A Complete Guide to DLP Implementation and Requirements
Learn the importance of DLP and the data loss prevention requirements to choose the right vendor. Implement DLP effectively and protect your sensitive data.
Data Loss Prevention (DLP) is crucial for organizations aiming to protect their data from unauthorized access, leaks, and breaches. In 2023 alone, reports indicate 3,205 publicly reported data breaches, a 78% increase from 2022. With stakes this high, relying on outdated practices is no longer viable, making robust DLP implementation essential.
This detailed guide explores the importance of DLP and provides an overview of its implementation and evaluation processes. We’ll also outline the key steps for selecting the right solution and provide effective strategies for implementing DLP. Let’s begin.
Data Loss Prevention (DLP) refers to a set of strategies and tools that protect sensitive data from loss, misuse, or unauthorized access. A DLP system monitors, detects, and responds to potential threats to data security, helping organizations maintain control over sensitive data. Here are the key benefits of DLP:
Data Loss Prevention (DLP) tools are essential for organizations aiming to protect their sensitive information from unauthorized access, leaks, and breaches. Here’s why using DLP tools is crucial:
Selecting the right Data Loss Prevention (DLP) solution is critical for protecting your organization’s sensitive data. A structured approach can help simplify the evaluation process and ensure you choose the best solution for your needs. Here are six data loss prevention requirements to guide you through the process:
Begin by identifying a broad range of potential vendors. Hundreds of vendors offer data protection solutions, so narrowing down your choices using specific criteria is important. Look for vendors that support all your operating environments and consult resources for guidance. Peer reviews and industry reports can also provide valuable insights.
Once you have a shortlist of potential vendors, develop a structured plan for contacting them. Outline your critical business needs and use cases. This preparation helps ensure that your interactions with vendors are focused and productive.
Engage with your shortlisted vendors and gather detailed information about their DLP implementations. Involve key stakeholders in your organization to build an agreement on which vendors are the best fit. This collaborative approach helps evaluate how well each vendor can meet your specific needs.
Based on the responses and evaluations, narrow down your choices from top DLP solutions. Use criteria such as Request for Proposal (RFP) scores, feature comparisons, and risk assessments to decide. Engage these top vendors for onsite presentations and further assessments to better understand their capabilities.
Request pilot tests from your top vendors to evaluate their solutions in a real-world environment. Pilot tests show how the solutions perform under your specific conditions and requirements. This step is crucial for identifying potential issues and ensuring the solution integrates smoothly with your existing systems.
After completing the pilot tests, present the results to your selection team. Based on the evaluations, select the vendor that best meets your needs. Begin negotiations to finalize the terms of the purchase. Ensure that you address all aspects, including pricing, support, and future scalability, before making the final commitment.
Selecting the right DLP solution protects your organization’s sensitive data. Here are six essential steps to guide you through effective data loss prevention procedures:
Establish a robust data handling policy that aligns with your business requirements and categorizes data based on its sensitivity and the potential impact of its loss. High-risk data, such as sensitive customer information and intellectual property, should have stringent handling procedures. The policy should include guidelines for data encryption, access controls, and compliance with relevant regulations such as GDPR and HIPAA.
Once the data handling policy is in place, the next step is to discover and classify all data assets within your organization. This involves identifying where data resides and categorizing it according to the defined classifications. Modern DLP tools can automate this process, ensuring accurate identification and classification of structured and unstructured data.
Assess potential vulnerabilities in your data handling processes. This includes evaluating situations and activities that could lead to data breaches, such as sharing sensitive data via unencrypted emails or storing high-risk data in public cloud environments. Understanding these vulnerabilities allows you to focus on critical areas and develop targeted measures to address them.
Implement automated enforcement mechanisms to ensure data handling policies are consistently applied across the organization. This can include automatically encrypting high-risk data, preventing unauthorized access, and monitoring data transfers to ensure policy compliance. These measures help protect data before it can be lost or misused.
Continuous monitoring ensures compliance with data loss prevention requirements. It is crucial for detecting and responding to potential threats in real-time. Every instance of data access, transfer, or exchange should be monitored to ensure adherence to data handling policies. This ongoing vigilance helps identify any unusual or unauthorized activities, enabling prompt action to mitigate risks.
It is essential to educate employees about the importance of data protection and their role in maintaining data security. Regular training sessions should be conducted to keep employees informed about the latest data handling policies and best practices. Real-time guidance during policy violations can help employees understand the correct actions, reinforcing a culture of data security within the organization.
Manually performing these tasks can lead to errors and inefficiencies. That's why a platform like Strac is essential to automate processes for accuracy, productivity, and risk reduction.
Effective Data Loss Prevention starts with understanding how sensitive data moves across your organization and how easily it can leak through modern SaaS, cloud, email, and AI tools. DLP best practices ensure that your security program is not only protective but also realistic for fast-moving teams that rely on collaboration platforms. With strong DLP best practices, companies can reduce risk; strengthen compliance posture; and minimize the friction typically associated with outdated, restrictive DLP programs.
Adopting these DLP best practices helps companies build a proactive security posture that stops leaks before they happen and stays aligned with compliance expectations. The right approach ensures that teams remain productive while sensitive data remains protected.
DLP compliance is essential because organizations are now responsible for managing large volumes of sensitive data across distributed systems, third-party platforms, and AI workflows. Regulatory frameworks like GDPR, HIPAA, GLBA, PCI DSS, and SOC 2 require strict controls over how sensitive information is accessed, shared, and stored. When companies fail to meet DLP compliance requirements they face fines; operational disruption; and long-term reputational damage.
Ultimately, DLP compliance is not just a regulatory requirement; it is a foundational element of modern security programs that reduces risk and preserves customer confidence. With the right DLP controls in place, organizations can innovate faster without compromising security or compliance obligations.
Strac is an advanced Data Loss Prevention (DLP) platform designed to secure sensitive data across SaaS applications, endpoints, and communication channels. Here’s how it meets all the needs of DLP implementation:

Schedule a demo to see how Strac can protect your data with DLP.
Successful DLP implementation and requirements go far beyond policy writing; they define the backbone of a company’s entire data security strategy. The right DLP solution doesn’t just identify where sensitive data lives; it actively protects it in motion and at rest across SaaS, cloud, endpoints, and GenAI environments. Strac simplifies every stage of DLP implementation and requirements by delivering agentless deployment, ML-powered detection, and real-time redaction that aligns with compliance standards like PCI DSS, HIPAA, and GDPR. With Strac, security teams can finally move from reactive alerts to proactive, automated data protection; all in one unified DSPM + DLP platform.
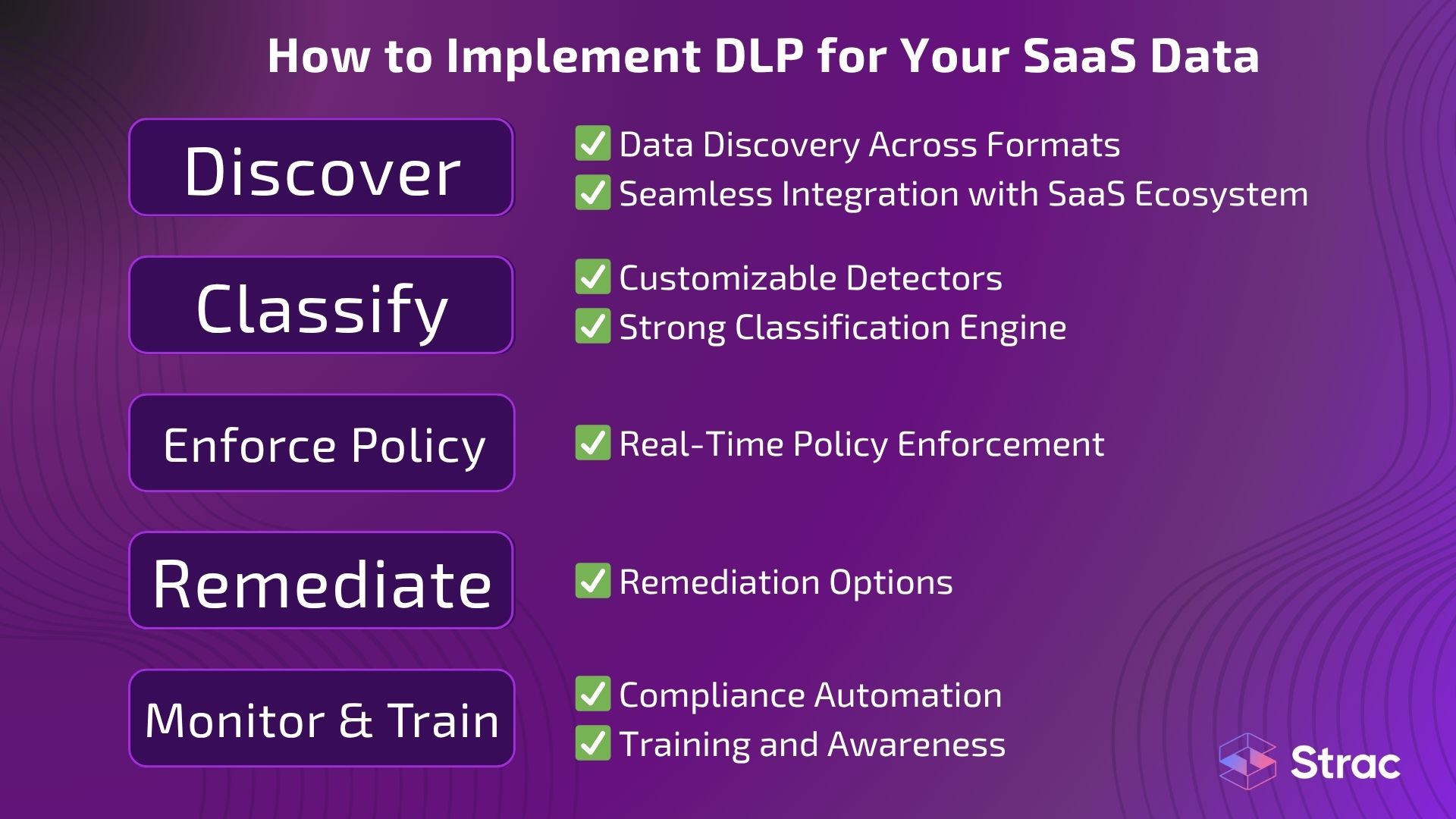
Implementing data loss prevention (DLP) involves clear planning, configuration, and continuous optimization. The process starts with identifying data flows, defining policies, testing detection accuracy, and expanding coverage across SaaS, cloud, and endpoints.
Key phases include:
Strong DLP implementation supports compliance frameworks like HIPAA, PCI DSS, SOC 2, and GDPR by automatically discovering and protecting regulated data. Tools like Strac go beyond detection—embedding compliance templates and redacting PHI or PCI data inline, ensuring audit readiness across SaaS and GenAI workflows.
Many teams face resistance due to tool complexity or false positives during DLP deployment. Legacy vendors require heavy agents and manual tuning. Strac’s agentless, ML-powered DLP eliminates these roadblocks—detecting sensitive data accurately and remediating inline without performance impact or disruption to business workflows.
Agent-based systems slow down devices and complicate updates. Agentless DLP, like Strac’s, integrates directly with SaaS, cloud, and GenAI platforms—delivering:
This architecture provides real-time protection without friction for IT or users.
Strac unifies Data Security Posture Management (DSPM) and DLP in one platform—automating discovery, classification, and remediation across data estates. Using ML and OCR detection, it minimizes false positives while ensuring sensitive data never leaves approved boundaries. Strac’s no-code setup and compliance-ready templates make enterprise-level DLP achievable in days, not quarters.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

