TL;DR
- Prove outcomes with SaaS DLP evidencepacks that log actor, action, timestamp, item, rule, and before/after ACL soaudits are a query, not a project.
- Extend SaaS DLP to GenAI sessions;protect prompts and responses, tokenize or redact sensitive content, andrestrict unapproved tools and outbound domains.
- Measure SaaS DLP impact with the rightKPIs: mean time to remediate in minutes, percent auto-resolved without tickets,low false-positive rate, multi-surface coverage, and weekly exposure burn-down.
- Operate SaaS DLP on adaily/weekly/monthly rhythm: daily deltas and digest evidence, weekly ruletuning and exception closure, monthly least-privilege scorecards and tabletopexercises.
- Use SaaS DLP owner notifications thatdrive action; concise messages explain what changed, why it changed, and how torequest a time-boxed exception.
- Outcome with SaaS DLP: real-timeremediation across Slack, Gmail, Google Drive, Zendesk, and GenAI, withexposure trending down in days and compliance ready by default.
Your company runs on four streams today. Files, chat, tickets, and prompts. Each is fast. Each is social. Most leaks in SaaS are not exotic. They are public links that never expired, screenshots parked in chat, ticket attachments that carry exports, and GenAI prompts that echo customer data. SaaS DLP is how you see those risks early, remove exposure in place, and keep clean evidence for auditors.
SaaS DLP is not a perimeter project. It is a workstream discipline.
SaaS DLP is about removing exposure where the work happens. If you can scan, label, right-size access, redact or quarantine in place, notify owners, and produce evidence in minutes, you are doing it right.
This guide is the operating model I use as a founder when I want measurable risk reduction this week, not next quarter.
🎥Why SaaS DLP Matters Right Now
Cloud work has four high-velocity streams: files, chat, tickets, and prompts. Each can expose crown-jewel data in seconds. Customers and regulators now expect more than alerts. They want proof that you discovered sensitive data, right-sized access, sanitized content, and recorded what changed.
Outcome to aim for:
- Fewer public shares across Google Drive and SharePoint.
- Inline redaction in Slack and Zendesk that preserves the conversation.
- Short link lifetimes by default, longer only by exception.
- Evidence packs that show who fixed what and when.
✨SaaS DLP For Files And Drives
SaaS DLP in Google Drive and SharePoint
Unclassified files and generous ACLs make link sprawl inevitable. Screenshots and PDFs hide PAN, PII, and secrets that simple patterns miss.
What to implement:
- Discovery with OCR for files, versions, and comments.
- Stable labels like Data:PCI:PAN, Data:PHI, Data:Secrets.
- Least privilege by default. Remove anyone-with-link, use group-based ACLs.
- Quarantine or targeted redaction to keep work moving when context matters.
- Owner notifications with one-click fixes and clear policy references.
- Immutable evidence that captures actor, action, timestamp, item, rule, before and after ACL.
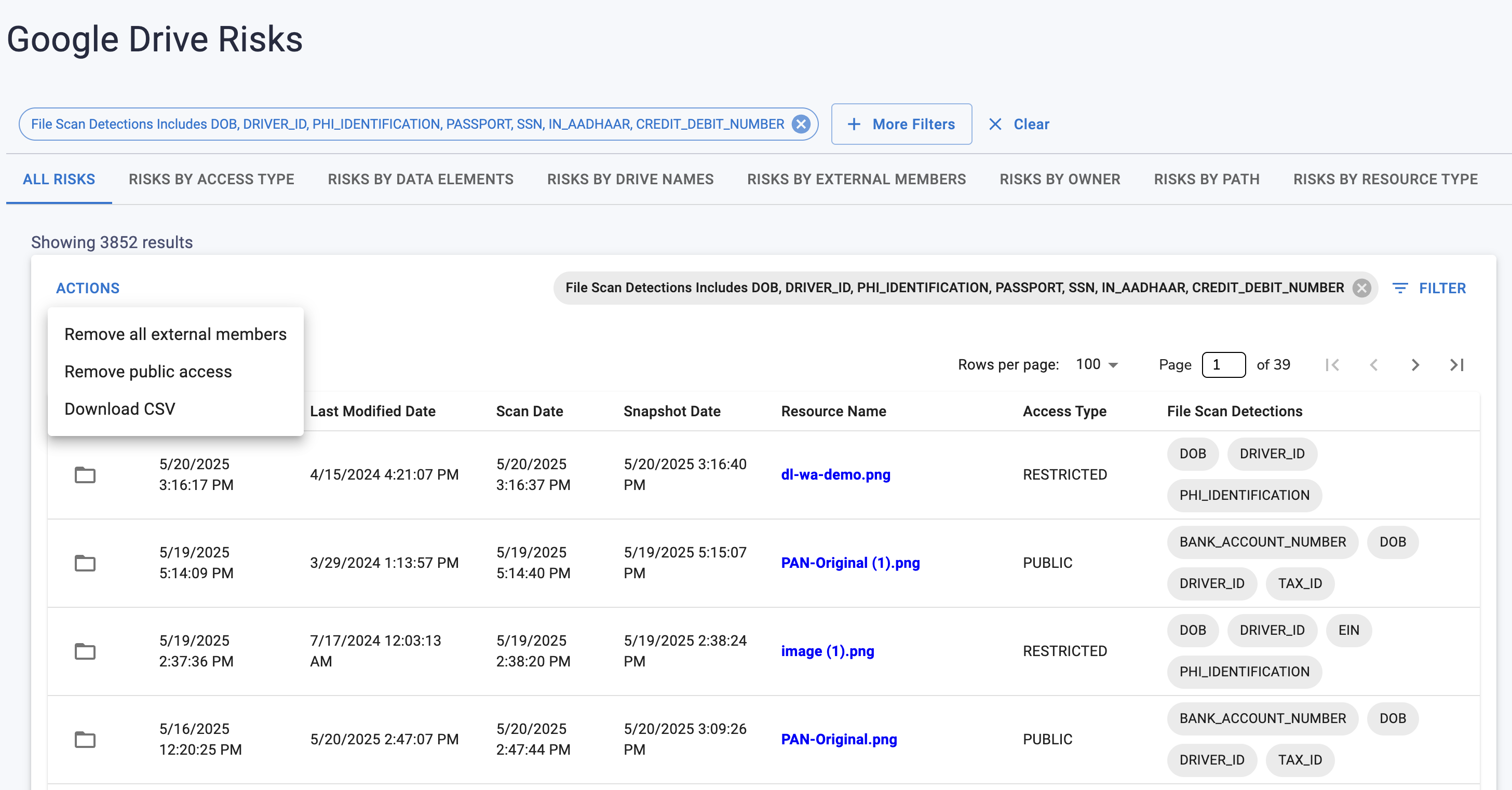
Outcome: External exposure removed, access simplified, audit trail complete.
✨SaaS DLP in Slack and Microsoft Teams
Chat accelerates decisions and also propagates sensitive strings. Guests join broad channels. Bots and webhooks post logs with secrets.
What to implement:
- Inline message redaction for PAN, PHI, and secrets that keeps the conversation readable.
- File quarantine for risky uploads with object hash controls to block re-shares.
- Automatic link expiry inside sensitive channels.
- Guest and bot governance. Curated channels only, token rotation on a schedule.
- Owner alerts that include the rule hit and the exact remediation taken.

Outcome: High-risk content never lingers. Collaboration continues. Evidence is captured at the moment of fix.
✨SaaS DLP in Jira and Confluence
Tickets absorb PHI and PII. Attachments carry exports. GenAI prompts and responses can echo secrets.
What to implement:
- Context-aware scanning for ticket bodies, comments, and attachments.
- Masking in text and redaction for attachments when feasible.
- Retention controls. Shorter lifetime for regulated content, legal hold only when necessary.
- Assignee guidance. Short checklists that close the loop without slowing service.
- Weekly analytics by queue and model to target training and process fixes.
- Access reviews to remove idle vendor accounts and narrow queue permissions.
Outcome: Support and AI stay productive while sensitive data is governed and auditable.
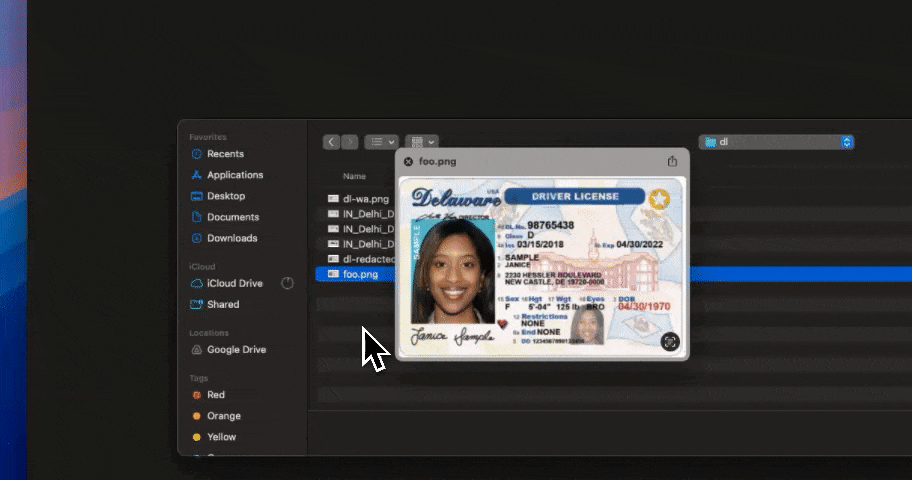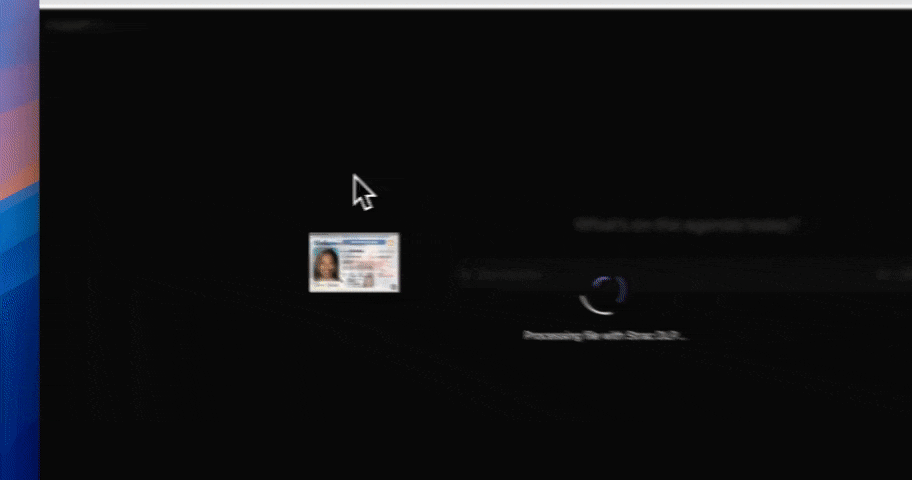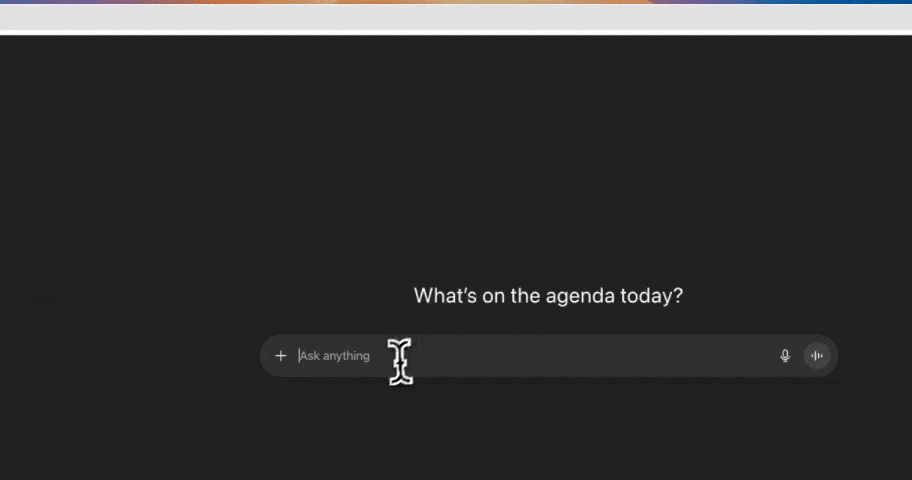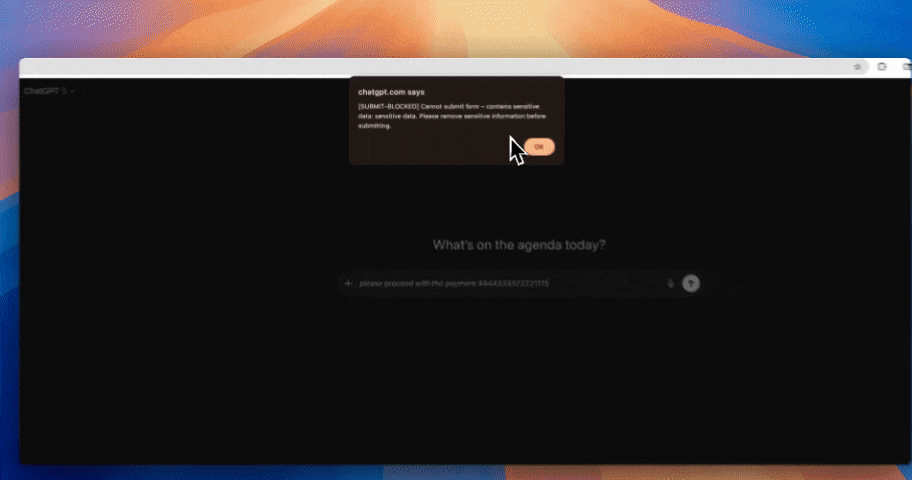
✨SaaS DLP in the Browser (GenAI & Web Apps)
Most data exposure now happens where people work: in the browser. Users paste prompts into ChatGPT, drag files into Gemini, share dashboards from BI tools, and grant access in Drive or SharePoint — all within a few clicks. Network-only controls miss this. Endpoint agents slow teams down. The answer is policy that works inline, inside the browser session, at the exact moment risk appears.
What makes the browser the control point
- It’s where prompts, files, screenshots, and copy-paste happen.
- It’s where SaaS permissions are granted and links are made public.
- It’s the last mile before sensitive content leaves your environment for model inference or external collaborators.
What “good” SaaS DLP in the browser looks like
- Real-time inspection of text inputs, file uploads, and paste/drag-drop — before content is sent.
- Context-aware decisions that consider app, user, data type, and destination (e.g., allowlist GenAI domains, block unknowns).
- Gentle UX that guides users with inline prompts, not blunt error pages; safe by default, informative when blocked.
GenAI-specific guardrails that matter
- Prompt protection: detect PII/PHI/PCI, secrets, and code in prompts; mask or tokenize before the model sees it.
- Output hygiene: scan model responses for sensitive echoes and strip before saving, sharing, or copying out.
- Tool scoping: only allow approved plugins, actions, and outbound domains during a GenAI session.
- File control: intercept uploads to AI tools and block or route to a redaction workflow when regulated data is present.
Strac’s browser-level DLP for GenAI delivers fast, visible risk reduction by enforcing policy inside prompts and file uploads while keeping teams moving. Key values you get immediately:
- Inline redaction and tokenization that stop PII, PHI, PCI, secrets, and code from reaching ChatGPT, Gemini, or Copilot
- OCR that catches sensitive data inside screenshots, dashboards, and PDFs that others miss
- Agentless rollout that protects major SaaS and GenAI tools without device agents or heavy change management
- In-place remediation that auto-revokes risky links, right-sizes permissions, and guides users to approved tools
- Measurable outcomes with time to fix in minutes, exposure trending down week over week, and minimal audit-ready evidence aligned to GDPR, HIPAA, PCI, and SOC 2
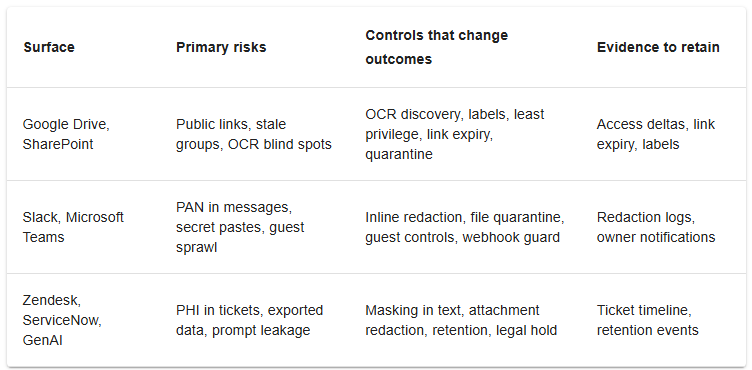
✨Table: SaaS DLP Surfaces And Controls
✨Building A SaaS DLP Rhythm That Sticks
Daily operating loop
- Run deltas to catch new exposures.
- Expire links and resolve owner-confirmed fixes.
- Export a short evidence digest for the security channel.
Weekly operating loop
- Review drift in shares, guests, and bot scopes.
- Tune rules for false positives without losing coverage.
- Age and close exceptions. Time-box everything.
Monthly operating loop
- Publish least-privilege scorecards by workspace or team.
- Revisit policy coverage for files, chat, tickets, and prompts.
- Run tabletop exercises using real incidents from the month.
Outcome: Time to remove exposure goes down. Exceptions do not become permanent. Audits become a query, not a project.
✨Owner Messages That Drive Action
Short, specific, and respectful messages get results.
Subject: Risky share removed on your file
We detected Data:PCI:PAN in Q2-Revenue-Export.xlsx at 10:17 CET. Public link expired and external collaborators removed. Please confirm the new access list or request a time-boxed exception. Guidance and evidence attached.Why this works: it explains what changed, why it changed, and what the owner should do next. It includes enough context to avoid back-and-forth.
✨Evidence Packs That Satisfy Auditors
Keep a minimal, consistent set:
- Incident ID and rule name.
- Item and location.
- Actor, action, timestamp.
- Before and after ACL.
- Redaction or quarantine record.
- Owner notification and response.
- Exception details with expiry.
- Retention or legal hold events.
Store evidence centrally and back it up. Do not scatter it across email threads.
✨Where Strac Fits In A SaaS DLP Program

1.Agentless coverage for SaaS and GenAI
Scan files, comments, chat, tickets, prompts, and attachments. Include OCR for images and PDFs. No endpoint software to manage.
2.controls to remediate exposure
Redact messages, mask fields, quarantine files, expire links, revoke sharing, notify owners, and log evidence. Alerts become actions.
3. Accurate detection at scale
Patterns and machine learning for PAN, PII, PHI, and secrets across structured and unstructured content. Tiered policies to balance sensitivity and noise.
4. Operational hygiene by design
Daily deltas, drift reporting, bulk remediation, least-privilege scorecards. Evidence exports map to SOC 2, HIPAA, PCI DSS, and GDPR.
Outcome: measurable reduction in exposure across Slack, Gmail, Google Drive, Zendesk, and GenAI within days, not months.
🌶️Spicy FAQs For SaaS DLP
What makes SaaS DLP different from traditional DLP?
Traditional DLP was built for endpoints and email — it watches what leaves your laptop.
SaaS DLP, on the other hand, protects what’s already in the cloud.
Sensitive data isn’t just “leaving”; it’s living inside tools like Slack, Google Drive, and Salesforce.
That’s where Strac comes in — scanning, classifying, and remediating sensitive data inside your SaaS apps in real time.Can SaaS DLP actually stop data leaks or just alert them?
Most tools just alert and pray.
Strac goes further — it can block, redact, label, delete, or revoke access automatically.
Think of it as DLP with a "muscle memory" — once it finds risk, it acts instantly.
Isn’t SaaS DLP overkill if my SaaS apps already have permissions and sharing controls?
That’s the illusion.
Most data leaks don’t happen because of missing controls — they happen because humans misconfigure or forget them.
Strac acts like your “autopilot,” constantly auditing file shares, links, and messages to ensure nothing slips through cracks.How is SaaS DLP different from DSPM or CASB?
· CASB controls access and visibility.
· DSPM tells you where your data lives and who can access it.
· SaaS DLP ensures your data stays protected wherever it lives — by redacting, labeling, deleting, or blocking risky content in real time.
· In short, DSPM discovers, DLP defends.
Why do I need SaaS DLP if I already have SOC 2, ISO 27001, or Vanta/Drata compliance?
Compliance is the receipt — not the security.
Auditors care about controls on paper.
Attackers care about the data you left exposed on Slack or Google Drive.
SaaS DLP ensures your actual environments live up to your compliance badges.Can SaaS DLP handle Gen AI tools like ChatGPT, Gemini, or Copilot?
Absolutely — and it must.
Employees paste sensitive data into AI tools daily.
Strac’s Browser DLP integration monitors, blocks, or redacts sensitive content before it hits those models.
Think of it as guardrails for your company’s AI era.What kind of remediation actions does SaaS DLP perform?
Depending on where the data lives:
· Redact or delete sensitive text in Zendesk, Slack, Jira, or email.
· Label or revoke access in Google Drive, OneDrive, or Dropbox.
· Block uploads on Gen AI sites or personal cloud apps.
· Strac adapts remediation to each SaaS platform — intelligently and automatically.
Does SaaS DLP create employee friction?
Not with Strac.
The goal isn’t to shame — it’s to educate and guide.
Admins can choose “alert-only” mode or “soft block” with pop-ups like:
“This message contains customer data. Please remove before sending.”
It’s compliance with empathy.
How long does it take to deploy SaaS DLP?
Legacy DLP = 6-month rollout and 12 angry emails to IT.
Strac SaaS DLP = 30 minutes.
No agents, no VPNs. Just OAuth and instant visibility across your connected apps.
Who’s responsible for SaaS data leaks — the vendor or the company?
Always the company.
Salesforce won’t tell you if an employee uploaded PII into an unencrypted field.
Slack won’t warn you if a contractor shares a secret in #support.
You own the data — and the risk.
That’s why SaaS DLP exists.
.avif)
.avif)
.avif)
.avif)
.avif)
Discover & Protect Data on SaaS, Cloud, Generative AI















.webp)














.webp)


.webp)










.gif)
