Top 5 AI Data Security Companies
A practical buyer’s guide to AI data security companies; how to evaluate governance, DSPM, and AI DLP capabilities.
Generative AI has fundamentally changed how sensitive data moves inside organizations. Data now flows through prompts, copilots, SaaS-embedded AI features, and AI-generated outputs; often outside traditional security controls and inspection points. As a result, choosing the wrong type of AI data security company can leave critical gaps that are invisible until an incident occurs. Vendor selection has therefore become a strategic security decision; not a simple tooling exercise.
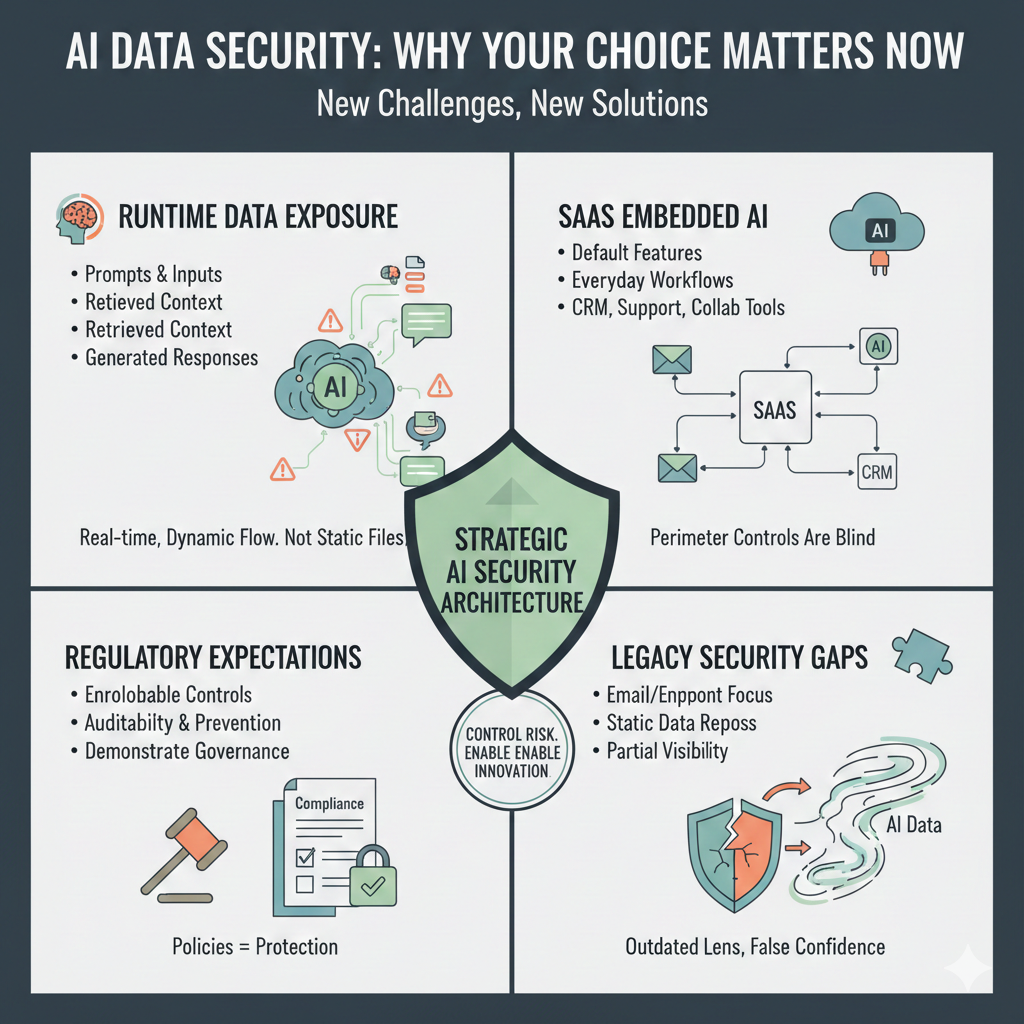
“AI data security companies” is an overloaded term. Vendors ranking for it often solve very different problems, which leads buyers to compare tools that were never meant to compete.
The only way to evaluate this space correctly is to separate vendors by where they operate in the AI data flow.
They improve AI reliability and application safety, not enterprise data protection.
They answer where data is and why it matters; not whether it is being used safely right now.
This category addresses where AI risk actually materializes.
The reality is that modern AI data security requires governance, discovery, and enforcement working together.
Buyers who understand this taxonomy avoid mismatched tools and choose platforms aligned with how AI is actually used in production.
AI data security vendors succeed or fail in production. Feature lists don’t matter; runtime control does.
What to evaluate:
Bottom line; AI data security platforms either control AI data in motion or they just describe risk.
There is no single “best” AI data security company. The right choice depends on how AI is actually used and where sensitive data intersects with those workflows. Teams that start with usage patterns; not vendor features; make better decisions.
Common scenarios and what matters most:
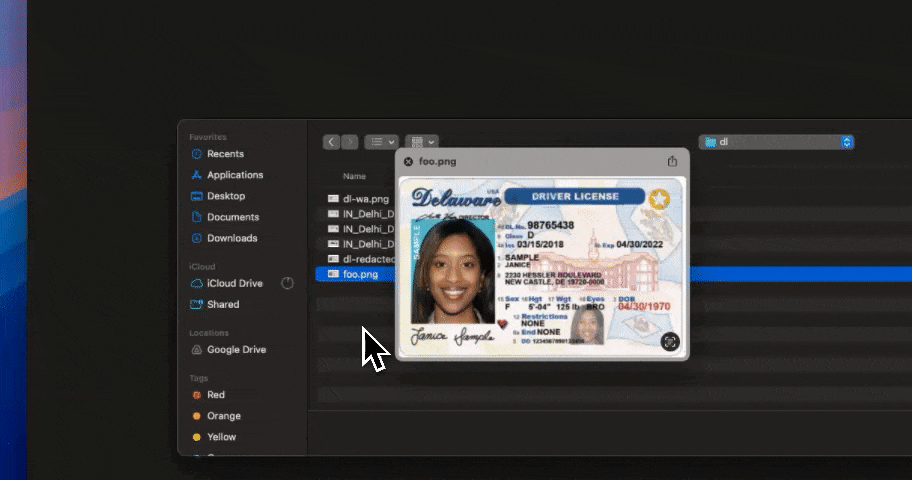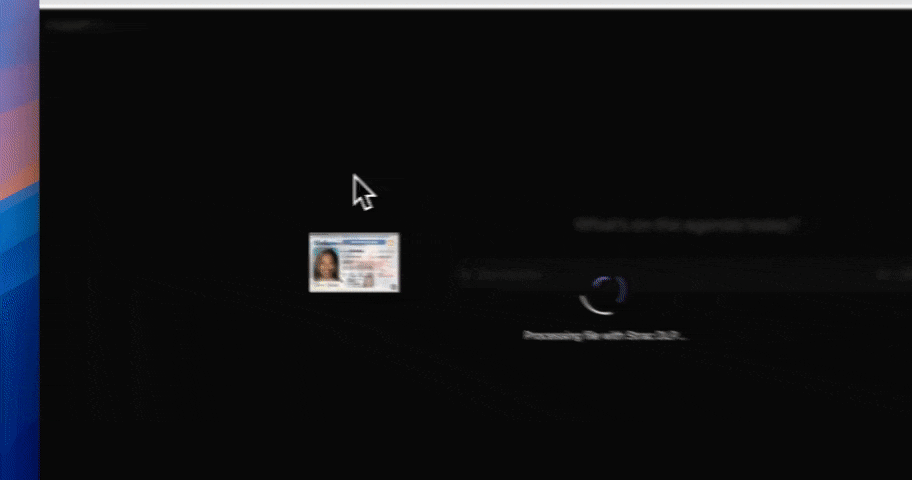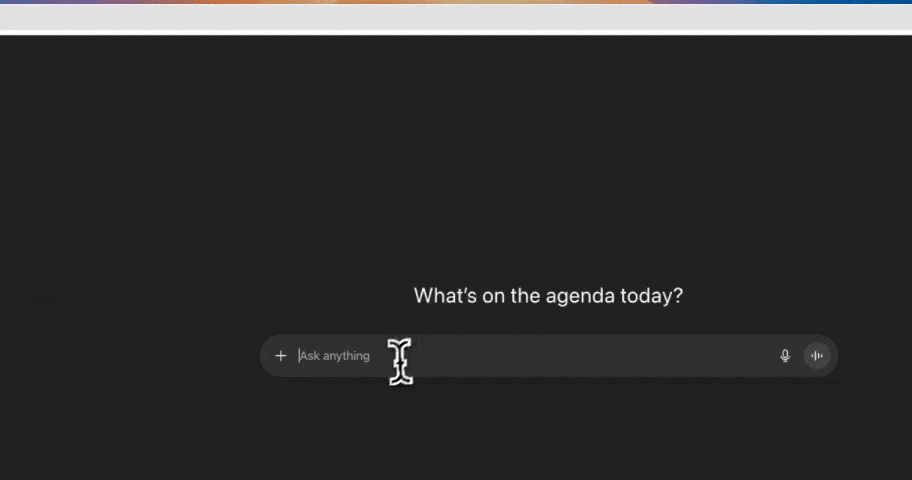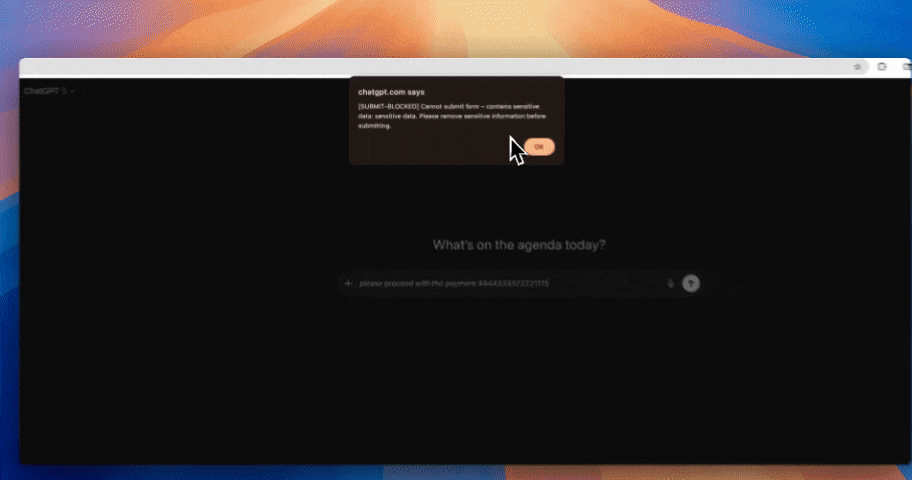
When conversational AI is part of everyday work, runtime control is mandatory.
Visibility alone does not reduce risk here; exposure happens at interaction time.
AI features are now default in CRMs, support tools, and collaboration platforms.
Securing one AI interface is not enough.
For GDPR, HIPAA, PCI DSS, and similar frameworks, proof matters.
Policy-only approaches fail audits in AI environments.
Fast adoption increases exposure if controls add friction.
Controls that slow teams down get bypassed.
Many organizations struggle with AI data security not because they lack tools, but because of flawed assumptions made during the buying process. As AI adoption accelerates, security teams often apply legacy evaluation frameworks to fundamentally new data flows. The result is a mismatch between perceived coverage and actual risk. The following mistakes are among the most common and most costly.
Avoiding these pitfalls requires reframing AI data security as an operational challenge rather than a theoretical one. Organizations that ground their vendor evaluations in real usage patterns are far more likely to achieve lasting risk reduction.
Some platforms are designed specifically for the intersection of AI data governance, DSPM, and AI DLP. Rather than treating AI as a standalone risk or focusing on a single control layer, these solutions address how sensitive data actually moves through AI-enabled SaaS workflows. This category has emerged in response to the limitations of tools that offer visibility without enforcement or policies without technical control.
These platforms start with understanding sensitive data in the context of AI usage. Discovery and classification are SaaS-native and API-driven, enabling visibility into where regulated or proprietary data lives and where it is likely to be used by AI features. This foundation allows security teams to reason about AI risk based on real data flows rather than assumptions.
Governance is enforced through technical controls that reflect how employees and systems actually interact with AI. Policies are applied to prompts, uploads, and AI-enabled workflows instead of existing as static documentation. This approach aligns governance intent with operational reality.
Enforcement occurs at the moment AI risk materializes. Inline inspection of data in motion allows platforms in this category to block, redact, or warn before sensitive information reaches an AI system or is generated in outputs. This distinguishes them from alert-only approaches that respond after exposure has already occurred.
A SaaS-native, agentless design reduces deployment friction and operational overhead. By integrating directly with cloud and SaaS platforms, these solutions can scale with AI adoption without requiring invasive endpoint agents or complex infrastructure changes.
Detailed logging and traceability provide evidence of how policies are enforced across AI-enabled workflows. This supports regulatory requirements by demonstrating not just intent, but consistent, repeatable control over sensitive data.
Platforms in this category reflect a broader shift in the AI data security market. As AI becomes embedded across everyday SaaS applications, effective protection increasingly depends on unifying governance, discovery, and enforcement into a single operational model rather than relying on isolated point tools.
As organizations move from experimenting with AI to deploying it across production SaaS workflows, the definition of AI data security has expanded. The leading AI data security companies differ significantly in how they approach governance, discovery, and enforcement. The list below highlights five vendors operating in this space, ranked by how comprehensively they address AI-driven data risk across modern enterprise environments.
Brief description
Strac is an AI data security platform designed to secure sensitive data as it moves through AI-enabled SaaS workflows. Rather than treating AI as a standalone risk, Strac focuses on governance, discovery, and real-time enforcement across prompts, uploads, and AI-generated outputs within everyday business tools.
Core use cases
Key strengths
Key weaknesses
Brief description
Securiti is a data governance and privacy automation platform with strong capabilities in data mapping, compliance workflows, and policy management. It is often evaluated by organizations prioritizing regulatory alignment and enterprise-scale governance programs.
Core use cases
Key strengths
Key weaknesses
Brief description
BigID is a well-established data discovery and classification platform widely used to identify sensitive data across large-scale enterprise environments. It plays a foundational role in many DSPM and data intelligence strategies.
Core use cases
Key strengths
Key weaknesses
Brief description
Cyera is a modern DSPM platform focused on identifying and reducing data risk across cloud environments. It emphasizes rapid visibility into sensitive data exposure and misconfigurations.
Core use cases
Key strengths
Key weaknesses
Brief description
Concentric AI specializes in context-aware DSPM, using semantic analysis to prioritize sensitive data risk. It is commonly evaluated by organizations seeking improved signal quality in data risk management.
Core use cases
Key strengths
Key weaknesses
AI data security companies are not interchangeable. The right choice is determined by how effectively a platform can see, govern, and enforce controls across AI-driven data flows that now run through prompts, copilots, SaaS-embedded AI features, and generated outputs. Organizations that evaluate vendors based on real AI usage patterns; rather than legacy categories or feature checklists; are far better positioned to reduce risk while continuing to scale AI adoption and innovation safely.
AI data security companies protect the sensitive data pathways created by AI adoption; not just the AI model itself. In practice, they focus on preventing regulated data, IP, credentials, and customer information from being exposed through AI-driven workflows across SaaS tools and employee usage. What matters is whether protection applies to the real places data moves today; prompts, uploads, context, and AI outputs; rather than only to traditional file or email channels.
AI data security companies differ from traditional DLP vendors because AI introduces runtime, context-dependent exposure that legacy DLP wasn’t designed to control. The key differences typically show up in:
Yes, but only if the platform is designed to cover AI usage where it actually occurs; not just where it is easiest to monitor. Buyers should validate three things in sequence; because gaps usually appear here first.
Yes, many can support GDPR or HIPAA compliance, but the value depends on whether the platform provides enforceable controls and audit evidence; not just policy templates. For GDPR, that often means reducing unauthorized exposure of personal data and improving traceability across SaaS and AI workflows. For HIPAA, it typically means preventing PHI from entering AI tools without appropriate safeguards, and maintaining clear logs of enforcement decisions for compliance reviews.
Deployment time varies widely based on architecture and scope, but most rollouts follow a similar pattern. For organizations prioritizing speed, the practical question is how quickly you can move from “visibility” to “enforced controls” without disrupting users. In general, timelines are driven by:
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

