How Secure is Microsoft OneDrive for Business?
Explore how to secure Microsoft OneDrive for business against cyber threats with encryption, real-time monitoring, and DLP solutions.
OneDrive integrates with Windows, offering AES 256-bit encryption and two-factor authentication.
Common Security Risks
Best practices to enhancing security in OneDrive
In August 2023, it was discovered that Microsoft OneDrive, which holds over half of all sensitive Microsoft Office documents, could be exploited by hackers through a ransomware attack. This exposed a significant security flaw between Windows and security systems, highlighting concerns about the safety of storing sensitive information on cloud services.
As we explore the security features of Microsoft OneDrive, a question arises: Can we trust that our data is truly secure in the cloud, or are we potentially putting ourselves at risk without even realizing it?
Besides serving as a cloud storage, Microsoft's OneDrive enables users to easily manage their documents, contacts, notes, passwords, and photos across all Windows devices.
Due to this broad integration, Microsoft prioritizes securing your data with AES 256-bit standard for all uploads, downloads, and backups, providing a high level of encryption. Additionally, they offer two-factor authentication to further protect against unauthorized access. To ensure the safety of your information during transmission, OneDrive also implements the SSL/TLS encryption standard.
But the question is, is this enough?

OneDrive is a cloud-based storage service offered by Microsoft as part of the Microsoft 365 Bundle. It allows users to store files online, providing seamless access and synchronization across various devices. Key features of OneDrive include:
Encryption is a core pillar of OneDrive security. Microsoft uses two layers of encryption:
Each file is split into fragments, individually encrypted, and distributed across multiple storage containers. This zero-trust encryption model ensures that even Microsoft employees can’t access customer files without authorization.
In Microsoft OneDrive security, data access is managed through a role-based access control (RBAC) system. This ensures users only have access to the files they need, aligning with the principle of least privilege.
Admins can:
Strac extends these controls with automated DLP and DSPM visibility, allowing organizations to identify who has access, what files are shared externally, and where sensitive data (PII, PHI, PCI) lives within OneDrive.
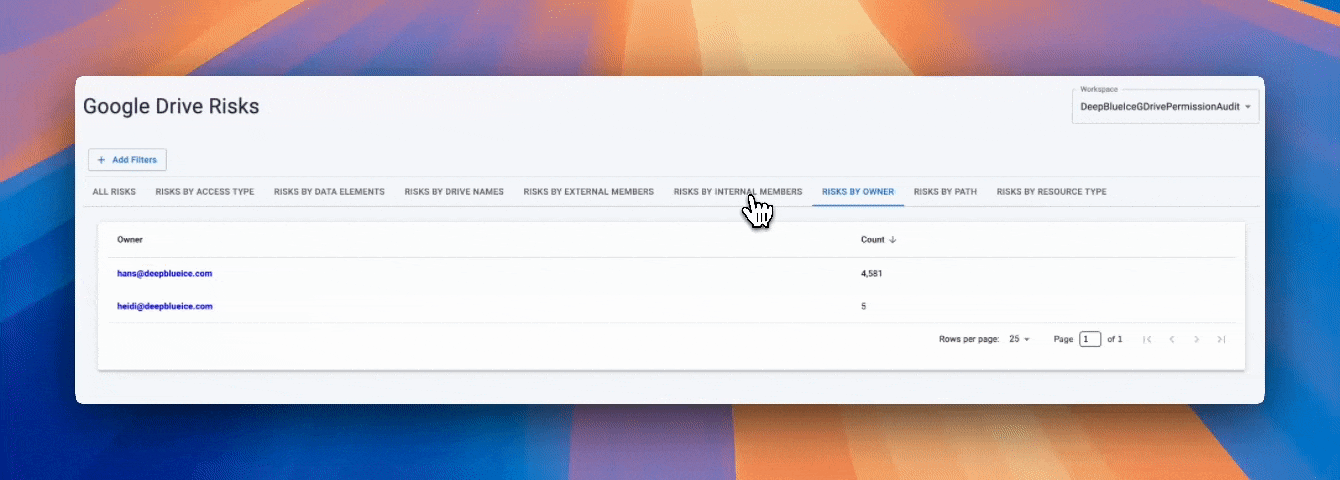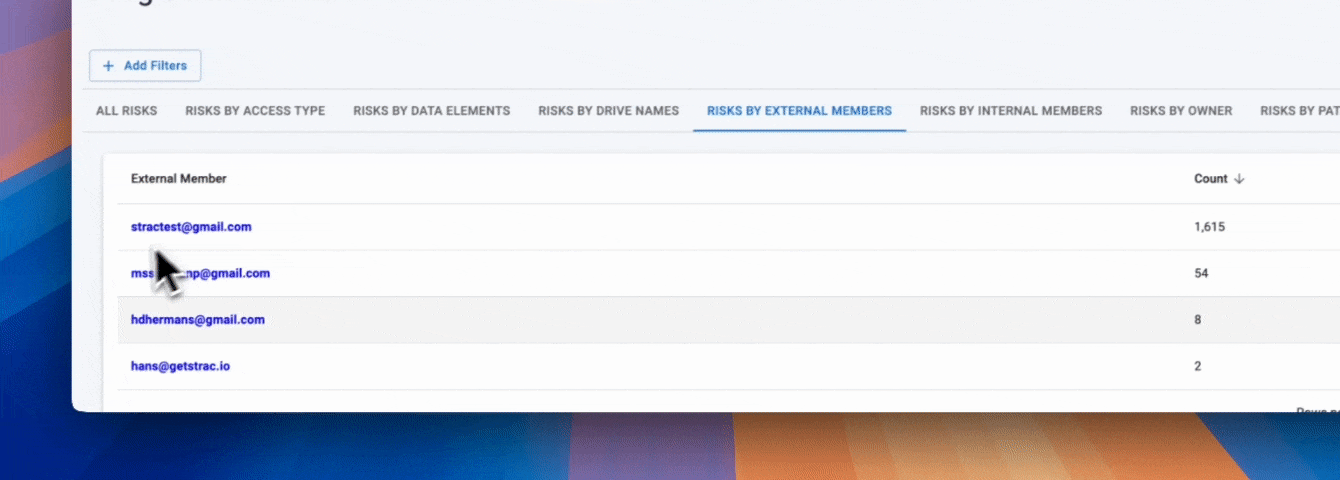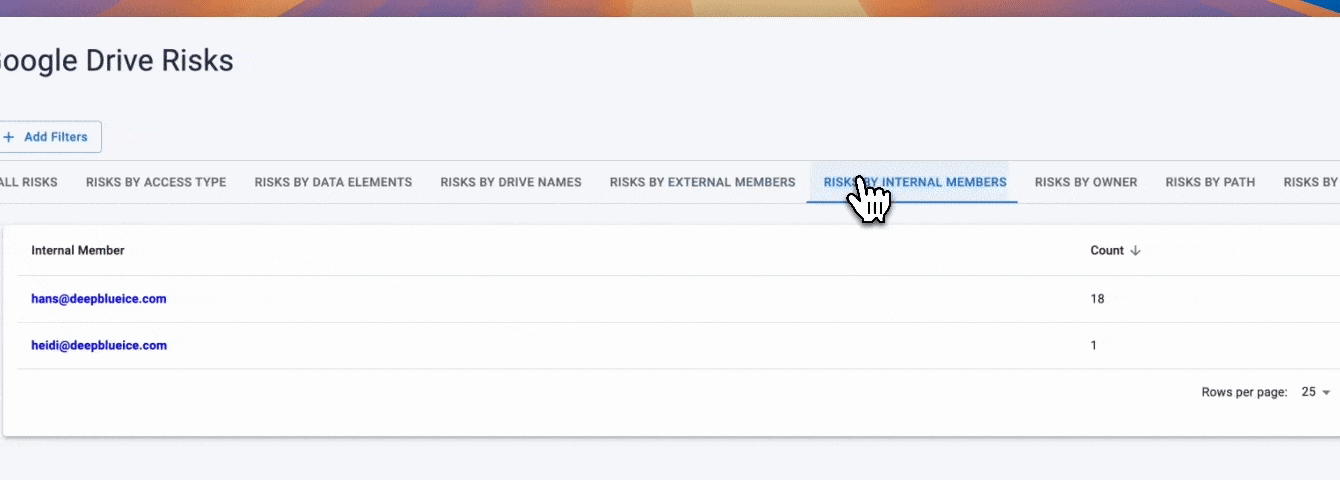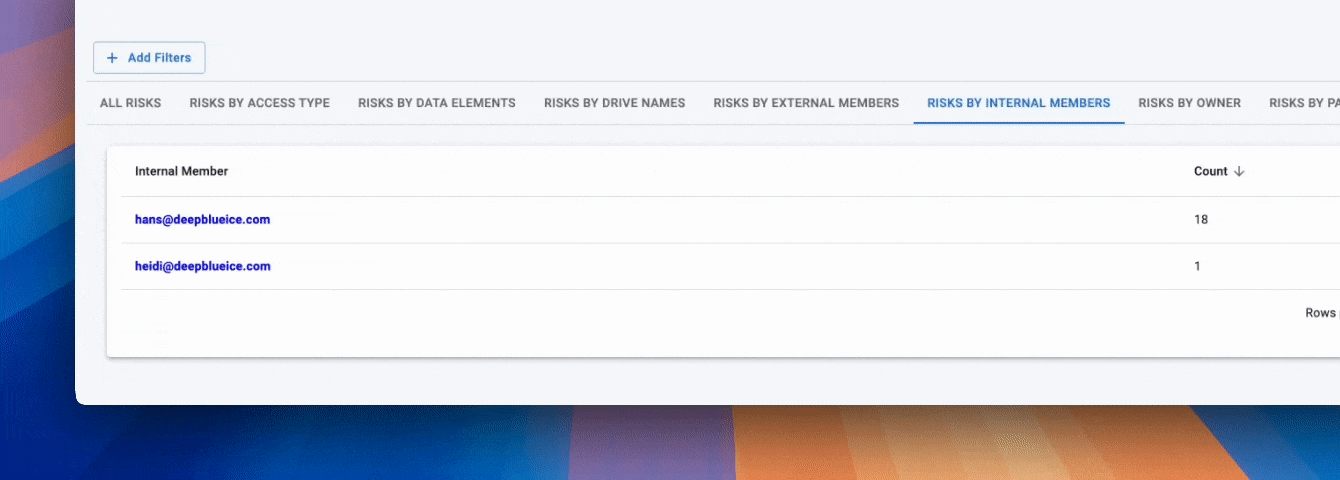
OneDrive incorporates several security measures designed to protect against cyberattacks:
Despite these measures, users should remain vigilant about potential threats such as phishing attacks or insider threats. Implementing best practices for data security—such as strong password policies and regular training on cybersecurity awareness—can further enhance the overall security posture when using OneDrive.

OneDrive for Business includes native Data Loss Prevention (DLP) policies, but they are relatively basic compared to more advanced, third-party solutions. The built-in DLP can identify and block common sensitive data types like credit card numbers and social security numbers, but it lacks the granularity required by organizations with complex, industry-specific data types or custom compliance needs.
For more comprehensive data protection, consider using third-party DLP solutions, such as Strac, which provide granular policy creation, real-time detection, and remediation of sensitive data beyond OneDrive’s default capabilities.

One of the major concerns for organizations is the risk posed by insider threats. While OneDrive for Business includes features like audit logs and access controls, it lacks advanced monitoring and detection capabilities for identifying malicious or negligent internal behavior. Employees or internal users with legitimate access to OneDrive can misuse or inadvertently share sensitive data without triggering sufficient alerts or protections.
To better protect against insider threats, organizations should consider using specialized security tools that integrate with OneDrive, such as insider threat detection platforms or behavioral analytics solutions. These tools monitor user activity for unusual patterns and can trigger alerts or block suspicious behavior in real-time.
While OneDrive encrypts data both at rest and in transit, file metadata (such as document titles, authors, and modification dates) may still be exposed, even if the content of the files is encrypted. This metadata could reveal sensitive information or inadvertently expose details that could be leveraged in a targeted attack.
Organizations should ensure they enforce strict naming conventions and limit sensitive information stored in metadata. Additionally, leveraging third-party tools like Strac can help classify and protect metadata more effectively, limiting exposure risks.
One of the strengths of OneDrive for Business is its ease of external sharing, but this feature can also introduce security risks if not managed properly. While OneDrive offers some basic controls over external sharing, such as restricting who can access shared links or setting expiration dates, these controls may not be sufficient for organizations with high compliance or confidentiality requirements.
To address these risks, organizations should implement strict external sharing policies and leverage third-party DLP tools that automatically detect and block sensitive files from being shared externally. Solutions like Strac can automatically restrict or revoke sharing permissions for files containing sensitive data.

OneDrive for Business is compliant with many industry standards (such as GDPR, HIPAA, and SOC 2), but its native compliance features may not be sufficient for organizations with complex or highly regulated environments. The built-in audit logs and eDiscovery tools, while helpful, may lack the depth needed for comprehensive compliance management or long-term data retention.
Organizations can address these compliance gaps by integrating OneDrive with external compliance management tools or solutions like Microsoft 365 Advanced Compliance or Strac, which provide deeper auditing, extended log retention, and more robust compliance reporting tailored to specific regulations.
Organizations can implement the best practices below to minimize cyber threats and breaches:
Implementing Data Loss Prevention (DLP) in OneDrive is essential for protecting sensitive information within your organization. By setting up DLP policies, you can monitor and control the sharing of sensitive data, ensuring compliance with various regulatory requirements.

One of the most effective ways to protect accounts and prevent unauthorized access is by enabling Multi-Factor Authentication (MFA). MFA requires users to provide two or more forms of identification before accessing OneDrive, significantly reducing the risk of compromised credentials.
While external sharing is a powerful collaboration feature, it poses security risks if not tightly controlled. Enterprises should limit external sharing based on business needs and apply time-based controls to prevent indefinite access to shared data.
Audit logs provide a record of user activities in OneDrive, such as file access, sharing, and modification. Monitoring these logs can help detect suspicious activity, insider threats, and potential data breaches.
Rights management and encryption are essential for protecting sensitive data in OneDrive, ensuring that only authorized users can access and edit content.
As employees increasingly access OneDrive on mobile devices, enterprises must implement controls to manage and secure mobile access. Mobile Device Management (MDM) solutions like Microsoft Intune ensure that only compliant devices can access OneDrive.
Strac OneDrive DLP Solution offers real-time monitoring, automated data classification, redaction capabilities, intelligent alerting system, and compliance management. Strac simplifies compliance management, provides audit trails and reporting features, and offers a user-friendly and customizable interface. One of our clients on G2 stated,
Strac One Drive DLP solution protects businesses with the following core features:
Strac OneDrive DLP solution keeps track of user activity, identifying and alerting any unauthorized or suspicious access to sensitive information in real time. With real-time monitoring and data classification features, Strac DLP protects confidential information on OneDrive.


The Strac OneDrive DLP feature automatically categorizes data according to its level of sensitivity and compliance, effectively managing and tagging information to protect sensitive data.

With Strac's advanced automated redaction capabilities, you can ensure the security and privacy of your data is well-maintained. This feature lets you easily remove or mask any sensitive information in documents before sharing or downloading them.

Strac OneDrive DLP provides efficient and reliable alerts for potential data leaks or breaches. It utilizes advanced machine learning algorithms to ensure high accuracy and reduce false positives, avoiding alert fatigue.

Strac OneDrive DLP is a powerful compliance management tool specifically designed to ensure regulatory compliance on the OneDrive platform. Its ability to identify regulated data and enforce regulatory policies simplifies the process of staying compliant. Additionally, it offers useful features such as audit trails and detailed reporting to help demonstrate compliance during audits.
Strac is a highly customizable tool designed to cater to your specific needs on OneDrive. It offers a user-friendly interface with detailed reporting and analysis of all sensitive data stored on OneDrive, including information on shared files and their distribution over time. With Strac, you can easily manage and monitor your OneDrive data in a way that suits you best.

While Microsoft OneDrive for Business provides solid baseline protection with encryption, compliance certifications, and access controls, true enterprise-grade security requires more than native settings. To fully safeguard sensitive data stored and shared through Microsoft OneDrive for Business, organizations should combine built-in tools with advanced DLP and DSPM capabilities that provide real-time visibility, redaction, and automated remediation. With Strac, you can elevate Microsoft OneDrive for Business security to detect, protect, and prevent data loss across all connected SaaS and cloud environments; seamlessly and agentlessly.
Yes — Microsoft OneDrive security is strong thanks to encryption, access controls, and compliance with global standards like GDPR and ISO/IEC 27018. However, while Microsoft protects infrastructure and accounts, the real security risk lies in user behavior — oversharing, weak access policies, or storing unclassified data. That’s why many enterprises layer in Strac’s DLP and DSPM to classify, redact, and monitor sensitive data across OneDrive in real time.
To strengthen OneDrive security, enable multi-factor authentication (MFA), limit external sharing, enforce data loss prevention (DLP) policies, and monitor activity logs through Microsoft Purview. For deeper visibility, integrate Strac — it automates data classification, detects sensitive PII/PHI/PCI, and remediates exposure instantly across SaaS and cloud apps, giving you unified Microsoft OneDrive security at scale.
You might disable OneDrive in environments with strict data residency or offline-only workflows, or when corporate policies require tighter local data control. But in most cases, disabling it reduces productivity more than it improves security. Instead of turning it off, harden OneDrive security with access policies, encryption, and continuous monitoring via a DSPM + DLP platform like Strac — so collaboration stays seamless and compliant.
Absolutely — OneDrive is essential for secure collaboration in the Microsoft 365 ecosystem. It simplifies file sharing, version control, and device synchronization while maintaining enterprise-grade encryption. What businesses truly need is not to remove OneDrive but to extend Microsoft OneDrive security with proactive data protection tools that automatically detect, redact, and report sensitive data exposure — ensuring both convenience and compliance.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

