Best PII Data Discovery Tools of 2025
Explore the leading PII Data Discovery Tools of 2025 in our comprehensive guide. Uncover the features, benefits, and user reviews to protect sensitive information and comply with data privacy laws
Choosing the Best PII Data Discovery Tools is not about features on a page. It is about finding sensitive records quickly, knowing who can see them, and fixing exposure before it becomes a problem. The Best PII Data Discovery Tools show exactly where data sits across Slack, Gmail, Drive, CRM, and laptops, then guide redaction, labeling, and access controls that hold up in audits.
This guide ranks the Best PII Data Discovery Tools for practical results in 2024. You will see what each tool does well, where it fits, and how the Best PII Data Discovery Tools help your team lower risk, hit compliance deadlines, and keep work moving without friction.
PII data discovery is the continuous process of locating, identifying, and classifying personally identifiable information—such as names, addresses, national IDs, card numbers, health records, and biometrics—across your organization’s systems. pii data discovery tools combine pattern matching, machine learning, and context signals to detect sensitive attributes wherever they live (structured and unstructured sources), tag them with the right classifications, and route that insight to security and compliance workflows.
Regulations like GDPR, CCPA/CPRA, HIPAA, PCI DSS, and sector frameworks (ISO 27001, SOC 2) require knowing where PII lives, who can access it, and how it’s protected. The best pii data discovery tools provide the evidence you need for data maps, RoPAs/records, DPIAs, right-to-access/erasure requests, and audit trails—turning discovery results into actionable compliance reporting.
Most organizations struggle with three realities: (1) PII is scattered across SaaS apps, tickets, chats, attachments, screenshots, and cloud buckets; (2) manual regex hunting doesn’t scale to images/PDFs or code repositories; (3) policies change faster than legacy tools. Purpose-built data discovery software gives you coverage, accuracy, and speed.
Missing PII leads to failed audits, regulatory fines, reputational damage, and protracted incident response. Robust pii data discovery tools reduce dwell time, shrink the exposed footprint, and generate audit-ready evidence—making it easier to demonstrate continuous compliance.
PII (Personally Identifiable Information) data discovery tools are essential software solutions designed to identify, classify, and manage sensitive personal data within an organization. These tools play an important role in ensuring compliance with data protection regulations & enhancing overall data security.
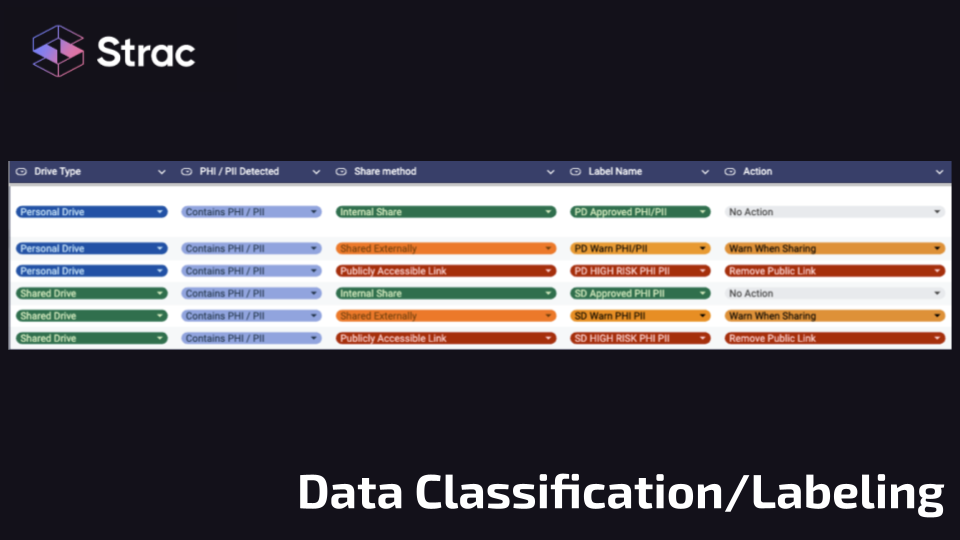
These tools perform automated scans across various data repositories, including databases, file systems, cloud storage, and applications. They utilize algorithms to detect patterns that match common PII formats, such as Social Security numbers, credit card information, and email addresses.
Once PII is located, the software categorizes it based on predefined rules related to its sensitivity and applicable regulations (e.g., GDPR, HIPAA). This classification helps organizations understand the nature of their data and prioritize protection efforts accordingly.
PII discovery tools enable organizations to evaluate the risk associated with sensitive data. By analyzing the content, permissions, and locations of PII, organizations can make informed decisions regarding data security measures.
These tools assist in meeting regulatory requirements by providing visibility into where PII resides within the organization. They help ensure compliance with various laws such as GDPR, CCPA, and HIPAA by automating the processes of locating, cataloging, and protecting PII.
Many PII discovery solutions offer continuous monitoring capabilities to detect new instances of PII as they enter the system. This proactive approach helps maintain up-to-date security measures and compliance status.
As data moves to S3, GCS, Azure Blob, data lakes, and SaaS file stores, cloud-native discovery tools index and classify PII at cloud scale. They connect via APIs, scan structured and unstructured data (including attachments), and surface findings in dashboards and alerts.
Why they matter
Typical strengths
Typical limitations
Best for: Teams prioritizing cloud storage, public link exposure, and compliance mapping across multi-cloud + SaaS file systems.
Many enterprise DLP platforms now bundle discovery to find PII at rest while enforcing policies in motion (email, chat, endpoints, web). Discovery features identify sensitive data sources; DLP policies then block, redact, quarantine, or encrypt when that data moves.
Why they matter
Typical strengths
Typical limitations
Best for: Enterprises that need unified discovery + prevention with mature governance and incident response.
Specialized platforms focus exclusively on PII data discovery and classification, going deep on accuracy, context, and coverage—including OCR for images/PDFs and LLM-assisted detection for unstructured text, tickets, and chats. Many integrate downstream with DLP, SIEM/SOAR, IAM, and ticketing to trigger remediation.
Why they matter
Strac blends specialized PII discovery with enterprise-grade DLP:
Best for: Security teams that want accurate PII discovery with real-time enforcement—not two separate products—across modern SaaS, cloud storage, and GenAI workflows.
Strac has emerged as a frontrunner in PII Data Discovery, catering to the pressing need for sophisticated tools to navigate the complex landscape of data security and compliance. With its innovative approach and advanced technological framework, Strac offers a comprehensive solution for businesses aiming to protect sensitive personal information effectively.
Key Features


Benefits
Unique Selling Point
What sets Strac apart is its no-code platform, designed to democratize data protection by making it accessible to non-technical users. This unique feature allows for rapid deployment and ease of use, ensuring organizations of all sizes and technical capabilities can achieve comprehensive PII protection.
DataGuard is a comprehensive solution tailored to address the multifaceted challenges of protecting Personal Identifiable Information (PII) in the digital era. Offering a robust platform that combines legal expertise with technological innovation, DataGuard provides businesses with the tools needed to navigate the complexities of data privacy laws while securing sensitive information against breaches.
Key Features
Benefits
Unique Selling Point
DataGuard's integration of legal compliance expertise with cutting-edge data protection technology sets it apart from other PII Data Discovery tools. This blend of services ensures that organizations' data handling practices are legally sound and that their sensitive information is robustly protected, providing a one-stop solution for data security and compliance.

Spirion has carved a niche in the privacy management and PII Data Discovery domain, offering robust solutions that prioritize the precise identification, classification, and protection of Personal Identifiable Information (PII) across diverse digital landscapes. Known for its accuracy and depth of discovery, Spirion is a tool of choice for organizations looking to uphold the highest data privacy and security standards.
Key Features
Benefits
Unique Selling Point
Spirion’s unique selling point lies in its unmatched precision and the depth of its data discovery and classification capabilities. By offering a level of accuracy that few other tools can match, Spirion not only enhances data security but also significantly bolsters an organization's compliance posture. This, combined with its consultative approach to integrating privacy into business processes, makes Spirion a leader in the PII Data Discovery space.

OneTrust has quickly ascended as a leader in the privacy management and PII Data Discovery sphere, catering to organizations’ growing need to navigate the complexities of privacy laws, secure sensitive information, and maintain consumer trust. Offering a robust platform that integrates privacy, security, and third-party risk into a cohesive ecosystem, OneTrust empowers businesses to not only comply with global data protection regulations but also to embed privacy by design into their operations.
Key Features
Benefits
Unique Selling Point
What distinguishes OneTrust from the crowded field of PII Data Discovery tools is its holistic approach to privacy management. It integrates comprehensive PII discovery and classification with a suite of tools designed to manage consent, assess privacy impact, and automate compliance tasks. This all-encompassing approach ensures data protection and compliance and fosters a culture of privacy and ethics within organizations.

Varonis offers a comprehensive suite that goes beyond mere identification to provide in-depth analysis, monitoring, and protection of sensitive data across enterprise environments. Renowned for its ability to secure data where it lives—be it in on-premises servers, cloud storage, or SaaS platforms—Varonis is the go-to solution for organizations seeking to fortify their defenses against data breaches and ensure regulatory compliance.
Key Features
Benefits
Unique Selling Point
Varonis sets itself apart with its advanced user behavior analytics and proactive data protection strategies. This unique combination ensures the security of sensitive information and provides organizations with critical insights into how data is used and accessed. This intelligence-driven approach to data protection makes Varonis a pivotal player in the PII Data Discovery and security landscape.
This table summarizes the capabilities, pros, and cons of five leading PII Data Discovery tools, providing a clear comparison to assist organizations in selecting the right solution for their needs.
The fastest way to get value from pii data discovery tools is to run a focused rollout that turns findings into action. Use these BOFU-ready steps to operationalize the best pii data discovery tools and your broader data discovery software stack.
Catalog systems, data owners, and flows across SaaS apps, cloud buckets, databases, endpoints, email, collaboration, and Dev/ticketing tools. Flag locations likely to hold PII—customer records, payment data, health data, and support attachments—so pii data discovery tools know where to start.
Sequence your first scans for cloud object stores, productivity suites, email, chat, and ticketing where PII frequently hides in files, screenshots, and PDFs. This focus lets data discovery software deliver immediate visibility and quick wins your stakeholders will feel.
Localize patterns for national IDs and phone formats, add custom dictionaries, and tune proximity logic (e.g., PAN near “CVV”). The best pii data discovery tools support ML + patterns + OCR—use all three and simulate policies before enforcing them.
Pipe results into DLP, SIEM/SOAR, EDR, ticketing, and IAM so discovery auto-triggers remediation: redact, block, revoke-sharing, quarantine, re-label, or expire links. This turns pii data discovery tools from dashboards into outcomes.
Align findings to GDPR/CCPA/HIPAA/PCI controls, owners, and SLAs. Generate consistent evidence (who, what, where, when, action taken) so your data discovery software becomes audit-ready by design.
Set clear KPIs and review them weekly so your pii data discovery tools stay aligned to business outcomes.
Percentage of prioritized sources successfully scanned (SaaS, cloud, email, endpoints). The best pii data discovery tools expand coverage fast—track growth per week.
True-positive vs. false-positive rate by data type and source. Mature data discovery software should improve accuracy as you tune rules and add dictionaries.
Public links revoked, external shares removed, and risky repositories cleaned. Tie every discovery to a closure action—proof that pii data discovery tools reduce real risk.
Median time from detection to action (redact, block, revoke, quarantine). Lower is better; aim for minutes, not days, as playbooks mature.
Number of GDPR/CCPA/HIPAA/PCI controls evidenced per quarter, plus DSAR fulfillment speed and audit artifacts generated. The best pii data discovery tools should make reporting one-click, not a fire drill.
Hours saved (automation), fines avoided (modeled), and incident count trending down. These metrics help leadership see why investing in pii data discovery tools—and the right data discovery software integrations—pays off.
The fastest path from “we think we found PII” to “we fixed the risk” is unifying discovery with prevention. Strac combines high-fidelity detection (patterns + ML + OCR + secrets/code) with real-time actions—redaction, block, tokenization, revoke-sharing, quarantine—and audit-ready reporting. That means better accuracy, fewer alert storms, and measurable reduction in exposure across SaaS, cloud, browsers, and GenAI.
Ready to take control of your data security? Discover how Strac’s PII data discovery software can automatically identify, classify, and secure sensitive information across your organization—while simplifying GDPR, CCPA, and HIPAA compliance. Book a demo today.
PII (personally identifiable information) is any data that can identify a person directly or in combination with other data. Common examples include full name, email, phone, home/IP address, national IDs (SSN, NIN), passport/driver’s license numbers, payment data (PAN/CVV), birth date, and biometrics. Regulations also recognize context and sensitivity: under GDPR, “personal data” is broader and includes online identifiers; special categories (health, ethnicity, religion) require stronger safeguards. The best pii data discovery tools label PII at the attribute level (e.g., “US SSN,” “EU VAT,” “PHI”) so your data discovery software can apply the right policy—retain, redact, tokenize, or delete—per jurisdiction.
Yes—modern pii data discovery tools are built for unstructured data. They combine pattern matching, ML/NLP, and OCR to detect PII in PDFs, scans, screenshots, slide decks, chat transcripts, ticket comments, and email bodies/attachments. Strong tools also understand file context (sharing state, link exposure, external collaborators) to prioritize real risk, not just matches. If you’re evaluating the best pii data discovery tools, check that they:
It depends on where and how encryption is applied:
The Best PII Data Discovery Tools find sensitive records across Slack, email, drives, CRM, and laptops. The Best PII Data Discovery Tools help security, compliance, and IT see what exists, who can access it, and what to fix first. The Best PII Data Discovery Tools work for startups and enterprises that need quick results.
Start with coverage, accuracy, and action. The Best PII Data Discovery Tools scan SaaS and endpoints, keep false positives low, and trigger real fixes like redaction and access cleanup. Compare how the Best PII Data Discovery Tools integrate with DLP, identity, EDR, and ticketing to turn findings into outcomes.
Yes. The Best PII Data Discovery Tools build a live inventory, speed DSAR responses, and show minimization with clean reports. The Best PII Data Discovery Tools document where data lives, who touched it, and what was done, which helps audits move fast.
You should see a ranked list of exposure points, fewer public links, and tighter access on sensitive folders. The Best PII Data Discovery Tools reduce stale shares, surface owners, and provide a baseline risk score. The Best PII Data Discovery Tools make progress visible with simple dashboards.
The Best PII Data Discovery Tools connect to Slack, Google Workspace, Microsoft 365, Salesforce, and laptops. The Best PII Data Discovery Tools trigger redaction in chat, labels in drives, and revokes for risky links. The Best PII Data Discovery Tools send tasks to ticketing so owners resolve issues quickly.
Ask vendors how they approach keys (KMS/HSM support), what they do when decryption isn’t possible, and whether discovery events can still trigger protective actions. For real outcomes, prefer pii data discovery tools that pair detection with controls like redaction, block, quarantine, and revoke-sharing.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

