Ensuring PCI DSS compliance is critical for any business handling payment card data, especially in the cloud. Amazon Web Services (AWS) provides a scalable and secure platform, but achieving compliance requires understanding and implementing specific security measures.
For founders and executives of e-commerce and financial services companies, navigating PCI DSS requirements in an AWS environment is essential to protect cardholder data and maintain customer trust.
This guide will provide a comprehensive overview of AWS’s capabilities, best practices, and additional tools to ensure PCI DSS compliance.
Understanding PCI DSS Compliance
Brief Overview of PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Established by the PCI Security Standards Council, PCI DSS aims to protect cardholder data from breaches and fraud. Its relevance to cloud services is significant because many businesses leverage cloud providers like AWS to manage their payment processing and data storage needs. Compliance with PCI DSS helps businesses mitigate the risk of data breaches and demonstrates their commitment to data security to customers and partners.
PCI DSS Compliance Requirements
PCI DSS compliance involves adhering to twelve key requirements, which are organized into six control objectives:
- Build and Maintain a Secure Network and Systems:some text
- Install and maintain a firewall configuration to protect cardholder data: Firewalls control the traffic between trusted internal networks and untrusted external networks.
- Do not use vendor-supplied defaults for system passwords and other security parameters: Default passwords are easily guessable and should be changed to something unique and secure.
- Protect Cardholder Data:some text
- Protect stored cardholder data: Data should be encrypted using strong encryption methods.
- Encrypt transmission of cardholder data across open, public networks: SSL/TLS or other encryption methods should be used to secure data in transit.
- Maintain a Vulnerability Management Program:some text
- Protect all systems against malware and regularly update anti-virus software or programs: Anti-virus software should be used and regularly updated to protect against malware.
- Develop and maintain secure systems and applications: Apply security patches and updates promptly to mitigate vulnerabilities.
- Implement Strong Access Control Measures:some text
- Restrict access to cardholder data by business need to know: Only authorized personnel should have access to cardholder data.
- Identify and authenticate access to system components: Use unique IDs for each person with computer access to ensure accountability.
- Restrict physical access to cardholder data: Physical security measures should be in place to prevent unauthorized access to data storage areas.
- Regularly Monitor and Test Networks:some text
- Track and monitor all access to network resources and cardholder data: Implement logging mechanisms to track user activities and detect security events.
- Regularly test security systems and processes: Conduct regular scans and penetration testing to identify vulnerabilities.
- Maintain an Information Security Policy:some text
- Maintain a policy that addresses information security for all personnel: Ensure all employees are aware of and adhere to security policies and procedures.
For cloud service providers like AWS, these requirements necessitate robust security measures and processes to ensure the protection of cardholder data. AWS supports PCI DSS compliance by offering services and tools that help businesses implement these requirements effectively, but the responsibility for maintaining compliance is shared between AWS and its customers.
AWS and PCI DSS Compliance
AWS PCI DSS Certification
Amazon Web Services (AWS) has achieved PCI DSS certification, which signifies that its infrastructure meets the stringent security requirements set by the Payment Card Industry Data Security Standard. This certification covers a wide range of AWS services, including Amazon EC2, Amazon S3, Amazon RDS, and AWS Lambda, among others. The PCI DSS certification ensures that these services are designed to securely store, process, and transmit cardholder data.
AWS’s PCI DSS certification provides assurance to businesses that they can build and host their payment processing applications on AWS’s infrastructure while maintaining compliance with PCI DSS standards. AWS regularly undergoes third-party audits to ensure its services remain compliant with the latest PCI DSS requirements. This certification simplifies the compliance process for businesses using AWS, as they can rely on AWS’s certified infrastructure to meet many of the technical and physical security requirements of PCI DSS.
Shared Responsibility Model
Understanding the division of responsibilities between AWS and its customers is crucial for maintaining PCI DSS compliance. AWS operates under a shared responsibility model, where both AWS and the customer have specific security and compliance obligations.
- AWS Responsibilities: AWS is responsible for securing the underlying infrastructure that supports its cloud services. This includes hardware, software, networking, and facilities that run AWS services. AWS’s responsibility extends to maintaining the physical security of its data centers, network infrastructure, and the hardware used to run the cloud services. AWS ensures that its infrastructure is compliant with PCI DSS requirements and provides the necessary tools and services to help customers achieve compliance.
- Customer Responsibilities: Customers are responsible for securing the data they store and process in the AWS environment. This includes configuring their AWS services securely, managing user access, and ensuring that their applications and data are protected. Customers must implement strong access controls, data encryption, regular monitoring, and vulnerability management to meet PCI DSS requirements. While AWS provides the infrastructure and tools, customers must use these resources effectively to achieve compliance.
The shared responsibility model requires customers to understand their security obligations and take proactive steps to secure their AWS environment. By leveraging AWS’s PCI DSS-certified services and following best practices for cloud security, businesses can ensure they meet PCI DSS standards and protect cardholder data.
For more detailed information on AWS’s PCI DSS certification and shared responsibility model, you can refer to AWS's official PCI Compliance documentation.
Key AWS Services for PCI DSS Compliance
Data Encryption
AWS provides robust encryption mechanisms to protect cardholder data both at rest and in transit. For data at rest, AWS offers server-side encryption (SSE) for services like Amazon S3 and Amazon RDS. These services use AES-256 encryption, a strong encryption standard recommended by PCI DSS. Additionally, AWS Key Management Service (KMS) allows customers to create and manage encryption keys, ensuring that only authorized users can decrypt sensitive data.
For data in transit, AWS uses Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols to encrypt data as it moves between systems. This ensures that cardholder data is protected from interception and unauthorized access during transmission. By utilizing these encryption features, businesses can ensure that their cardholder data is securely encrypted in accordance with PCI DSS requirements.
Access Controls
AWS Identity and Access Management (IAM) provides comprehensive access control features to manage who can access your AWS resources and what actions they can perform. IAM allows businesses to create and manage AWS users and groups, and assign permissions using fine-grained policies. Multi-factor authentication (MFA) can be enforced to add an additional layer of security, ensuring that only authorized users can access sensitive data.
Additionally, AWS provides features like AWS Organizations and Service Control Policies (SCPs) to centrally manage and enforce access policies across multiple AWS accounts. These tools help businesses implement the principle of least privilege, granting users only the permissions necessary to perform their tasks and reducing the risk of unauthorized access to cardholder data.
Audit and Monitoring
AWS offers several tools for auditing and monitoring cardholder data to ensure compliance with PCI DSS requirements. AWS CloudTrail provides detailed logs of all API calls made within your AWS account, enabling you to track user activity and detect any unauthorized access attempts. These logs can be analyzed to identify security events and ensure that access to cardholder data is properly monitored.
AWS Config helps you continuously monitor and record your AWS resource configurations, ensuring that they comply with your security policies and PCI DSS requirements. AWS Config Rules can be used to automatically check the compliance of your resources and trigger alerts when configurations drift from your desired state.
Amazon CloudWatch provides real-time monitoring of AWS resources and applications, allowing you to set up custom alarms and dashboards to track key metrics and events. CloudWatch Logs can be used to centralize and analyze log data from various sources, helping you identify and respond to security incidents promptly.
By leveraging these AWS services, businesses can implement effective data encryption, access controls, and auditing measures to achieve and maintain PCI DSS compliance, protecting cardholder data and ensuring the security of their payment processing environments.
Best Practices for Using AWS to Ensure PCI DSS Compliance
1. Implementing AWS Security Best Practices
Configuring AWS services for PCI DSS compliance involves several critical steps. Start by ensuring that all your AWS resources use strong encryption for data at rest and in transit. Utilize AWS Key Management Service (KMS) to manage encryption keys securely. Implement Identity and Access Management (IAM) policies to enforce the principle of least privilege, and enable multi-factor authentication (MFA) for all accounts accessing sensitive data. Regularly update your security groups and network access controls to restrict unnecessary access.
2. Regular Audits and Risk Assessments
Continuous monitoring and risk management are vital for maintaining PCI DSS compliance. Conduct regular security audits using AWS tools like CloudTrail, Config, and CloudWatch to monitor and log all activities within your AWS environment. These tools help identify potential security threats and ensure that your configurations comply with PCI DSS requirements. Perform regular vulnerability assessments and penetration tests to identify and remediate any weaknesses in your infrastructure.
3. Employee Training and Awareness
Ensuring that your staff is well-trained on PCI DSS requirements and AWS security configurations is crucial. Regularly conduct training sessions and workshops to educate employees about the importance of data security, best practices for using AWS, and the specific compliance requirements of PCI DSS. Awareness programs help reinforce the importance of adhering to security protocols and staying updated on the latest threats and compliance standards.
4. Implementing Data Loss Prevention (DLP) Solutions
In addition to the aforementioned practices, implementing a Data Loss Prevention (DLP) solution is essential for comprehensive security and compliance. DLP solutions like Strac integrate seamlessly with AWS to provide advanced protection for cardholder data. Strac’s DLP features include automated data discovery, real-time monitoring, and robust encryption, ensuring that sensitive data is protected from unauthorized access and potential breaches. By using a DLP solution, businesses can enhance their security posture and ensure continuous compliance with PCI DSS standards.
Following these best practices ensures that your AWS environment is secure and compliant with PCI DSS, protecting cardholder data and maintaining customer trust.
Using Strac DLP for Ensuring PCI DSS Compliance with AWS
Overview of Strac’s DLP Solutions
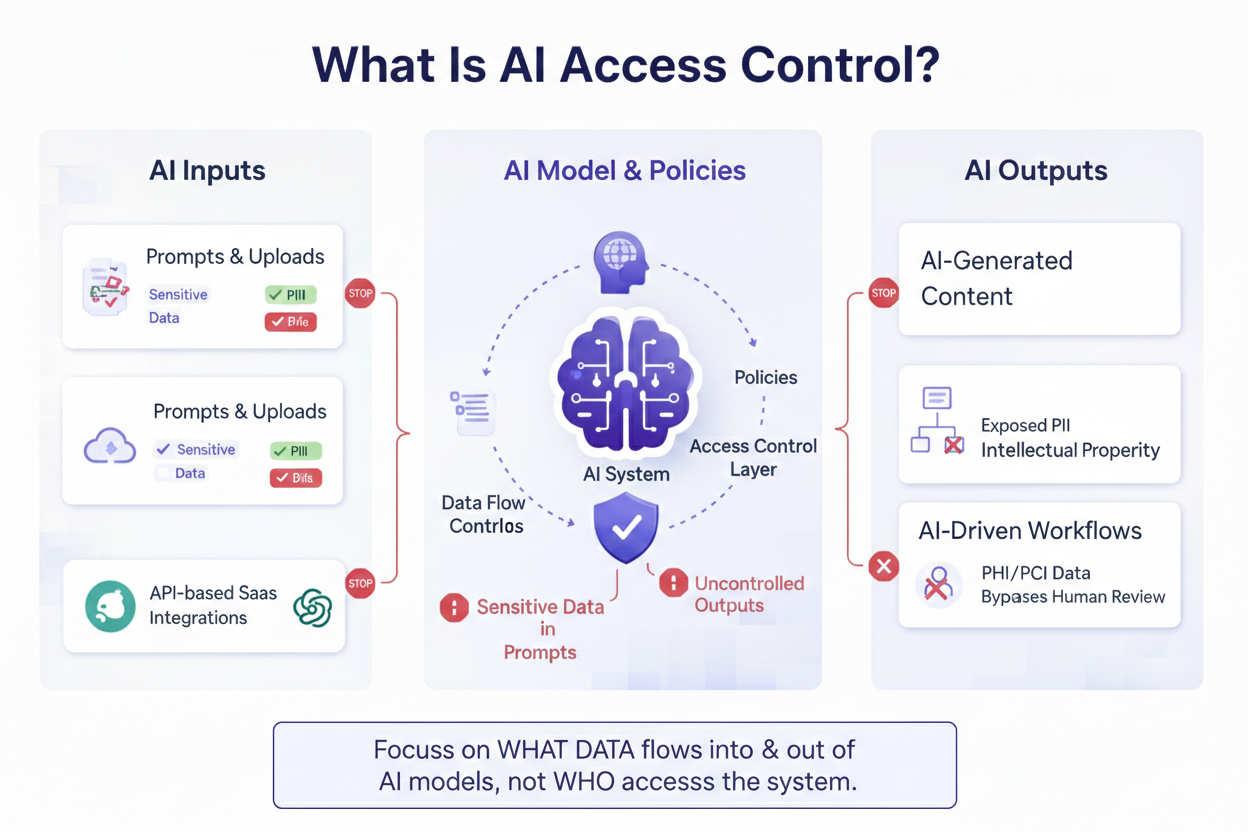
Strac’s Data Loss Prevention (DLP) solutions are designed to integrate seamlessly with AWS, providing comprehensive protection for sensitive payment card data.
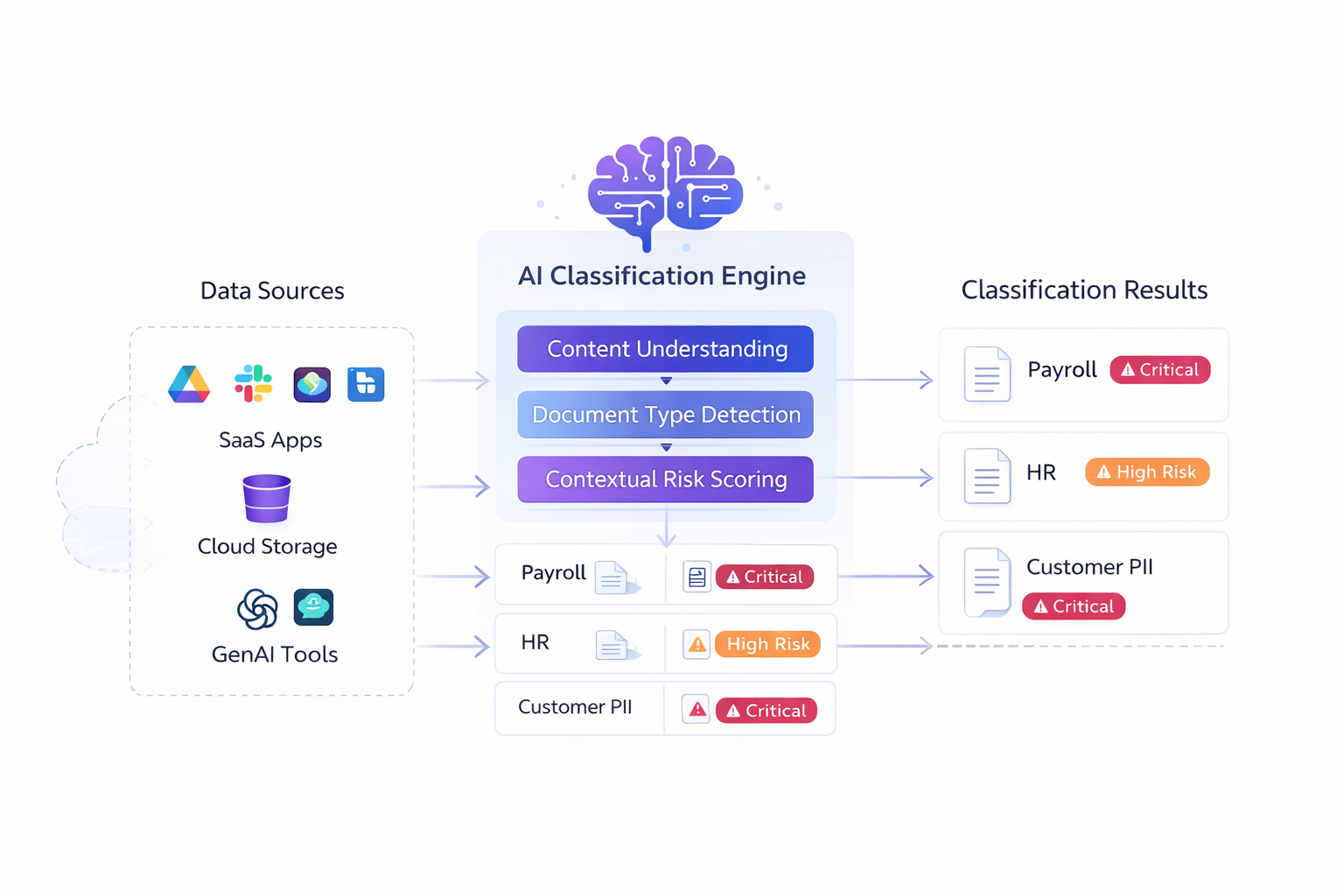
Strac leverages AWS’s robust infrastructure to offer advanced features such as automated data discovery and classification. This functionality continuously scans your AWS environment to identify and categorize cardholder data, ensuring that all sensitive information is accurately tracked and protected.
Strac’s DLP also includes real-time monitoring and alerting capabilities, which are crucial for maintaining PCI DSS compliance. By integrating with AWS CloudTrail and CloudWatch, Strac provides continuous oversight of data access and usage, allowing for immediate detection and response to potential security threats.
Additionally, Strac uses AWS Key Management Service (KMS) for managing encryption keys, ensuring that data is securely encrypted both at rest and in transit.
Benefits of Using Strac with AWS for PCI DSS Compliance
Using Strac’s DLP solutions in conjunction with AWS offers several key benefits that enhance security, monitoring, and compliance efforts:
- Enhanced Security: Strac’s robust encryption and access control features ensure that cardholder data is protected from unauthorized access and breaches. By implementing multi-factor authentication and role-based access controls, Strac ensures that only authorized users can access sensitive data, significantly reducing the risk of data breaches.
- Comprehensive Monitoring: Strac provides continuous monitoring of your AWS environment through integrations with AWS CloudTrail and CloudWatch. This real-time monitoring helps identify suspicious activities and potential security incidents promptly. Strac’s automated alerts enable quick responses to threats, ensuring that any unauthorized access attempts are detected and mitigated immediately.
- Automated Compliance: Strac’s automated data discovery and classification tools simplify the process of maintaining PCI DSS compliance. These tools ensure that all cardholder data is accurately identified and protected, reducing the risk of non-compliance. Strac’s solutions also generate detailed audit logs and reports, making it easier to demonstrate compliance during audits.
- Scalability: Strac’s DLP solutions are designed to scale with your business needs. As your company grows and your data management requirements increase, Strac’s solutions can adapt to provide continuous protection and compliance support. This scalability ensures that your security measures remain robust and effective as your AWS environment evolves.
- Simplified Audits: With Strac’s comprehensive audit trails and logging capabilities, conducting regular security audits becomes more straightforward. These logs provide detailed insights into data access and activity, helping ensure ongoing compliance with PCI DSS regulations. Strac’s automated reporting features streamline the audit process, making it easier to identify and address any compliance gaps.
Integrating Strac’s DLP solutions with AWS allows businesses to enhance their data protection measures, ensuring PCI DSS compliance and safeguarding sensitive cardholder data. By leveraging Strac’s advanced security features, businesses can maintain a secure and compliant environment, fostering trust with their customers and stakeholders.
Conclusion
Ensuring PCI DSS compliance on AWS involves leveraging AWS’s PCI DSS-certified services, implementing strong encryption and access controls, and utilizing tools like Strac’s DLP for enhanced security and monitoring. AWS provides a robust infrastructure with built-in security features, but businesses must configure these services correctly to protect cardholder data.
Strac’s DLP solutions integrate seamlessly with AWS, offering automated data discovery, real-time monitoring, and robust encryption, which help in maintaining PCI DSS compliance more efficiently.
Continuous diligence and regular updates are vital for maintaining compliance and protecting cardholder data. Regular security audits, employee training, and proactive risk management ensure that security measures remain effective against evolving threats. Businesses must remain vigilant and adapt their strategies to address new vulnerabilities. Book a demo with Strac to know more about comprehensive data protection strategies.











.webp)














.webp)


.webp)






.avif)






.gif)
