CCPA Data Mapping: How to Achieve CCPA Compliance?
Learn how to achieve CCPA compliance with effective data mapping practices. Discover steps to understand, identify, and map your data sources, create a data map, and conduct a gap analysis.
The California Consumer Privacy Act (CCPA) is a data privacy law that provides California residents with enhanced privacy rights and control over their personal data. The CCPA applies to any company that does business in California and collects personal information from California residents. Compliance with the CCPA requires companies to implement certain data mapping practices. In this blog, we will discuss what companies should do for data mapping in order to be CCPA compliant.
CCPA Data Mapping refers to the systematic process of identifying, documenting, and visualizing the flow of personal information within an organization to comply with the California Consumer Privacy Act (CCPA). The CCPA is a data privacy law that grants California residents enhanced rights and control over their personal data. To comply with this regulation, businesses must have a thorough understanding of the personal information they collect, process, store, and share.
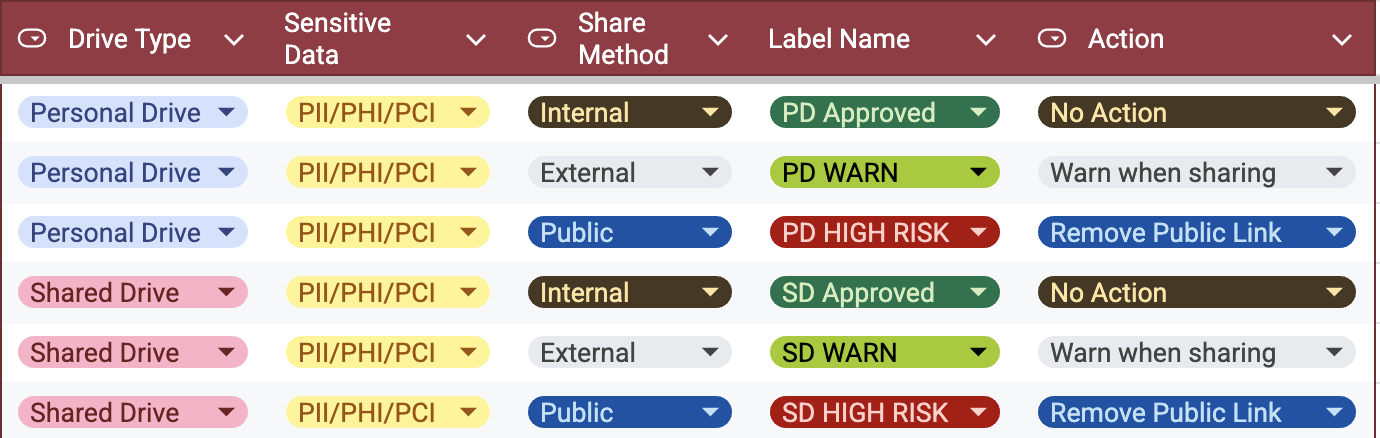
The first step in data mapping is to understand the data that your company collects. This means identifying what personal information is collected, why it is collected, where it is stored, and who has access to it. Personal information includes any information that can be used to identify an individual, such as name, address, email address, Social Security number, and IP address.
Once you understand the data that your company collects, you need to identify the sources of that data. This means identifying all the systems, applications, and third-party services that collect, process, or store personal information. This can include customer relationship management (CRM) systems, marketing automation platforms, data warehouses, and cloud-based services.
The next step is to map your data flows. This means identifying how personal information is collected, processed, and shared within your organization and with third-party service providers. You need to identify who has access to the data, how it is transmitted, and where it is stored.
Once you have identified your data sources and mapped your data flows, you need to create a data map. This is a visual representation of your company's data ecosystem that shows where personal information is collected, processed, and stored, as well as how it flows between different systems and applications.
The final step in data mapping for CCPA compliance is to conduct a gap analysis. This means comparing your data map to the requirements of the CCPA to identify any areas where you need to make changes. For example, you may need to update your privacy policy to provide more detailed information about the personal information you collect, or you may need to implement additional security measures to protect personal information.
Here is a general outline to help you create a data mapping template that aligns with CCPA requirements:
Let's say you are using AWS in your business. In addition to AWS, there will be hundreds of SaaS apps and systems you would be using. From Data Mapping perspective, this is how AWS will be mapped out:

Complying with the CCPA requires companies to implement robust data mapping practices. By understanding your data, identifying your data sources, mapping your data flows, creating a data map, and conducting a gap analysis, you can ensure that your company is CCPA compliant and that you are protecting the privacy rights of your customers. Remember that compliance with data privacy laws is an ongoing process, and you should regularly review and update your data mapping practices to ensure that you are meeting all legal requirements.
Strac offers a robust SaaS/Cloud DLP and Endpoint DLP solution with modern features designed to enhance data security and compliance:
Strac supports detection of all sensitive data elements for PCI, HIPAA, GDPR, and other confidential data. It also allows customers to configure their own data elements. Strac is unique in its ability to detect and redact images (jpeg, png, screenshots) and perform deep content inspection on document formats such as PDFs, Word documents (doc, docx), spreadsheets (xlsx), and zip files. Explore Strac’s comprehensive catalog of sensitive data elements.
Strac DLP ensures compliance with a range of standards, including PCI, SOC 2, HIPAA, ISO-27001, CCPA, GDPR, and NIST frameworks.
Strac integrates with customer systems in under 10 minutes, providing immediate DLP/ live scanning/ live redaction capabilities on their SaaS applications.
Strac utilizes custom machine learning models trained on sensitive PII, PHI, PCI, and confidential data, delivering high accuracy with minimal DLP false positives and negatives.
Strac boasts the broadest and deepest range of SaaS and Cloud integrations. Discover all integrations at Strac Integrations.
Strac integrates with LLM APIs and AI platforms like ChatGPT, Google Bard, Microsoft Copilot, and more to protect sensitive data within AI or LLM applications. Learn more in the Strac Developer Documentation.

Strac is the only DLP solution that accurately and comprehensively works across SaaS, Cloud, and Endpoint environments. Learn more about Endpoint DLP at Endpoint DLP.
Strac provides APIs for developers to detect or redact sensitive data. Check out the Strac API Docs.
Strac can redact (mask or blur) sensitive text within any attachment.
Strac offers out-of-the-box compliance templates for detecting and redacting sensitive data elements, along with flexible configurations to meet specific business needs, ensuring that data protection measures align with individual requirements.
Book a demo to learn about Data Mapping and how Strac can protect you.

Data mapping for CCPA compliance is more than a regulatory checkbox; it’s a proactive strategy for controlling, securing, and governing personal data across your entire digital ecosystem. When done right, data mapping for CCPA compliance gives organizations the clarity to locate every piece of personal information, streamline “Right to Know” and “Right to Delete” requests, and prove accountability to regulators and customers alike.
With Strac’s agentless DSPM and DLP platform, data mapping for CCPA compliance becomes automated, continuous, and intelligent; enabling you to discover, classify, and remediate sensitive data across SaaS, cloud, and GenAI in real time. The result: stronger privacy posture, faster audits, and full transparency that builds lasting trust.
Data mapping under CCPA is the process of documenting how personal information is collected, stored, shared, and deleted across systems. It provides a visual representation of your data flows — helping organizations comply with consumer rights requests, such as data access or deletion.
Because CCPA mandates that businesses know what personal data they hold and how they use it. Accurate data mapping helps:
Manual spreadsheets are no longer enough. Automated tools like Strac streamline the process by discovering and classifying personal data across connected systems (Slack, Google Drive, Salesforce, AWS, etc.) and visualizing where sensitive data moves. This automation reduces human error and ensures compliance readiness.
A data map should be a living document, not a one-time exercise. Organizations should update it:
Strac unifies Data Security Posture Management (DSPM) and Data Loss Prevention (DLP) to automate every step of the data-mapping process:
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

