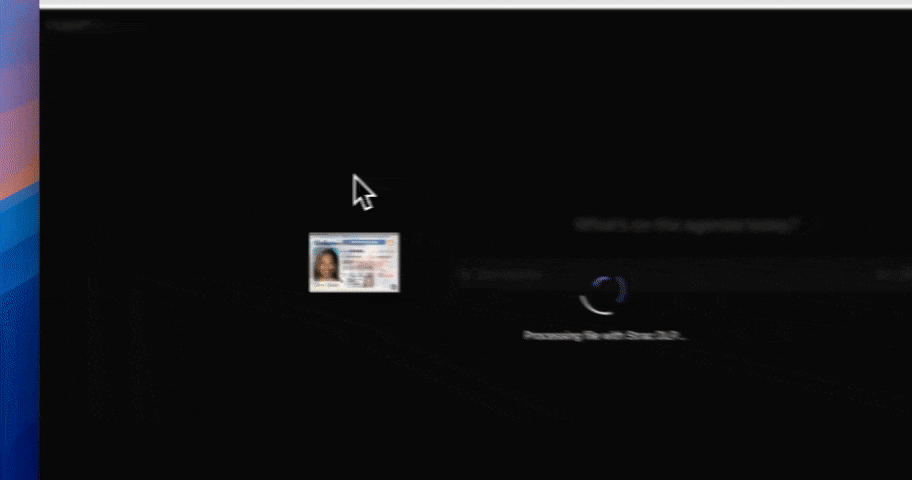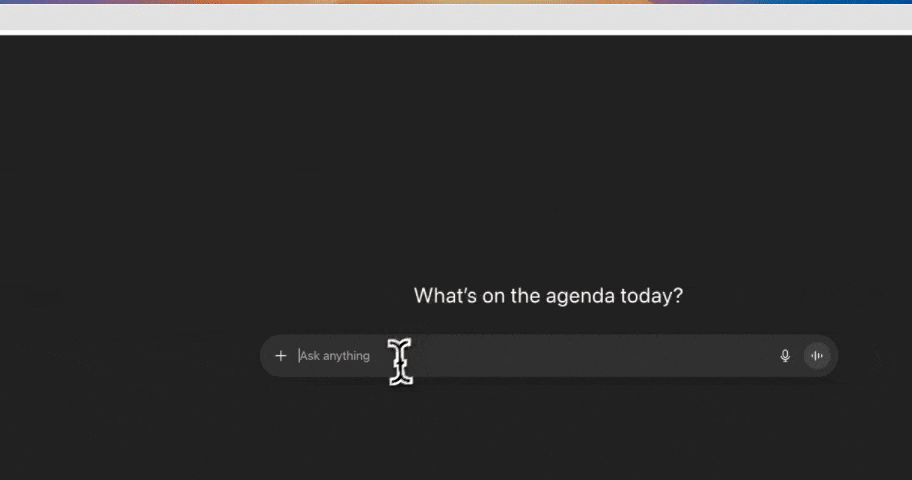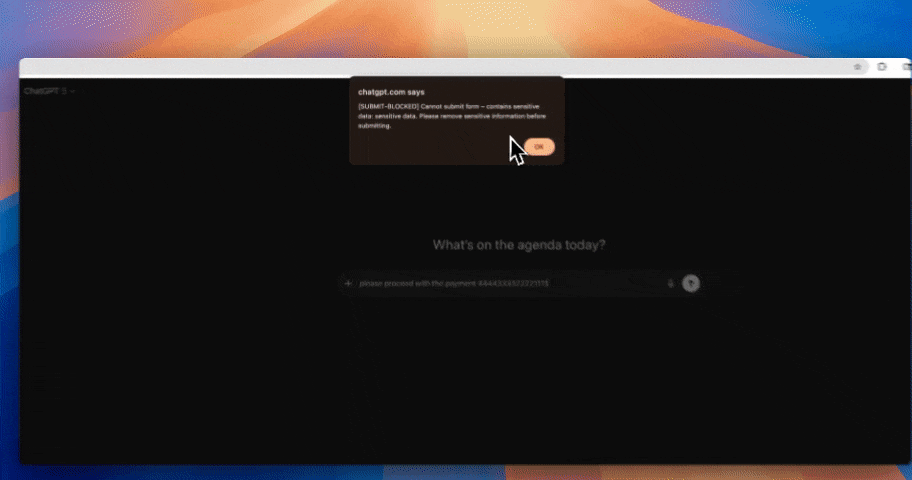
AI data exposure rarely comes from model training alone. In production environments, risk appears when employees paste data into ChatGPT, when copilots access internal documents, or when support tickets and uploads are reused as AI inputs. Strac secures these real-world flows by enforcing controls before data leaves controlled systems, not after alerts fire.
Strac provides:
This architecture eliminates the blind spots created by point tools that only see part of the AI data path.
Detection accuracy determines whether enforcement can scale. Strac uses content-aware ML and OCR-based classification, rather than regex-only rules, to understand sensitive data in unstructured text, files, screenshots, and attachments. This dramatically reduces false positives while improving coverage across AI-driven workflows.
By classifying data before it reaches AI systems, Strac enables confident enforcement decisions without disrupting legitimate usage. Security teams gain control without becoming bottlenecks.
Most AI security tools stop at visibility. Strac is enforcement-first by design. It does not just flag risky behavior; it automatically mitigates it inline.
With Strac:
This approach prevents AI data leakage at scale and removes the operational burden of manual response.
Strac uniquely combines DSPM and DLP into a single AI data security platform. Security teams get continuous visibility into where sensitive data lives, how it is accessed, and how it flows into AI systems; while enforcing policies through one centralized engine.
This unified model:
Instead of stitching together DSPM dashboards and DLP alerts, teams operate from a single system that both understands and controls AI data risk.
Strac’s agentless, API-native architecture enables fast rollout and low operational overhead. There are no endpoint agents to manage and no traffic proxies that introduce latency or fragility. Most teams can begin enforcing meaningful AI data controls within days, then expand coverage as AI adoption grows.
This deployment model makes Strac especially well-suited for fast-moving organizations that need AI security without slowing innovation.
Strac supports compliance expectations for GDPR, HIPAA, PCI DSS, and SOC 2 by generating real enforcement evidence, not just policies. Every detection and remediation action is logged, creating an auditable trail that demonstrates reasonable safeguards across AI and SaaS workflows.
For buyers evaluating AI data security platforms, this combination of prevention, scale, and operational simplicity is what separates Strac from monitoring tools and fragmented stacks. It is why organizations adopting AI at scale increasingly choose Strac as their AI data security foundation.
AI has changed regulatory expectations, even when the language of regulations has not explicitly caught up. Frameworks such as GDPR, HIPAA, PCI DSS, and SOC 2 increasingly expect organizations to apply reasonable safeguards to AI-driven data processing, especially where personal or sensitive data is involved. In this context, compliance is no longer about documenting intent; it is about demonstrating continuous, enforceable control over AI data flows.
In practical terms, AI data security and compliance readiness require organizations to protect sensitive information wherever AI touches it. This includes safeguarding personal and regulated data used in prompts and responses, preventing unauthorized exposure through AI copilots and automation, and maintaining verifiable evidence of active enforcement rather than relying on static policies. These expectations are rapidly becoming baseline requirements for audits and risk assessments.
Auditors are increasingly looking for concrete proof that AI workflows are secured in practice. This means logs showing detection and remediation of sensitive data, evidence that AI usage is covered by security controls, and confirmation that enforcement is continuous and aligned with documented policies. Platforms that can only produce policy documents or high-level dashboards fall short of these expectations.
AI data security platforms support compliance by operationalizing controls directly within AI and SaaS workflows. Instead of relying on documentation alone, they generate real enforcement evidence as data moves through AI systems. This approach reduces audit friction while materially lowering risk, which is ultimately the objective of compliance in an AI-driven environment.
An AI data security platform is a preventive, enforcement-driven system that discovers, classifies, and controls sensitive data as it flows through AI tools and the systems feeding them. The difference is that it does not just “monitor AI usage”; it protects the actual data paths where leaks happen, including prompts, responses, attachments, logs, and downstream SaaS workflows. The best platforms combine visibility with real-time action so sensitive information is blocked, redacted, or masked before it ever reaches an AI model.
To make this concrete, a true AI data security platform typically includes capabilities such as:
Bottom line; if it only alerts after data is already exposed, it is not an AI data security platform, it is monitoring.
AI data security is built for unstructured, high-velocity workflows where data moves through prompts, copilots, and embedded AI features inside SaaS apps. Traditional DLP was built for predictable channels like email, endpoints, and file transfers; it often cannot see or control AI interactions in real time. That is why AI environments expose the limits of legacy detection and delayed enforcement.
Here is the practical difference that matters in production:
If your teams use copilots daily, AI data security is not a “DLP add-on”; it is a new enforcement layer for modern data flows.
Yes; the right AI data security platforms can prevent ai data leakage in ChatGPT-style tools and copilots by applying controls at the exact point of use. Instead of waiting for an alert, they inspect prompts and responses in real time and enforce policy automatically. This is how you stop users from accidentally pasting sensitive data into AI, and how you prevent copilots from returning regulated content from internal documents.
In practice, prevention includes controls such as:
This is the difference between “we can see risky AI usage” and “we can stop it.”
They can strongly support GDPR and HIPAA readiness by operationalizing safeguards, enforcement, and audit evidence across AI workflows. Compliance frameworks generally expect organizations to implement appropriate protections for personal data and health data; AI introduces new data paths that must be controlled, not ignored. AI data security platforms help by enforcing policies continuously and producing evidence that controls are active.
What they typically help you produce for audits:
This is practical compliance support, not legal advice; it reduces audit friction because you can show enforcement outcomes rather than policy intent.
Deployment time depends on the platform architecture and the scope of integrations, but modern AI data security platforms are designed to roll out quickly. Agentless, API-native approaches typically deploy much faster than agent-based, endpoint-heavy models because they avoid device installs and complex maintenance.
A realistic rollout often looks like this:
The key is time-to-risk-reduction; a strong platform starts enforcing meaningful controls early, then expands coverage without increasing operational drag.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

