PII vs PHI vs PCI: Comprehensive Comparison
Explore the differences between PCI, PHI, and PII data, their regulations, and how to protect sensitive information in our comprehensive guide.
Navigating the complexities of data protection in today’s digital landscape requires a deep understanding of the types of sensitive information organizations commonly handle. Among the most frequently discussed are three critical categories: Personally Identifiable Information (PII), Protected Health Information (PHI), and Payment Card Information (PCI).
Each represents a distinct set of data with its own set of risks, regulatory requirements, and protection strategies. The distinctions between PII, PHI, and PCI are crucial for any organization striving for compliance and aiming to safeguard the privacy and security of the data under its stewardship.
This article comprehensively compares these categories, shedding light on their definitions, the legal frameworks governing them, and the best practices for protecting them. You can gain insights into managing each type of sensitive information effectively, thereby mitigating risks and ensuring regulatory compliance.
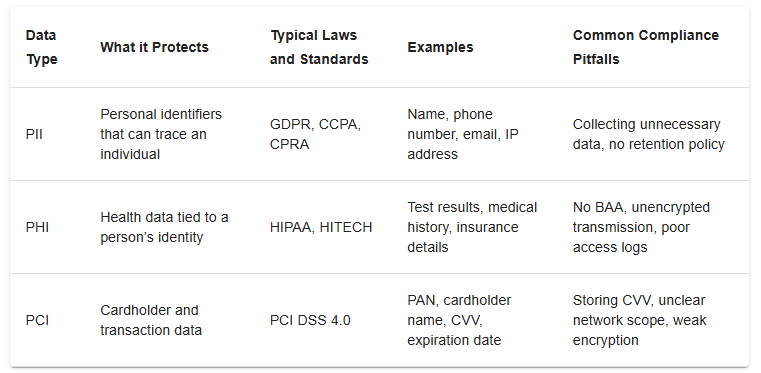
PII, or Personally Identifiable Information, is the cornerstone of individual privacy and data security practices within organizations worldwide. It encompasses a broad range of data that, when disclosed, could be used to identify, contact, or locate a single individual, directly or when combined with other accessible information. Given its widespread use across various operational and communication platforms, this category is central to discussions on data protection.
.webp)
The necessity to protect PII arises not only from a legal standpoint but also as a matter of ethical responsibility and business integrity. The unauthorized disclosure of PII can lead to identity theft, financial fraud, and a loss of consumer trust, significantly impacting an organization's reputation and bottom line.
PHI, or Protected Health Information, represents a category of sensitive data that demands rigorous safeguards to protect individuals' privacy and the confidentiality of their health-related information. This type of information encompasses a wide array of data points collected, processed, or stored by healthcare providers, health plans, and other entities involved in the healthcare ecosystem. The safeguarding of PHI is not just a regulatory mandate but a crucial aspect of maintaining trust between patients and healthcare providers.

The protection of PHI extends beyond compliance to embody the ethical responsibility healthcare entities have toward individuals' privacy rights. Unauthorized access, disclosure, or breaches of PHI can have profound consequences, including identity theft, discrimination, and personal harm, highlighting the necessity for stringent security measures.
PCI is a critical category of sensitive data in financial transactions and e-commerce, focusing on protecting information related to credit and debit card transactions. In an era of ubiquitous digital payments, securing PCI is paramount for safeguarding financial transactions against fraud and ensuring consumer trust in payment systems.
The significance of PCI DSS compliance extends beyond regulatory adherence; it embodies a commitment to maintaining a secure and trustworthy environment for financial transactions. Non-compliance not only risks penalties and fines but can also lead to damaging data breaches, loss of consumer confidence, and long-term reputational harm.
Achieving full pci pii compliance starts by understanding what these three data categories mean and how they intersect across your systems. Most organizations handle all three daily without realizing it — customer data in CRM platforms (PII), patient information in health apps (PHI), and payment card data in billing systems (PCI). Each category is governed by different regulations and controls, and auditors expect clear separation between them. By knowing these distinctions, teams can apply the right safeguards, evidence models, and continuous monitoring policies to maintain ongoing pci pii compliance across SaaS, cloud, and endpoint environments.
The audit process is where pci pii compliance becomes real — because it proves your policies work in practice. Each audit framework focuses on different risk areas: PII audits check privacy transparency, PHI audits assess data safeguards under HIPAA, and PCI audits verify strict cardholder data controls under PCI DSS 4.0. To pass confidently, organizations must show consistent evidence that sensitive data is discovered, encrypted, accessed by the right users, and remediated in real time.
A well-prepared audit process for PII, PHI, and PCI builds trust with regulators, customers, and partners while positioning the company as security-mature and audit-ready for pci pii compliance year-round.

Navigating the protection of sensitive information within the digital domain necessitates a nuanced understanding of the diverse types of data that organizations handle. From Personally Identifiable Information (PII) to Protected Health Information (PHI) and Payment Card Information (PCI), each category embodies unique security challenges and regulatory demands.
I've seen the evolution of data protection strategies in response to these challenges. Here, I delve into the specific requirements and methods for safeguarding PII, PHI, and PCI, drawing from my experience and industry best practices.
Protecting PII is foundational to safeguarding personal privacy and maintaining trust in the digital ecosystem. Key strategies include:
Compliance with PII involves a deep commitment to principles of transparency, allowing individuals to understand how their data is used; accountability, ensuring organizations take responsibility for managing PII; and upholding individuals' rights over their data, including the rights to access, correct, and delete their information as dictated by laws like the GDPR and CCPA.
The sensitive nature of health-related information demands stringent protection measures:

Moreover, PHI encryption during electronic transmission is non-negotiable, safeguarding data integrity and confidentiality. When PHI is not necessary for specific healthcare operations, it should be de-identified, removing all direct and indirect identifiers to protect patient privacy.
Securing PCI is paramount to preventing financial fraud and maintaining the integrity of the payment processing ecosystem:

Access to cardholder data must be strictly need-to-know, supported by strong authentication methods to verify the identity of users accessing this information.
Implementing these protection strategies for PII, PHI, and PCI requires a multifaceted approach, integrating technological solutions, organizational policies, and a culture of security awareness. As threats evolve, so too must our strategies for safeguarding sensitive information, underscoring the importance of continuous assessment and adaptation in cybersecurity practices.
The repercussions of failing to protect these data types extend far beyond potential regulatory fines; they include severe reputational damage, loss of consumer trust, and direct financial losses from fraud and remediation efforts. Given the stakes, organizations must prioritize the deployment of comprehensive data protection strategies.
Amidst the diverse array of data protection tools and methodologies, Strac emerges as an exemplary Data Loss Prevention (DLP) partner, uniquely equipped to meet the challenges of securing PII, PHI, and PCI. Strac stands out due to its holistic approach to data security, offering features that not only prevent data breaches but also ensure compliance with the myriad of regulations governing sensitive data.
Protecting sensitive data effectively means operationalizing pci pii compliance through automated discovery, inline prevention, and continuous policy enforcement. Instead of reacting to audits, leading organizations use real-time data visibility and contextual risk scoring to stay compliant every day. This proactive approach integrates DLP, DSPM, and access governance into a single workflow that adapts to evolving SaaS and GenAI environments. Strac makes it easy to enforce compliance standards for PII, PHI, and PCI without manual overhead — turning protection into a measurable, reportable process that aligns with every stage of pci pii compliance.
1. Discover and Classify Data
2. Enforce Policy-Based Access Control
3. Apply Inline DLP Actions
4. Encrypt and Tokenize Data
5. Monitor and Report Continuously
When organizations ignore proper safeguards, pci pii compliance failures can lead to financial, legal, and reputational collapse. Every leaked record invites not only regulatory fines but also a permanent loss of trust from customers and partners. A single misconfigured SaaS connection or unsecured endpoint can expose millions of personal and financial records in seconds. The experts at Linford & Company point out that most breaches occur not from lack of policy, but from inconsistent enforcement and incomplete visibility into where sensitive data lives. Beyond penalties, companies face operational downtime, forensic costs, lawsuits, and contractual breaches. Understanding these risks helps build a stronger business case for proactive compliance, where continuous discovery and automated enforcement make pci pii compliance both achievable and sustainable.
1. Financial and Legal Consequences
2. Reputational and Trust Damage
Once PHI or PCI data is leaked, it often resurfaces on the dark web, resulting in identity theft, account fraud, and long-term customer churn.
3. Operational Impact
Breach investigations consume engineering and compliance resources, slowing innovation and productivity.
4. Contractual Breach and Business Loss
Violating BAAs, DPAs, or PCI service provider agreements can void partnerships and lead to termination clauses being enforced.



.png)
The consequences of data breaches can be devastating, both for the individuals whose data is compromised and for the organizations responsible for protecting it. This underscores the importance of choosing a DLP partner like Strac, whose comprehensive suite of features provides robust protection for all sensitive data types.
By leveraging Strac's advanced capabilities, organizations can ensure that their sensitive information is secure and managed in compliance with the highest standards of data protection regulations.
In today's digital landscape, where data breaches can tarnish reputations overnight and lead to significant financial and legal repercussions, securing sensitive information such as PII, PHI, and PCI is not just a necessity—it's an imperative. Safeguarding this data against ever-evolving threats and ensuring compliance with stringent regulatory standards can seem daunting. However, with the right tools and strategies, it's a challenge that organizations can confidently meet.
Strac stands at the forefront of Data Loss Prevention (DLP) solutions, offering a comprehensive suite of features designed to protect sensitive data across the board. Its automated discovery and classification, real-time monitoring, advanced encryption, and intuitive policy enforcement work in concert to provide a robust defense mechanism against data breaches. Moreover, Strac simplifies the complex landscape of compliance management, making it easier for organizations to navigate the requirements of GDPR, HIPAA, PCI DSS, and other regulations.
Contact Strac today and embark on your journey to a more secure digital future.
PCI and PII compliance refers to two complementary frameworks that protect sensitive customer data from misuse, theft, or unauthorized exposure.
While PCI aims to secure financial transactions, PII compliance governs privacy and consent. Together, they form the foundation of holistic pci pii compliance, which every SaaS, cloud, and GenAI-enabled business must maintain to prove due diligence and trustworthiness.
Encryption is the cornerstone of pci pii compliance and HIPAA security because it transforms readable information into ciphered data that is useless to attackers.
Strac automates these safeguards by scanning SaaS, cloud, and endpoint systems for unencrypted sensitive data and triggering inline encryption or masking policies instantly. This ensures your environment continuously meets encryption requirements for PII, PHI, and PCI without manual effort — a key advantage in sustainable pci pii compliance.
Detecting a breach early is critical to limiting damage and maintaining pci pii compliance. Traditional methods often rely on logs and manual analysis, but modern programs combine DSPM (Data Security Posture Management) and DLP (Data Loss Prevention) for real-time visibility.
With Strac, breach detection becomes continuous. The platform unifies contextual scanning with AI-driven policies to instantly flag leaks and quarantine sensitive content, providing full audit trails and compliance evidence for every incident — all vital for proven pci pii compliance.
The majority of pci pii compliance failures stem from simple oversights rather than sophisticated hacks. Understanding these weak points helps prevent repeat incidents.
Strac eliminates these gaps through continuous discovery, contextual classification, and automated inline remediation that blocks risky actions before data leaves your control. When compliance is embedded into workflows, organizations drastically reduce vulnerabilities and uphold pci pii compliance effortlessly.
Effective pci pii compliance is measurable. The best programs treat compliance like an ongoing KPI, not a one-time audit task. Organisations can evaluate their performance through several quantifiable indicators:
Strac simplifies measurement by centralizing these KPIs inside one dashboard — connecting discovery, policy enforcement, and reporting. CISOs can generate audit-ready metrics instantly to demonstrate effectiveness and sustain long-term pci pii compliance.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

