Data Discovery On Premise (Self-Hosted): Complete Visibility Without Data Ever Leaving Your Environment
TL;DR
- Data Discovery on premise means identifying and classifying sensitive data within your own data center or private cloud (e.g., customer’s AWS or Azure account) — without ever sending that data externally.
- It gives organizations full visibility and control over sensitive data such as PII, PHI, and PCI across internal databases, file servers, and applications.
- On-prem discovery ensures data sovereignty, zero egress, and the strongest security posture — ideal for regulated or privacy-conscious enterprises.
- Strac Data Discovery can be deployed entirely inside your environment, ensuring data never leaves your infrastructure while still offering advanced AI-driven classification and compliance reporting.
What Is Data Discovery On Premise (Self-Hosted)?
Data Discovery on premise refers to the process of automatically identifying, scanning, and classifying sensitive information stored within your organization’s internal systems or private cloud.
Unlike cloud-hosted discovery tools, on-prem discovery solutions are deployed within your environment — for example, inside your AWS VPC, Azure subscription, or physical data center — ensuring that no data or metadata ever leaves your boundary.
Simply put:
On-premise Data Discovery = Visibility + Compliance + Zero Data Exposure.
It’s how security-conscious enterprises find and protect sensitive data without compromising privacy or regulatory requirements.
Why Data Discovery On Premise (Self-Hosted) Matters
1. Data Never Leaves the Customer’s Environment
This is the core value of on-prem discovery.
All scanning, classification, and metadata processing happen locally — inside your private cloud or on-prem servers.
No data samples, file contents, or metadata are transmitted outside your network, ensuring zero data egress and absolute sovereignty.
2. Stronger Security and Compliance
With on-prem discovery, organizations maintain total control of their sensitive data locations and movement.
This architecture is ideal for compliance with:
- HIPAA (Health data protection)
- GDPR (European data residency)
- PCI DSS (Financial and cardholder data)
- FedRAMP, SOC 2, ISO 27001
3. Visibility Across Internal Data Stores
Data doesn’t just live in SaaS apps.
A huge amount of unstructured and semi-structured data lives within:
- File servers
- Windows shares
- Oracle / SQL / RDS databases
- ERP systems like SAP ECC or Oracle Siebel
On-premise discovery ensures you know exactly where that data resides.
How Data Discovery On Premise Works
1. Local Deployment
Strac’s discovery engine runs inside your data center or private AWS/Azure cloud — via Docker or Kubernetes containers.
2. Secure Data Source Connection
Connects to on-prem or private databases, file servers, and document stores securely using local credentials (no external API calls).
3. In-Place Scanning and Classification
Strac scans and classifies data in place, detecting sensitive data elements such as:
- PII (Name, SSN, DOB, Address)
- PHI (Diagnosis, Medical Record Number)
- PCI (Credit Card, CVV)
- Financial and Confidential data
4. Local Reporting and Remediation
All logs, findings, and dashboards remain within your VPC or internal environment.
Admins can remediate (redact, mask, delete) data locally — without data leaving your perimeter.
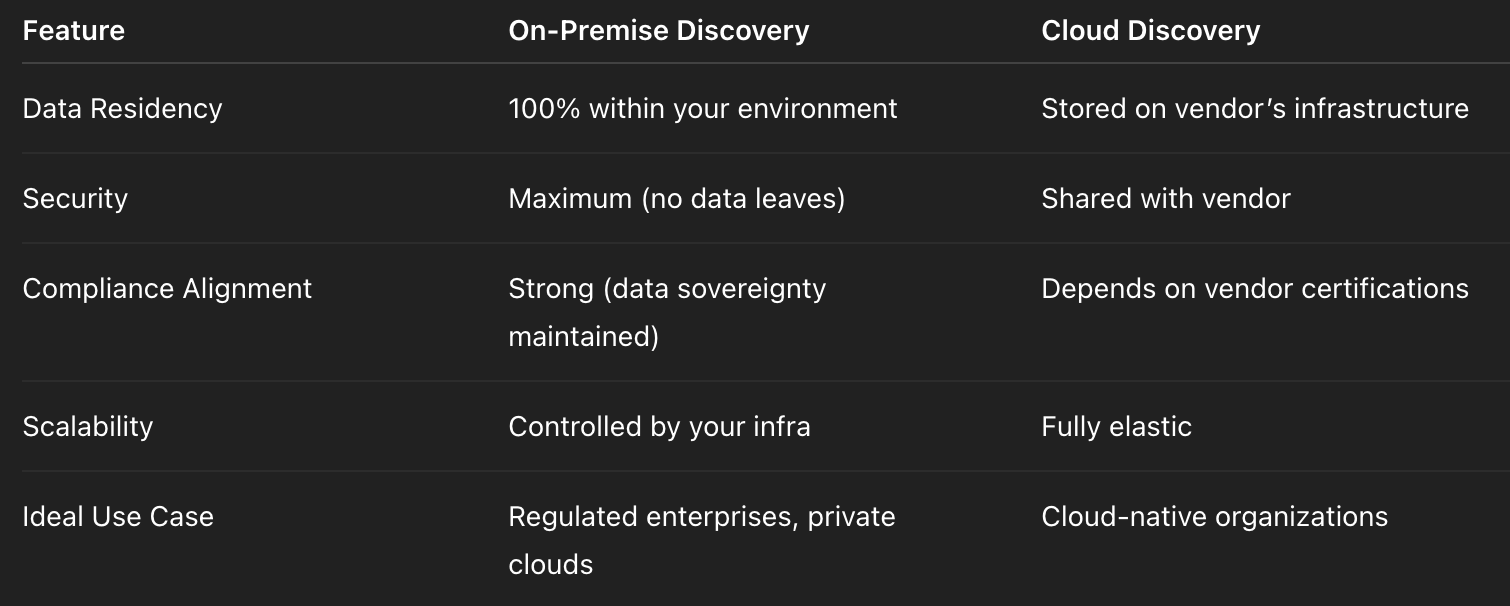
Data Discovery On Premise vs Cloud Discovery
Strac: Unified Data Discovery Across SaaS, Cloud, and On-Prem
Strac provides a single platform for Data Discovery and Classification that works seamlessly across SaaS, Cloud, and On-Prem environments — using the same core detection and remediation engine.
Strac On-Prem Deployment Highlights:
- Deployed directly in your AWS VPC, Azure subscription, or on-prem servers.
- Scans RDS, S3, DynamoDB, SQL, Oracle, SAP ECC, and file servers.
- Detects sensitive data like PII, PHI, PCI, and financial information.
- No data leaves your environment — Strac runs 100% locally.
- Integrates with your SIEM, SOAR, and IAM stack via internal APIs.
🌶️ Spicy FAQs on Data Discovery On Premise
Why is on-premise data discovery more secure?
Because no data ever leaves your environment.
All scanning, metadata analysis, and reports remain within your network or private cloud, ensuring zero risk of data leakage.
Can Strac integrate with on-prem databases and ERP systems?
Yes. Strac supports Oracle, SQL Server, SAP ECC, PostgreSQL, and file shares for on-premise data discovery and classification.
How does Strac handle scalability in private environments?
Strac’s containerized deployment allows you to scale scanners horizontally across your own infrastructure (ECS, EKS, or bare metal).
Can I combine on-prem and cloud data discovery?
Absolutely. Strac offers hybrid DSPM, letting you discover data across SaaS (Google Drive, Slack, Salesforce) and on-prem sources with unified policies and dashboards.
Final Thoughts
Data Discovery On Premise gives enterprises complete visibility and control — without compromising privacy, compliance, or security.
It’s the best solution for organizations that want to understand where sensitive data lives while ensuring that data never leaves their environment.
With Strac, you get the power of AI-driven discovery and classification — deployed entirely within your infrastructure, ensuring the strongest possible data protection and complete compliance readiness.
When security and sovereignty matter, Data Discovery On Premise with Strac is the ultimate choice.











.webp)














.webp)










.avif)


