Top DSPM Use Cases
Explore practical DSPM use cases for SaaS and cloud environments; from sensitive data discovery to exposure reduction and compliance.
DSPM use cases have become essential as SaaS sprawl and cloud data growth reshape how sensitive information is created, shared, and exposed across modern organizations. Teams now operate across dozens of SaaS applications, cloud platforms, and data stores, where information flows continuously through collaboration tools, customer systems, and automated workflows. In this environment, data risk is rarely caused by a single breach; it accumulates through everyday access and sharing that security teams struggle to see.
Sensitive data exposure is increasingly driven by who has access and how data is shared, not by traditional perimeter failures. Files are over-shared, permissions drift over time, and regulated data quietly spreads into tickets, chats, attachments, and analytics systems. Regulatory pressure from GDPR, HIPAA, PCI DSS, and SOC 2 intensifies this problem by requiring clear visibility, control, and proof of compliance across the full data lifecycle. Infrastructure-centric security models focus on networks and systems, but they miss these data-level risks; DSPM addresses this gap by centering security on the data itself and how exposure actually happens in SaaS-heavy environments.
Data Security Posture Management is used when organizations need clarity and control over sensitive data that is spread across SaaS applications, cloud platforms, and modern data workflows. As environments grow more dynamic, security teams can no longer rely on static inventories or infrastructure signals to understand risk. DSPM addresses this gap by continuously mapping sensitive data, access paths, and exposure in a way that reflects how data is actually used.
In practice, DSPM is used across several critical security and compliance scenarios.
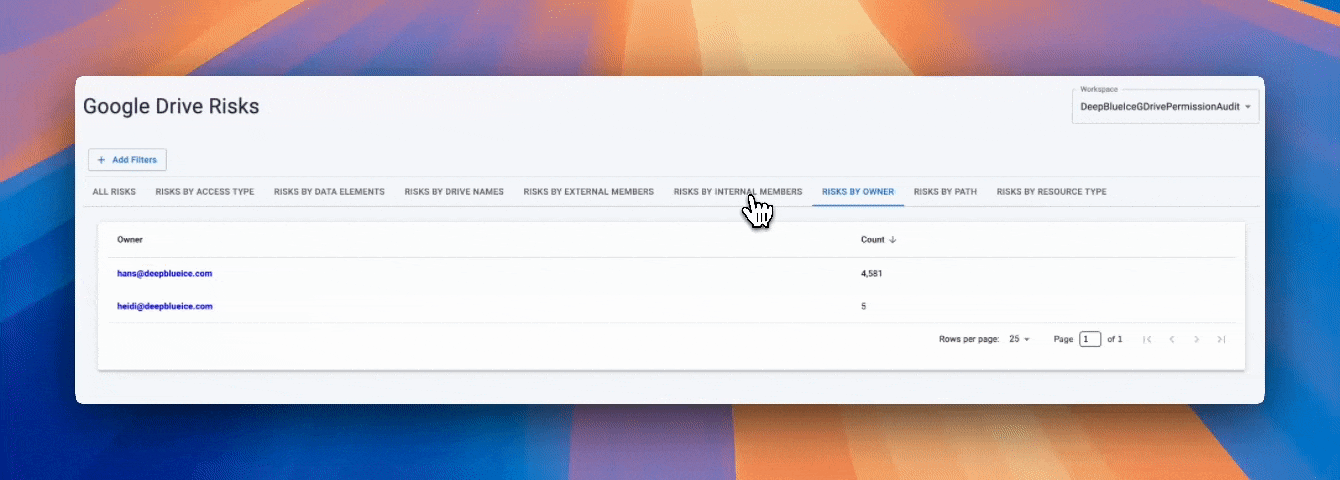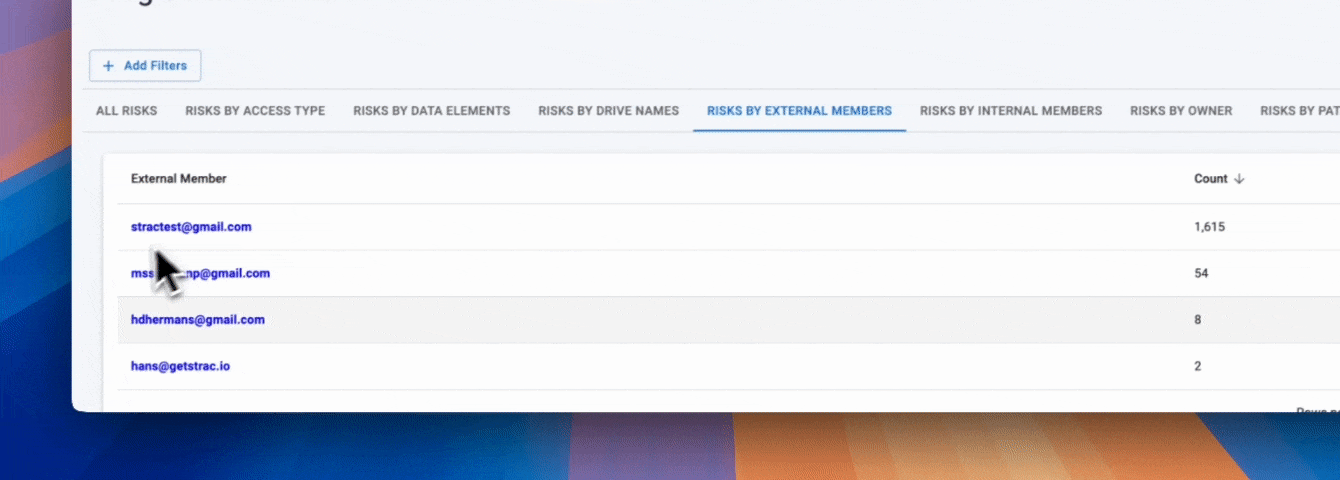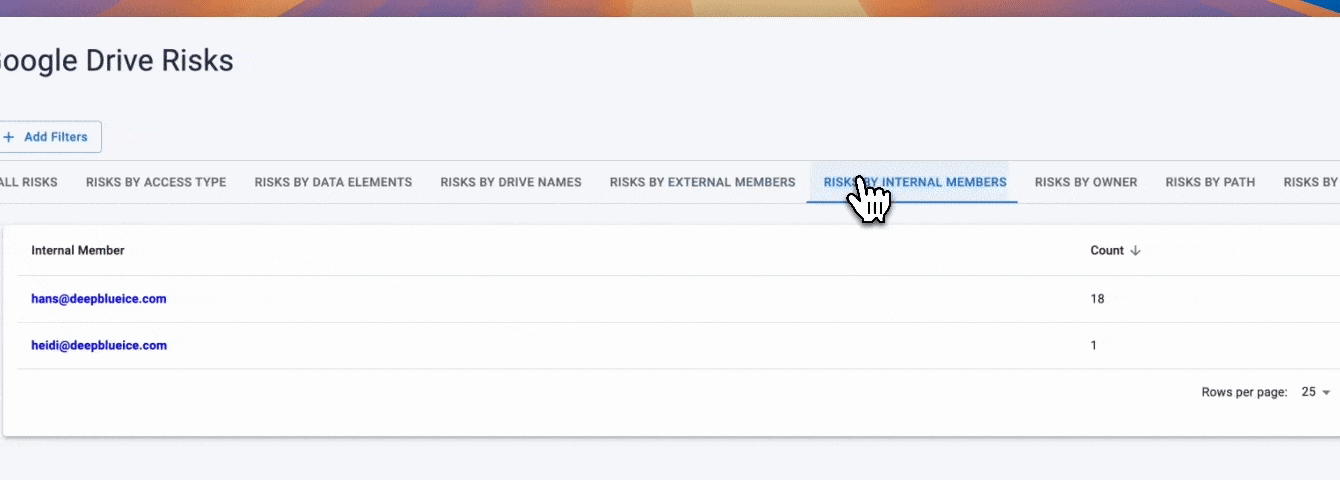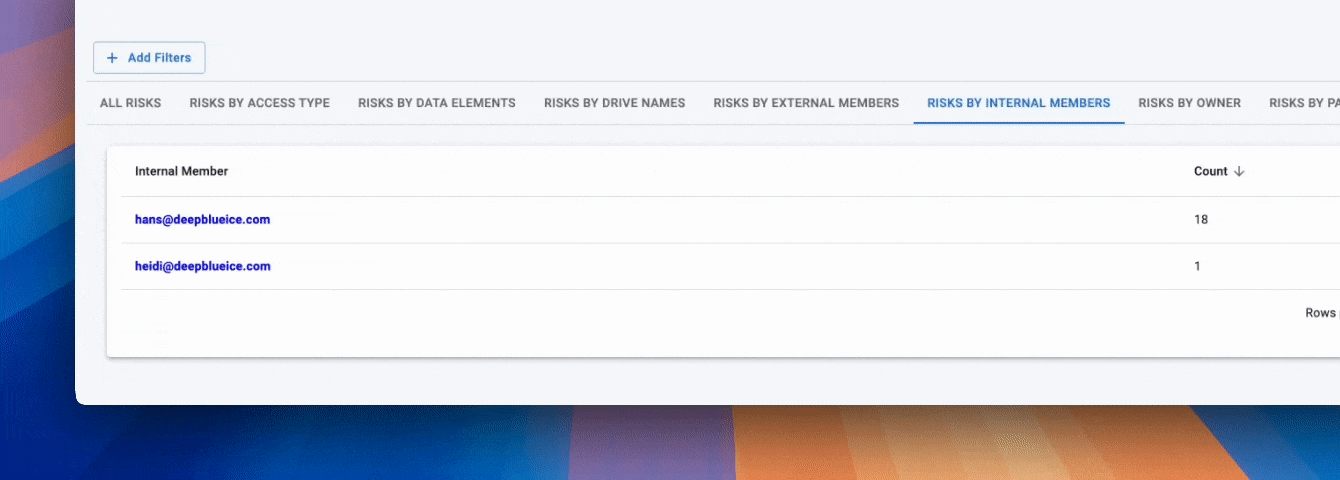
The most impactful DSPM use cases address the realities of how sensitive data is created, shared, and accessed across modern SaaS and cloud environments. Security teams are no longer struggling with isolated systems; they are managing sprawling data ecosystems where exposure is driven by access, sharing behavior, and constant change. The following DSPM use cases illustrate how organizations reduce real-world risk by shifting security controls from infrastructure assumptions to data-centric visibility and action.
Sensitive data is no longer confined to databases or well-defined systems; it appears across SaaS platforms, cloud storage, collaboration tools, and analytics environments. Data is copied, exported, embedded into tickets, or shared in chats, often without security teams realizing it exists. Without accurate discovery and classification, organizations cannot assess exposure or apply meaningful controls.
The real security problem: PII, PHI, PCI data, credentials, and intellectual property are spread across both structured systems such as databases and warehouses, and unstructured locations such as documents, messages, attachments, and support tickets.
Why legacy tools fail: Traditional tools rely on static scans, predefined repositories, or pattern-based detection, which miss unstructured data and fail to keep pace with constantly changing SaaS environments.
How DSPM addresses it: DSPM continuously discovers and classifies sensitive data across SaaS and cloud platforms, maintaining visibility regardless of data format, location, or movement.
This use case establishes the foundation for all other data risk reduction efforts.
Overexposed data represents one of the most common and dangerous forms of modern data risk. Sensitive information is frequently shared to move work forward, but those sharing decisions often persist long after their business purpose has passed. Over time, exposure accumulates quietly and becomes difficult to track.
The real security problem: Sensitive data is exposed through public links, external sharing, and misconfigured permissions that grant broader access than intended.
Why legacy tools fail: Infrastructure-centric tools may detect misconfigurations but cannot correlate them with the sensitivity of the underlying data or the real impact of exposure.
How DSPM addresses it: DSPM connects data sensitivity with sharing and permission states, allowing teams to identify and remediate overexposed sensitive data based on actual exposure risk.
By prioritizing exposure over configuration noise, DSPM enables faster and more effective remediation.
Access risk is the primary driver of data exposure in SaaS-heavy environments, yet it is often poorly understood. As organizations grow, access accumulates across employees, contractors, partners, and integrations. Without continuous insight, excessive access becomes normalized.
The real security problem: Sensitive data is accessible to a mix of internal and external identities, often far beyond what is required for business operations.
Why legacy tools fail: Legacy security models focus on system access rather than data-level access, making it difficult to see who can actually reach sensitive information.
How DSPM addresses it: DSPM maps sensitive data to identities and access paths, surfacing excessive access risk and enabling alignment with least-privilege principles.
This visibility allows teams to reduce exposure without disrupting legitimate collaboration.
When incidents occur, the severity of impact depends on how widely sensitive data is accessible. Excess permissions and dormant access dramatically increase breach blast radius. Reducing this exposure is one of the most effective ways to limit damage.
The real security problem: Unused permissions and overly broad access paths allow attackers or insider threats to reach far more data than necessary.
Why legacy tools fail: Traditional access reviews lack data sensitivity context, resulting in slow, manual processes that fail to prioritize meaningful risk reduction.
How DSPM addresses it: DSPM guides access cleanup by identifying unused permissions and limiting high-risk access paths based on data exposure impact.
This targeted approach reduces blast radius while preserving operational efficiency.
SaaS adoption accelerates productivity but also fragments data governance. Platforms such as Google Drive, Slack, Salesforce, Jira, and Zendesk become repositories for sensitive data that were never designed to act as systems of record. Shadow data emerges as teams adopt unmanaged tools.
The real security problem: Sensitive data proliferates across sanctioned and unsanctioned SaaS applications, creating blind spots and inconsistent controls.
Why legacy tools fail: Many tools cover only a limited subset of applications or require heavy configuration that does not scale with SaaS growth.
How DSPM addresses it: DSPM provides unified visibility across SaaS environments, revealing shadow data and unmanaged SaaS exposure in a single data-centric view.
This enables consistent governance even as SaaS ecosystems expand.
Data risk evolves continuously as user behavior changes, permissions drift, and systems integrate. One-time assessments cannot capture emerging threats. Continuous monitoring is essential to prevent small issues from becoming incidents.
The real security problem: Bulk downloads, abnormal access behavior, and posture drift indicate elevated risk but often go undetected until after damage occurs.
Why legacy tools fail: Snapshot-based scans and alert-only systems lack the continuity and context needed to detect exposure patterns over time.
How DSPM addresses it: DSPM continuously monitors data posture and access behavior, surfacing risky exposure patterns as they develop.
This allows teams to intervene early and reduce downstream impact.
Compliance expectations increasingly demand ongoing control rather than periodic validation. Auditors want evidence that reflects real data handling practices, not assumptions. Meeting these expectations requires continuous visibility into sensitive data.
The real security problem: Organizations struggle to produce evidence-ready reporting that accurately reflects where regulated data lives and how it is protected.
Why legacy tools fail: Point-in-time audits and manual reporting quickly become outdated and fail to capture dynamic SaaS environments.
How DSPM addresses it: DSPM supports continuous compliance by maintaining up-to-date visibility and evidence tied to actual data exposure.
This transforms compliance from a reactive exercise into an ongoing operational capability.
DSPM delivers the most value in organizations where data moves faster than traditional security controls can track. As SaaS adoption accelerates, cloud usage expands, and teams work across distributed environments, data exposure increasingly stems from access, sharing, and duplication rather than from infrastructure failures. The following organizational profiles consistently see the strongest outcomes from DSPM use cases because they face persistent visibility and governance gaps that legacy tools cannot address.
Organizations that rely heavily on SaaS applications generate large volumes of sensitive data outside of centralized systems. Customer data, internal records, and operational information spread across collaboration tools, CRMs, and support platforms as part of everyday work.
For SaaS-heavy organizations, DSPM becomes essential to regain control over data sprawl.
Industries subject to strict regulatory requirements face higher consequences when sensitive data is exposed. Financial services, healthcare, technology platforms, and B2B SaaS providers must demonstrate ongoing control over personal, financial, and health data.
For regulated industries, DSPM shifts compliance from a reactive audit exercise to a continuous operational capability.
Cloud-first architectures and remote work models increase the number of access paths to sensitive data. Employees, contractors, and partners collaborate across locations, devices, and identities, often with broad permissions granted for convenience.
For cloud-first and remote teams, DSPM provides the clarity needed to manage access risk at scale.
Many security teams know sensitive data exists but lack a clear understanding of where it lives, who can access it, and how exposure accumulates over time. This gap makes prioritization difficult and increases the likelihood of missed risks.
For organizations struggling with visibility, DSPM becomes the foundation for effective data risk management.
As security stacks expand, confusion often arises around where DSPM, DLP, and CSPM fit and whether one replaces the others. In reality, these tools address different layers of risk, and the most effective programs use them together. Understanding how each operates clarifies why many DSPM use cases emerge specifically to fill gaps left by infrastructure- and policy-centric controls.
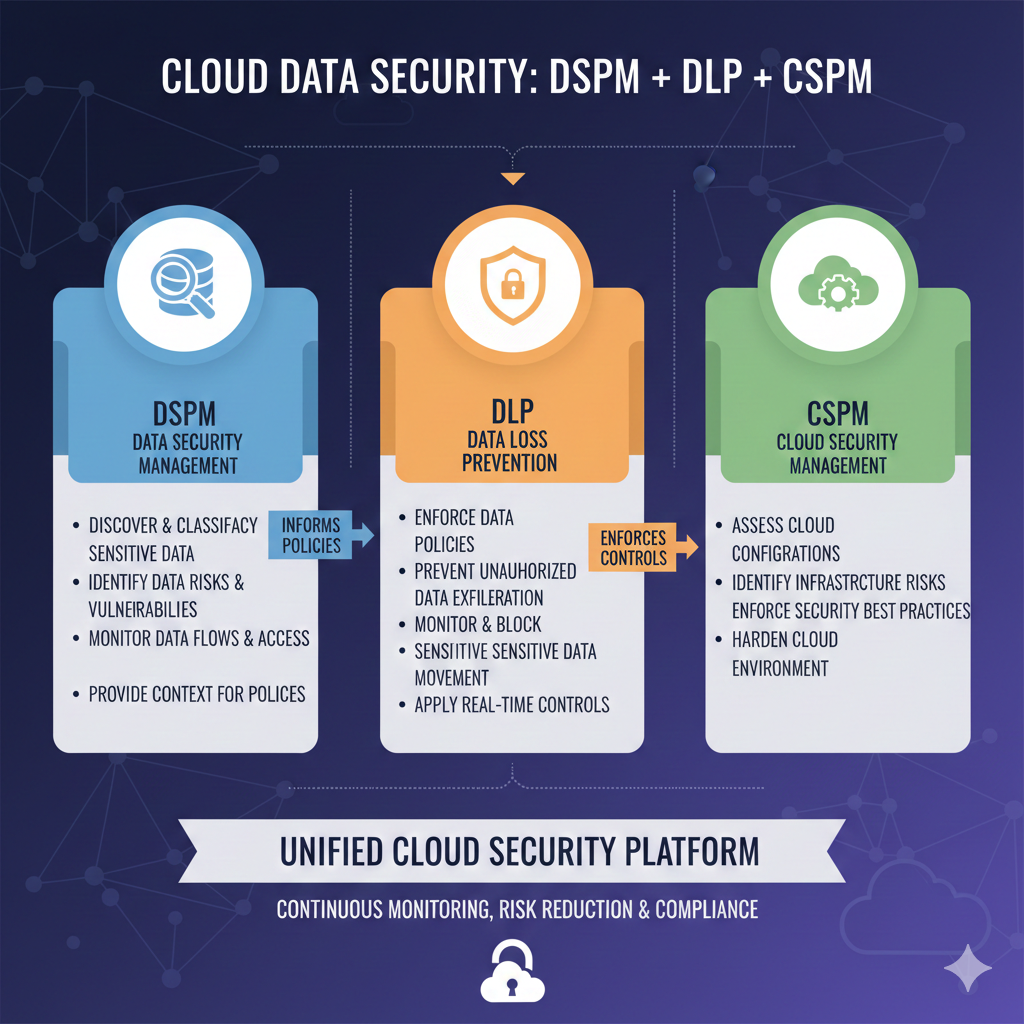
DSPM focuses on the state of sensitive data itself; where it lives, how it is classified, and who can access it. Its primary role is to make data exposure visible across SaaS, cloud, and modern data environments, regardless of where that data originated or how it is used.
DSPM establishes the data-level context that other tools depend on to operate effectively.
DLP is designed to control how sensitive data moves through systems and workflows. It enforces policies around sending, sharing, uploading, or transmitting data through channels such as email, SaaS apps, endpoints, and APIs.
This is why DSPM does not replace DLP; it strengthens it by providing the context needed to apply enforcement intelligently.
CSPM focuses on the configuration and security posture of cloud infrastructure. Its goal is to detect misconfigurations, insecure services, and policy violations at the infrastructure layer.
CSPM secures the environment; DSPM secures the data within it.
DSPM and DLP address different stages of data risk and are most effective when used together. DSPM provides the continuous understanding of data exposure and access that DLP relies on to enforce meaningful controls.
Together, these tools form a layered approach to data security. DSPM grounds enforcement and configuration decisions in real data exposure, ensuring that security teams focus on the risks that matter most rather than chasing isolated alerts or misconfigurations.
DSPM is implemented as a continuous operational process rather than a one-time deployment or assessment. In modern environments, data changes faster than infrastructure, permissions drift daily, and new workflows are introduced without centralized oversight. Effective DSPM use cases depend on treating data security as an ongoing lifecycle; from discovery to remediation; that adapts to SaaS, cloud, and GenAI realities.
At the core of DSPM implementation is a repeatable sequence that turns visibility into measurable risk reduction. Each stage builds on the previous one to ensure actions are grounded in real data exposure rather than assumptions.
DSPM continuously scans SaaS applications, cloud storage, data platforms, and AI workflows to identify where sensitive data exists, including both structured and unstructured sources.
Once discovered, data is classified by sensitivity; such as PII, PHI, PCI, credentials, or intellectual property; creating context for downstream risk decisions.
DSPM then maps who can access sensitive data, including internal users, external collaborators, service accounts, and integrations, revealing excessive or risky access paths.
Based on exposure and access risk, DSPM guides or automates actions such as restricting sharing, tightening permissions, or assigning ownership to reduce exposure.
This lifecycle ensures that DSPM use cases move beyond visibility and deliver concrete security outcomes.
One of the defining differences in DSPM implementation is the shift from periodic scans to continuous monitoring. Scheduled assessments quickly become outdated in SaaS-heavy environments where data and access change daily.
By operating continuously, DSPM aligns security posture with the real pace of modern data environments.
DSPM is not designed to replace existing security controls; it is implemented to complement and strengthen them. Most organizations already rely on DLP, CSPM, IAM, SIEM, and compliance tooling to manage different aspects of risk.
Through integration rather than isolation, DSPM becomes the connective layer that aligns data posture, access control, and enforcement across SaaS, cloud, and GenAI environments.
Strac enables real-world DSPM use cases by focusing on how sensitive data is actually created, accessed, and exposed across modern SaaS, cloud, and GenAI environments. Rather than treating data security as a point-in-time assessment, Strac applies a continuous, data-centric approach that aligns with how organizations operate today. The platform is designed to surface meaningful exposure risk and support practical remediation without disrupting business workflows.
Strac is built for SaaS-first and cloud-first environments, where sensitive data lives far beyond traditional databases and file systems. It operates natively across modern applications and cloud services, reflecting how data flows through collaboration tools, customer platforms, and analytics environments.
This architecture allows DSPM use cases to remain effective even as tools and workflows evolve.

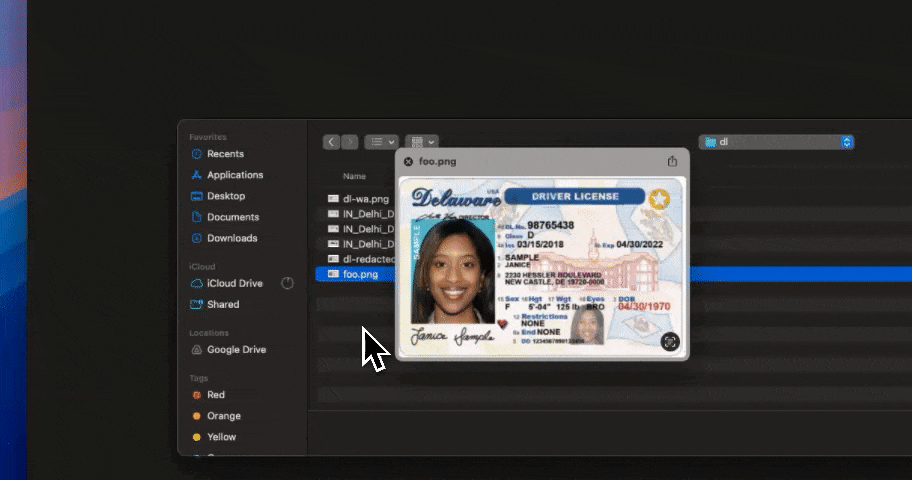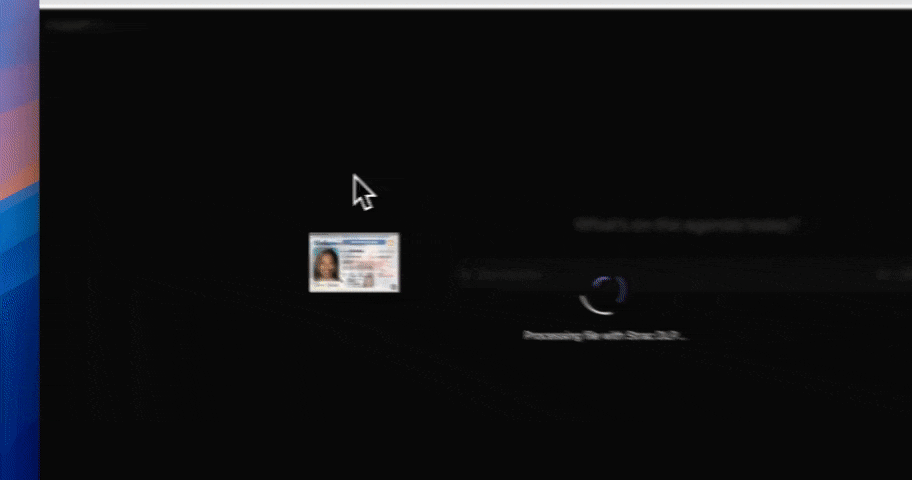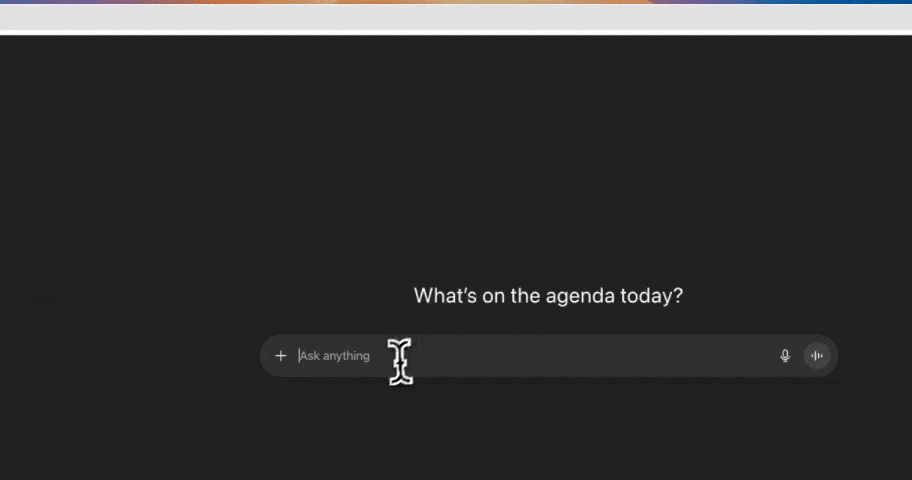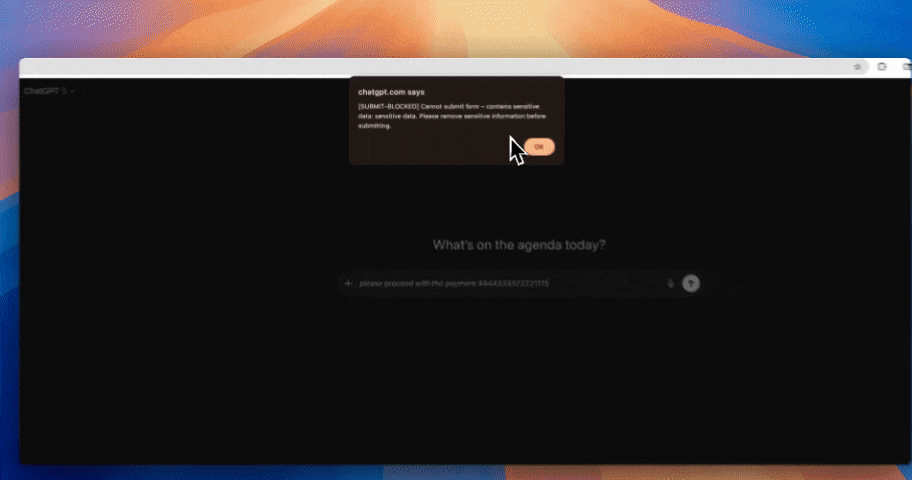
Strac continuously discovers and classifies sensitive data across structured and unstructured sources. This includes personal, financial, health, and proprietary data that appears in files, messages, tickets, attachments, and AI-driven workflows.
By keeping discovery and classification up to date, Strac provides the foundation for accurate exposure and access analysis.

Understanding who can access sensitive data is central to reducing real-world risk. Strac maps sensitive data to identities and access paths, revealing how exposure accumulates over time.
This visibility enables security teams to focus remediation efforts where they will have the greatest impact.
Strac goes beyond visibility by enabling practical posture remediation actions tied directly to exposure risk. These actions help teams reduce data exposure without relying solely on alerts or manual intervention.
These remediation capabilities allow DSPM use cases to translate into measurable risk reduction rather than static reporting.

Strac supports DSPM use cases across the full data lifecycle, including emerging GenAI workflows where sensitive data enters prompts, uploads, and generated outputs.
By providing unified coverage across these environments, Strac enables organizations to manage data exposure consistently, even as data moves into new tools and usage patterns.
This outcome-focused approach allows security teams to maintain visibility, reduce exposure, and support compliance in environments where data is constantly in motion.
DSPM exists because modern data risk is driven by access, sharing, and sprawl; not by missing firewalls or misconfigured servers alone. The most valuable DSPM use cases help organizations understand where sensitive data lives, who can reach it, and how exposure changes over time across SaaS, cloud, and GenAI workflows. When implemented correctly, DSPM shifts security from reactive alerts to proactive exposure reduction and transforms compliance from a point-in-time exercise into a continuous capability. For data-driven organizations, DSPM is no longer optional; it is the foundation for managing data risk at scale.
DSPM use cases describe the practical ways organizations apply Data Security Posture Management to reduce real data exposure risk across SaaS, cloud, and modern data environments. Rather than focusing on theoretical controls, these use cases address how sensitive data is actually handled in day-to-day operations.
Common DSPM use cases include:
Together, these use cases help security teams move from reactive response to proactive data risk management.
DSPM is used to maintain continuous visibility into sensitive data and the risks created by access and sharing. Security teams rely on DSPM to understand data posture as environments change, rather than relying on outdated inventories or assumptions.
In practice, DSPM is used to:
This makes DSPM especially valuable in SaaS-heavy and cloud-first organizations where data movement is constant.
DSPM and DLP address different but complementary aspects of data security. DSPM focuses on data posture and exposure; where sensitive data exists and who can access it; while DLP focuses on enforcing policies when data moves through systems. Without DSPM, DLP often lacks the context needed to apply controls accurately, which is why DSPM complements rather than replaces DLP in modern security programs.
Yes. DSPM supports GDPR and HIPAA compliance by aligning security controls with how regulated data is actually handled, not just how policies are written. It helps organizations move away from point-in-time compliance exercises toward continuous compliance readiness.
DSPM supports compliance by:
This makes audits more defensible and reduces last-minute compliance effort.
Deployment timelines vary by environment, but DSPM is typically faster to roll out than agent-heavy or infrastructure-centric tools. Because DSPM connects directly to SaaS and cloud data sources, initial visibility is often achieved quickly.
Most organizations see value in stages:
DSPM delivers incremental value from the start while improving accuracy and coverage as monitoring continues.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

