DLP On Premise (Self-Hosted): The Ultimate Data Security Within Your Own Environment
TL;DR
- DLP on premise means the Data Loss Prevention system runs entirely inside the customer’s environment — either in their own data center or private cloud (e.g., customer’s AWS or Azure account).
- It ensures data never leaves the customer’s perimeter, providing maximum control and compliance.
- On-prem DLP is the best security solution for enterprises that prioritize sovereignty, privacy, and zero data egress.
- Strac DLP can be deployed on-premise or in your private cloud, offering discovery, classification, and remediation — without any data ever leaving your environment.
What Is DLP On Premise?
DLP on premise (Data Loss Prevention on-premise) refers to deploying DLP software entirely within your own infrastructure —
either inside your corporate data center or within your private cloud (such as your own AWS, Azure, or GCP environment).
Unlike traditional SaaS-based DLPs, an on-premise DLP never transmits or stores data outside your environment.
Every discovery scan, classification, and remediation action occurs locally, inside your network or private cloud.
In simple terms:
On-premise DLP = Your data, your infrastructure, your control — 100% contained.
Why Enterprises Choose DLP On Premise (Self-Hosted)
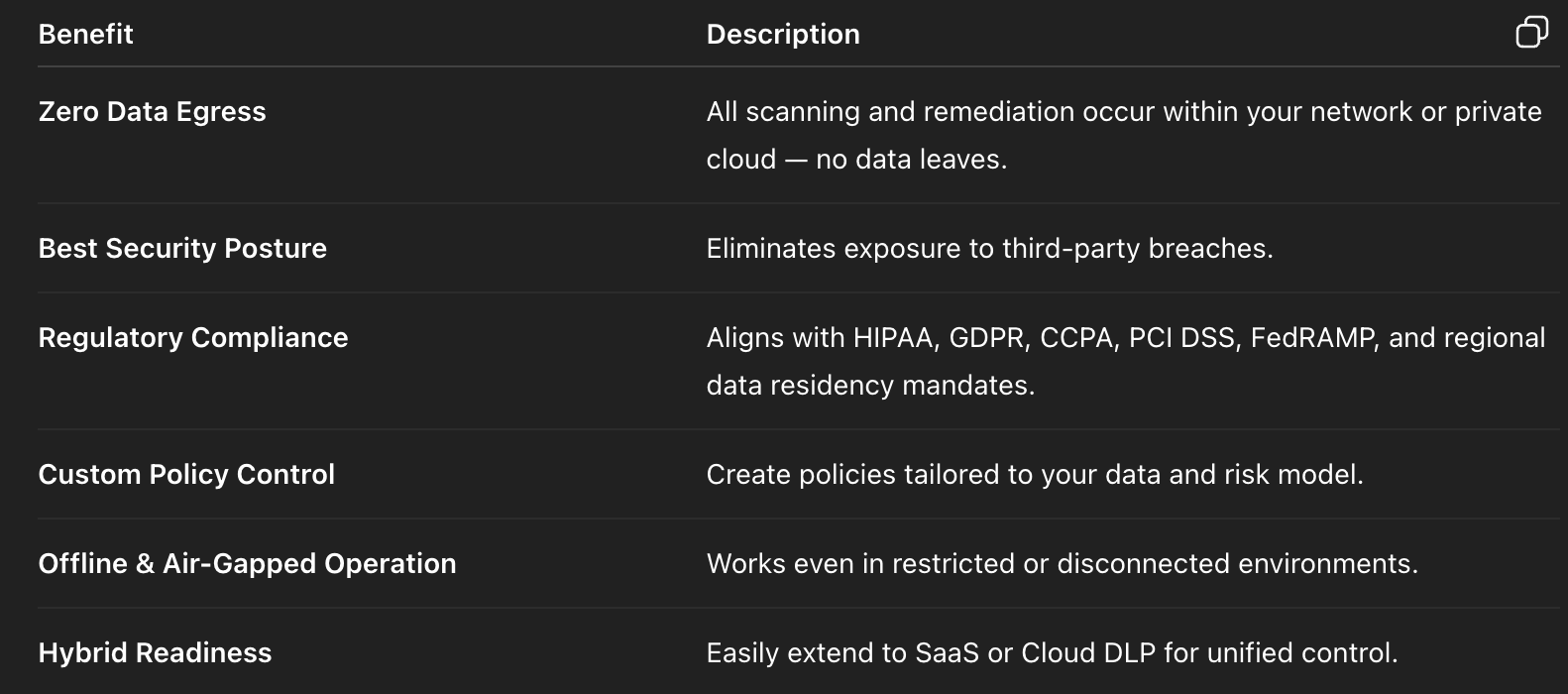
1. Data Never Leaves the Customer’s Environment
This is the single most important benefit.
In an on-premise deployment, all scanning, inspection, and remediation are performed within your VPC or data center.
No file, record, or metadata ever leaves your boundary — ensuring zero data egress and complete confidentiality.
2. Strongest Security Posture
Since data never leaves your infrastructure, on-prem DLP offers the highest possible level of protection.
Even if a vendor is compromised, your data remains untouched because it never travels outside your control plane.
3. Ideal for Regulated and Privacy-Conscious Industries
Sectors like financial services, healthcare, defense, and government prefer on-prem deployments for compliance with HIPAA, GDPR, FedRAMP, PCI DSS, and local data residency laws.
4. Customizable Policies and Tight Control
On-prem DLP allows deep customization:
- Tailor regex, keyword, or ML-based detections.
- Integrate with internal IAM or SIEM tools.
- Choose when and how to remediate.
No dependency on a vendor’s hosted infrastructure.
How DLP On Premise (Self-Hosted) Works
A modern on-premise DLP system consists of lightweight scanners, agents, and APIs that operate inside your private network or cloud.
Architecture:
- DLP Server (Deployed in Your VPC or Data Center)
Hosts policies, discovery jobs, and audit logs. - Scanners and Agents
Deployed close to your data sources — databases, file servers, endpoints. - Local Remediation Workflows
Redact, mask, or delete sensitive data in place. - Secure Admin Console
Runs locally or privately, accessible only to your administrators.
On-Prem DLP in Private Cloud (Customer AWS Example)
Many enterprises now prefer private cloud on-prem deployments.
For example, with Strac:
- You deploy Strac’s DLP engine inside your AWS account (ECS, EKS, or EC2).
- Strac scans S3, RDS, DynamoDB, or EBS volumes directly from within your VPC.
- All data classification and remediation happen locally — no data or metadata leaves your AWS.
This architecture gives you the benefit of the cloud’s scalability while maintaining the same control and sovereignty as an on-premise deployment.
✅ You own the compute, storage, and logs. Strac only provides the intelligence — deployed inside your perimeter.
Benefits of DLP On Premise (and Private Cloud)
Strac: The Modern Hybrid DLP Platform
Strac offers the industry’s most flexible DLP platform, allowing enterprises to choose on-premise, private cloud, or SaaS deployment — all with the same capabilities.
Strac On-Premise Highlights:
- Deployable inside your AWS account or data center.
- Scans S3, RDS, file servers, and internal applications.
- Performs in-place redaction, masking, and access revocation.
- Sends real-time alerts to Slack, Teams, or SIEM — without sharing raw data externally.
- Integrates with compliance frameworks like SOC 2, HIPAA, and PCI DSS.
Example:
A Fortune 500 healthcare provider deployed Strac inside its private AWS cloud to:
- Discover PHI in RDS and file servers.
- Redact sensitive data from support ticket attachments.
- Keep 100% of data inside its own VPC, meeting both HIPAA and internal infosec policies.
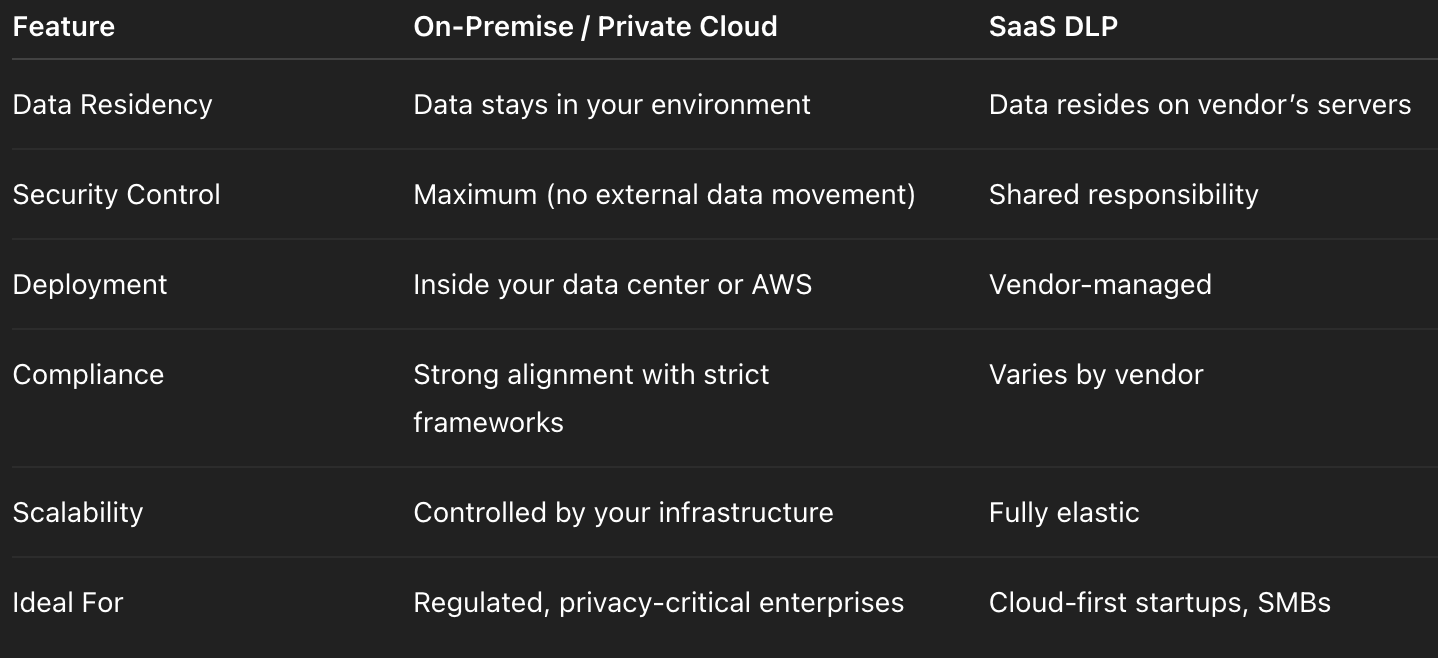
On-Premise vs SaaS DLP: Choosing the Right Fit
🌶️ Spicy FAQs on DLP On Premise (Self-Hosted)
Why is DLP on premise considered the best security solution?
Because it guarantees data never leaves your environment.
All sensitive data scanning, classification, and remediation happen inside your infrastructure, eliminating third-party exposure.
Can I deploy Strac on my private AWS account?
Yes. Strac’s self-hosted mode allows you to deploy the entire DLP engine within your AWS, giving you full ownership of data, compute, and logs.
Is on-premise DLP future-proof?
Absolutely. With hybrid DLP models, you can extend the same Strac platform to protect SaaS apps (like Slack, Google Drive, O365) while keeping your private data entirely local.
How do I ensure no data leaves my environment?
Strac’s self-hosted model ensures that no data, metadata, or logs are transmitted externally.
All processing occurs within your VPC, following your IAM and network controls.
Final Thoughts
DLP on premise represents the gold standard of data protection.
In a world where data breaches and supply-chain risks are increasing, the ability to keep every byte of sensitive data inside your own environment is the ultimate defense.
Strac gives you the flexibility to deploy wherever you prefer — your data center, private AWS, or hybrid cloud — while ensuring zero data egress and the strongest possible security posture.
When it comes to sensitive data protection, nothing beats DLP on premise — powered by Strac.











.webp)














.webp)










.avif)


