Data Loss Prevention Strategies and Best Practices
Explore effective DLP strategies and best practices to safeguard sensitive data and enhance your organization's security posture.
Data has become the backbone of every aspect of commercial operations. However, a data breach can have catastrophic consequences, leading to financial losses, reputational damage, and even legal repercussions. This makes a strong Data Loss Prevention (DLP) strategy more critical than ever.
Implementing a broad DLP strategy involves several key elements. Data classification, encryption, access controls, and incident response planning are some of the fundamental components, to name a few. This blog will highlight the many nitty-gritties of a DLP strategy, how to implement it, and some of its best practices, stating the essentiality behind it for your business.
Data Loss Prevention (DLP) refers to a cluster of tools & processes designed to assure that sensitive information is not lost, misused, or accessed by unauthorized individuals. DLP solutions monitor and control data movement across networks, endpoints, and cloud environments, applying security policies to protect sensitive information such as personal data, financial records, and intellectual property.
By classifying and tracking data, DLP systems aim to prevent unauthorized access & data breaches, ensuring compliance with regulatory standards like GDPR, HIPAA, and PCI-DSS.

Sensitive data encompasses any information that requires protection due to its confidential nature. Common categories of sensitive data include:
Identifying and classifying this data is crucial for developing effective DLP strategies.
Data loss prevention (DLP) is crucial for organizations in multiple ways, and its importance is paramount; here is why:
1. Protection of Sensitive Data: DLP ensures that sensitive data remains securely within the corporate network, preventing unauthorized access, theft, or misuse.
2. Prevention of Data Breaches: DLP helps prevent data breaches by monitoring and filtering data in real time, detecting and blocking malicious activities, and enforcing disclosure policies.
3. Compliance with Regulations: DLP helps organizations comply with data privacy regulations such as GDPR, HIPAA, and PCI-DSS by ensuring data security and confidentiality.
4. Protection from Insider Threats: DLP prevents insider threats by monitoring and controlling user activities, detecting and preventing unauthorized data access, and enforcing data usage policies.
5. Protection from External Threats: DLP protects against external threats by monitoring network traffic, detecting and blocking malicious activities, and enforcing network access policies.
6. Protection from Accidental Data Loss: DLP prevents accidental data loss by monitoring and controlling user activities, detecting and preventing unauthorized data access, and enforcing data usage policies.
7. Protection from BYOD Risks: DLP protects against BYOD risks by monitoring and controlling mobile device activities, detecting and preventing unauthorized data access, and enforcing mobile device policies.
8. Protection from Cloud Storage Risks: DLP guards against cloud storage risks by monitoring and controlling cloud storage activities, detecting and preventing unauthorized data access, and enforcing cloud storage policies.
The average cost of a data breach continues to rise as companies deal with the fallout from unauthorized access to sensitive information.
Here’s a graphical representation for you to understand the necessary:

Numerous factors lead to data breaches, and the resulting costs are substantial. Below is a chart categorizing the types of data loss within an organization.

Considering this, the question appears “What eventually leads to data breaches, and What are the primary key factors behind them?”
Here’s what we found.
1. Security System Complexity: Organizations with intricate security infrastructures often face higher costs because the complexity makes detecting and containing breaches more challenging and resource-intensive.
2. Security Skills Shortage: A lack of skilled security professionals forces organizations to rely on expensive external expertise, which can prolong breach containment and increase overall costs.
3. Noncompliance with Regulations: Noncompliance with data protection regulations can lead to hefty fines and legal expenses, significantly adding to the total cost of a data breach.
4. Ransomware and Destructive Attacks: Ransomware and destructive attacks require extensive incident response and recovery efforts, making them particularly expensive to manage and resolve.
5. Employee Training and Awareness: High levels of employee training and awareness reduce the likelihood of human error causing breaches, thereby lowering the overall costs associated with data breaches.
6. Incident Response Planning: Organizations with robust incident response plans can minimize costs as they can contain and recover from breaches more efficiently, saving time and resources.
Organizations need DLP to mitigate risks associated with data breaches and leaks. Key reasons include:

DLP is critical in cybersecurity for several reasons:
To enhance data protection through DLP, organizations can follow these strategies:

A DLP strategy is necessary when an organization recognizes the importance of protecting its sensitive data and is willing to invest in a data loss prevention program. This can occur at various stages, including:
1. After a Vulnerability Assessment: Conducting a vulnerability assessment can identify potential weaknesses in the organization’s data protection posture, making it clear that a DLP strategy is necessary to address these vulnerabilities.
2. After a Cost-Benefit Analysis: Performing a cost-benefit analysis can help organizations understand the financial implications of data breaches and the benefits of implementing a DLP strategy to mitigate these risks.
3. When Executive Leadership is On Board: Once executive leadership is committed to implementing a DLP solution, it is a good time to develop a DLP strategy. This ensures that the program is aligned with the organization’s overall goals and objectives.
4. When Data Breaches Occur: Organizations that have experienced data breaches or near-misses often recognize the need for a DLP strategy to prevent similar incidents in the future.
5. When Data is Identified as a Critical Asset: If data is identified as a critical asset, such as intellectual property or sensitive customer information, a DLP strategy is necessary to ensure its protection.
6. When Compliance Requirements are Mandated: Compliance requirements like HIPAA, GDPR, or PCI-DSS often necessitate the implementation of a DLP strategy to ensure data protection and compliance.
7. When Data is Stored or Transmitted: Anytime data is stored or transmitted, whether it is at rest or in transit, a DLP strategy should be implemented to ensure its protection.
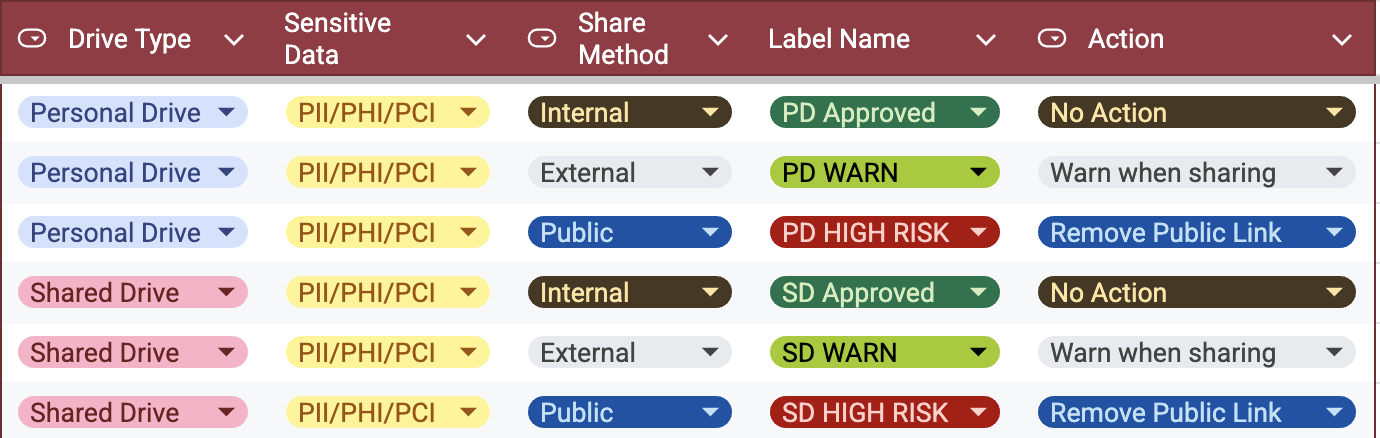
Here are the 5 pillars of an effective data loss prevention (DLP) strategy:
Identify all sensitive or confidential information across your IT ecosystem, including in cloud storage, services, and source code repositories. Data should be classified based on sensitivity levels—such as public, confidential, or critical—to prioritize its protection. Employing automated data classification tools helps identify and tag data based on predefined criteria, ensuring a systematic approach to data management.
Implementing effective access control measures involves granting users the least permissions necessary for their tasks. This includes removing default levels of trust in users or devices to mitigate insider threats and data breaches. Moreover, evolving towards a model of continually verifying user access requests through adaptive authentication enhances security.
Establishing clear policies and procedures ensures employees understand their role in safeguarding data. These policies should be regularly reinforced through reminders and audits. Additionally, developing policies stipulating who can access which data, how it can be shared, and when it can be transmitted is fundamental to maintaining data integrity.
It is necessary to continuously monitor data access patterns to identify suspicious activity or policy violations. Leveraging the analytics and insights functionalities of DLP tools provides visibility into data flows within the organization. This allows for the detection of potential data breaches in real time by continuously surveilling data movements and flagging suspicious activities.
Incident response plans should be designed to mitigate damages efficiently in case of potential data leakages or unauthorized access incidents. Swift action upon detecting potential data breaches minimizes impact, while periodic reviews of the DLP program's effectiveness and conducting audits ensure compliance with internal policies and external regulations.
Here is a concise overview of how to develop and implement an effective data loss prevention (DLP) strategy:
This involves classifying data into high-risk categories (sensitive data and intellectual property), medium-risk (operational data), and low-risk (public information) categories. It's crucial to align the policy with business requirements and information resources and address compliance with security and privacy standards like HIPAA and GDPR, especially in regulated industries.
This step includes discovering data assets across the entire computing environment to classify them accurately. It also involves identifying situations or activities that present data vulnerabilities, such as sharing sensitive data via email, transmitting data from remote endpoints, or storing data in public cloud storage.
Monitoring data movement is necessary to ensure compliance with the data handling policy, which involves subjecting every data exchange, transfer, or access to the policy, covering both internal and external uses, to maintain control over data flows.
Providing ongoing education helps reinforce the data handling policies. It is vital to educate employees on the policy and their role in protecting information resources. Providing real-time guidance when a DLP policy violation occurs can help modify behavior and prevent future incidents.
Look for a solution that can monitor all file activity in endpoints and external ports, track copy-and-paste actions, detect unwarranted data transfers, and instantly halt attempts to exfiltrate sensitive data. Also, it ensures that the solution can operate on classified content and enforces policies through the infrastructure. Once done, deploy the DLP solution in phases, starting with a small subset of policies to build a baseline and then expanding
It is essential to fine-tune and update the DLP strategy regularly. Adjusting risk profiles, policies, and rules regularly helps reduce false positives, enhance effectiveness, and realign the strategy with changing business needs. Maintaining clear communication and controls for reducing data risk and escalating as needed ensures the continued effectiveness of the DLP strategy.
Here are the 7 best practices for implementing an effective data loss prevention (DLP) strategy with descriptions in paragraph form:
Identifying the crown jewels involves classifying data based on sensitivity levels to prioritize protection. This involves determining which organizational data needs to be protected, such as personally identifiable information (PII), financial data, and intellectual property. Organizations can focus their DLP efforts on the most valuable and sensitive information by identifying the most critical data assets.
Comparing multiple vendors requires understanding your organization's size, industry, regulatory requirements, and specific data protection needs. This includes looking for a DLP solution that can monitor data movement across endpoints, networks, and cloud storage. By researching multiple vendors, organizations can find the best solution for their specific needs and ensure that it meets their data protection requirements.
Defining incident response and remediation involves specifying the steps to be taken when suspicious activity is detected and who is responsible for each of them. This includes having an incident response plan in place to mitigate damages efficiently in case of potential data leakages or unauthorized access incidents. By defining incident response and remediation, organizations can ensure that they are prepared to respond quickly and effectively in the event of a data breach.
By deploying DLP in phases, you build a baseline of policies by deploying only a small subset of policies, then expand from there. This approach allows organizations to gradually build their DLP capabilities and refine their policies over time. By implementing DLP in phases, organizations can ensure that they are building a robust and effective data loss prevention strategy.
Performing a proof of concept exercise involves testing the DLP solution in a controlled environment to ensure it meets your organization's specific requirements. This includes validating the solution's ability to detect, prevent, and respond to data loss incidents in real-world scenarios. By performing a proof of concept exercise, organizations can ensure that the DLP solution is effective and meets their specific needs.
Identifying the DLP stakeholders and support team involves engaging key stakeholders from various departments, such as IT, security, compliance, and legal. This includes establishing a dedicated DLP support team responsible for managing the solution, investigating incidents, and refining policies. By identifying the DLP stakeholders and support team, organizations can ensure that they have the necessary resources and expertise to implement and maintain their DLP strategy.
Continuously monitoring and refining policies involves regularly monitoring data access patterns and looking for suspicious activity or policy violations. This includes adjusting policies and tools as needed based on real-world performance and emerging threats. By continuously monitoring and refining policies, organizations can ensure that their DLP strategy remains effective and up-to-date.
Here are five prevalent misconceptions that could undermine your data loss prevention (DLP) strategy, countered with the facts:
Fact: Contemporary DLP options have streamlined the requirement for internal resources. Advances in automation and the advent of managed security services have dramatically reduced the expenditures associated with hosting, setup, monitoring, tuning, and maintenance. Managed Service Providers (MSPs) offer comprehensive data protection solutions that eliminate the need for additional hardware or staffing, significantly reducing the total cost of ownership for DLP programs.
Fact: Modern, modular DLP architectures can start delivering benefits within days. These solutions are designed for incremental deployment, allowing for an evolving data protection strategy that begins with a foundational solution providing immediate value and scales by adding specific modules over time. This approach enables organizations to tailor their DLP infrastructure, purchasing only necessary modules and expanding capabilities as their data protection needs grow.
Fact: Content- and context-aware DLP systems can autonomously gather data on usage and movement, equipping business leaders with the insights needed to craft more effective data protection policies. With the expertise of MSPs, DLP professionals can identify and categorize critical data, pinpoint risky user behaviors, and formulate targeted policies that safeguard sensitive information.
Fact: DLP can be strategically implemented in phases. Organizations may start with a select group of policies to establish a foundational risk profile and then progressively broaden their DLP framework. Regular adjustments to risk profiles, policies, and rules are critical to minimizing false positives, boosting overall effectiveness, and ensuring alignment with evolving business objectives.
Fact: Modern DLP systems can monitor data movements across various platforms, including endpoints, networks, and cloud environments. These solutions enforce data governance policies throughout the digital infrastructure, ensuring protection for newly created data, data residing in legacy systems, and newly integrated information. DLP technologies enable device lockdowns, cloud service scanning, and real-time prevention of data exfiltration attempts, whether through hardware or software.
Here are some advanced data loss prevention (DLP) techniques and tools in a tabular form:
To effectively protect against data loss, organizations should consider a comprehensive DLP solution that combines pattern matching, fingerprinting, endpoint protection, and network monitoring capabilities. Strac offers a unified DLP platform that integrates these advanced techniques and tools to provide complete data protection across the organization.
Effective data security is pivotal for safeguarding sensitive information and ensuring organizational success. Below, we outline a strategic approach to fortify your data protection efforts.
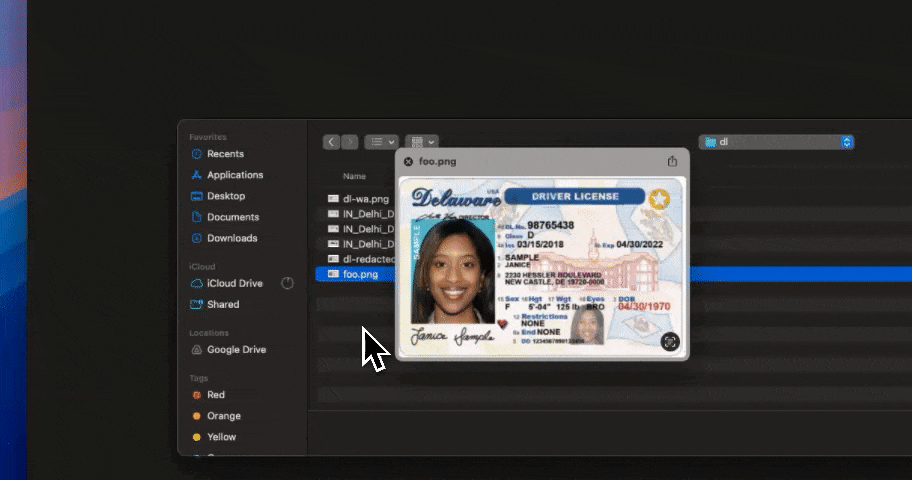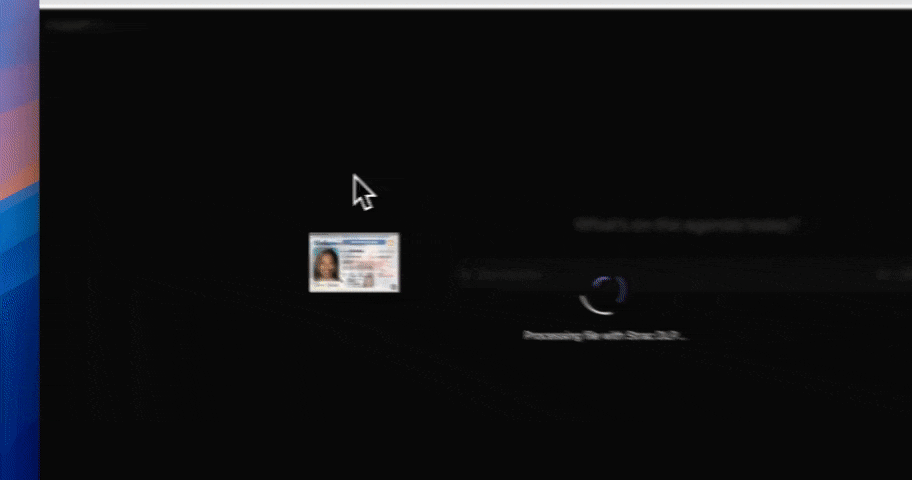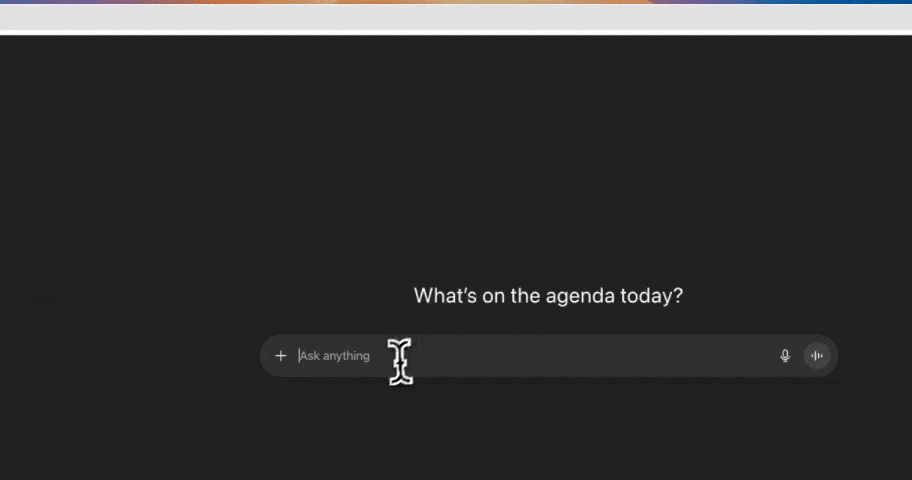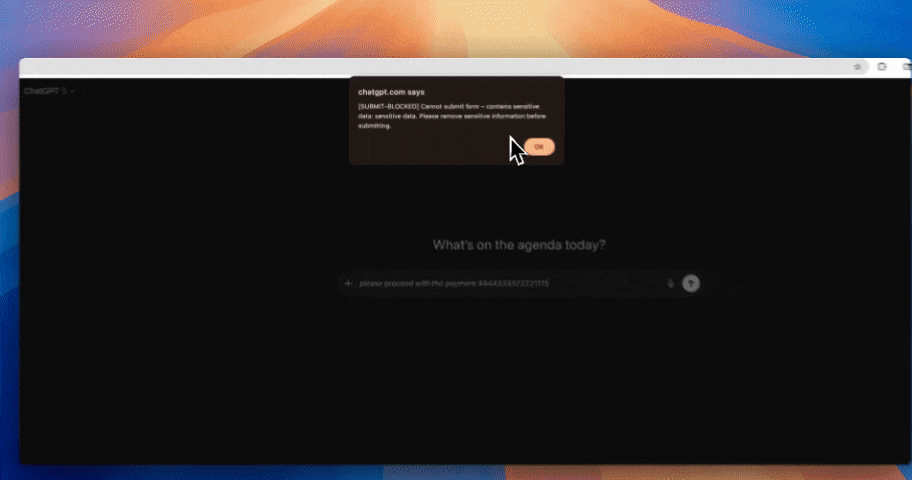
Strac offers advanced data classification capabilities using AI and ML to identify sensitive data across various applications and endpoints. This includes detecting and classifying PII, PHI, PCI, and other sensitive data types.
It provides real-time redaction and alerting capabilities to protect sensitive data across various communication channels, including email, Slack, Teams, Zendesk, and Notion. Strac's redaction technology can detect and mask sensitive data in real time, ensuring compliance with regulatory requirements.
Strac offers seamless integration with various SaaS applications, including email, Slack, Teams, Zendesk, Notion, and more. This allows for real-time detection and protection of sensitive data across these platforms.
Strac also provides endpoint DLP protection for devices such as Mac and Windows, ensuring that sensitive data is protected even when accessed or transferred outside the organization.
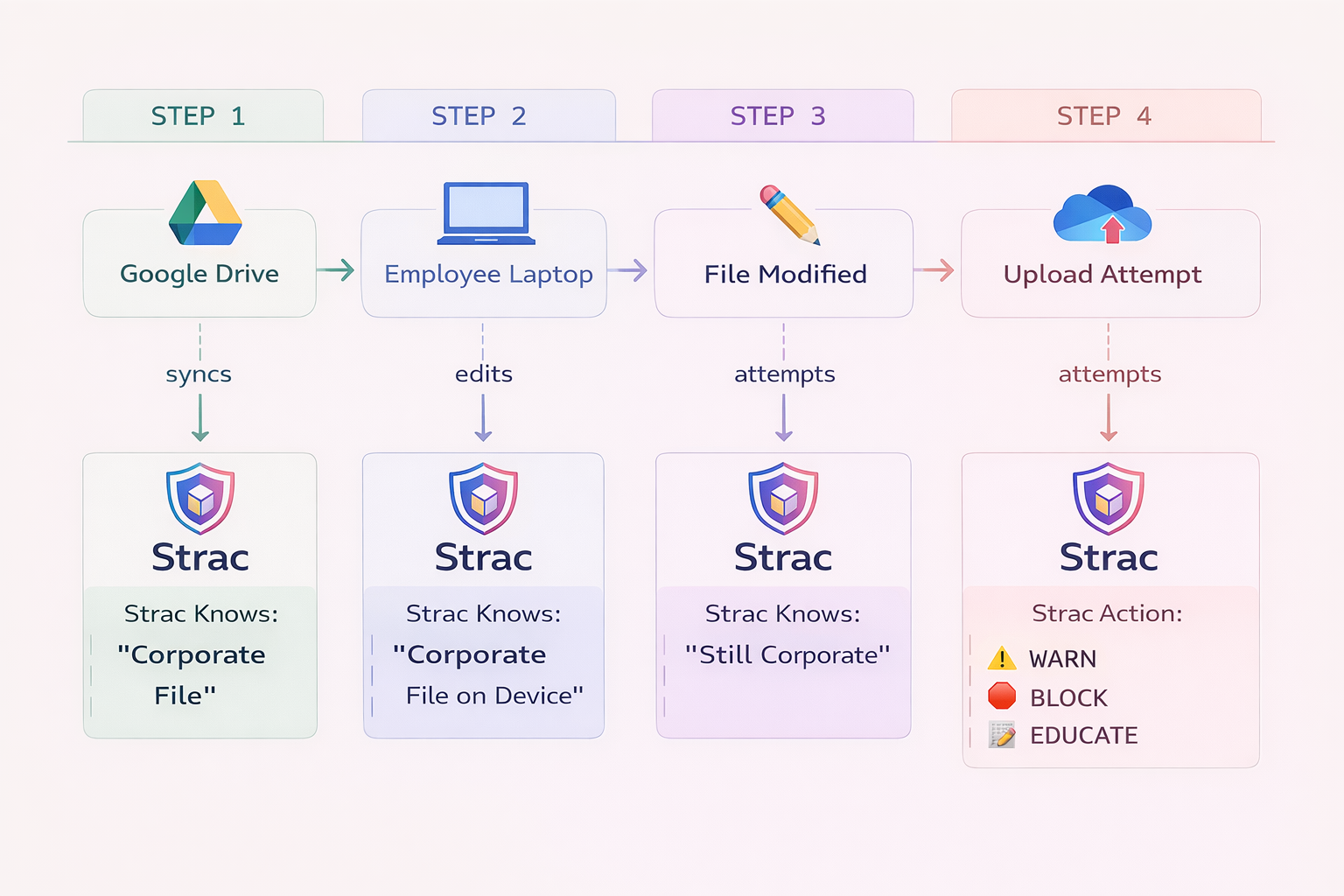
The platform also leverages AI and ML to enhance data classification capabilities, ensuring that sensitive data is accurately identified and protected. This includes advanced algorithms for detecting and classifying sensitive data in unstructured text and documents.
Take the first step towards enhanced data security by consulting with Strac’s experts today. Schedule a Demo call today and protect your organizational information unlike ever before.
Data Loss Prevention isn’t a “nice to have.” If your business handles customer data, financial records, health information, or intellectual property; you need it.
A strong DLP strategy gives you visibility into where sensitive data lives and control over how it moves. It helps you reduce breach risk, stay compliant, and respond faster when something goes wrong.
Modern DLP goes beyond alerts. It discovers, classifies, and remediates risk across SaaS apps, cloud storage, endpoints, and even AI tools; without slowing teams down
Protecting data where it actually lives today is what separates reactive security from real security.
The primary goal of a DLP strategy is to prevent sensitive data from being exposed, misused, or exfiltrated. This includes protecting data at rest, in motion, and in use across SaaS apps, endpoints, cloud environments, and AI tools. A mature DLP strategy not only detects risks but also enforces policies and automates remediation.
No. Small and mid-sized businesses are often more vulnerable because they lack dedicated security teams. Any organization handling PII, financial data, health records, intellectual property, or regulated data needs DLP; regardless of size. In fact, SMBs benefit significantly from modern, easy-to-deploy DLP platforms.
Traditional DLP focused on email gateways and network perimeters. Modern SaaS DLP protects data directly inside tools like Slack, Google Workspace, Salesforce, Zendesk, and AI platforms. It monitors real-time conversations, attachments, uploads, and API flows; not just network traffic.
Implementation timelines vary. Traditional enterprise DLP deployments could take months. Modern agentless DLP platforms can be deployed in days or weeks, especially when rolled out in phases; starting with discovery and expanding into enforcement.
Legacy DLP tools were known for high false positives and workflow friction. Modern solutions use ML-based classification and inline remediation to reduce noise and avoid unnecessary disruptions. When properly configured, DLP should protect data without slowing productivity.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

