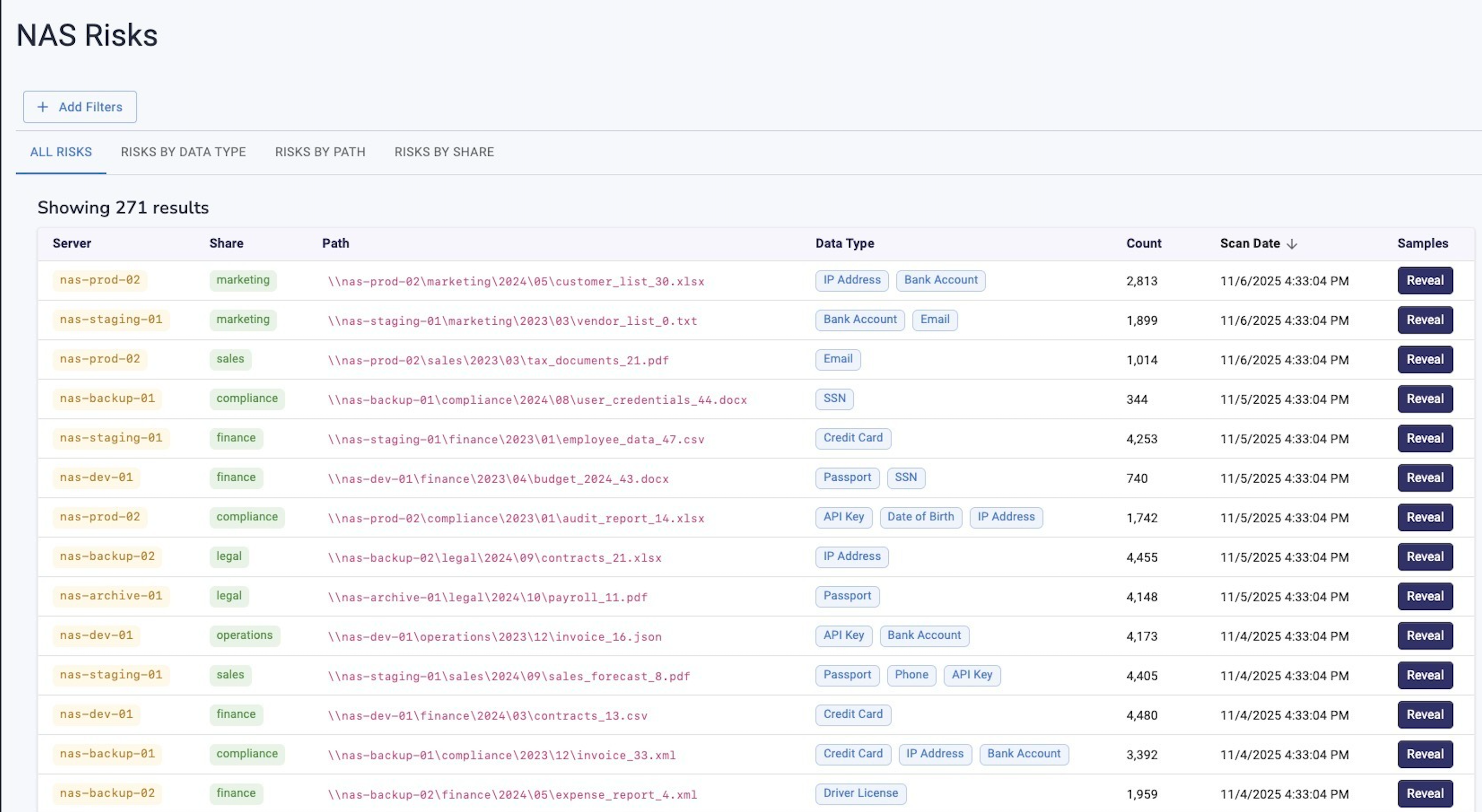
NAS Sensitive Data Discovery & Classification: The Complete 2025 Guide
TL;DR
- NAS environments store decades of unstructured data—PII, PHI, PCI, IDs, contracts—that security teams cannot see or classify.
- NAS Sensitive Data Discovery & Classification automatically scans SMB/CIFS/NFS file shares, extracts text, detects sensitive data, and maps exposure.
- The workflow includes connecting to NAS, enumerating folders, downloading files, scanning content with OCR/ML/regex, and producing actionable findings.
- Strac provides real-time and historical classification across NAS, SaaS apps, Cloud storage, and Endpoints with remediation and alerting.
✨ What Is NAS Sensitive Data Discovery & Classification?
Network Attached Storage (NAS) is the backbone of on-premises file storage for enterprises—SMB, CIFS, NFS, Windows File Servers, NetApp, Synology, QNAP, and DFS shares.
These file shares accumulate:
- HR records
- Customer spreadsheets
- Financial data
- Contracts
- Backups
- Images and PDFs
- Exported CSVs from SaaS apps
Because this is unstructured, deeply nested, and often decades old, organizations lose visibility into what sensitive data is stored inside these folders.
NAS Sensitive Data Discovery & Classification solves this by automatically:
- connecting to NAS
- enumerating all folders
- extracting + scanning contents
- classifying PII, PHI, PCI, Secrets
- mapping permissions
- uploading findings for remediation
It is the same core capability that Strac provides across Google Drive, Slack, Salesforce, Jira, O365, S3, RDS, and more — now extended to NAS.
✨ How NAS Sensitive Data Discovery & Classification Works
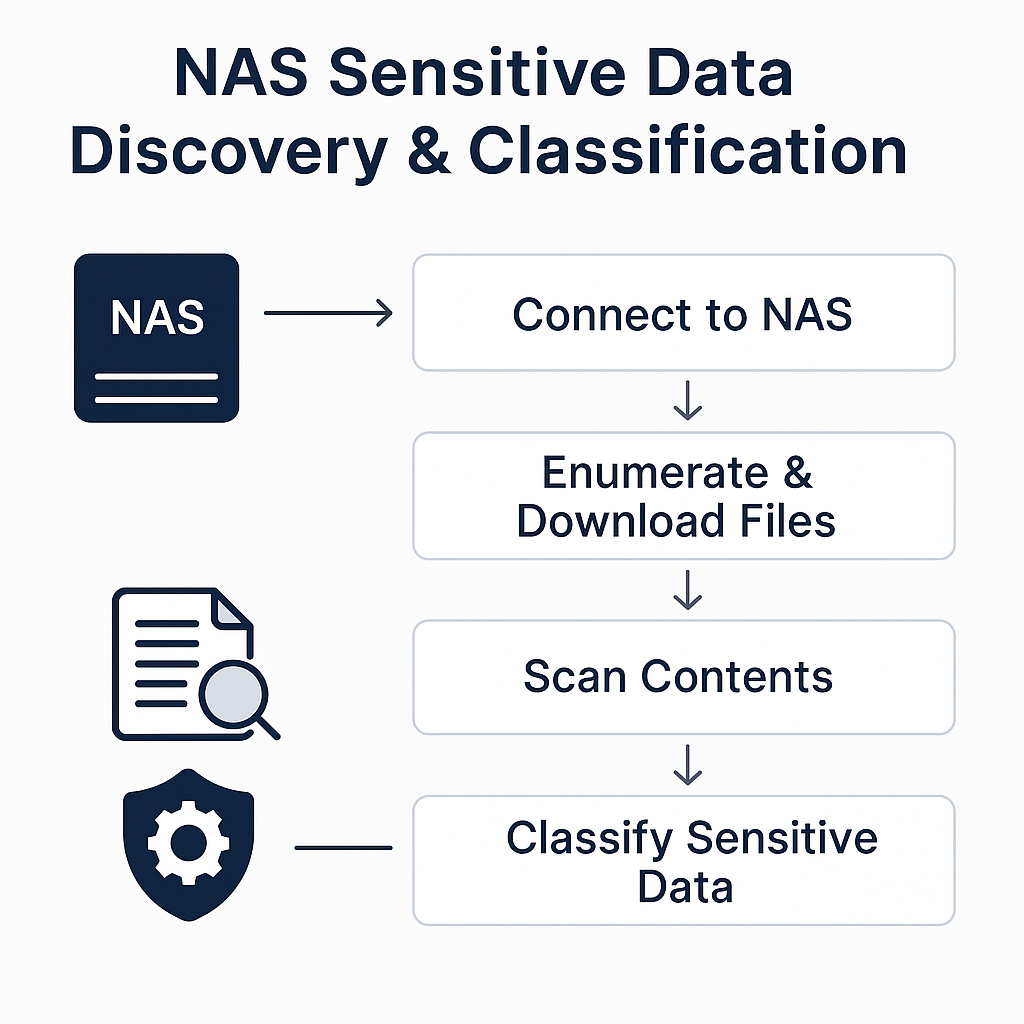
Connecting to NAS
The scanner authenticates via SMB/NFS credentials and identifies all accessible shares and directories.
Enumerating Files
It recursively walks folder structures and collects:
- file path
- owner
- permissions
- size
- modified timestamp
- file type
- MIME type
Downloading & Extracting Text
The engine retrieves files (fully or in chunks) and extracts content using:
- native text extraction
- OCR for images/PDFs
- ZIP/TAR/GZ/PST multi-level extraction
Classifying Sensitive Data
Strac’s engine identifies:
- PII: names, emails, addresses, phone numbers, government IDs
- PCI: card numbers, PAN, CVV
- PHI: diagnosis keywords, MRN, subscriber ID
- Financial data
- API keys and secrets (optional)
Classification uses regex + context keywords + ML embeddings + structure analysis.
Generating Findings
Each file receives:
- sensitive data types detected
- exposure level
- risk score
- prioritization tags
- recommended remediation actions
Results appear alongside other Strac integrations like Slack, Jira, Google Drive, Salesforce, and more:
https://www.strac.io/integrations
Why NAS Sensitive Data Discovery & Classification Matters
Most enterprises underestimate the volume of sensitive data in NAS. Over time, file shares become dumping grounds for:
- customer exports
- CRM/UI logs
- employee data
- financial records
- legacy backups
- ZIP archives from decommissioned systems
Visibility Risk
No one knows where sensitive data lives.
No one knows who can access it.
No one knows what is overexposed.
Shadow AI Risk
Employees increasingly upload NAS files into:
- ChatGPT
- Gemini
- Copilot
- Claude
This creates uncontrolled exfiltration.
Compliance Risk
Multiple frameworks require mapping sensitive data in on-prem storage:
- PCI DSS
- HIPAA
- ISO 27001
- SOC 2
- GDPR
Without NAS scanning, compliance evidence is incomplete.
Access Risk
NAS frequently contains:
- Everyone-read access
- Guest access
- Orphaned AD permissions
- Inherited misconfigurations
This is where breaches originate.
Common Challenges in NAS Sensitive Data Discovery & Classification
Terabytes of Unstructured Data
Legacy archives, backups, PST files, and multi-level folders make discovery hard.
Strac uses incremental scanning, hashing, and change detection to avoid rescanning everything.
Deeply Nested File Structures
Some companies have 10–20 levels of nested folders.
Strac’s optimized crawler handles unlimited depth.
Mixed Document Types
DOCX, PDF, XLSX, CSV, TXT, PPTX, ZIPs, logs, images, emails — Strac extracts them all.
Permissions Mapping
Many breaches stem from misconfigured access.
Strac identifies:
- world-readable folders
- external access
- AD group inheritance
- stale users
Prioritization
Instead of scanning everything equally, Strac highlights:
- highest-risk folders
- files with large amounts of PII/PHI/PCI
- exposed sensitive data
- PCI hotspots
- PHI clusters
✨ Real-World Use Cases for NAS Sensitive Data Discovery & Classification
Finding Legacy PCI Card Data
Old spreadsheets and CSVs often contain full card numbers.
Identifying PHI in Support Dumps
Support teams export customer data, then drop it into NAS without protection.
Discovering SaaS Exports
Salesforce, Zendesk, Jira, HubSpot exports often contain sensitive fields and end up in NAS folders.
Detecting Overexposed Folders
Inherited permissions allow entire departments to access sensitive data left in shared drives.
Audit Preparation
Auditors require proof of:
- data classification
- data minimization
- access restrictions
- breach risk reduction
Strac generates audit-ready evidence.
NAS Sensitive Data Discovery & Classification With Strac
Strac is a unified Data Security Platform offering:
- NAS and on-prem file server scanning
- SaaS DLP for Slack, Google Workspace, O365, Salesforce, Jira, Zendesk, etc.
- Cloud DSPM for AWS/Azure/GCP storage
- Endpoint DLP for macOS, Windows, Linux
- Browser DLP for Gen AI upload blocking
Key NAS capabilities include:
- Agentless scanning inside customer environment
- OCR + ML classification
- Real-time + historical scanning
- Alerts to Slack, Teams, Email
- Unified view of exposure across NAS + SaaS + Cloud + Endpoint
- Roadmap: Remove public access, fix permissions, quarantine files
Explore integrations:
https://www.strac.io/integrations
NAS Sensitive Data Discovery & Classification FAQs
Is NAS scanning required for compliance?
Yes. PCI, HIPAA, ISO, SOC 2, and GDPR require organizations to know where sensitive data resides—NAS included.
Does scanning slow down the NAS?
Strac uses throttled, incremental crawlers to avoid load spikes.
Does data leave the customer’s environment?
No. Scanning happens on-prem. Only metadata and findings are sent to Strac Vault (or stay fully on-prem if deployed self-hosted).
Can Strac remediate risks automatically?
Remediation roadmap includes:
- removing “Everyone” access
- removing guest access
- notifying file owners
- quarantining files
Does Strac understand Windows AD permissions?
Yes. Strac reads ACLs, inheritance, and AD group structures.











.webp)














.webp)




.avif)


