The Essential Guide to Endpoint Encryption
Learn about the role of endpoint encryption and its benefits. Apply the best practices for effective data protection strategies to stay ahead of emerging threats
Imagine a world where your digital secrets are locked away and accessible only to you. Endpoint encryption is the key to this reality. It transforms sensitive data on devices into indecipherable code, barring unauthorized access and safeguarding against data breaches. This security measure is vital as a defense against external threats and internal risks like accidental leaks or deliberate sabotage.
For these reasons, endpoint encryption is a cornerstone of data protection. In this guide, we delve deep into the nuances of this crucial security measure. We'll discuss the role, benefits, and best practices of implementing endpoint encryption.
Endpoint encryption is a security measure that involves encoding data on endpoint devices. In essence, it converts data into an incomprehensible secure language without the correct decryption key. This process ensures that the information remains inaccessible to unauthorized users even if the data is intercepted or the device is lost or stolen.
Without endpoint security, sensitive data are exposed to potential breaches. This includes personal identifiable information (PII) like social security numbers, financial details like credit card numbers, confidential business information, intellectual property, and even personal photos and communications.
Endpoint encryption software converts data into a coded format or unreadable cipher text without the correct decryption key. When data is saved onto an endpoint device, such as a laptop or smartphone, the encryption algorithm transforms this data into a secure form.
This process involves complex mathematical algorithms, like Advanced Encryption Standard (AES) and Rivest-Shamir-Adleman (RSA), that scramble the data, making it inaccessible to anyone who doesn't have the decryption key. There are two primary types of endpoint encryption:

Here are the benefits of endpoint encryption, highlighting how it safeguards sensitive data and promotes overall organizational security.
Many standards, such as the Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), and Payment Card Industry Data Security Standard (PCI-DSS) demand rigorous protection of sensitive data.
Encryption transforms sensitive data into a secure code, readable only with a specific key. This ensures that the data remains protected and confidential even if accessed by unauthorized parties, meeting regulatory requirements.
Related Reads: How DLP helps with Endpoint security compliance ?
As per the data breach report by IBM, the average total cost of a ransomware breach in 2023 has escalated to $5.13 million, which is a 13% increase from the previous year. With the rise in cybercrime, encrypting sensitive data is a proactive measure to prevent potential breaches and cyber-attacks. It ensures that data accessed by unauthorized individuals remains unreadable and secure.
Endpoint encryption software can protect data across devices as remote work becomes more prevalent. Encrypting data on laptops, smartphones, and tablets ensures sensitive information remains secure, regardless of where the device is being used. This is particularly crucial in a world where work-from-home arrangements and mobile workforces are the norm.
While the initial investment in endpoint encryption may seem substantial, it is cost-effective in the long run. The cost of a data breach can be significantly higher, not just in terms of financial loss but also in reputational damage. Investing in encryption can save organizations from these costly consequences.
Modern endpoint encryption solutions, like Strac, offer simplicity in deployment and management. These user-friendly solutions are designed to make it easy for organizations to implement and maintain robust data security measures. With technological advancements, managing encryption across various devices and platforms has become more streamlined and efficient.

Here are a few best practices to implement and manage endpoint encryption effectively.
It is crucial to involve essential IT, legal, and management teams in the planning phase. This collaborative approach ensures that critical data is identified and adequately secured, aligning encryption strategies with organizational goals.
Establishing clear, detailed policies regarding what data to encrypt and how to manage access is fundamental. These guidelines should be tailored to your organization's specific needs and regulatory requirements.
Encrypting data on removable media like USB drives is vital for protecting portable data. This practice prevents unauthorized access to sensitive information that leaves the organization's premises.
Utilizing established, secure encryption methods such as AES-256 or RSA is essential for robust data protection. These standards have been tested and proven effective against various security threats.
Effective key management systems are crucial for data recovery. Secure and centralized key management ensures that encryption keys are safely stored and accessible when needed.
Before integrating encryption with your broader cybersecurity strategy, conducting thorough assessments of the devices is important. This ensures that the encryption is applied to systems free of vulnerabilities or corruption.
Endpoint DLP is a pivotal component in endpoint encryption, offering advanced features to enhance data security and streamline compliance.
Strac's endpoint DLP provides extensive visibility into data stored and transferred across endpoints, enabling organizations to monitor and control the movement of sensitive information effectively.
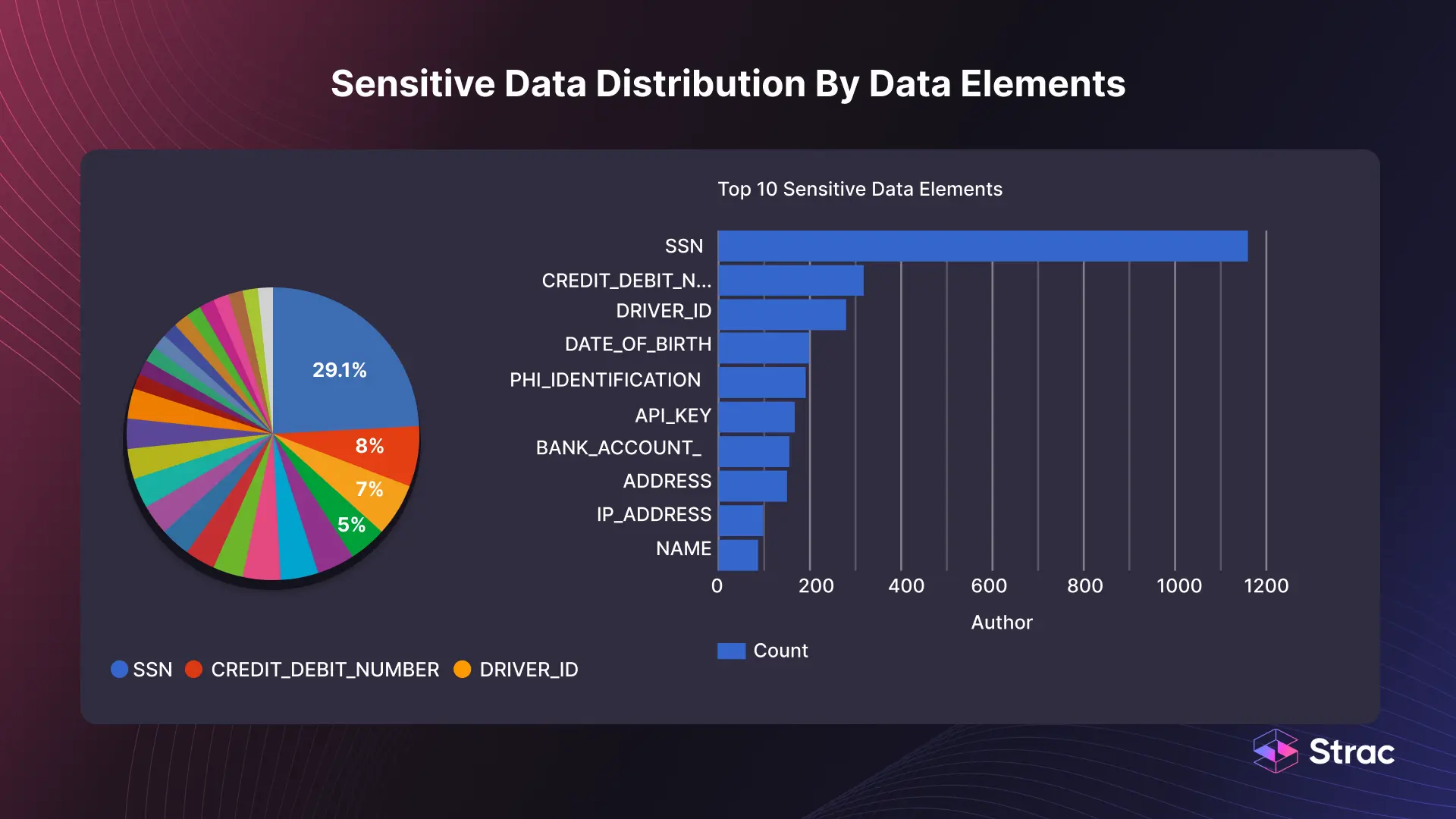
The platform offers sophisticated content inspection capabilities, analyzing data in-depth to identify sensitive information. Coupled with behavior analysis, it can detect and mitigate risks posed by unusual or unauthorized user activities, enhancing the security of encrypted data.
Strac's endpoint DLP aids in maintaining compliance with various data protection regulations. Its real-time intervention capabilities allow for immediate responses to potential compliance breaches, ensuring encrypted data remains within regulatory boundaries.

The solution integrates seamlessly with existing encryption and security systems, enhancing the overall effectiveness of data protection strategies. This integration ensures robust data loss prevention measures complement encryption efforts.
Strac's endpoint DLP includes strong control features for both devices and applications. This ensures that encrypted data is accessed and used appropriately across all endpoints, further securing the data environment.

The platform extends its protection capabilities to email and cloud storage, monitoring these channels for potential data leaks or breaches. This feature is particularly important for encrypted data shared or stored in these mediums.
Strac enhances overall data security by enforcing encryption policies. It ensures that sensitive data is encrypted according to set standards, thereby maintaining high data protection.
Even when devices are offline, Strac enforces data protection policies, ensuring continuous security. Its machine-learning detection capabilities further enhance its ability to identify and protect sensitive encrypted data.