CrowdStrike DLP Alternatives: A 2026 Buyer’s Guide
A practical guide to API-first DLP for SaaS, cloud, email, endpoints, and GenAI.
CrowdStrike Falcon Data Protection is a module in the Falcon platform that uses the same lightweight agent and single console as your EDR/XDR stack. It combines content + context (file attributes, source, process lineage) to govern movements from endpoints to USB, web browsers, and SaaS destinations; 2025 updates added GenAI data leak prevention and encryption detection with expanded macOS coverage.
Where it shines
Where buyers still look at crowdstrike dlp alternatives
What most teams need in practice:

What it is
A cloud-native DSPM + DLP platform that protects sensitive data where people actually work—inside Slack, Google Drive, Gmail, Microsoft 365 (Teams/SharePoint/OneDrive/Exchange), Salesforce, Jira/Confluence, Zendesk/Intercom, GitHub, and modern GenAI tools—plus optional endpoint/browser controls.
Our POV
If most of your risk sits in SaaS, collaboration, tickets, and GenAI—not just on devices—start here. Strac’s strength is in-app remediation (redact/mask/label/revoke/remove externals) and at-rest discovery at scale. Use endpoint/browser controls only where you truly need them (USB, local uploads, print).
Pros
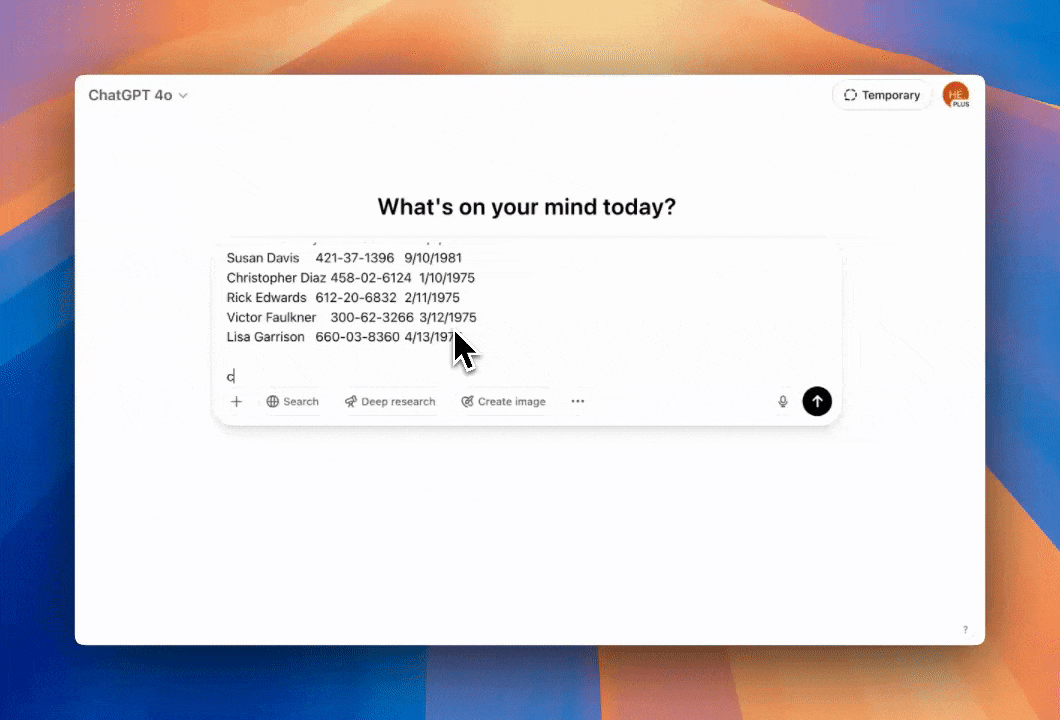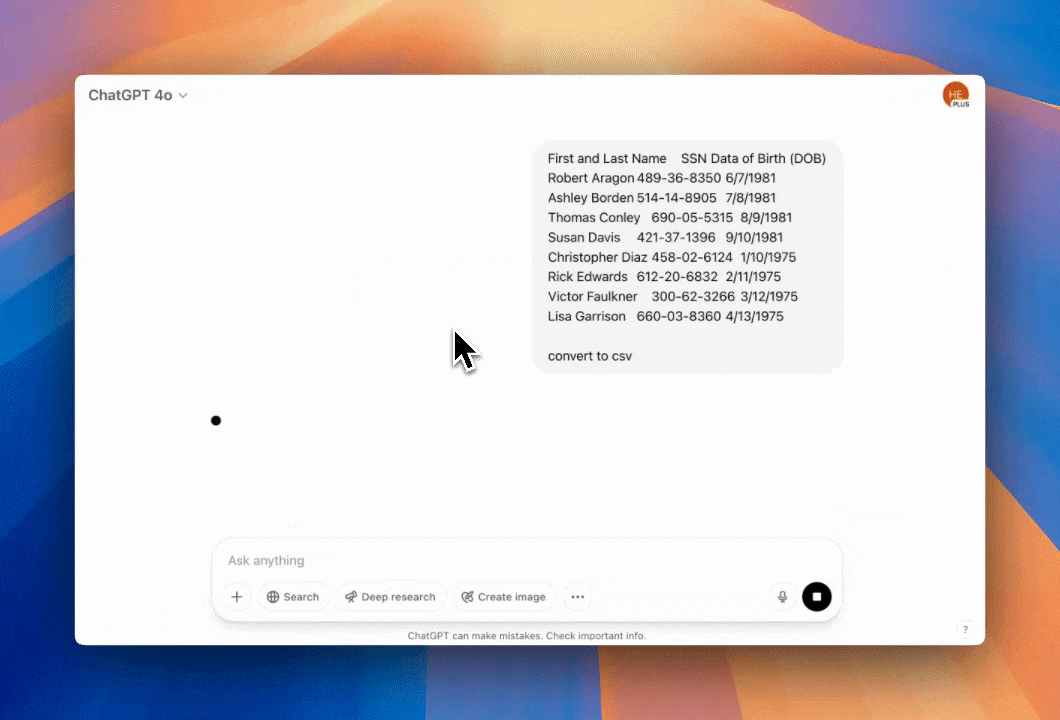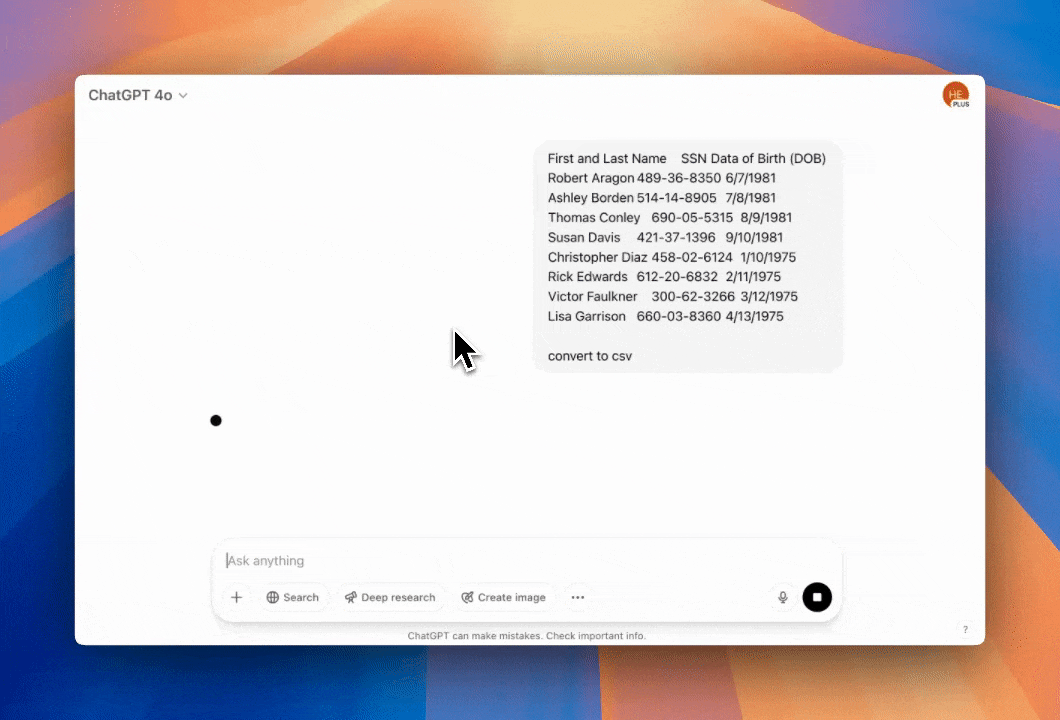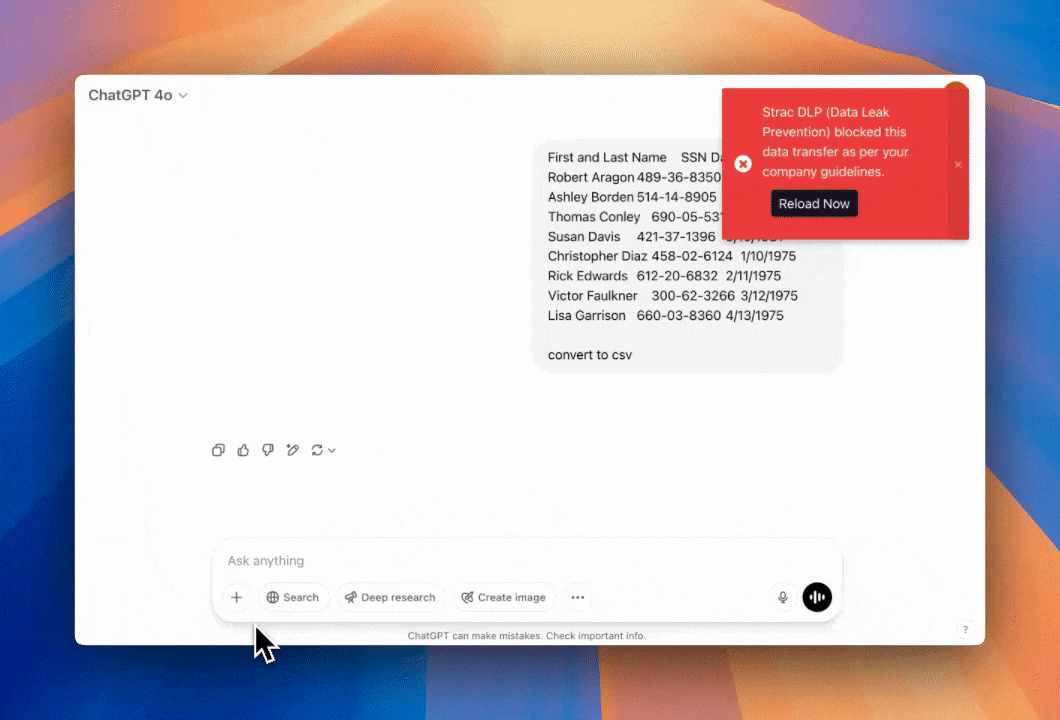

Example instant remediations you can enable in minutes
What it is
Forcepoint DLP is enterprise DLP spanning endpoints, email/web gateways, and CASB with risk-adaptive controls.
Our POV
Great when you want behavior-based, risk-adaptive decisions across multiple channels, including deep endpoint controls.
Pros
Cons / watchouts
Pilot checklist
What it is
Symantec DLP is a long-standing leader with deep inspection for endpoint and network, famous for EDM/IDM (exact data matching, fingerprinting).
Our POV
Still the benchmark for high-precision fingerprinting at scale—especially regulated datasets and document templates.
Pros
Cons / watchouts
Pilot checklist
What it is
Trellix DLP is an Endpoint-centric DLP tied into Trellix’s XDR ecosystem with ePO for central orchestration.
Our POV
Makes sense for Trellix-standardized shops that want DLP signals tightly correlated with EDR/XDR telemetry.
Pros
Cons / watchouts
Pilot checklist
What it is
Digital Guardian (Fortra) is an Endpoint-first DLP with very granular on-device controls; popular in IP-centric engineering/manufacturing.
Our POV
Choose when device governance is king (file flows, USB, print, clipboard/screen capture), including off-network.
Pros
Cons / watchouts
Pilot checklist
1) Can CrowdStrike Falcon Data Protection replace a full DLP stack?
It can cover endpoint exfiltration (USB, clipboard, print, browser uploads). It does not natively scan email servers or SaaS data at rest. Most enterprises pair Falcon with a SaaS/API-first DLP (e.g., Strac) or CASB/DSPM.
2) How do I cover GenAI data leakage across managed and unmanaged devices?
3) We collaborate in Slack/Drive/Teams—what’s the fastest way to reduce exposure?
Connect an API-first platform (Strac), discover at rest, then enable auto-remediation: label sensitive files, revoke public links, remove externals, and redact messages with sensitive snippets.

4) Can Strac be deployed inside our cloud for data residency?
Yes—Strac supports customer-hosted options (e.g., inside your AWS) where data cannot leave your environment.
5) What’s the tuning burden for each approach?
6) Do I still need endpoint DLP if I adopt Strac?
Strac has SaaS DLP + Endpoint DLP in the form of Browser DLP that does 90% of all endpoint dlp security controls
7) Can I simulate policies before blocking?
Yes—both endpoint and SaaS tools support monitor-only or “audit” modes. Run for 1–2 weeks, measure noise, then phase to enforcement.
8) How do I keep false positives low?
Use context + proximity keywords, ML/OCR, and (when needed) EDM/fingerprinting. Start with alert/label, then graduate to redact/block once confident.
9) How do these tools handle encrypted archives?
Most flag or block password-protected archives by policy; content inspection is limited without the key.
10) Will DLP slow people down?
Poor policies will. Favor granular remediation (redact/label, user justification, time-boxed auto-remediation) over blanket blocks. This is where Strac’s in-app controls shine.
11) BYOD and contractors are a blind spot—what should we do?
Endpoint DLP can’t see unmanaged devices. Use SaaS-side controls (Strac) to enforce policies inside Slack/Drive/Teams/Gmail regardless of device.
12) Reporting & audits—what matters most?
13) How should we budget (TCO)?
14) Migration strategy from endpoint-only to hybrid
Keep Falcon DLP for device channels. Add Strac to discover at rest and remediate in SaaS. Over 60–90 days, move from alert→label→redact/block in high-risk apps.
15) What does “good” look like at 90 days?
16) Do we need both EDM/fingerprinting AND ML/OCR?
If you protect known datasets/templates (e.g., patient or customer lists), EDM/fingerprinting is valuable (Symantec/Forcepoint). For unstructured chatter, screenshots, PDFs, ML/OCR (Strac) reduces noise. Many programs use both.
17) Can Strac apply Microsoft sensitivity labels?
Yes—Strac can apply or honor labels as part of remediation in supported apps, helping you standardize on MIP/Purview where it exists.
18) How do we run a low-risk POC?
Start “read-only” for 1–2 weeks → switch on label + user justification → enable redact/mask and link revocation for high-risk findings → finally consider “block” where appropriate.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

