Sensitive Data scanning: Top 13 PII Data scanning tools in 2026
Let's take a look at the top 13 sensitive data scanning tools for 2026
As businesses digitize faster than their security programs can adapt, personally identifiable information (PII) is no longer confined to a single database or system. It spreads across SaaS applications, cloud storage, support tickets, internal chat tools, file uploads, and increasingly, generative AI workflows. For security and compliance teams, the challenge is no longer whether PII exists, but whether it can be continuously located, assessed, and controlled.
This is where PII scanning software becomes essential. Modern PII scanning software continuously discovers and analyzes sensitive personal data across distributed environments, helping organizations understand where PII lives, who can access it, and where it is exposed. Without this visibility, enforcing privacy controls, responding to incidents, or proving compliance becomes guesswork.
This article will guide you through why data scanning is important, what to consider when choosing a data scanning tool, and provide a detailed review of the top 10 tools this year, positioning you to make informed decisions that protect your company's data integrity.
Personally Identifiable Information (PII) refers to any data that can identify an individual — directly (name, SSN, email) or indirectly (IP address, login pattern, geolocation).
PII scanning is the process of automatically locating, classifying, and monitoring such data across your environment. It answers questions like:
Without automated scanning, organizations are essentially blind to their data exposure — and therefore at risk of breaches, fines, and loss of trust.
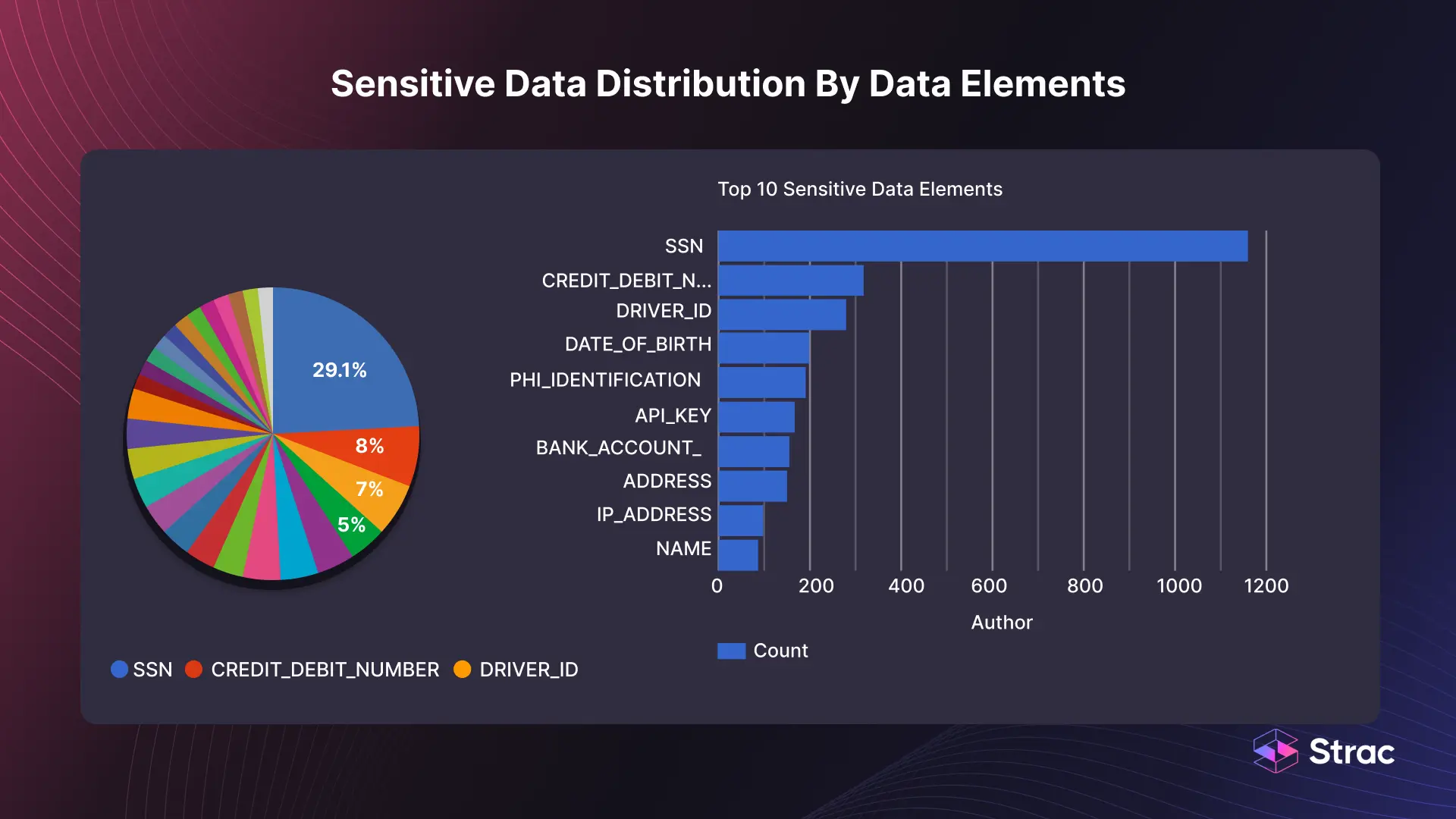
Data scanning is a vital component in the cybersecurity arsenal of organizations across various industries. As digital landscapes evolve and data breaches become more sophisticated, the need for robust security measures that preemptively identify and mitigate risks has never been more crucial.
The primary importance of data scanning lies in its ability to maintain security and ensure compliance with stringent regulatory standards. Industries such as healthcare, finance, and e-commerce, where sensitive personal and financial information is frequently processed, require rigorous data protection measures to safeguard against breaches and unauthorized access. Data scanning tools help detect vulnerabilities in systems before they can be exploited by malicious actors, thus preventing potential data breaches.
Moreover, proactive data scanning facilitates ongoing vigilance in a cybersecurity landscape that is constantly changing. These tools scan databases, applications, and network systems to identify anomalies that could indicate a security threat or compliance issue, providing an early warning system to mitigate risks effectively. Regular data scanning not only helps in recognizing the immediate threats but also aids in understanding broader security trends, allowing organizations to adapt and strengthen their defenses against future attacks.
By implementing comprehensive data scanning practices, organizations can maintain a strong security posture, comply with global data protection regulations, and foster trust among customers and stakeholders.
PII scanning softwares solve this by:
Choosing the right data scanning tool is pivotal for enhancing your organization's cybersecurity posture. There are several critical criteria to consider to ensure that the tool not only meets your current needs but is also a viable long-term solution.

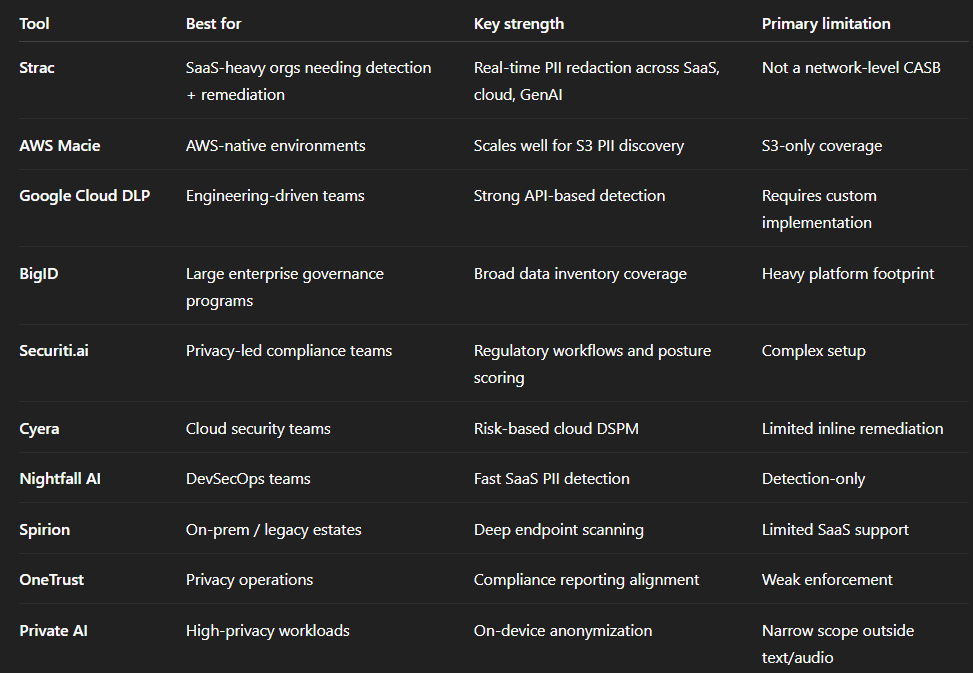
This table gives a quick, side-by-side look at popular PII scanning software, highlighting where each tool works best and where it may fall short, so you can quickly narrow down the right option for your needs.
Now, let’s take a deeper look at the top data scanning tools you can pick in 2026.
Overview:
Strac is an all-in-one Data Discovery, DSPM, and DLP platform that automatically scans, classifies, and remediates PII across SaaS apps, Cloud platforms, GenAI tools, and Endpoints. It identifies sensitive information in real time and enforces security through redaction, masking, labeling, and access revocation — all from a single console.
Best For: Companies that need unified discovery + protection across Slack, Google Workspace, Office 365, Salesforce, Zendesk, Intercom, AWS, and GenAI apps.
Key Features:
Why It Stands Out:
Unlike traditional scanners that only detect data, Strac performs end-to-end remediation — helping you find, fix, and prevent PII exposure.

Overview:
Amazon Macie is a fully managed data discovery and classification service for S3. It uses ML to identify PII, financial data, and credentials across large-scale cloud storage.
Best For: Organizations storing sensitive data in AWS S3 buckets.
Key Features:
Limitation:
Only covers S3 data — not ideal for multi-cloud or SaaS environments.
Overview:
Google’s DLP API detects and classifies over 100+ data types in Cloud Storage, BigQuery, and custom applications.
Best For: Engineering teams building custom pipelines that require API-based detection and redaction.
Key Features:
Limitation:
Requires technical setup and limited visibility into SaaS or non-GCP systems.
Overview:
BigID is an enterprise-grade data discovery and privacy intelligence platform. It scans across structured, unstructured, and semi-structured data to map sensitive assets and access rights.
Best For: Large enterprises needing compliance-grade discovery and cataloging.
Key Features:
Limitation:
Heavy deployment; slower time-to-value for mid-market teams.
Overview:
Securiti combines DSPM, PrivacyOps, and Governance into one platform. It offers rich discovery, data lineage, and regulatory mapping.
Best For: Privacy and compliance teams managing multi-jurisdictional privacy laws.
Key Features:
Limitation:
High setup complexity; better suited for regulated industries.
Overview:
Cyera focuses on cloud-native DSPM — discovering and classifying data across cloud and SaaS environments to provide contextual risk intelligence.
Best For: Security teams needing risk scoring and data flow visualization.
Key Features:
Limitation:
Primarily cloud-focused; lacks remediation features like redaction or masking.
Overview:
Nightfall provides API-first DLP and PII scanning for modern SaaS applications such as Slack, GitHub, and Jira.
Best For: Engineering and DevSecOps teams wanting plug-and-play DLP APIs.
Key Features:
Limitation:
Detection-only focus; lacks native access control or remediation actions.
Overview:
A pioneer in endpoint and file scanning, Spirion offers on-premises PII discovery with strong customization and audit capabilities.

Best For: Enterprises with legacy infrastructure and strict data residency requirements.
Key Features:
Limitation:
Limited automation and SaaS/cloud coverage.
Overview:
Presidio is an open-source framework for PII detection, anonymization, and redaction. It supports text, audio, and images, and can be deployed locally.
Best For: Developers building custom privacy workflows or on-device detection.
Key Features:
Limitation:
Requires engineering effort; not plug-and-play for enterprise use.
Overview:
An affordable data visibility and protection suite for SMBs that includes file scanning and PII detection.
Best For: Mid-sized organizations securing file servers and local storage.
Key Features:
Limitation:
Lacks real-time SaaS or API-level scanning.
Overview:
OneTrust is a privacy and compliance management platform that includes PII discovery as part of its broader governance suite.
Best For: Enterprises focused on GDPR, CCPA, and ISO 27701 compliance alignment.
Key Features:
Limitation:
Not purpose-built for real-time DLP or SaaS integrations.
Overview:
Open Raven provides cloud-native data security and PII discovery for AWS, GCP, and Azure environments.
Best For: Cloud security teams needing continuous discovery and classification of unstructured data.
Key Features:
Limitation:
Limited support for SaaS and endpoint-level protection.
Overview:
Private AI offers on-device, privacy-preserving PII detection for text, audio, and video. It’s designed for companies that need GDPR-grade anonymization without sending data to the cloud.
Best For: Organizations that handle sensitive user communications or voice data (e.g., healthcare, finance, call centers).
Key Features:
Limitation:
Primarily focused on text/audio; less coverage for cloud-native SaaS.
A PII scanning tool automatically identifies personally identifiable information across your data sources. It can detect patterns like names, SSNs, emails, and credit card numbers.
PII scanning focuses on detection and discovery, while DLP (Data Loss Prevention) adds enforcement — blocking, redacting, or alerting when PII moves outside safe zones.
You can, but regex-only solutions have high false positives and lack context. Modern tools use ML, NLP, and OCR for accuracy.
Yes. Strac can be deployed inside your AWS account, ensuring sensitive data never leaves your environment.
PII scanning tools typically combine multiple detection techniques:
The best tools use a hybrid approach. Regex-only scanning produces excessive false positives, while ML-only approaches can miss obvious patterns.
Modern PII scanning tools can detect a wide range of sensitive data:
Personal Identifiers
Financial Data
Contact Information
Health Information (PHI)
Authentication & Secrets
Biometric Data
Custom Data
Checkout the entire catalog here: https://www.strac.io/blog/strac-catalog-of-sensitive-data-elements
The right frequency depends on data velocity and risk tolerance:
Real-time scanning (recommended)
Daily scanning
Weekly scanning
Monthly or quarterly
Best practice: continuous scanning for new or modified data, combined with periodic full scans.
Effectively, yes. While GDPR doesn’t explicitly mandate “PII scanning tools,” it requires capabilities that are nearly impossible without them:
Article 30 – Records of Processing
You must know what personal data you process and where it’s stored. PII scanning automates this discovery.
Article 17 – Right to Erasure
To delete a person’s data on request, you must first find it everywhere it exists.
Article 32 – Security of Processing
You must implement appropriate technical safeguards. You can’t protect data you don’t know about.
Article 33 – Breach Notification
You must assess what personal data was exposed during a breach. Scanning provides this inventory.
Practical reality: regulators expect visibility. “We didn’t know we had that data” is not an acceptable defense.
Yes, but coverage varies by vendor and platform.
AWS S3
Azure Blob Storage
Google Cloud Storage
SaaS storage (Google Drive, OneDrive, Dropbox, Box)
Key evaluation questions
Most cloud scanning uses agentless API integrations, not infrastructure-level agents.
PII scanning focuses on identifying specific personal data elements such as SSNs, credit cards, and health records. It answers:
“Where is sensitive personal data?”
Data classification is broader. It labels all data based on sensitivity, business context, or regulatory requirements. It answers:
“What type of data is this, and how should it be handled?”
How they overlap
Example
A document may be labeled Confidential – HR (classification) because it contains employee SSNs and salary data (identified via PII scanning).
What to choose
It depends on the architecture:
Real-time inline scanning (SaaS, GenAI)
Batch scanning (cloud storage, databases)
Endpoint scanning
Factors that affect performance
Best practice: start in monitoring or audit mode before enabling blocking or remediation.
Related Resources:
Selecting the right data scanning tool is crucial for effectively safeguarding your business’s sensitive data and ensuring compliance with various regulations. Each tool offers unique features and benefits tailored to different business needs and environments. As such, it's important to thoroughly assess these tools based on your specific requirements to find the best fit for your organization.
We encourage you to delve deeper into these options, explore their detailed functionalities, and consider a demo or trial. This will provide you with a hands-on understanding of how each tool can integrate into and enhance your security infrastructure. Discover more about these powerful tools today and take a proactive step towards strengthening your data security.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

