TL;DR
- SQL Data Discovery and Classification ≠ optional – it is table‑stakes for GDPR, HIPAA, PCI DSS and every modern data‑governance framework.
- Native Microsoft tooling (SSMS & Azure Portal) is a strong starting point—automatic column scans, built‑in labels, exportable reports.
- Gaps remain: pattern‑based only, no remediation, blind to cross‑database exfiltration, minimal API automation.
- Third‑party platforms add richer taxonomies, AI‑driven patterning, and workflow automation, but often stop at discovery.
- Strac unifies SQL Data Discovery and Classification with active DLP, giving real‑time remediation (mask, encrypt, redact, revoke) plus agentless, self‑hosted scanners for AWS RDS, Azure SQL, on‑prem SQL Server and more.
✨ SQL Data Discovery and Classification (DSPM) – A Visual Overview
Think of SQL Data Discovery and Classification as the “x‑ray” that shows exactly where sensitive data lives (columns, tables, result sets) and how critical it is (labels, ranks). Without that visibility, any downstream DLP or access‑control is guesswork.
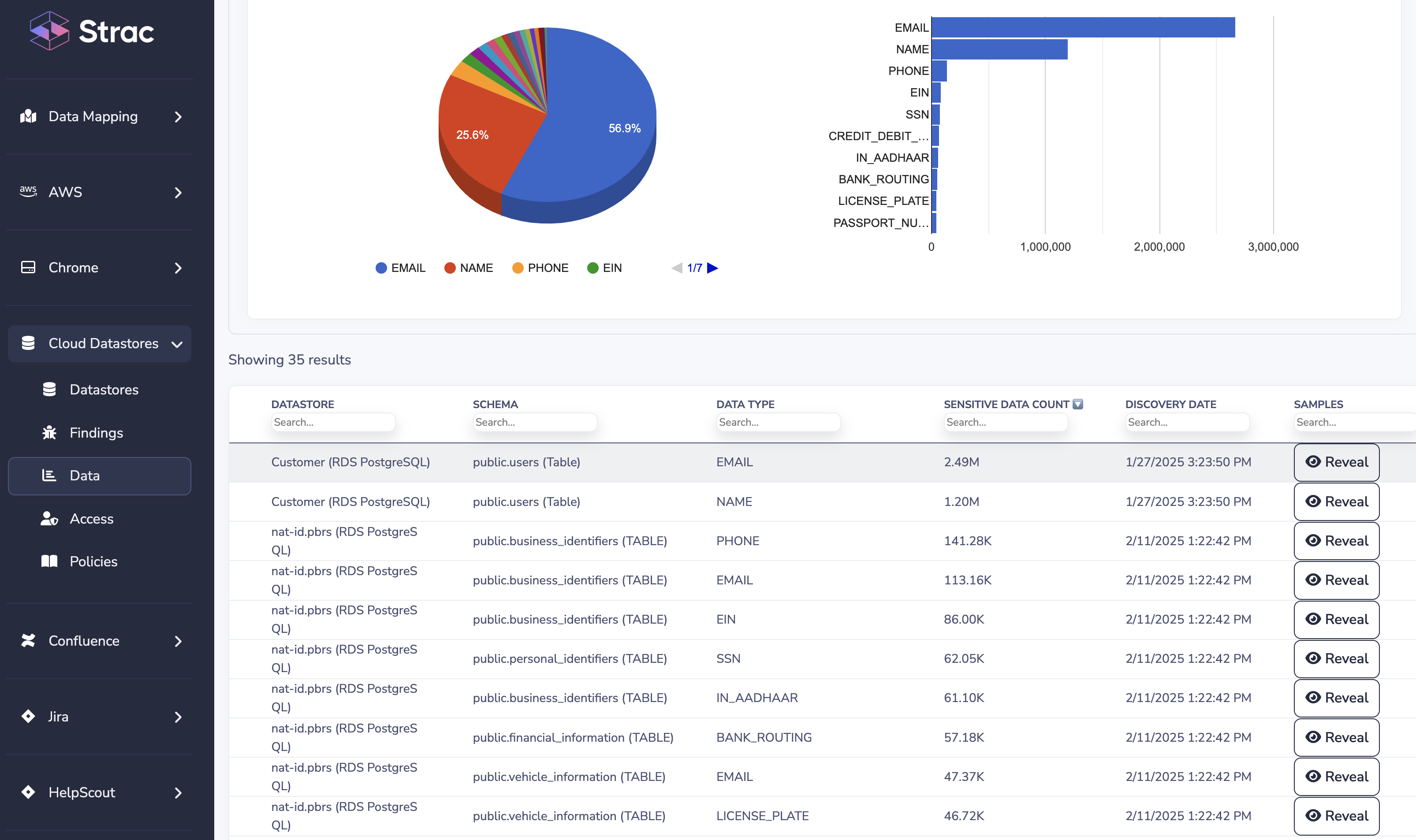
Why SQL Data Discovery and Classification Matters for Modern Security
SQL Data Discovery touches every pillar of a security program:
- Compliance evidence – auditors want proof that you know which columns hold PHI/PCI and that those columns are protected.
- Risk scoring – mapping crown‑jewel data to exposure paths drives smarter investment.
- Incident response – faster blast‑radius analysis when a credential is stolen.
- Least‑privilege enforcement – sensitivity labels tie into Dynamic Data Masking or Purview policies to block unauthorized selects.Microsoft Learn
Gaps in Native SQL Data Discovery and Classification Features
- Name‑pattern bias – Columns called
card_numberare caught;cnor JSON blobs are missed. - No OCR or LLM context – Free text and images inside varbinary/BLOB columns stay invisible.
- Limited automation – T‑SQL / PowerShell APIs exist but lack webhook‑ready events; CI/CD pipelines still need glue code.
- No response actions – Discoveries do not automatically mask, tokenize, or block downstream access.
Result: security teams still export CSVs, open tickets, and hope developers fix things.
Evaluating Third‑Party SQL Data Discovery and Classification Tools
Platforms such as Netwrix DSPM, Secoda and others add:
- AI/ML pattern engines to lower false positives.
- Data catalogs & lineage for governance teams.
- Cross‑source dashboards (SQL, NoSQL, SaaS).
Yet most vendors stop at discovery—they surface problems but hand remediation back to you
✨ How Strac Reinvents SQL Data Discovery and Classification
Strac ties together discovery and real‑time DLP, eliminating the hand‑off gap.
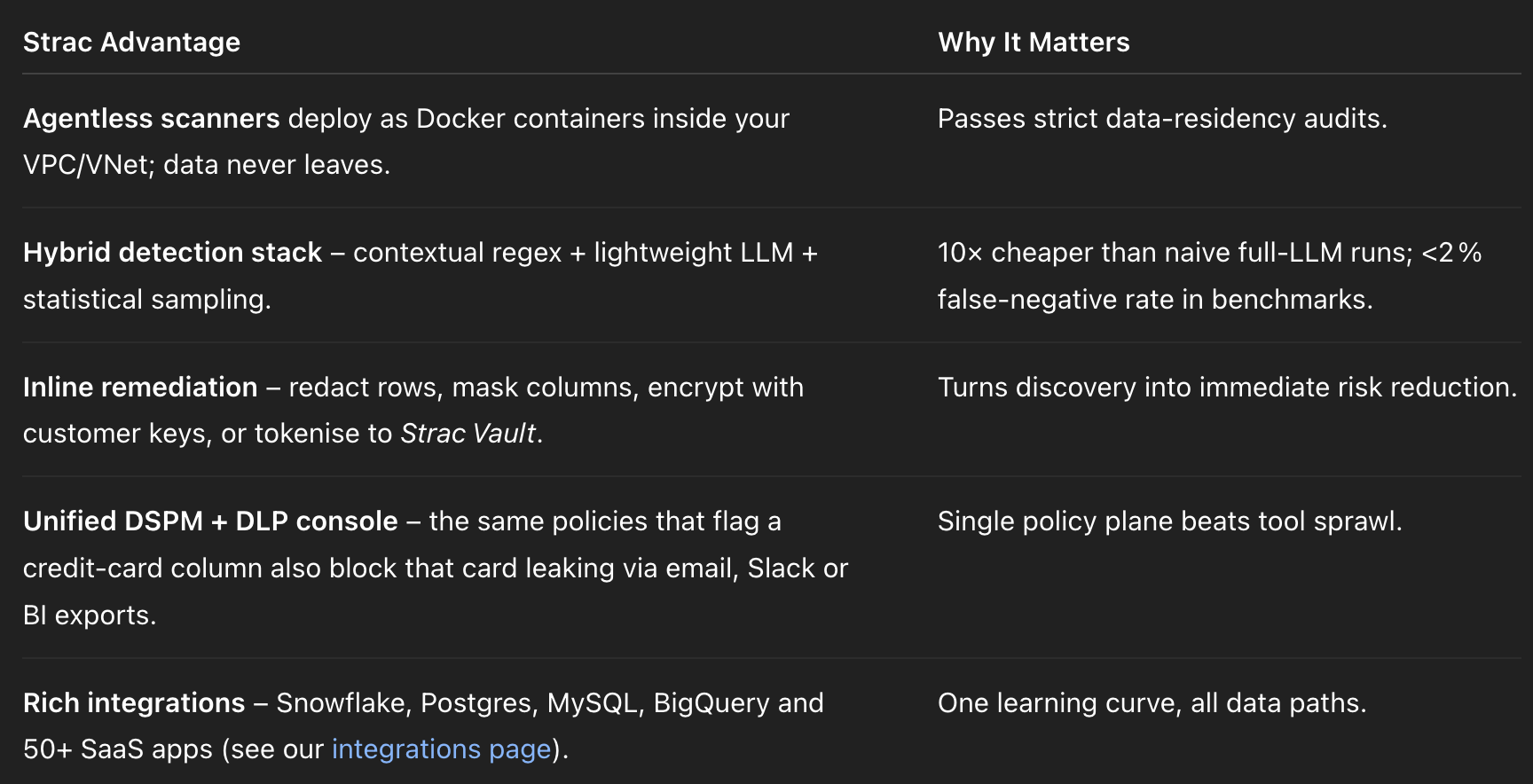
Implementation Roadmap for Effective SQL Data Discovery and Classification
- Inventory every SQL data store (prod, staging, BI replicas).
- Baseline with native sql data discovery and classification scan—export the report.
- Prioritise high‑risk labels (e.g.,
Highly Confidential+Financial). - Deploy Strac scanner in a read‑only role; schedule nightly incremental scans.
- Enable auto‑remediation rules (mask, redact) for Tier‑1 labels.
- Connect Strac DLP to email, SharePoint, BI and browser to enforce the same policies in transit.
- Review metrics weekly: newly discovered columns, remediated incidents, policy drift.
FAQs – SQL Data Discovery and Classification
SQL Data Discovery and Classification: Is sampling 10 K rows per column really enough?
Industry baseline is 100 representative values per column; beyond that, accuracy plateaus while costs rise sharply. Strac samples adaptively—scaling up on free‑text columns, down on deterministic fields—to balance accuracy and cost.
SQL Data Discovery and Classification: Can’t I just use regex everywhere and skip ML?
Regex excels for SSNs or credit‑cards but fails on context‑driven data like “Diagnosis: Asthma.” Strac blends deterministic regex with lightweight LLM context scoring so you don’t choose between accuracy and budget.
SQL Data Discovery and Classification: Will running Strac scanners impact query latency?
No. Scans run against read replicas or snapshot copies; production workloads stay isolated.
SQL Data Discovery and Classification: How does Strac compare to Microsoft Purview?
Purview labels and audits but relies on manual enforcement. Strac acts—masking, blocking, or tokenising data automatically across SQL, SaaS and endpoints, while still ingesting Purview labels for continuity.
(More questions? Ping us or explore the full connector list on our integrations page.)











.webp)














.webp)










.avif)


