The modern enterprise doesn't live in a single server room anymore. It lives in a chaotic, multi-cloud mesh. You have customer logs in AWS S3, marketing analytics in Google BigQuery, corporate records in Azure Blob Storage, and a massive data lake in Snowflake.
And here’s the uncomfortable truth: Your data is moving faster than your security team.
Developers replicate production databases to "Test" environments in different clouds. Data Scientists pull PII into Databricks notebooks for modeling. DevOps teams leave unmanaged snapshots in regions you didn't even know you were using.
You can’t protect what you can’t see. That’s exactly where Cloud DSPM (Data Discovery) comes in.
This is the guide you wish existed years ago—tactical, real-world, and written specifically for the multi-cloud reality.
TL;DR
- Cloud DSPM (Data Discovery) provides a unified map of sensitive data across all your cloud environments (AWS, Azure, GCP) and data warehouses (Snowflake, Databricks).
- Most risk comes from "Data Sprawl"—sensitive data copied from secure production environments into insecure dev/test buckets or forgotten storage accounts.
- DSPM identifies what data exists, where it lives, who has access, and how it is misconfigured (e.g., unencrypted or public).
- Remediation includes automated tagging, redaction, encryption, and enforcing "Least Privilege" access.
- DSPM is the prerequisite for safe AI adoption—you cannot feed your data to an LLM if you don't know it contains hidden secrets.
- Strac provides automated scanning, risk scoring, and remediation across multi-cloud and SaaS in a single pane of glass.
What Is Cloud DSPM (Data Discovery)?
Cloud DSPM (Data Security Posture Management) is the process of:
- Discovering sensitive data across IaaS (AWS, Azure, GCP), PaaS, and DBaaS (Snowflake, MongoDB Atlas).
- Classifying it (PII, PHI, PCI, Secrets, Intellectual Property).
- Mapping access (Which IAM roles, users, or external accounts can read this data?).
- Assessing risk (Is this PII sitting in a public bucket? Is it unencrypted?).
- Remediating exposure (Redaction, Encryption, Deletion, Access Revocation).
In short: DSPM = Visibility + Understanding + Action
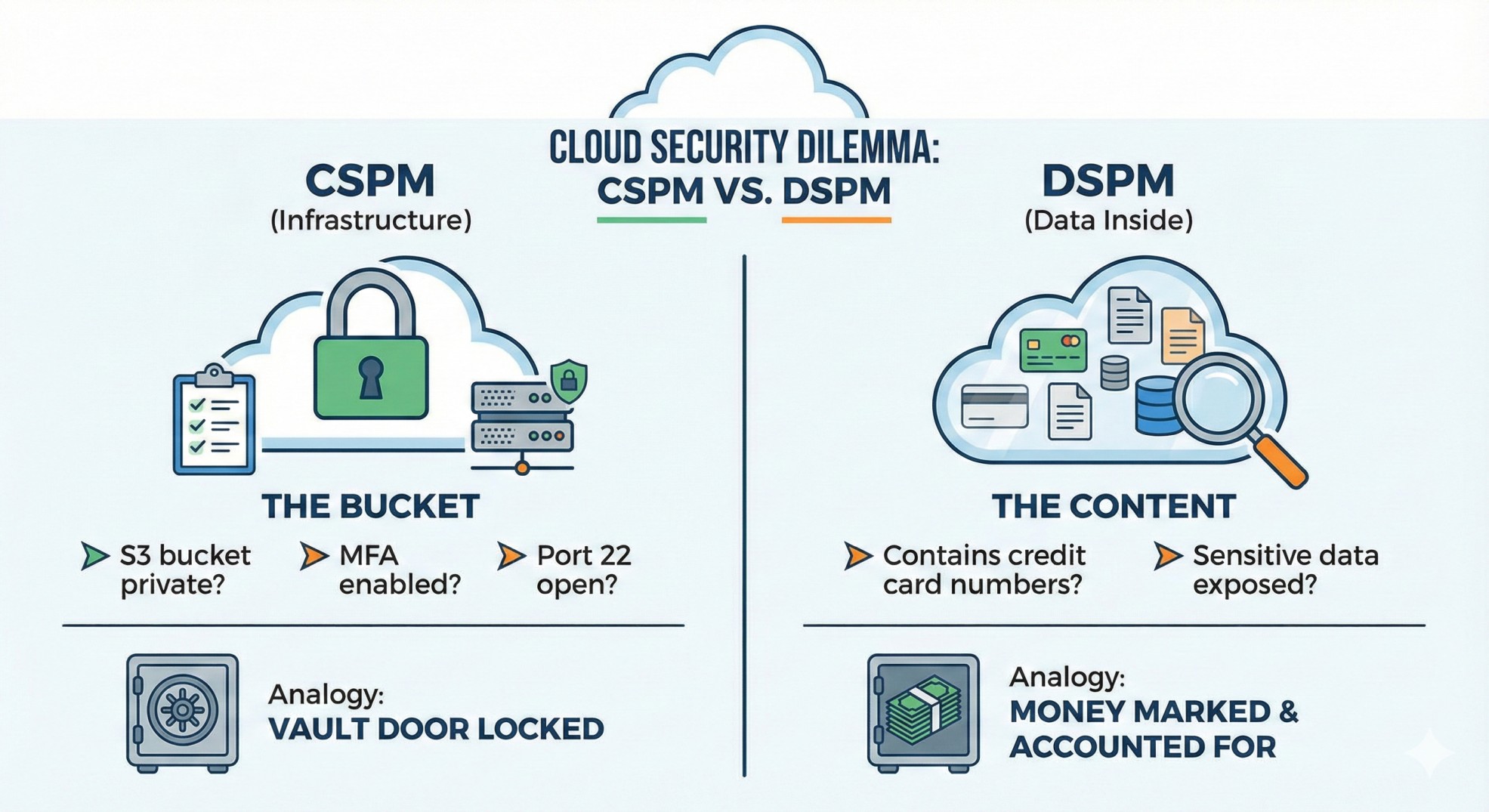
✨ Cloud DSPM vs. CSPM — The "Bucket vs. Content" Problem
This is the most common confusion in cloud security.
✅ CSPM (Cloud Security Posture Management) protects the infrastructure.
- Asks: "Is this S3 bucket private? Is MFA enabled on root? Is port 22 open?"
- Analogy: Checking if the bank vault door is locked.
✅ DSPM (Data Security Posture Management) protects the data inside.
- Asks: "Does this file inside the bucket contain 10,000 credit card numbers?"
- Analogy: Checking if the money inside the vault is actually marked and accounted for.
Why you need both: A "Private" bucket (CSPM compliant) that contains unencrypted, readable passwords accessible to every developer in your org is still a catastrophic breach waiting to happen.
Cloud DSPM vs. Cloud DLP — Why You Need Both
✅ DSPM = X-ray (Scans existing data at rest to find historical risks)
✅ DLP = Treatment (Blocks new data from leaving or being uploaded incorrectly)
Once DSPM uncovers that your "Archive" storage account contains unencrypted tax records, you use DLP to prevent employees from uploading similar files in the future.
👉 Learn more with our Cloud DLP solutions
This pairing creates true closed-loop protection.
Why Companies Need Cloud DSPM (Data Discovery)
The cloud is the default backend for the world. It stores:
- Object Storage: Documents, images, backups (S3, Azure Blob, GCS).
- Managed Databases: Customer profiles, transactions (RDS, Cloud SQL, Cosmos DB).
- Data Warehouses: Aggregated analytics (Snowflake, Redshift, BigQuery).
And these problems make Cloud high-risk:
✅ 1. The "Shadow Data" Crisis Developers spin up temporary resources for proof-of-concept work and forget to delete them. These "zombie" resources often lack the strict security controls of production but contain real data.
✅ 2. Multi-Cloud Fragmentation You might have strict policies in AWS, but what about that marketing project on GCP? Data flows effortlessly between clouds, but security policies often don't follow it.
✅ 3. The "Lift and Shift" Legacy Companies migrate on-prem servers to the cloud without cleaning them first. This means decades of old, unstructured files (with hidden PII) are dumped into cloud storage, invisible to modern tools.
✅ 4. Developer Over-Privilege In the cloud, identity is the perimeter. If a developer's IAM role has ReadOnly access to all storage accounts to "debug issues," they effectively have access to every customer secret you own.
✅ 5. Data Sovereignty & Compliance GDPR requires you to know if European customer data has drifted into a US-East storage region. Without DSPM, tracking data residency across clouds is impossible.
✅ 6. AI Risk (RAG & Training) If you point an enterprise LLM (like Azure OpenAI or AWS Bedrock) at your data lake, it learns everything. If that lake contains sensitive HR data, the AI becomes a leakage vector.
Historical Scanning in Cloud DSPM
Most native cloud tools are triggered by events (new file upload). They miss the petabytes of data that have been sitting there for years.
Historical scanning answers:
- Which Azure Blob container holds the backup from 2019?
- Are there API keys hardcoded in our old Google Cloud Function logs?
- Did we leave unmasked PII in a Snowflake "DEV" database?
- Is that "public" GCS bucket actually empty, or full of contracts?
Historical scanning must cover:
✅ Object Storage (S3, Azure Blob, GCS)
✅ Block Storage Snapshots (EBS, Azure Disk)
✅ Managed Databases (RDS, Cloud SQL)
✅ Cloud Logs (CloudWatch, Stackdriver, Azure Monitor)
✅ Data Warehouses (Snowflake, Databricks, BigQuery)
Without historical scanning, you’re blind to 90% of your cloud risk.
Access Visibility: Who Can See Your Data?
Finding the data is only half the story. You must know: Who has the IAM permission to read it?
Cloud DSPM identifies:
- Public Exposure: Resources accessible to
0.0.0.0/0orAllUsers. - Cross-Account Trust: Data shared with third-party vendors or personal accounts.
- Toxic Combinations: A sensitive file (e.g.,
passwords.txt) accessible by a broad role (e.g.,Intern-Role).
This is the difference between: "We have sensitive data in the cloud." and "We have sensitive data in a bucket that our marketing agency's vendor account can read."
Only the second is an immediate emergency.
✨ Remediation in Strac Cloud DSPM
Visibility without action is useless. Strac allows you to fix Cloud risks instantly.
✅ Auto-Tagging Automatically apply tags like Confidential,PII, or Do-Not-Deleteto cloud resources. This allows downstream policies to enforce stricter controls.
✅ Redaction Strac can physically redact sensitive values inside files (CSV, JSON, Text) or logs. It replaces a credit card number with ****-****-****-1234 directly in the object.
✅ Encryption Enforcement Identify unencrypted storage and trigger workflows to encrypt them with Customer Managed Keys (CMK).
✅ Permissions Right-Sizing Identify roles that have access to sensitive data but haven't used it in 90 days, and suggest revoking that access.
✅ Bulk Remediation Clean up thousands of exposed log files or orphaned snapshots in a single action.
How Cloud DSPM Protects Against AI & GenAI Risk
AI services (Azure OpenAI, AWS Bedrock, Vertex AI) are hungry for data. They are "Data Amplifiers."
When you connect a cloud data lake to an LLM, you risk:
✅ AI RISK #1: The "Knowledge Base" Leak If you use RAG (Retrieval-Augmented Generation) on your S3 or Blob storage, the AI indexes everything. An employee asking "What are the bonus structures?" might get an answer pulled from a sensitive HR spreadsheet you forgot was there.
✅ AI RISK #2: Model Poisoning Training a model on low-quality or sensitive data (like real SSNs) "bakes" that data into the model weights. You cannot simply "delete" it later; you have to retrain the model from scratch ($$$).
✅ Cloud DSPM is Step Zero for AI Before connecting any data source to an AI service:
1. Scan the source buckets/databases.
2. Clean (Redact/Delete) toxic data.
3. Certify the dataset as "AI-Ready."
How Strac Solves Cloud DSPM (Data Discovery)
Strac provides a unified Data Security Platform for the Multi-Cloud era:
- Coverage: AWS, Azure, Google Cloud (GCP), Snowflake, Databricks, MongoDB.
- Detection: PII, PHI, PCI, API Keys, Secrets, IP, Custom Regex.
- OCR: Scans images (passports, driver's licenses) and scanned PDFs in cloud storage.
- Real-Time & Historical: Scans existing "dark data" and monitors new data streams.
- Compliance: Maps findings to SOC2, HIPAA, PCI-DSS, GDPR, NIST, ISO 27001.
- Remediation: Redact, Label, Encrypt, Block Access, Delete.
🔗 Explore Strac's Cloud Integrations
🌶️ Spicy FAQs on Cloud DSPM
Why can't I just use Amazon Macie + Azure Purview + Google DLP?
You can, but you will have three different dashboards, three different billing models, and zero unified policy. You will spend your life correlating spreadsheets. Strac gives you one view across all clouds with a single policy engine.
Does Strac move my data out of the cloud to scan it?
Strac is architected with privacy in mind. We use ephemeral scanning where data is processed in memory and never stored on our servers. We give you the verdict (Risk/No Risk), not the data custody headache.
Can you scan private databases (RDS/Sql Server)?
Yes. Strac can connect to managed databases, scan schemas and tables for sensitive patterns (like a column full of SSNs), and report back without disrupting the application.
How is this different from a "Cloud Security" tool like Wiz or Orca?
Wiz and Orca are phenomenal at infrastructure (CSPM/CNAPP). They tell you vulnerabilities (e.g., "This VM has Log4j"). Strac tells you content (e.g., "This VM contains a file with 500 patient records"). You need both layers for a complete defense.
Trusted by enterprises
Discover & Remediate PII, PCI, PHI, and Secrets in AWS, Azure, and GCP











.webp)














.webp)








