Google Drive has become the largest unstructured data graveyard in most companies — files from 2016, old PDFs, salary spreadsheets, customer IDs, PHI, PCI, screenshots, secrets, and product docs… all sitting somewhere in Drive with unknown access.
And here’s the uncomfortable truth:
You can’t protect what you can’t see.
That’s exactly where Google Drive DSPM (Data Discovery) comes in.
This is the guide you wish existed years ago — tactical, real-world, and written specifically for Google Drive.
TL;DR (Numbered)
- Google Drive DSPM (Data Discovery) gives full visibility into sensitive data across all existing files — not just new uploads.
- Most risk comes from historical files, public links, external sharing, and orphaned documents.
- DSPM identifies what data exists, where it lives, who has access, and how exposed it is.
- Remediation includes labeling, removing public access, removing external users, and revoking shared links.
- DSPM is critical before rolling out AI like Gemini or Copilot.
- Strac provides automated scanning, risk scoring, access mapping, and bulk remediation for Google Drive.
What Is Google Drive DSPM (Data Discovery)?
Google Drive DSPM (Data Discovery) is the process of:
- Discovering all sensitive data stored in Google Drive
- Classifying it (PII, PHI, PCI, secrets, IP, confidential docs)
- Mapping access (internal, external, public, third-party)
- Assessing risk
- Remediating exposure
In short:
DSPM = Visibility + Understanding + Action
✨ Google Drive DSPM (Data Discovery) vs Google Drive DLP — Why You Need Both

Think of it as:
✅ DSPM = X-ray
✅ DLP = Treatment
Once DSPM uncovers where sensitive data lives and how exposed it is, companies need Google Drive DLP to prevent new uploads, shares, and leaks moving forward.
👉 Learn more with our Google Drive DLP solution
This pairing creates true closed-loop protection.
✨ Why Companies Need Google Drive DSPM (Data Discovery)
Google Drive has become the default place for:
- HR onboarding docs
- Support screenshots
- Customer exports
- Finance spreadsheets
- Engineering design files
- Product roadmaps
- Customer tickets and logs
- M&A and legal docs
And these problems make Drive high-risk:
✅ 1. Unstructured Data Sprawl
Employees drag, drop, upload, download, copy, clone, share — endlessly.
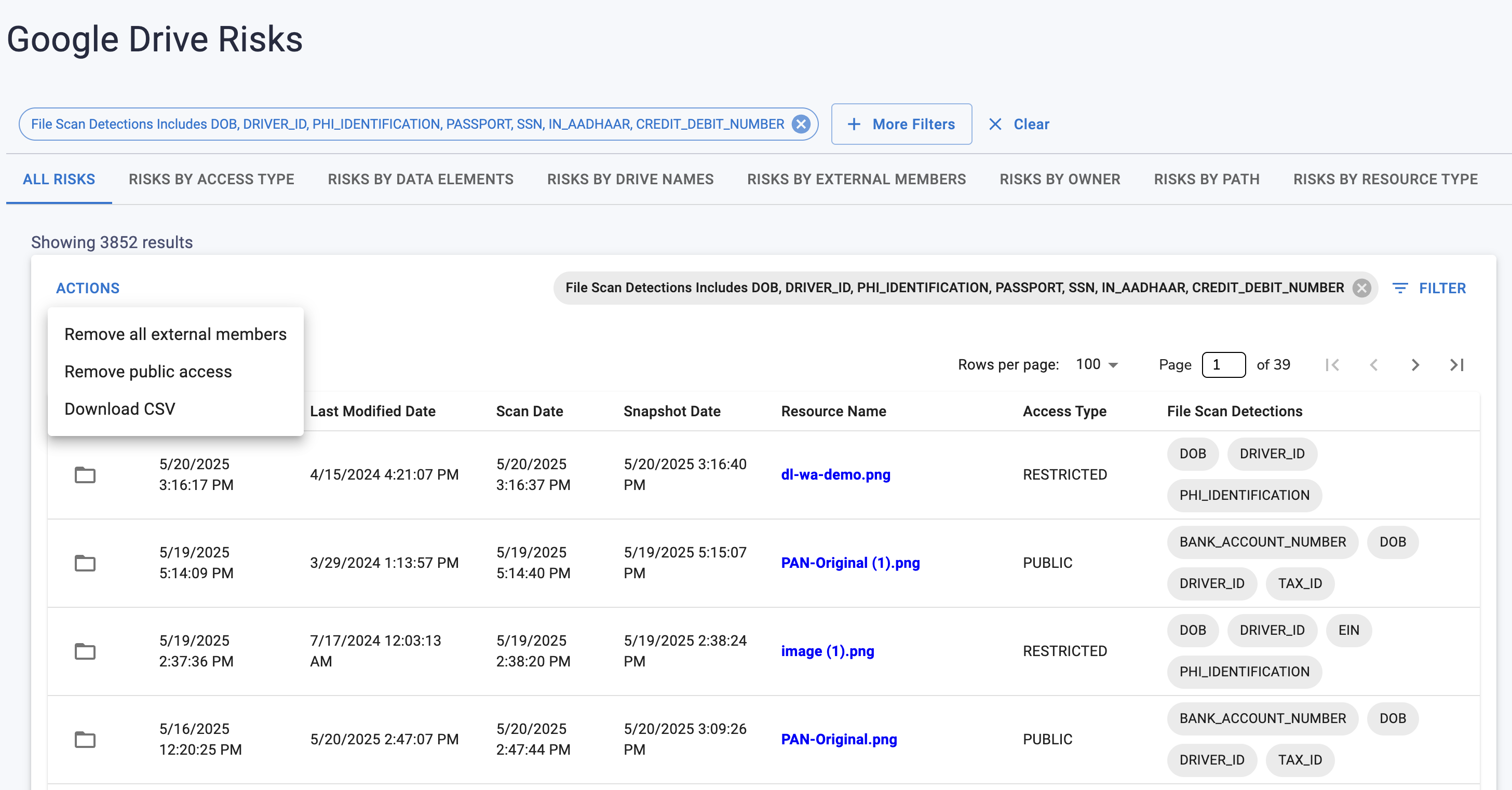
✅ 2. Public Link Exposure
"Anyone with the link" = public.
These links surface in:
- Slack
- Tickets
- ChatGPT prompts
- Browser history
✅ 3. External Users
Agencies, vendors, freelancers, interns — all gain access and rarely lose it.
✅ 4. Departed Employees
Files remain accessible.
Ownership remains unchanged.
Risk remains invisible.
✅ 5. Compliance Gaps
SOC2, HIPAA, PCI, GDPR all require:
- Data inventory
- Access control
- Retention
- Risk reduction
✅ 6. AI Risk
If Drive contains sensitive data, AI tools can access it, ingest it, and expose it.
More on that later.
✨ Historical Scanning in Google Drive DSPM (Data Discovery)

Most companies only think about what’s happening today.
The real danger lives in files from years ago.
Historical scanning answers:
- What sensitive data already exists?
- Where is it stored?
- How old is it?
- How exposed is it?
- Who has access?
- Is it public?
- Is it shared externally?
Historical scanning must cover:
✅ All My Drive files
✅ Shared Drives
✅ Old project archives
✅ PDFs (OCR)
✅ Images/screenshots (OCR)
✅ Duplicate files
✅ Version history
✅ Hidden folders
Without historical scanning, you’re blind to 90% of risk.
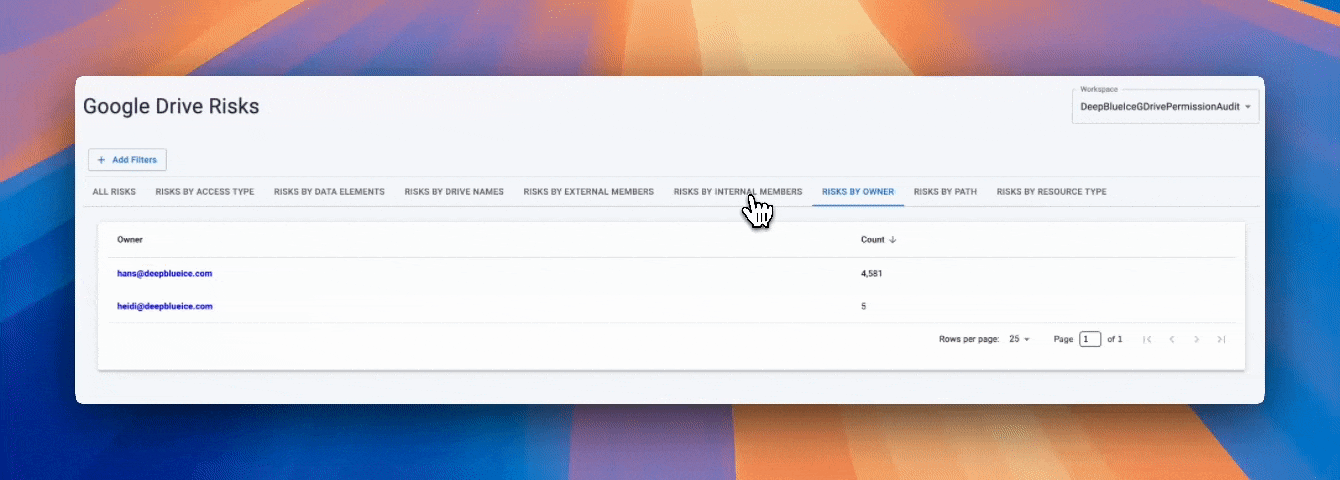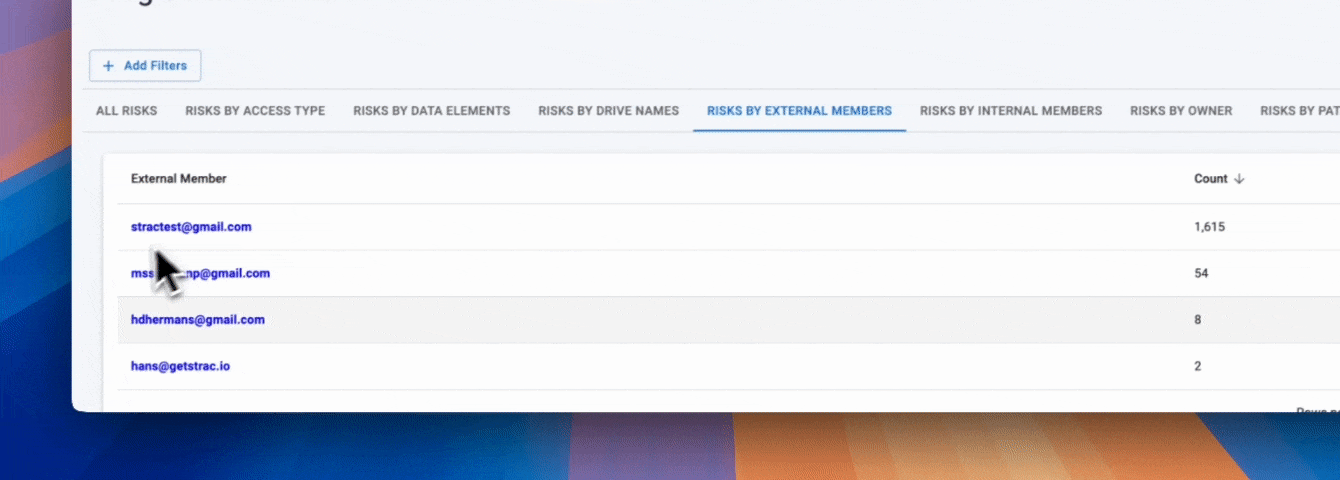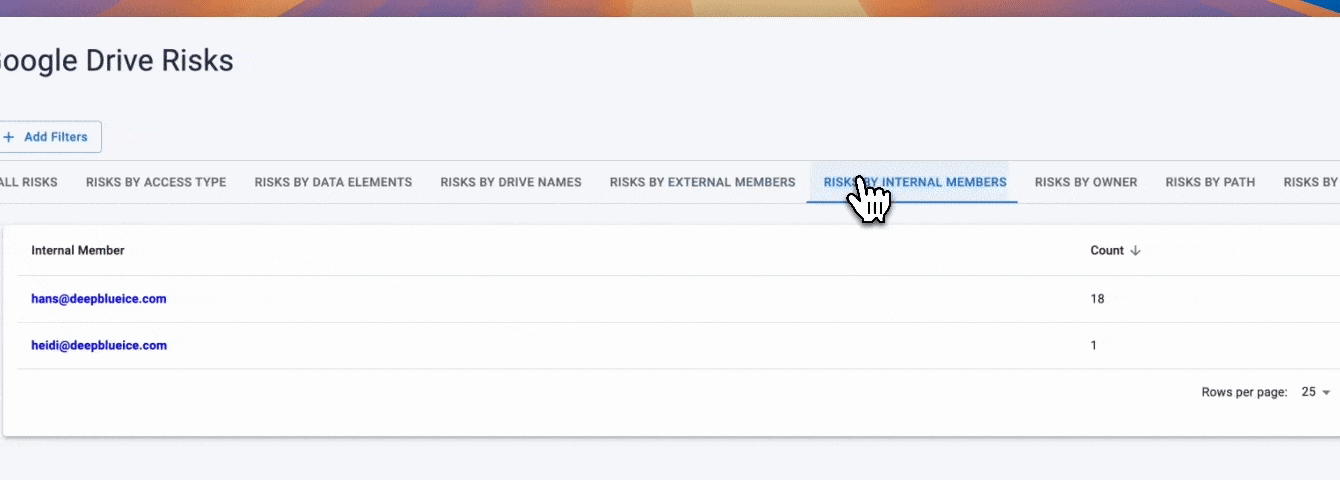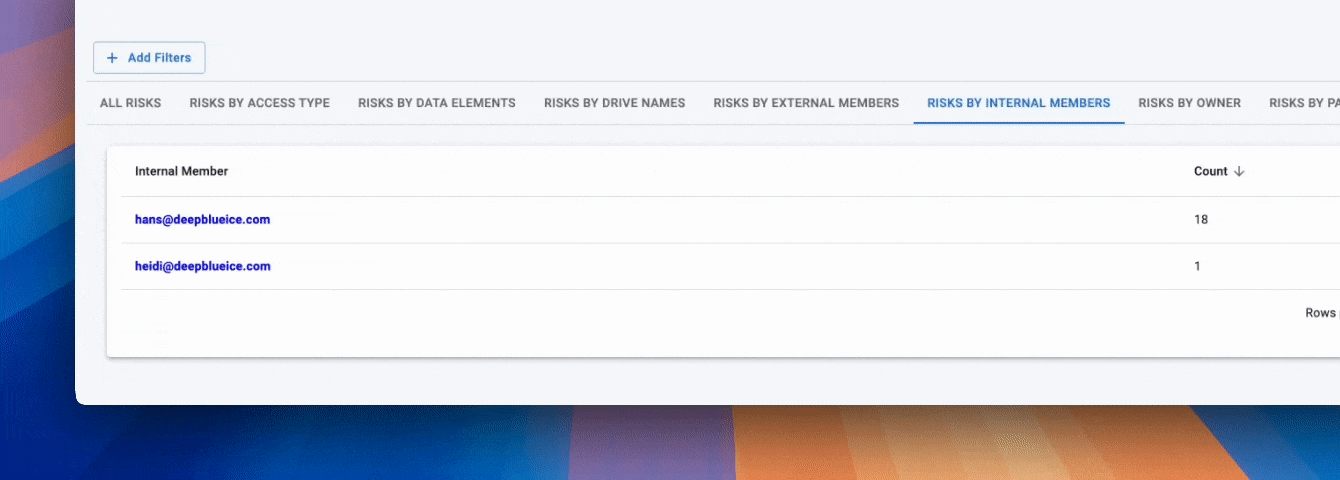
✨ Access Visibility in Google Drive DSPM (Data Discovery)
Finding sensitive data is only half the story.
You must know:
Who can see it?
Google Drive DSPM (Data Discovery) identifies:
- Files shared with external domains
- Files shared via public links
- Files owned by departed employees
- Files with over-permissioned access
- Files shared with personal Gmail accounts
- Files connected to third-party apps
- Files with unknown or orphaned ownership
This is the difference between:
“This folder contains PCI data.”
and
“This folder contains PCI data and is publicly accessible.”
Only the second is an emergency.
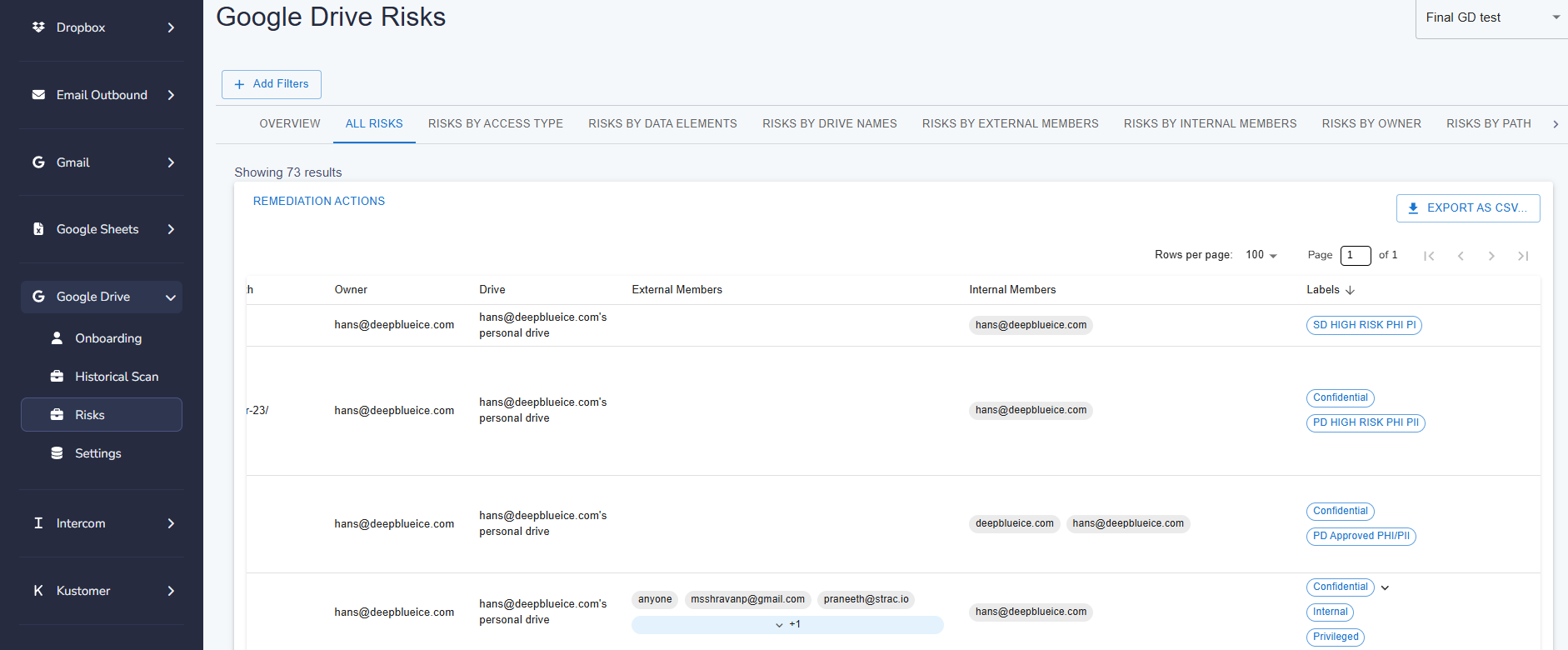
✨ Remediation in Strac Google Drive DSPM (Data Discovery)
Visibility without action is useless.
Remediation in Google Drive DSPM (Data Discovery) includes:
✅ Labeling Files
Marking documents as:
- Confidential
- Restricted
- Internal
- Public
Helps employees make better decisions.

✅ Removing Public Access
Turn "Anyone with the link" → Restricted
✅ Removing External Members
Kick out non-employees:
- Contractors
- Vendors
- Former partners
✅ Revoking Shared Links
Disables stale, risky links instantly.
✅ Reassigning Ownership
Fixes files owned by former employees.
✅ Archiving or Deleting
Reduces long-term risk.
✅ Bulk Remediation
The only scalable way to fix thousands of files.
With Strac, admins can:
- Remove public access
- Remove external users
- Apply labels
- Fix hundreds of files in one action
This is how you reduce Drive risk in hours — not months.
✨ Google Drive Labels in Strac Vault: Contextual DSPM for Classified Data
In a DSPM workflow, labels alone are not enough. A “confidential” or “restricted” label does not explain whether a file is overexposed, externally accessible, or sitting in a risky location. Strac brings Google Drive labels directly into the Strac Vault and evaluates them together with continuous data discovery and exposure signals, giving security teams a clear picture of how labeled data is actually positioned across Google Drive.
✅ Google-native Drive labels appear automatically inside Strac Vault alongside discovered sensitive data
✅ Labeled files are analyzed with access paths, external sharing, public links, owners, and locations
✅ Risk prioritization is driven by both classification and real exposure posture, not labels alone
✅ Label updates stay synchronized with Google Drive, preserving a single source of truth
By correlating labels with live DSPM insights, Strac turns Google Drive classification into an actionable security signal. Teams can immediately identify where their most sensitive labeled data lives, how it is exposed, and which risks require remediation first.
How Google Drive DSPM (Data Discovery) Protects Against AI & GenAI Risk
AI isn't just a productivity tool — it’s a data amplification engine.
When AI systems like Google Gemini, Microsoft Copilot, ChatGPT Drive plugins, and browser AI agents connect to Google Drive, they gain the ability to:
✅ Index
✅ Analyze
✅ Summarize
✅ Reference
✅ Generate content from
✅ Retain embeddings of
…the data stored inside Drive.
This creates FOUR massive new risks:
✅ AI RISK #1: Accidental Exposure Through AI Responses
If sensitive data lives in Google Drive, AI can:
- Surface salary data during a chat
- Reveal PHI in a summary
- Pull API keys or secrets into a generated document
- Include customer PII in an auto-composed email
AI doesn’t understand confidentiality — it understands relevance.
If a query matches the data, AI may use it.
Example:
“Show me the latest marketing performance numbers.”
AI might pull financial spreadsheets never meant to be shared.
✅ AI RISK #2: AI Training & Memory Risk
Depending on the AI system:
- Prompts
- Files
- Context
- Embedded vectors
…may be retained, logged, or used for future model improvement.
If Drive contains:
- PHI
- PCI
- Employee SSNs
- Customer documents
- Legal contracts
- Source code
- Secrets
That data could:
- Leave organizational boundaries
- Get referenced in other contexts
- Become part of model behavior
If it goes into the model, you lose control forever.
✅ AI RISK #3: "Privilege Escalation by AI"
AI systems often have access that exceeds human least-privilege.
Example:
An employee in Support may only access their customer files —
but Copilot or Gemini may have access to the entire Drive corpus.
Meaning:
AI becomes the most privileged user in the company.
If Drive has exposed sensitive data, AI can unintentionally bypass human access boundaries.
This turns AI into a single point of catastrophic leakage.
✅ AI RISK #4: Shadow AI Workflows
Employees now:
- Paste Drive links into ChatGPT
- Upload files for summarization
- Drag screenshots into AI tools
- Ask AI to generate reports using exported CSVs
This pushes sensitive Drive data into unmonitored systems.
DSPM becomes critical because:
You cannot govern AI usage if you don’t know what’s in Google Drive.
✅ Why Google Drive DSPM Is Step Zero for AI
Before you enable AI inside Google Workspace:
You MUST know:
- What sensitive data exists
- Where it lives
- Who can access it
- Whether it's public or external
- Whether it's appropriate for AI visibility
DSPM answers these questions and creates:
✅ An “AI-safe dataset”
✅ A least-privilege access baseline
✅ A governed perimeter of what AI should and shouldn’t see
Once DSPM identifies and remediates exposure, DLP prevents new sensitive uploads or links from entering Drive.
DSPM ≠ DLP ≠ AI governance.
They stack like this:
DSPM → Discover & remediate existing data
DLP → Prevent future leaks
AI Governance → Control AI access & behavior
Without DSPM, AI governance is blind.
Without DLP, AI governance is porous.
How Strac Solves Google Drive DSPM (Data Discovery)
Strac provides:
✅ Historical scanning
✅ OCR for images & PDFs
✅ Real-time monitoring
✅ Sensitive data classification (PII, PCI, PHI, IP, secrets)
✅ Access visibility
✅ Public link detection
✅ Risk scoring
✅ Bulk remediation
✅ Labels & restrictions
✅ Alerts to Slack/Teams/SIEM
✅ Compliance reporting (SOC2, HIPAA, PCI, GDPR)
Strac supports:
- Google Drive
- Slack
- Teams
- SharePoint
- Salesforce
- Zendesk
- Jira
- AWS
…and dozens more.
🔗 Explore all integrations: https://www.strac.io/integrations
🌶️ Spicy FAQs on Google Drive DSPM (Data Discovery)
Does Google Drive already protect sensitive data, so why do we need Google Drive DSPM (Data Discovery)?
Google Drive protects storage — not exposure.
DSPM identifies sensitive data, maps access, and fixes risk that Drive will never surface.
Can Google Drive DSPM (Data Discovery) help prevent AI tools like Gemini or Copilot from leaking data?
Yes — by removing sensitive exposure before AI is enabled.
Can Google Drive DSPM (Data Discovery) find sensitive data in PDFs, images, or screenshots?
Only if it includes OCR. Strac does.
What’s the difference between Google Drive DSPM and Google Drive DLP?
DSPM finds historical risk.
DLP enforces real-time policy.
You need both. And Strac is the only platform that does both. Here is a detailed blog post on Strac Google Drive DLP.
Can Google Drive DSPM (Data Discovery) automatically remove public access or external users?
With Strac — yes, and in bulk.
Does Google Drive DSPM (Data Discovery) help with SOC2, HIPAA, PCI, GDPR?
Absolutely. DSPM creates the inventory, controls, and evidence auditors demand.











.webp)














.webp)








